
The Desert Falcons are a new group of Cyber Mercenaries operating in the Middle East and carrying out Cyber Espionage across that region. The group uses an arsenal of homemade malware tools and techniques to execute and conceal its campaigns on PC and Mobile OS.
#FalconsAPT is the 1st known campaign to be fully developed by Arabic #hackers to target the Middle East #TheSAS2015
Tweet
The first Desert Falcons operations were seen in 2011 and the group made its first infections in 2013. By the end of 2014 and beginning of 2015 the group was very active.
Full report
The full report can be found here.
FAQ
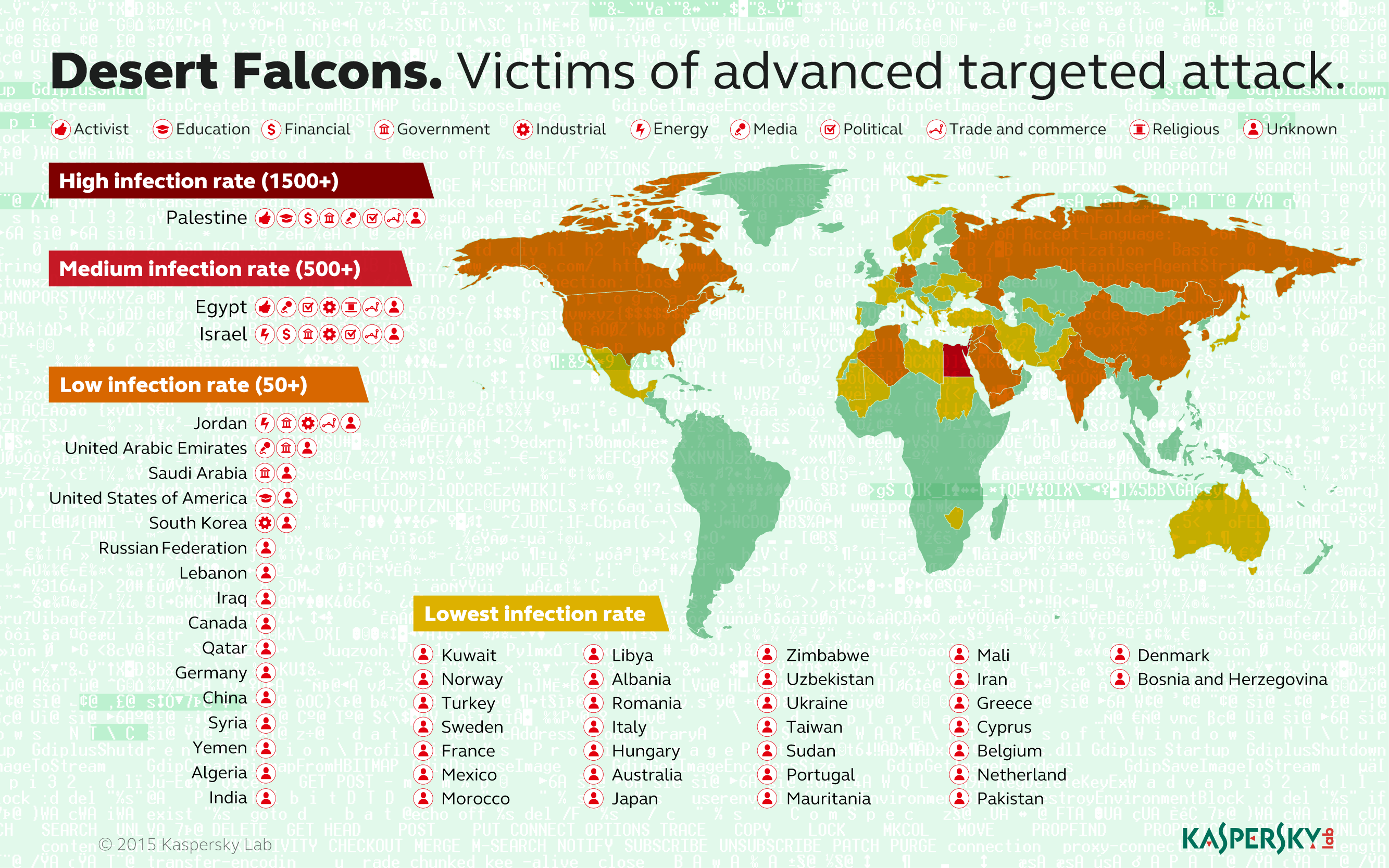
Where are the Victims Located?
There are more than 3,000 victims in 50+ countries. Most of them are found in Palestine, Egypt, Israel and Jordan, but others have been discovered in Saudi Arabia, the UAE, the US, South Korea, Morocco, Qatar and others.
Who are the Victims?
The attacks targeted several classes of victim, including Military and Government organizations, employees responsible for health organizations, combating money laundering, economic and financial institutions, leading media entities, research and educational institutions, energy and utilities providers, activists and political leaders, physical security companies and other targets that have access to important geopolitical information.
How are the victims infected?
Malware writers use a variety of technical and social engineering methods to deliver their files and encourage victims to run them, creating an effective infection vector. Examples include a fake website that promises to publish censored political information and asks users to download a plugin to view a video (the plugin contains the malware). Another example involves the use of spear phishing emails or social network messages to deliver malicious files using an extension override (e.g. malicious files ending with .fdp.scr would appear .rcs.pdf).
Sample of documents and videos used in spear phishing
What are the goals of the operations?
The attackers are looking for sensitive intelligence information that could help them in further operations or even extortion. The victims are targeted for the secrets in their possession or intelligence information relating to their positions in governments or important organizations.
More than 1 million files were stolen from victims. Stolen files include diplomatic communications from embassies, military plans and documents, financial documents, VIP and Media contact lists and files.
Who are the attackers and what do we know about them?
The Desert Falcons operators are native Arabic speakers. There are about 30 of them working in three teams. Some of their identities are already known. The attackers are running three campaigns to target different types of victim.
Where are the attackers based?
The attackers are based in Palestine, Egypt and Turkey.
Which malware do they use to infect their victims?
There are three main backdoors used to infect victim devices:
Computer backdoors
- The Main Falcons Trojan
- The DHS* Spyware Trojan
Computer Backdoors give the attackers full scope to use keyloggers and screenshotters, access files and even make audio recordings. DHS naming is used by the attackers to describe the nickname initials of one of the developers (D** H*** Spyware).
Mobile Backdoor
- A mobile backdoor targeting Android devices.
Mobile Backdoors give attackers access to Call and SMS logs
How did you become aware of this threat? Who reported it?
We became aware of the threat during an incident investigation in the Middle East.
Is it still active?
The operation is very active and is currently in peak condition. We are continuously identifying new samples and victims for all related campaigns.
How is this different from any other Cyber espionage attacks?
Desert Falcons are the first known Cyber espionage attacks to be fully developed and operated by Arabic speakers to target the Middle East. It has affected a stunning range of victims, stealing more than 1 million special files.
Is this a nation-state sponsored attack?
The profiles of the targeted victims and the apparent political motives behind the attacks make it possible that Desert Falcons operations could be nation state sponsored. At present, though, this cannot be confirmed.
Why this name?
The falcon is a rare bird that has been highly prized for a centuries in desert countries in the Arab world. It is a symbol of hunting and sharp vision. The Desert Falcons are proficient cyberhunters with carefully chosen targets, all of whom are thoroughly investigated before the attack and closely watched after being infected.
How can users protect themselves?
Kaspersky Lab products detect and block all variants of the malware used in this campaign:
Trojan.Win32.DesertFalcons
Trojan-Spy.Win32.Agent.cncc
Trojan-Spy.Win32.Agent.ctcr
Trojan-Spy.Win32.Agent.ctcv
Trojan-Spy.Win32.Agent.ctcx
Trojan-Spy.Win32.Agent.cree
Trojan-Spy.Win32.Agent.ctbz
Trojan-Spy.Win32.Agent.comn
Trojan.Win32.Bazon.a
The Desert Falcons targeted attacks



























Ivan
Are you going to provide further technical details about the backdoors? Thanks.
E K
There are some details in the full report https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/08064309/The-Desert-Falcons-targeted-attacks.pdf
If you want some additional information, please, write an e-mail to “intelreports [at] kaspersky.com”
Lazarus
Any thoughts on whether this is associated with the “MoleRats”, previously identified by FireEye?