
The Java 0day activity that we have been monitoring and preventing for almost the past week has been irresponsibly reported on other blogs, with early posts publicly linking to known sites serving the 0day. In itself, the race to publish on this 0day that will be assigned CVE-2012-4681 (a problem with processing access control within “protection domains”), has been irresponsible. Would you encourage folks to walk down a mugger’s dark alley with no protection or would you work to communicate the muggers’ whereabouts to the right folks and work on lighting the alley or giving better directions? Would you provide muggers with some new weapons that they haven’t considered? The efforts this time around seem misplaced.
Anyway, initial sites hosting the exploit were unique and spreading known APT related toolset components, including a Poison Ivy variant. Here is a somewhat unexpected heat map of early, related PIvy detections.
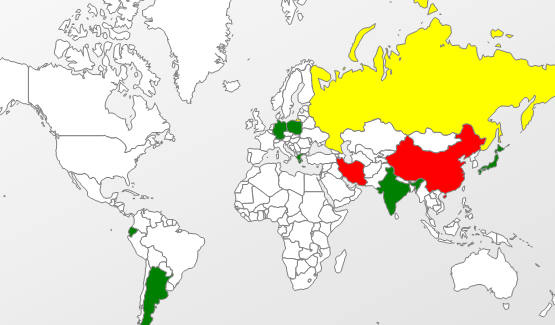
And here is a heat map of early detections for related web pages and javascript delivering the Java exploit:
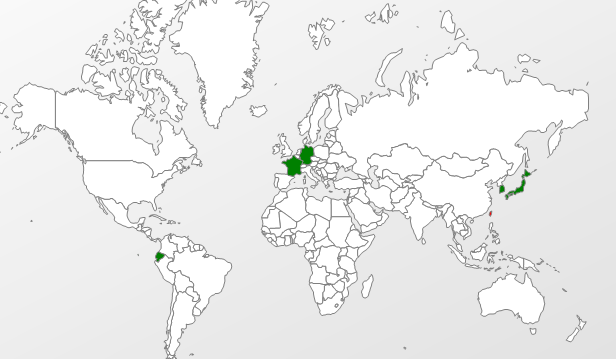
All the related malware that I have seen to this point targeted Windows systems. The exploits are effective against Java 7 and since the initial targeted attacks, news and the samples spread throughout the broader security community and the exploits made their way to metasploit developers, who added PoC to the open source framework. In turn, the Blackhole authors added the exploit to their COTS. So the attacks are widespread at this point. The first victim regions to be hit with the Blackhole stuff were the US, the Russian Federation, Belarus, Germany, the Ukraine and Moldova. But, in relation to the other exploits included in the pack, victims are getting hit only a fair number of times with the 0day. Internet Explorer users are being hit the most, followed by Firefox, Chrome, and Opera, and then a variety of other applications that handle URLs within their documents and eventually pass the malicious .jar on to a Java client, like Adobe Reader.
We are using a variety of detections and techniques to identify the malicious sites, the web pages involved, the exploit code, and the backdoor payloads delivered by these sites. Even though this particular Java 0day is getting hyped, other older exploits in the Blackhole exploit pack continue to get hit on victim systems with higher volume. So our community is protected from the Blackhole sites themselves, the Blackhole webpages serving the Blackhole Java 0day, compromised sites redirecting to the Blackhole sites, the more prevalent older Blackhole exploits and their delivery pages, and the trojans being delivered by these Blackhole sites. In addition to all that, Kaspersky “Advanced Exploit Prevention” adds another runtime/behavioral layer of protection against the 0day itself with with “Exploit.Java.Generic”. This addition is the most interesting to myself – exploit pack authors have been focused on improving their Java exploit server-side polymorphism, and this AEP feature defeats those efforts. So, our user community will see access denied altogether for current Blackhole sites, individual Blackhole web pages detected with variations on “Trojan-Downloader.JS.Agent”, the backdoors detected with “Trojan.Win32.Generic” and others (i.e., 61A3CE517FD8736AA32CAF9081F808B4, DEC9676E97AE998C75A58A02F33A66EA, 175EFFD7546CBC156E59DC42B7B9F969, 0C72DF76E96FA3C2A227F3FE4A9579F3), and the 0day Java exploit code detected with “HEUR:Exploit.Java.Agent.gen” (i.e. E441CF993D0242187898C192B207DC25, 70C555D2C6A09D208F52ACCC4787A4E2, E646B73C29310C01A097AA0330E24E7B, 353FD052F2211168DDC4586CB3A93D9F, 32A80AAE1E134AFB3D5C651948DCCC7D) among others, along with the runtime AEP prevention. So while you may see a few links to Virustotal with the inevitable complaining that a scanner is missing a specific chunk of altered code along with innaccurate claims that “AV is dead!” or “AV can’t detect it”, you should take them for the grain of salt that they are. The real story about client side mass exploitation is more complex than those claims. Some researchers call the various points in a delivery vector a kill chain, and Kaspersky products are killing it.
At the same time, Oracle needs to step it up and deliver an OOB patch, which historically they have failed to do. Maybe this event will provide even more pressure to step up their security update delivery process. They have been snapping up some good security research talent and beginning to reach out, which is a start. A very late start.
UPDATE (2012.08.30): Oracle patches CVE-2012-4681 and two other client side RCE vulnerabilities. It is probably a better idea for Windows users to go to their control panel, find the Java applet, and use the Java update software to manually get the latest JRE 7 and 6 releases – the default delay for the Java Update package to check is currently one week for the Java 7 installer.























The Current Web-Delivered Java 0day