
Introduction
Last week we reported on the xDedic underground marketplace that facilitated the selling and buying of access to compromised RDP servers. We counted over 70,000 hacked server accounts from 173 countries for sale on the marketplace. After the public announcement the xDedic website very quickly went offline, thanks to the cooperation of several major ISPs. However, it seems that this was not the end of the story.
The day after the announcement, an anonymous source from a Lithuanian IP address posted an unusual comment on our blog using the alias “AngryBirds.”
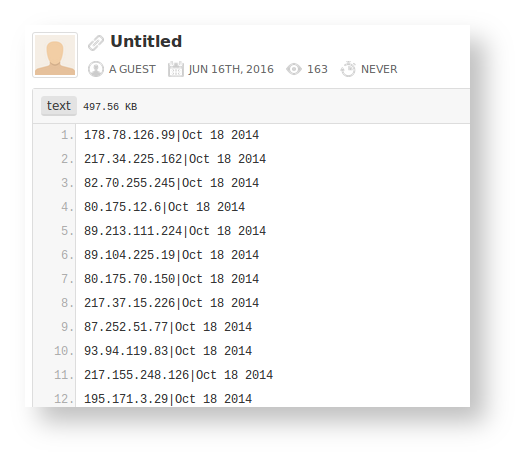
We usually take such comments with a pinch of salt and generally don’t pay too much attention to comments with strange links. However, this time the links pointed to a series of pastes on the popular resource Pastebin, which in turn contained long lists of IP addresses and date information.
One such paste contains about 19,000 records. The author of the comment mentioned that the list of pastes is related to hacked servers from the xDedic marketplace. At first glance it looked real – the earliest date was close to the time when the first servers were listed on xDedic (according to our records the first server was added in November 2014). However, we were slightly sceptical and decided to validate the list before making use of it. With this blogpost we share the results of that validation and our thoughts on the data we received.
We have collected and concatenated all the pastes in one list: it contains around 176,000 unique records from October 2014 to February 2016.
Validation Challenge
The first problem we faced is that we didn’t have full IP addresses from the xDedic marketplace, because the marketplace revealed only first two octets of each IP. We had some data from the sinkhole, but this was just part of the full xDedic dataset and related to the operation of a single criminal (group) relying on the SSCLIENT backdoor that we managed to sinkhole. The problem becomes even worse when you consider the fact that our sinkhole data starts from the end of March 2016 while the Pastebin dataset ends at the end of February 2016. Theoretically, we can’t provide a strong validation of the submitted data. Nevertheless, we decided to do our best.
One way of comparing the datasets was to check the correlation between the numbers of servers added monthly, so we combined them into one chart, seen below:
The orange bars show the number of servers added to the marketplace while the blue bars show the IPs found on Pastebin. There is a weak but still recognizable correlation between the two datasets starting from June 2015. We have no solid theory as to why this began in June 2015, but one thought is that the developers of xDedic introduced a major change to the platform code around that time which somehow affected the server information displayed.
Another check we did was to see how much the Pastebin dataset overlaps with our data from the sinkhole. As mentioned above, the sinkhole data started coming in at the end of March 2016 while Pastebin data ends in February, leaving a one month gap between the two datasets. However, we should still see an element of overlap considering that some servers could have been resold on the marketplace. And so it turned out: 1,303 unique IP addresses were found both in our sinkhole data and in the Pastebin data.
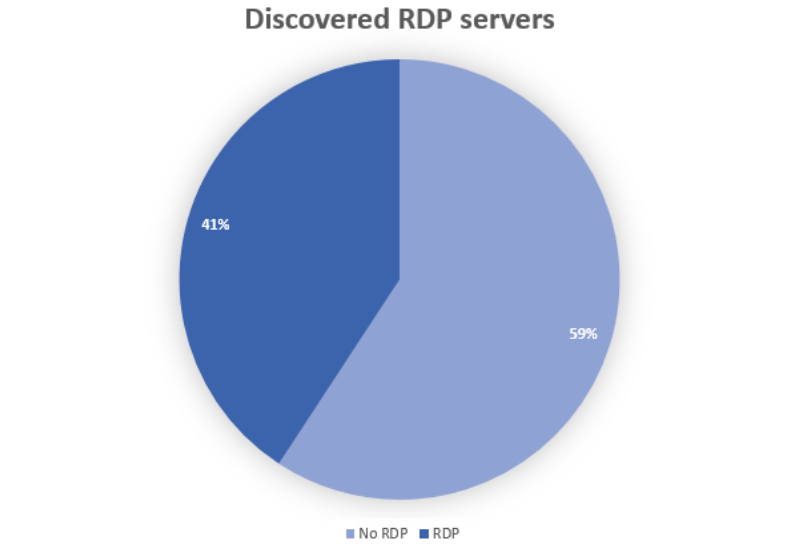
Next, we decided to check how many of the reported IP addresses from the Pastebin dataset were RDP servers. So we simply scanned known IPs for the most popular RDP ports. The results were quite impressive: 71,784 IPs had the RDP service running on port range 3300-3400 (most of them were on standard port 3389).
Finally, we decided to compare the list of subnets, based on the first two octets we had from the marketplace before March 2016 and check to see if these subnets were part of the Pastebin data too. The results were astonishing:
| Subnets from marketplace before March’16 | Subnets that matched Pastebin dataset |
| 8,721 | 8,718 |
There were only three IPs on the marketplace which didn’t make it into Pastebin dump. We checked those and found that they were added on 29th of February 2016. We assume that these three IPs (subnets) were added at the end of the day, right after the Pastebin dump ended.
Aftermath
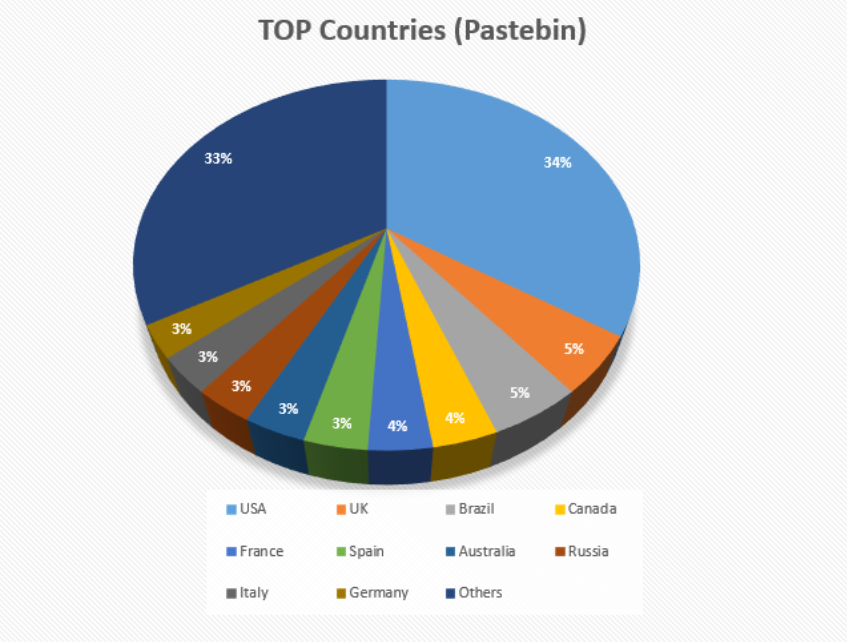
We sorted the Pastebin IPs by the country they belong to and got a different picture compared to what we saw previously. Here is the new TOP 10 (new countries marked in bold):
| Marketplace TOP 10 | Pastebin TOP 10 (NEW) | |||
| # | Country | Compromised Servers | Country | Compromised Servers |
| 1 | Brazil | 6,540 | USA | 60,081 |
| 2 | China | 5,023 | United Kingdom | 8,817 |
| 3 | Russia | 4,020 | Brazil | 8,770 |
| 4 | India | 3,488 | Canada | 6,112 |
| 5 | Spain | 3,155 | France | 5,973 |
| 6 | Italy | 3,119 | Spain | 5,954 |
| 7 | France | 2,474 | Australia | 5,855 |
| 8 | Australia | 2,448 | Russia | 5,608 |
| 9 | South Africa | 2,438 | Italy | 5,536 |
| 10 | Malaysia | 2,140 | Germany | 4,988 |
If we compare visually what we saw on the marketplace and on Pastebin:
Interestingly, the number of servers hosted in the USA and the UK jump into the TOP 10 to rank first and second respectively. Also, Canada and Germany now appear in the TOP 10. This may make more sense when you consider that the marketplace data concerns only unsold offerings, while the huge Pastebin dataset could reflect a more realistic picture of all compromised servers. This suggests that the source of the data is either high-frequency monitoring of the xDedic marketplace (with access to full IP information) or someone had advanced access to the backend (be it a hosting provider or one of the developers). Meanwhile our charts from the sinkhole also had the USA, the UK and Germany in the TOP 10, which supports the fact that the real picture should have these major countries in the TOP 10.
Extra Note
In our earlier report we mentioned that the average server on the xDedic marketplace cost around $7-8 USD. However, many journalists asked us: “What was the most expensive server for sale on xDedic?”
When we looked at the data again we saw one server that cost $6,000 USD. In fact, only around 50 servers cost more than $50 USD, and all of them were located in the USA, from Alaska to Florida. The TOP 10 most expensive servers on xDedic marketplace were offered by a single criminal (group) with the alias “Narko“:
| Subnet | State | City | OS | Date | Price, USD |
| 72.69.*.* | Illinois | Chicago | Windows 7 | 03.04.2016 | $6,000 |
| 50.195.*.* | Massachusetts | New Bedford | Windows 7 | 12.05.2016 | $4,000 |
| 173.10.*.* | Washington | Bellevue | Server 2012 R2 | 29.04.2016 | $4,000 |
| 162.233.*.* | Mississippi | Lucedale | Windows 7 | 05.04.2016 | $4,000 |
| 104.57.*.* | Oklahoma | Stratford | Windows 7 | 10.05.2016 | $4,000 |
| 97.87.*.* | Michigan | Davison | Windows 7 | 24.12.2015 | $2,500 |
| 50.255.*.* | Michigan | Ypsilanti | Server 2012 R2 | 18.03.2016 | $2,000 |
| 108.58.*.* | New York | Hicksville | Server 2008 R2 | 11.04.2016 | $2,000 |
| 74.124.*.* | North Carolina | Randleman | Windows 7 | 18.04.2016 | $1,500 |
| 24.178.*.* | Georgia | Gainesville | Windows 7 | 08.04.2016 | $1,500 |
We can only speculate as to why these servers cost more than others, but there is no objective way to find their exact IPs because they were added to xDedic after the period covered by the Pastebin dataset.
Conclusions
If we consider the newly obtained Pastebin data as authentic this can help many organizations, companies and individuals to identify compromised servers they own. For us it was yet another confirmation that when it comes to cybercrime, we often see just the tip of the iceberg. The reason why the xDedic marketplace looked smaller to the buyer is because the most desirable servers were often sold almost as soon as they were added to marketplace, leaving only the least interesting and unwanted servers for sale.
After all the analysis we still have many questions:
- Where does the data come from?
- Why does the dataset from Pastebin not include more data from March to June 2016? That would make validation far easier.
- How many of these IPs are still compromised now?
What we can tell for sure is that the Pastebin dataset:
- Matches the timeline of the xDedic operation.
- Contains the IPs of many RDP servers.
- Contains many IPs of known compromised RDP servers.
- Shows a correlation with the dynamics of the xDedic marketplace offering.
- Contains 100% of the subnetworks we saw on the xDedic marketplace within the same timeframe.
In any case, whatever unanswered questions remain, it makes sense for the system administrators of the listed IP addresses to check carefully for a potential past compromise of their servers.
Since much of this information has already become public through the open comment on our blog post, we are releasing for national CERTs a full combined list of IPs with country code based on the GeoIP.
On the assumption that the Pastebin data provided by AngryBirds is genuine, we would like to say a formal thank you for sharing this data with us. However, there is one thing that can be improved next time, namely responsible disclosure. Making this data fully public may encourage other criminals to attack easy targets or result in the undeserved public shaming of administrators who run currently secure systems.
Had we received this information via a private channel (email, private URL, etc.), we would have been happy to relay it to CERTs and local authorities of affected countries via our established channels and partners. So we would ask that in future those who respond to our research refrain from dumping such data into the public domain. Thank you!
A full combined list of IPs with country code based on the GeoIP (.csv file)
The tip of the iceberg: an unexpected turn in the xDedic story
























MacSys
Who gave you the rights to scan the ports ? This is illegal, you know this ? And you posted the list of Ips in the official article…
OtherSys
I’m kind of glad they did, actually
Netops
Ditto.
To OP: Most definitely NOT illegal to do simple scanning. Research organization and watchdogs are scanning all the time – and I’m thankful they do. They responsibly inform parties of potential problems.
And THANK YOU Kasp for posting the IPs. At least now people can check to see if they have any compromised hosts on the list. Thankfully, we do not. 🙂