
October in figures
- The amount of spam in email traffic fell by 3.7 percentage points compared to September’s figure and averaged 77.4%.
- Phishing emails accounted for 0.87% of all mail traffic.
- Malicious files were found in 1.47% of all emails, a decrease of 2.86 percentage points compared with the previous month.
- In October, there were lots of emails containing links that exploited the Halloween theme.
Spam in the spotlight
Legislation in action
A few words about the ZeuS case
As we wrote in last month’s report, at the end of September law enforcement agencies arrested a number of members from the criminal group behind ZeuS. This caused a considerable drop in detections of this malicious program in the USA and the UK on the day of the arrests – 30 September. According to Kaspersky Security Network, in October the lull in ZeuS distribution in the USA only lasted a couple of weeks, while in the UK the malicious program was detected no more than 10 times a day throughout the whole month (see the diagram below):

Detection levels for Trojan-Spy.Win32.Zbot and Trojan-Dropper.Win32.Zbot
in the USA and the UK in September and October 2010
The graph shows the frequency with which ZeuS ended up in users’ email inboxes in the USA and the UK before September 30 – the intervals between mailings did not exceed four days. After the ZeuS-related arrests the number of ZeuS detections in the UK did not revert to its previous level, whereas in the USA the interval between mailings lasted nearly two weeks.
This suggests that the legal measures were not in vain: in order to protect users from spam and malware it is necessary to combine the efforts of companies involved in IT security with those of governments and law enforcement agencies from different countries.
About Bredolab
A blow to zombie networks
Just like in September, the most noteworthy events took place at the end of the month. The Dutch law enforcement authorities launched a series of raids against botnets that included Bredolab-infected computers. A total of 143 command centers were neutralized and one arrest made. George Avanesov, a 27-year-old Russian citizen, was earlier put on Interpol’s wanted list by the Dutch authorities and arrested on 26 October at Yerevan airport.
And what is Bredolab?
Backdoor.Win32.Bredolab first appeared in the summer of 2009. It immediately attracted the attention of virus and spam analysts and since that time our anti-spam lab has received messages that contain links to compromised legitimate sites. The analysis of one of this messages resulted in the article The Cash Factory by Sergey Golovanov and Igor Sumenkov published in September 2009. The article provides a detailed analysis of the scheme used by fraudsters to distribute Bredolab and earn money. The prime method for distributing malware at that time was drive-by downloads from infected sites. However, in August 2009 cybercriminals also started using another trick to distribute this malicious program – via email attachments. At the time, Backdoor.Win32.Bredolab variations accounted for more than 30% of all malicious attachments.
The Bredolab botnet is mostly used for sending spam, carrying out DDoS attacks, data theft and spreading other malicious programs. Interestingly, in the summer of 2009 Bredolab received a command to download the spam bots Rustock (Backdoor.Win32.HareBot) and Pushdo (Backdoor.Win32.NewRest.aq). Later the Pushdo spam botnet became the main distributor of Backdoor.Win32.Bredolab.
Bredolab and spam traffic
Of course, the closure of a major zombie net command center will be reflected in both the quantity of spam and its categories. Unfortunately, the consequences of such attacks on cybercriminals do not have a long-term effect. We need look no further than McColo’s ignominious demise and the considerable decrease in the volume of spam it caused…but that drop was very short-lived. In the case of Bredolab, we didn’t expect any considerable reduction, and definitely not a long-term one. And that was basically what happened:

Spam in October 2010
As can be seen from the graph, the lowest spam levels were recorded in mail traffic in the period from 26 to 29 October. The share of spam for those days barely exceeded 70%, a decrease of 8-9 percentage points compared to the usual figures. However, by 31 October the level of spam was approaching the more familiar level of 80% of email traffic.
Over the last few months the level of spam has actually declined slightly. For example, up to 26 October the amount of spam averaged 78.7%, a decrease of 2.4 percentage points compared to the previous month.
Now a few words about the shifts in spam categories. The most important change caused by the closure of the zombie network command centers was a short-time decrease in the quantity of spam that contained malicious attachments.

Spam mailings containing malicious attachments in October 2010
The graph shows that the most active malware distribution occurred at the beginning of the month. Over 30% of the malicious files found in October’s emails appeared on 1-6 October. This period is marked red in the graph. The thin line in the graph marks the anomaly of this period: generally malware distribution is less intense at weekends, but Saturday, 2 October, saw it peak for the month.
The purple arrows in the graph indicate weekends.
The light blue arrow points to the decrease in the distribution of spam with malicious attachments on 28 October, the day after the Bredolab command centers were shut down.
The botnets were used most often for distributing pharmaceutical spam, so after the closure of the zombie network command centers there was a decrease in the amount of this type of spam. However, October saw other events that affected the quantity of pharmaceutical spam on the Internet.
SpamIt, Glavmed… Who’s next?
As we wrote in last month’s spam report the level of pharmaceutical spam was affected by the closure of the Spamlt partner program on 1 October. The end of the month witnessed yet another important event affecting this particular category of spam – on 26 October Moscow law enforcement agencies launched a criminal case against Igor Gusev, CEO of Despmedia, who is believed to be behind the GlavMed partner program.
Besides the quantitative changes in spam traffic which occurred simultaneously with Gusev’s arrest, and the more significant Bredolab closure, there were also qualitative changes. The graph below shows the changes in the share of messages belonging to different spam categories that were distributed in cooperation with partner programs.
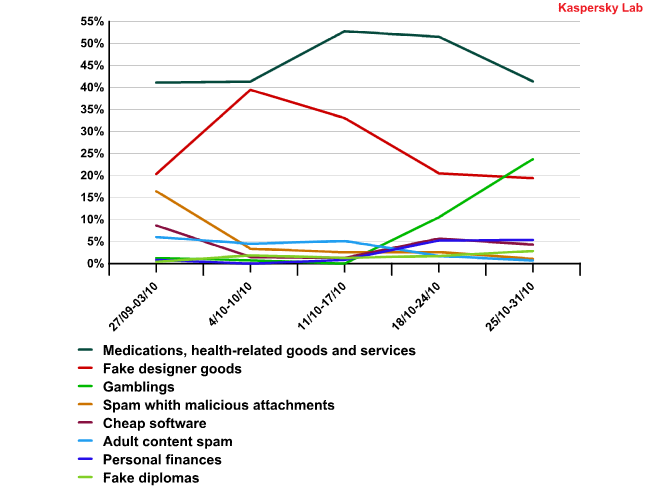
Shifts in partner spam in October 2010
One of the most obvious changes was the fall in pharmaceutical compared to the previous month. At the same time, in the middle of October the amount of this type of spam began to grow again in some locations. The spammers seemed to come to their senses after Spamlt’s closure and decided to start distributing Viagra spam again, but the fuss surrounding the Igor Gusev incident a few days later seems to have put them off.
As can be seen from the graph, the decrease in the volume of malicious spam started at the beginning of October. At the end of the month it reached its lowest point for the last quarter.
Having lost part of their income from pharmaceutical and malicious spam, the spammers sought out other opportunities to make money. The share of spam messages containing adverts for fake designer goods increased at the beginning of the month while the second half of October saw a growth in spam advertising online casinos. Adult content spam reached the 4-5% mark, which suggests that there are both distributors and buyers out there for “sexy” mass mailings.
The Matthew Anderson affair
Meanwhile, in the UK the investigation into Scotsman Matthew Anderson’s case is proceeding swiftly by help from Finnish police. Sentencing looks likely to be passed in late November, but a guilty verdict is not in doubt after Anderson partially admitted his guilt.
Anderson is considered a key player in the cybercriminal gang m00p, which spread malicious spam in order to steal people’s credentials and personal data. Anderson also followed his victims via their web cameras. The victims were primarily ordinary users and organizations based in the UK.
Compensation for Facebook
Canadian law enforcement agencies took an interest in spam distributed on social networks, or to be exact, one social network in particular – Facebook. This popular Internet community was used by Adam Guerbuez of Montreal to send spam. He has since been ordered to pay compensation.
The sum that Guerbuez has to pay the social networking site was set at more than one billion Canadian dollars. Within the space of just two months he managed to send nearly 4.5 million spam messages to Facebook users.
It’s no wonder that the Facebook owners were far from pleased – instead of sending legitimate messages their servers were working overtime for the spammer, who no doubt irritated a lot of Facebook users.
Harry Potter: targeting users
On 17 November 2010 the long-awaited Harry Porter sequel was released. The release of part 6 in June 2009 went more or less unnoticed by the spammers. After all, Michael Jackson’s death was more sensational news, but this time there are no distractions.
The first messages exploiting the release began to appear in early October.

Spam featuring the premiere of Harry Potter and the Deathly Hallows
Spammers offered users free tickets to the premiere. In order to be among the lucky winners, users were asked to click on the “Submit” button and enter their email address along with other personal data.
Of course, there were no tickets to be won – miracles only happen in the movies. Daniel Radcliffe’s portrait was actually being used to advertise a special offer from a deluxe hotel.
Statistical summary
Spam in mail traffic
The amount of spam detected in mail traffic decreased by 3.7 percentage points and averaged 77.4% in October 2010. A low of 70.1% was recorded on 28 October with a peak of 88.2% on 24 October.
Sources of spam
In October the top 20 most popular sources of spam looked like this:

Sources of spam in October 2010
In October, major shifts occurred in the list of top 20 sources of spam. First of all, Russia took the lead as the most popular source of spam having distributed twice as much compared to September’s figures. The share of spam spread from the territory of Ukraine also doubled while the amount of spam originated from the USA decreased by a factor of three. For the first time over a very long period the USA could not be found even in the top 10 most popular spam distributors: it ended up back in 18th place.
These shifts were caused by the changes in the spammer infrastructure around the world: the closure of the Pushdo/Cutwail and Bredolab botnet command centers undoubtedly affected the sources of spam traffic. The decrease in the quantity of spam originating from the USA was already noticeable in September. In October this trend became even stronger, although by the end of the month the amount of spam coming from the USA had increased compared to the beginning of October. It looks like spam traffic distributed from the USA was getting back to normal after intervention by law enforcement agencies in various countries.
In October, the amount of spam coming from Europe decreased slightly. However, the share of spam from Western Europe – Germany, France, Portugal, the Netherlands, Ireland and the UK – was considerably less than in September.
Portugal, the Netherlands and Ireland dropped out of the rating having distributed less than 1.5% of all spam. For the first time Bulgaria made it into the rating going straight in at 11th place.
Besides Bulgaria the rating also saw the arrival of Israel (2%) and Indonesia which in the previous two months distributed less than 1.5% of all spam.
Malware in mail traffic
In October, the USA maintained its leadership as the country where malware was detected most frequently in mail traffic, though the share of malicious attachments dropped below 10%. Germany, which came 5th in September, moved up to 2nd place in the rating with an increase of more than 2 percentage points compared with the previous month. The amount of malicious attachments detected in UK mail traffic barely changed.
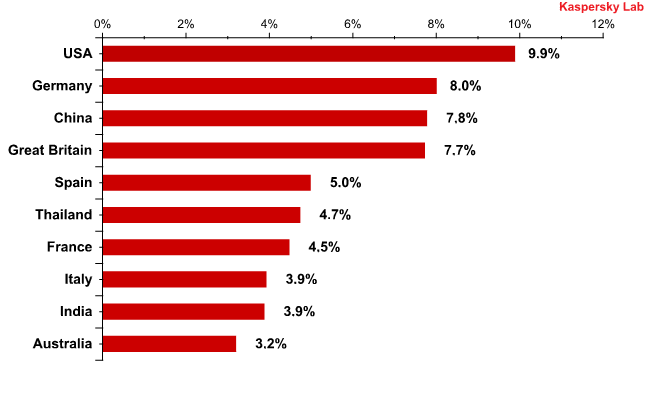
Countries where mail antivirus detected malware most frequently in October 2010
Malicious files were found in 1.47% of all emails, a decrease of 2.86 percentage points compared with the previous month.

The Top 10 malicious programs distributed via mail traffic in October 2010
In October, Trojan-Spy.HTML.Fraud.gen regained top spot in the Top 10 malicious programs distributed via mail traffic. This Trojan program uses spoofing technology and appears in the form of an HTML page. This malicious program comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password.
The programs from the FraudLoad family (one of its variations claimed first place in September’s malicious Top 10) are still being distributed via email attachments. In October, the total share of Trojan-Downloader.Win32.FraudLoad.hby and Trojan-Downloader.Win32.FraudLoad.xgfm accounted for 5.5% of all the malware found in mail traffic. The programs from the FraudLoad family download a rogue antivirus program that is designed to extort money from the users of victim computers.
The programs from the Oficla family are still being actively distributed via email. These programs download other malicious programs and adware, or updates for them, from the Internet and launch them on the victim computer.
In conclusion, 10% of all malicious programs found in mail traffic were new threats and were detected by Kaspersky Anti-Virus proactively.
Phishing
Phishing emails accounted for 0.87% of all mail traffic.
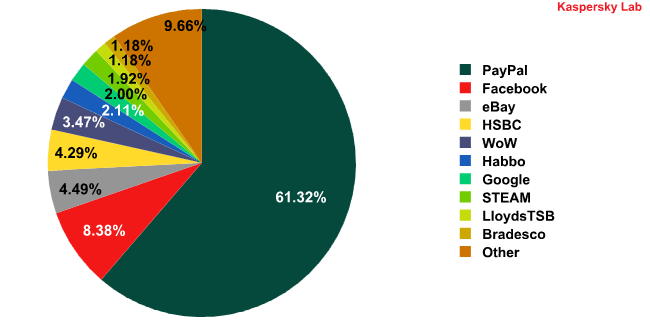
Top 10 organizations targeted by phishing attacks in October 2010
In October, PayPal had the unenviable distinction of being targeted most by the phishers once again. The share of attacks on this e-pay system increased by 1.5 percentage points compared to the previous month’s figures.
As expected, the fraudsters’ interest in Facebook, which seemed to tail off in September, came back with renewed force in October. Last month we forecasted that Facebook would replace HSBC in third place. However, phishers went even further and Facebook ended up taking over from eBay in 2nd place. The total share of attacks on Facebook doubled compared to September and rose fourfold against August’s figure.
The other three members of the Top 5 remained the same – eBay, HSBC and Blizzards, the World of Warcraft developer. The only serious change was the amount of attacks on eBay: it fell by half compared to September’s figures.
Conclusion
High-profile events continue to shake the spammer community. Law enforcement agencies have actively intervened in the work of zombie networks and partner programs which has resulted in a reduction in the amount of spam. In October, it decreased by 1.5-2 percentage points. After the closure of the Bredolab command centers there was even less spam appearing in users’ inboxes.
Operations by law enforcement agencies also affected the various spam categories. There was a decrease in the amount of pharmaceutical and malicious spam, though this caused other changes, with advertising for porn and online casino regaining their niche in spam traffic. When one partner program closes, the spammers immediately find other ways to make money.
Importantly, porn and online casino spam is as dangerous as malicious spam. Adult content and gaming sites often hide malicious programs that download to a victim computer while an unwary user is watching pornography or gambling.
The changes brought about by the closure of botnet command centers also affected the sources of spam. The share of spam originating from the USA decreased by a factor of three while the amount of spam distributed from the territory of Russia and Ukraine doubled.
It’s difficult to make forecasts in these circumstances. However, even now it is possible to talk about the amount of spam in mail traffic returning to the 79-80% level in November, though these figures are still lower than those seen in the first and second quarters of 2010.
As for the spam categories, those spammers who have given up pharmaceutical and malicious spam distribution and failed to find another partner program will most likely turn to a Christmas theme. The amount of adult content and online casino spam also looks set to grow.






















Spam report: October 2010