
We’ve written several times about mobile malware that can send text messages to premium numbers or steal money from online bank accounts. We also know that cybercriminals are constantly looking for new ways of stealing money using mobile Trojans. So our recent discovery of Trojan-SMS.AndroidOS.Waller.a highlighted a new get-rich technique that not only sent a premium SMS but also saw the malware attempt to steal money from a QIWI electronic wallet.
After Trojan-SMS.AndroidOS.Waller.a launches, it contacts its C&C server and awaits further commands.
The cybercriminals’ C&C server is located at playerhome.info. The domain is registered by a French company and the registration data gives a French telephone number, but the email is an account with the Russian company Yandex. The Cloudflare cloud service is used to host the domain.
After receiving the relevant commands, Trojan-SMS.AndroidOS.Waller.a can:
- Check the balance of a mobile phone account by sending an SMS to the mobile network operator; it intercepts the text message sent in response
- Send an SMS to a specified number with a specific text
- Open a web page at a specified address
- Update itself
- Download and install other malicious objects
- Intercept text messages from specified numbers
- Send text messages with specified text to all the entries in the victim’s contact list.
However, as well as the standard Trojan-SMS functions, Waller possesses several other features that mean it can steal from QIWI-Wallets belonging to the owners of infected smartphones. After receiving the relevant command, the Trojan checks the balance of the QIWI electronic wallet. It does this by sending an SMS request to the number 7494. The message sent in response is intercepted by the Trojan and forwarded to its owners.
If the owner of an infected smartphone has a QIWI account and Waller receives information that there is money in the e-wallet, then the Trojan can transfer the money from the user’s account to the QIWI account of the cybercriminals. To do this a command is given to the Trojan to send an SMS to the number 7494 that includes the wallet number of the criminals and the sum to be transferred. Up to 15,000 rubles (approximately $430) can be transferred per day.
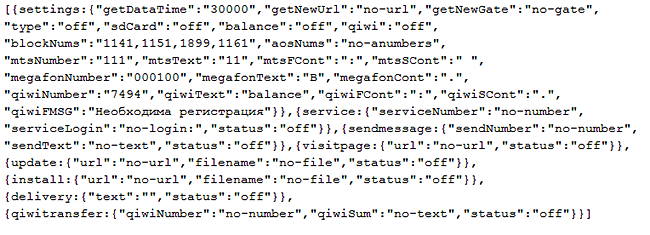
Below is a sample answer from a C&C server with commands to check the balance of a phone account, the balance of a QIWI Wallet and to delete incoming text messages from the premium numbers 1141, 1151, 1899, and 1161:
Using electronic wallets makes it possible for cybercriminals to steal money from people in countries where premium-rate numbers don’t work. Electronic wallets that can be managed via SMS are available in lots of countries. According to Wikipedia, the QIWI service is on the market in seven other countries apart from Russia (Romania, Brazil, Kazakhstan, Belarus, Moldova, Jordan and the USA) and there are franchises in 15 other countries.
The Trojan spreads from the cybercriminal sites in the guise of applications such as “universal android firmware”, “media player classic for android”, “change your voice on android”. Waller also spreads via SMS spam. The Trojan is still not very widespread, but cybercriminals are increasingly using it to try and infect mobile devices.
To reduce the risk of infection by mobile malware we recommend that users:
- Do not activate the “developer mode” on the device
- Do not activate the “Install applications from third-party sources” option
- Only install applications from official channels (Google Play, Amazon Store, etc.)
- When installing new apps, carefully study which rights they request
- If the requested rights do not correspond with the app’s intended functions (e.g., a game requests rights to send text messages), do not install the app
- Use protection software























Stealing from Wallets