
It is a well-known fact that events of global interest are exploited by cybercriminals for financial gain. Natural disasters in the past like the earthquake in Haiti, hurricane Katrina or the earthquake in New Zealand a few weeks ago are proof of this. The current situation in Japan is no exception. Such cases are a golden opportunity for cybercriminals and cybervandals whose main aim is to make a profit, even if it means exploiting other people’s misery.
There are lots of ways you can make donations to help the people of Japan, but the sheer number of charity organisations and campaigns can confuse those who want to donate. What is more, it’s not always clear whether the people behind these campaigns can be trusted.
The same goes for the overwhelming flood of information and news in such situations. Nowadays, we have the traditional mass media – TV stations, radio and newspapers – as well as lots of websites, blogs, video portals and social media sites which promise news in real time.
This variety plays into the hands of cybercriminals. The quality of the scams that accompany such events is steadily increasing, which makes it more and more difficult to determine how trustworthy they are. The criminals use modern media and social engineering in particular to lure victims into their scams. They’re mostly manipulating human emotions:
- Charity, to donate money
- Sensationalism
- Exploiting a desire to help the victims
- Causing panic
In the case of Japan the cybercriminals pulled out all the stops. It is over a month since a major earthquake and tsunami struck on 11 March – time to review the most important events from a security perspective.
Please note: this article makes no claim to be complete, but shows a variety of incidents in chronological order.
March 11 – Google relaunches Person Finder
In February, Google helped in the aftermath of the New Zealand quake by releasing Person Finder. Google relaunched its app to support people affected by the Japan crisis. Person Finder is a tool that helps locate missing people. Back to top
March 12 – First Facebook likejacking scams appear
The first Facebook likejacking scam to pick up the tsunami was rather surreal:
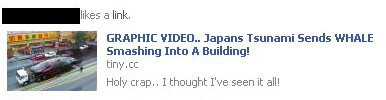
After clicking the link, the user is redirected to a Facebook website which appears to have a Flash Player window showing the video. But clicking anywhere leads to a status message spreading among your friends and to a survey, which the user is asked to fill out in order to watch the video and the chance, allegedly, of winning an iPad 2, an iPhone or a laptop. The cybercriminals behind the scam gain money for every survey form that is filled out.
Another similar scam does more or less the same, with the main difference being that the website allegedly containing the video doesn’t look like Facebook, but more like YouTube. There’s also a fake lottery to win iPads and iPhones.
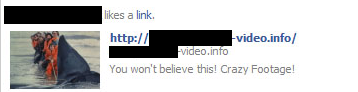
Otherwise, it also spreads the message via the Facebook news feed and tricks users into filling out a survey. Back to top
March 13 – New likejacking scams on Facebook promoting non-existent tsunami videos
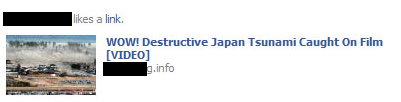
The scam is designed like the examples above and ends with offers for cheap insurance. The video, like in most cases, doesn’t play.
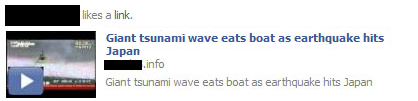
The website wants the user to accept one of its offers in return for showing the video – which again doesn’t exist. The offers include browser games, insurance offers and customized Facebook themes. The website passed this behaviour off as age verification for the video. Back to top
March 14 – Fake American Red Cross donation messages spread via Twitter
Besides Facebook, Twitter was also used to spread scams related to the disasters in Japan. Faked Red Cross Twitter accounts began to send out appeals for money. It was claimed that the funds would support people in Japan. Back to top
March 14 – Massive black SEO campaign with 1.7 million pages according to Google
According to SANS and Google, shortly after the Japan disaster over 1.7 million pages were leading to rogue AV via a massive black SEO campaign. Obviously, the cybercriminals are very active and able to react very quick to such hot topics in the media. Back to top
March 14 – Reports of radiation in SMS hoax cause panic in the Philippines
According to reports from Spiegel and the BBC an SMS hoax spread in the Phillipines. The text stated that a radioactive cloud was due to reach Manila on Monday, 14 March at 4pm, and was allegedly sent by a British news channel. The aim of this hoax seemed to be purely to create a state of hysteria, as there was no obvious sign of financial gain. Back to top
March 15 – Fake Japan donation groups appear on Facebook
Hundreds of groups and pages appealing for donations are created on Facebook within a matter of days. Some promise to donate a certain amount of money every time someone clicks the corresponding ‘Like’ button, while others offer the chance to send money to an account via an online payment system. The real intentions behind many groups were difficult to figure out. Back to top
March 15 – IT expert Michael Horn, aka Nibbler, initiates the ‘geigerCrowd’ project
Hacking for Japan: IT expert Michael Horn, aka Nibbler, initiates the project geigerCrowd. His project uses crowdsourcing to develop the software as well as to process the radiation data from different locations and then to visualize it. Back to top
March 16 – Links in spam messages lead to malicious website
One of the first waves of spam exploiting the situation in Japan used several headlines, all of them genuine and taken from BBC News. The links, however, lead to a malicious website which uses Java exploits to spread malware.
This screenshot above shows a sample received on 19 March. Our colleague Nicolas has already blogged about a similar example received on 16 March. Back to top
March 17 – Fake Twitter mail lures users with video from inside Fukushima I
This sample pretends to be sent from Twitter and lures users with a video of the exclusion zone around Fukushima. The link redirects users to a malicious website serving variants of the Trojan-Downloader.Win32.Codecpack via multiple exploits from the Incognito exploit kit.
Our colleague Nicolas recently wrote a blogpost about it. Back to top
March 18 – Airline ticket scams uncovered
According to Koreatimes.co.kr, South Koreans were defrauded after paying for airline tickets that weren’t available. The tickets were sold out following panic by people who wanted to leave the country.
The scam said that two tickets had been cancelled and were now available for sale. The offer allegedly came from an employee of a travel agency. The victims were asked to send a copy of their passport and to transfer $674. The cybercriminals got hold of both the money and personal data. Back to top
March 18 – Spam with fake requests for Japan donations
The sender of this spam message is allegedly a member of a Japanese community forum. The donation should be sent via Western Union, a very popular online payment portal among scams of this type, which offers strong anonymity for the people behind them.
Our colleague Michael also blogged about this case. Back to top
March 23 – Spam messages allegedly sent by the British Red Cross
This is a relatively late example of a fake donation scam. It tries hard to look like it was sent by the British Red Cross. However, the sender’s address is forged.
A special feature of this sample is the ease with which people can donate money…which, of course, goes right into the pockets of the cybercriminals. At the bottom of the email you can see an HTML-based donation form. The victim is also asked to give personal information. This way, the criminals kill two birds with one stone.
March 25 –Websites continue to spread malware
On 25 March, our colleague Michael found another website spreading malware. It advertises a video with the headline roughly translated as ‘New tsunami reaches the Sendai area, Japan declares state of emergency at nuclear power plant’. Clicking on the page, however, downloads and executes a file we detect as Trojan-Downloader.Win32.AutoIT.po, which again downloads three additional binaries.
March 28 – Another fake donation email allegedly from the Red Cross
Another wave of fake Red Cross donation emails, this time pretending to be sent from the Japanese branch.














































The Japan crisis – an IT security timeline