
January 18, 2004 – Email-Worm.Win32.Bagle.a appears. This new malicious program immediately causes a worldwide epidemic. No one in the antivirus industry was sure what the author’s plans for his creation might be.
A detailed analysis of Bagle.a code showed that it would cease propagating on January 29, 2004. Kaspersky Lab analysts decided this meant that new versions were bound to appear. The first modifications of Bagle did indeed appear within a month.
Each new version contained new features which made it harder to detect and/or caused a more serious outbreak – that is, more machines were infected. The evolution of Bagle is detailed in the table below.
| Modification | Detected | Innovations |
| Bagle.b | Feb. 17, 2004 | The worm’s executable file was packed to make analysis more difficult. |
| Bagle.c | Feb. 27, 2004 | Excel file icons were used as attachment icons, in order to trick recipients into opening the infected attachment. The author also used social engineering techniques in message headers to tempt curious users into opening the email. |
| Bagle.d | Feb. 28, 2004 | The author seems to have decided that most users do not trust Excel files, which are well known for potentially containing malicious code. Instead, the executable attachments are disguised using standard text file icons. |
| Bagle.f | Feb. 29, 2004 | The author begins using P2P networks as an additional infection vector. The tempting names of the P2P files are clearly a social engineering technique — such as, Microsoft Office 2003 Crack, Working!.exe, Porno pics archive, xxx.exe and so forth. This latest modification infects yet more computers. The author is now aware that antivirus vendors are successfully blocking new outbreaks of Bagle and introduces a new approach. Infected attachments are placed in password protected archives and the password is included in the message body. |
| Bagle.i | Mar. 3, 2004 | This modification is the opening shot in the so-called Virus Wars of 2004. Bagle.i contains an insult directed at the author of NetSky. In the future, new Bagle versions will delete NetSky versions from infected computers. Bagle.i also contained a clever social engineering trick — the email text contained a message purportedly written and signed by Kaspersky Lab, while the sender address was spoofed to look as if the message came from @kaspersky.com. |
| Bagle.n | Mar. 13, 2004 | This modification uses a number of new techniques to hinder detection by antivirus solutions and/or identification by users. For one, the password for the infected archive is a graphics file instead of the text files that antivirus vendors were already detecting. This version is also the first to be written using polymorphing techniques. As Bagle.n propagated it also mutated, making it more difficult to identify and detect. |
With each new version, Bagle’s author continues to hone previous techniques and introduce additional ones. The Internet community continues to be fooled by newer versions, and virus analysts are kept on their toes. The newer Bagle versions will:
- block access to antivirus sites from infected machines, which prevents users from downloading the latest updates that they need to cure and block new Bagles;
- contain longer and more complete lists of processes that the worm blocks, including antivirus and firewall services. Once again, users are prevented from accessing protection; and,
- attempt to use VBS scripts to activate malicious code.
Bagle’s author monitors the methods antivirus vendors use to block new versions. For instance, antivirus products scanned password protected archives checking if the first file was an exe file. In response, newer versions contained an HTML file with an exploit in the first file position. In this case, the worm’s exe file was second and additional analysis was required to detect it.
At the time of writing, the Kaspersky Virus Lab has detected over 100 variants of Email-Worm.Win32.Bagle along with about the same number of Trojan-Proxy.Win32.Mitglieder. Mitglieder is written using the Bagle source code but does not self-replicate. In other words, the Bagle author is producing new pieces of malware every two days on average.
| The Bagle author is currently producing new pieces of malware on average every 2 days. |
Most Bagle modifications were programmed to cease functioning within a specified time period. It is clear that the author was planning to continue churning out new modifications all along. More importantly, all of the versions delineated above contained code for remote administration of infected machines.
Bagle’s author focused on honing social engineering techniques to fool users into launching infected attachments. At the same time, the worms all contained functionality targeted at avoiding detection by antivirus vendors: blocking security services, masking passwords from infected archives and so forth. In short, Bagle’s author engaged in a long term campaign against antivirus vendors, whilst searching for new machines to infect and control.
However, it turned out that Bagle’s author had plans that went further than waging war against antivirus vendors and infecting hapless users…
The never-ending story: Bagle today
Bagle’s author spent significant time polishing penetration techniques and writing new worms and Trojan-proxies. The result was a large network of zombie machines, obedient to the controller’s every whim. The zombies are controlled using a number of URLs where the Bagle author regularly places updated malicious code. In an attempt to fool both users and virus analysts, a given URL may be left empty/dormant for long periods of time.
Spammer tricks boomerang
On February 15, 2005 Bagle’s author launches a new form of malware: SpamTool.Win32.Small.b. This SpamTool is designed to scan infected machines and harvest all available email addresses. The program then scans the resulting list for email addresses of security software vendors and rejects these – not because the author is afraid, but simply to increase the window of opportunity. The longer security vendors lack a sample, the more time the controller has to infect new machines. Mailing spam to millions of users takes several hours, so every minute counts. In this case, every minute won by the virus writer equals thousands of new zombie machines, which equals more profit.
Kaspersky Lab virus analysts created an email pot with several thousand addresses and used SpamTool.Win32.Small.b to deliver these addresses to Bagle’s author. The response was a flood of new Bagles and more – e.g., spam, phishing letters and even other email worms. What happened? Was Bagle’s author working hand in hand with other cyber criminals? Several scenarios are possible:
- Other members of the cyber underground have access to Bagle-generated mailing lists.
- Other malware harvests our addresses from incoming emails after spam has been purportedly sent from the addresses we had created.
- Bagles’s author is selling mailing lists.
In any case, it is clear that the addresses are being leaked in one way or another by Bagle’s author.
Moreover, the speed with which the large number of addresses was processed and began receiving additional malware indicates that the processes of searching and infecting new machines are likely automated. Virus writers – in this case Bagle’s author – have robots that harvest and implement data automatically to infect new machines and create new botnets.
Testing reaction speed
On March 1, 2005, Bagle’s author evidently decided to test antivirus vendors’ reaction speeds when 15 Bagle-related pieces of malware, worms and Trojan-proxies were released in less than 24 hours.
If we trace how frequently new Bagle-related malware appeared beginning in January 2004, it is evident that the Bagle author is becoming more active (numbers based on Kaspersky Virus Lab data and may vary from figures published by other antivirus vendors).
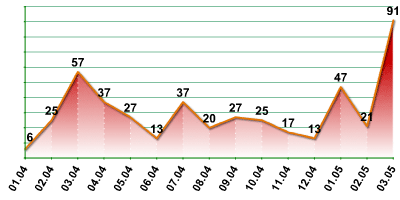
Making a profit
At the time of writing, Bagle’s author had ceased to focus primarily on eluding antivirus vendors. Instead, the focus is now on infecting as many users as possible in order to make a profit in one of the following ways:
- selling botnets for use as DoS or spam platforms;
- selling harvested addresses to spammers and/or phishers; and,
- harvesting confidential data from infected machines – e.g., logins and passwords to online payment and banking systems.
In order to run a successful business, Bagle’s author needs to keep the zombie machines active. The most cost effective technique is regularly updating malware stored on infected URLs.
Most of the latest Bagle-related malware is packed using modified packers, both commercial and underground versions. This indicates that the author is no longer focusing on outwitting antivirus vendors. The goal is maximum profit with minimal effort.
What can we expect in the future?
Bagle’s author will undoubtedly continue to look for easy ways to earn money by preying on hapless users in order to maintain a viable and/or marketable network of botnets. Detailed analysis of the latest versions indicates that the author’s plans are extensive. The code refers to several hundred online payment systems and ebanks. An attempt to earn money from these sources is obviously next on the list.
The degree of automatic processing achieved already proves that Bagle’s author will only continue to write more utilities and robots until the entire system of identifying, infecting and maintaining zombies is fully automated.
User Recommendations
The Kaspersky Virus Lab is monitoring the situation closely. New updates are released in a timely manner and other protective measures have been instituted.
Here are some basic guidelines that will help you protect your machine:
- Update your antivirus database regularly – Kaspersky Lab releases updates hourly.
- Patch your system and applications regularly.
- Never open and/or launch email attachments that you were not expecting, even if they are from friends, or from reputable software vendors. Check whether the email is legitimate first.
In conclusion, Bagle botnets are far from the only botnets on the Internet. Today, surfing without a reputable and updated antivirus solution is an invitation to having your machine infected and turned into a zombie.





















The Bagle botnet