
The TDSS loader, a malicious program that we wrote a lot about (e.g. here and here) now has legs, i.e. a tool for self-propagation. TDSS is a very complicated piece of malware and the cybercriminals have created an ingenious propagation tool for its loader.

The TDSS loader was named Net-Worm.Win32.Rorpian and has two methods of propagation:
- Via removable media
- Via a LAN
When propagating via removable media, the worm creates the files setup.lnk, myporno.avi.lnk, pornmovs.lnk and autorun.inf. These files contain a link to the file rundll32.exe whose parameters reference the worm’s DLL. This is a standard technique used in many malicious programs.
The worm uses the following methodology when working with a LAN. To infect a computer, the worm checks if a DHSP server is used in the network. If the victim computer is located on a network using the DHCP protocol, the worm starts scanning the network to see if there are any available IP addresses. After that, the worm launches its own DHCP server and starts listening to the network. When a DHCP request from a computer in the local network arrives, the worm attempts to respond to it before the “official” DHCP server does, and species the following:
- An IP address from the pool of available IP addresses
- The main gateway specified on the infected computer
- The address of the malicious DNS server belonging to the cybercriminals
After these manipulations, whenever the user tries to visit any web page, they will be redirected to the malicious server and prompted to update their web browser.
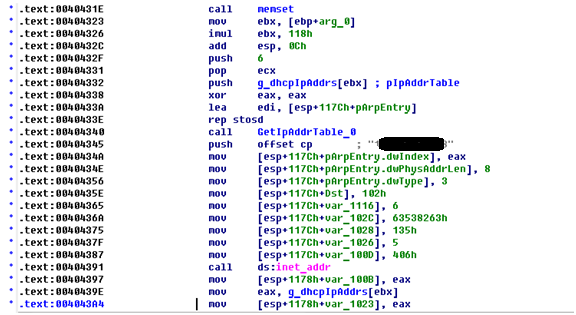
Fragment of Net-Worm.Win32.Rorpian code that works with the DHCP protocol
The user will only be able to visit sites after agreeing to install an “update”. If the user agrees, they unwittingly download a variant of Net-Worm.Win32.Rorpian. After infecting the user’s computer, it changes the DNS settings into a Google server address and lets the user browse.
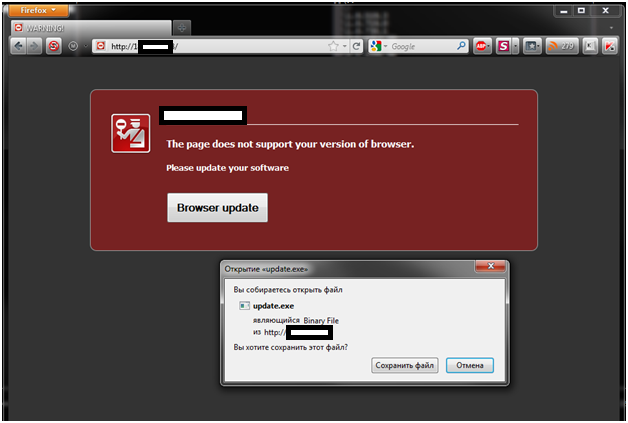
Screenshot of the malicious site from which the worm propagates
Thus the Net-Worm.Win32.Rorpian worm acts as a loader for TDSS, one of the most advanced and sophisticated malicious programs around. The worm leverages the users’ indiscretion – the most dangerous vulnerability of them all.
PS Acknowledgements go to Evgeny Aseev for his help in preparing this article.






















TDSS loader now got “legs”