
Recent trends
- The amount of spam in email traffic decreased by 0.3 percentage points compared to May’s figure and averaged 84.8%.
- The number of links to phishing sites remained unchanged compared to the previous months.
- Malicious files were found in 2.68% of all emails, an increase of 0.99 percentage points compared with the previous month.
- Spammers exploited the World Cup theme.
Spam in mail traffic
The amount of spam detected in mail traffic averaged 84.8% in June 2010. A low of 80% was recorded on 4 June with a peak value of 89% being reached on 27 June.
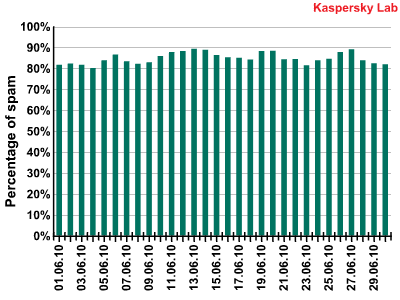
Spam in mail traffic in June 2010
Sources of spam
June saw major shifts in the rating of the most popular sources of spam: though the USA and India maintained their leading positions as the prime distributors of spam, three new members entered the Top 5 – Brazil, Columbia and Spain. In general, Spanish- and Portuguese-speaking countries are widely represented in the Top 20 with Mexico, Argentina, Portugal, Morocco and Chile among them.
Russia dropped from third to sixth position with 3.6% of spam distributed from its territory, a decrease of 1.8 percentage points compared to May.
Europe took the lead as the main spam distributor by region: almost 40% of the total volume of spam originated from this part of the world.
The amount of spam distributed from the UK increased slightly in June compared to the previous month, accounting for 2. 8%.
Phishing
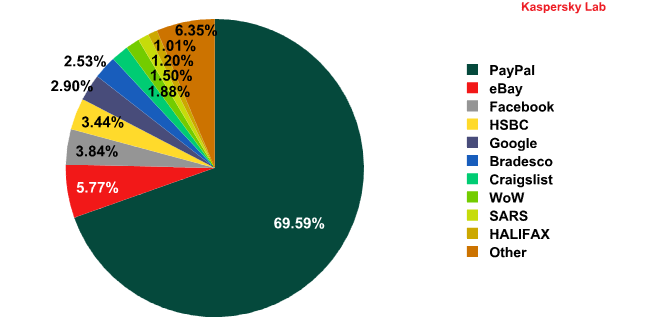
Organizations targeted by phishing attacks in June 2010
There were no changes in the Top 6 most popular targets for phishers. PayPal is the unsurpassed leader: in June the number of attacks on this e-pay system increased by 20 percentage points compared to May’s figure. The share of the other Top 6 members decreased. Facebook and HSBC swapped positions again to become third and fourth place respectively.
Notably, World of Warcraft appeared in the Top 10 in June. This popular online game has been mentioned more than once in our spam reports as an attractive target for phishers.
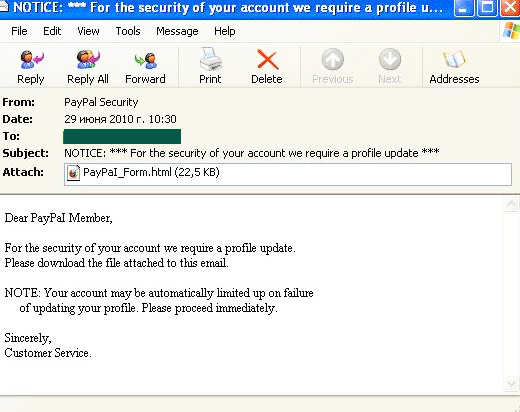
In June, PayPal users fell victim to an attack in which spammers tried their old trick of informing a user that their account has been blocked and in order to enable it again, a user must open the attachment and enter their login and password. The attachment contained a phishing HTML page.
Malware in mail traffic
In June, the Top 10 list of countries from which malware was distributed via email looked like this:
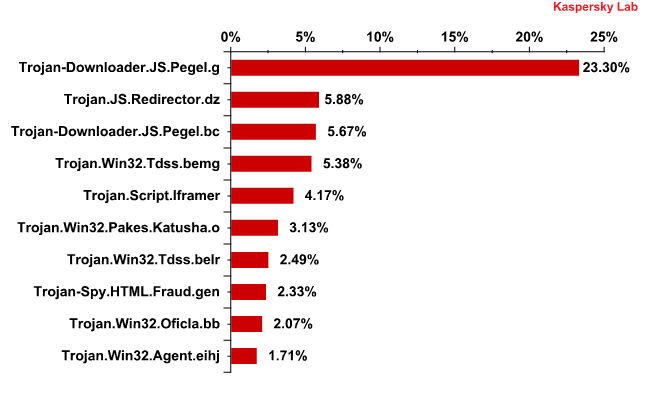
This month’s undoubted leader is the Pegel family of malicious programs, from which Trojan-Downloader.JS.Pegel.g and Trojan-Downloader.JS.Pegel.bc came first and third in the rating with over 30% of all malicious attachments found in mail traffic. The programs belonging to this family are just HTML pages containing JavaScript. After opening an infected page in the browser, the Trojan starts decrypting its code and executing it. At the same time, a user is redirected to a website infected with exploits from which other malicious programs can be downloaded to the computer using vulnerabilities in its browser.
Second position is occupied by a malicious program consisting of an HTML page containing JavaScript – Trojan.JS.Redirector.dz. Considering the fact that the fifth position is taken by Trojan.Script.Iframer and the eighth by long term Top 10 resident Trojan-Spy.HTMLFraud.gen, an interesting feature emerges: at present, 40% of the Top 10 malicious programs distributed via email work on platforms other than Win 32.
Interestingly, Pegel, Redirector and Trojan.Script.Iframer were distributed in very different emails – from fake notifications purportedly sent by social network sites, to standard messages with laconic text such as ‘see my photos’. Common to all of these bulk emails were HTML attachments or links to an HTML page.
More details about such bulk emails will be provided in the spam report for Q2, 2010.
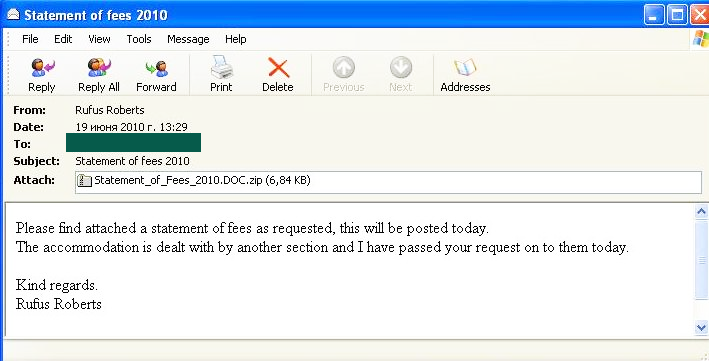
Variants of one of the most dangerous rootkits currently in circulation, Trojan.Win32.TDSS, were also actively distributed via email in June, taking fourth and seventh places in the Top10. Variants of this program could be found in different links, however, always in the form of an attachment packed in a zipped archive. In order to distribute them, fraudsters used one of their favorite themes – taxes. In the email below spammers tried to mask the .exe extension of the archived file with the extension .doc.
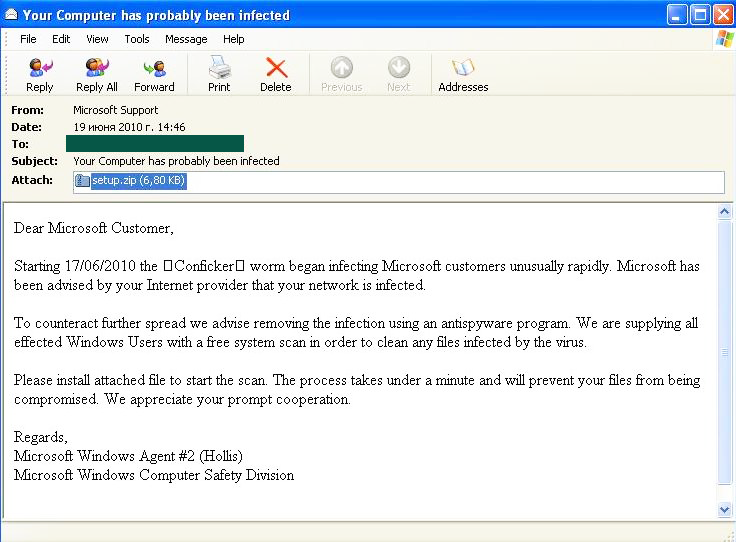
In another bulk email which distributed a representative of the Trojan.Win32.TDSS family, fraudsters used a very popular trick – a fake notification about the possible infection of a recipient’s computer with Conficker. In order to treat this infection a user was instructed to download the setup.exe program attached to the message. Of course this program treated nothing at all.
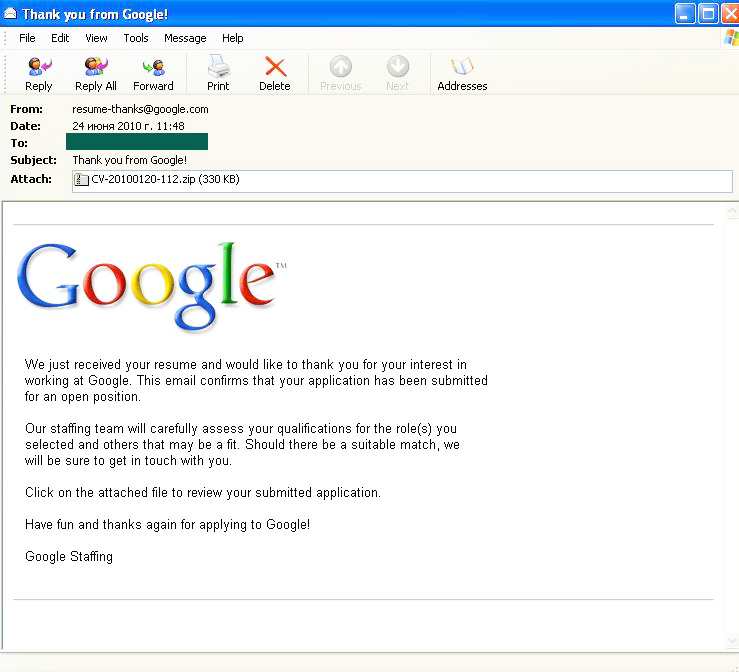
Another malicious program, Trojan.Win32.VBKrypt.cpz, which didn’t make it into June’s Top 10, was distributed in emails which allegedly originated from Google and thanked a user for sending their CV.
The list of countries from which users most often received malicious programs distributed via email saw several changes compared to May:
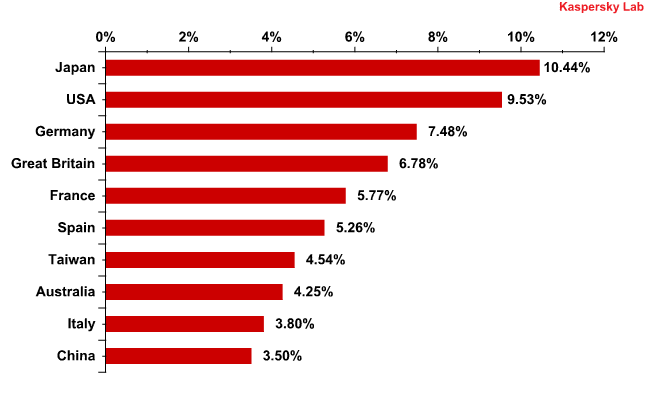
Most popular sources of malware in mail traffic
Last month’s leaders, Germany and the UK, dropped two places, leaving Japan and the USA to fill their positions. However, only in the case of Japan did the quantity of malware received by users increase considerably, doubling in comparison to May’s figure. Interestingly, India dropped out of the Top 10, being replaced by China with 3.5% of all emails with malicious attachments.
Spam by category
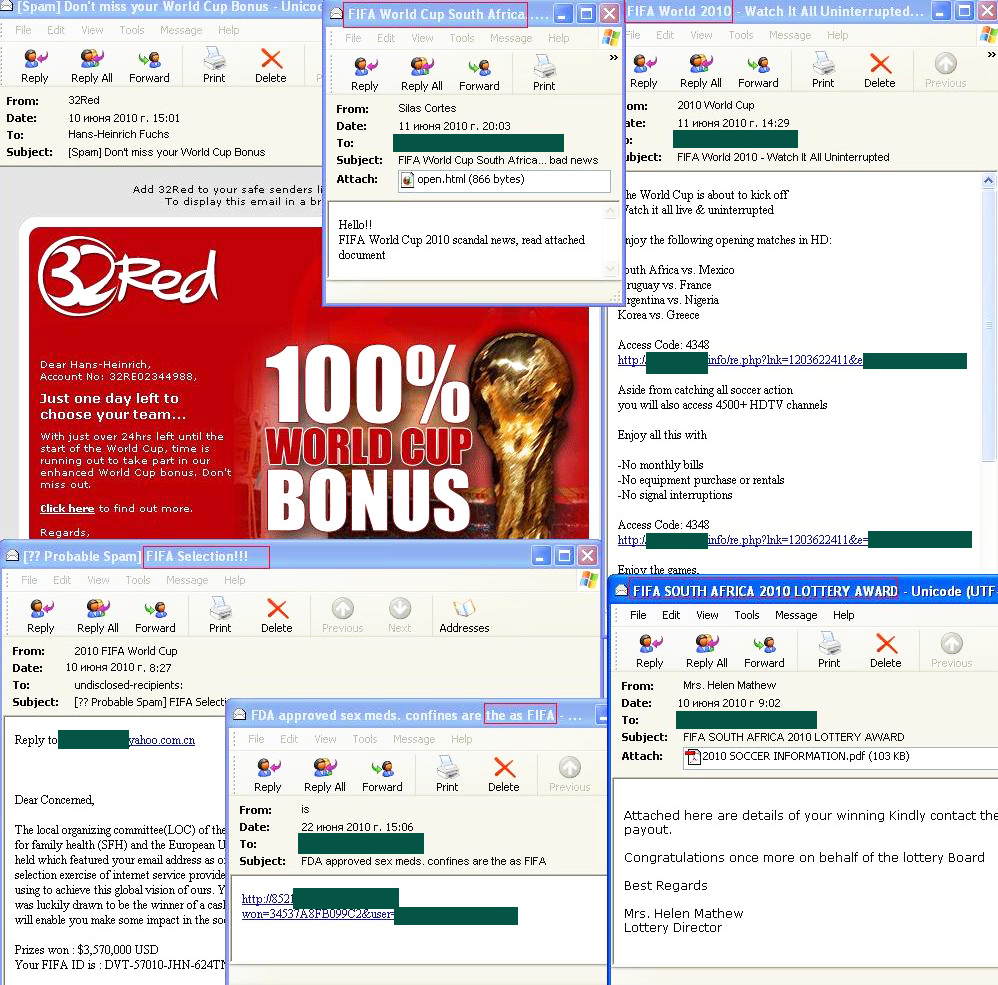
The Medications and Health-Related Goods and Services category retained the lead for English-language spam. In June, this category’s share averaged 35%. Emails advertising Viagra imitated notifications from different social networks. They were also distributed with the header ‘Medications for men approved by FIFA’ or ‘World Cup. Bad news’.
The Computer Fraud category came second in the rating with 25% of all spam messages. The emails from this category also exploited the World Cup theme. For example, it was used in the majority of Nigerian letters which lie at the core of this category. This theme was beneficial for spammers who distributed offers to users encouraging them to try their luck in an online casino or by betting on football results.
June also saw amusing emails offering the recipients a chance to have a look at the ash from the volcano that disrupted European air traffic for several weeks:
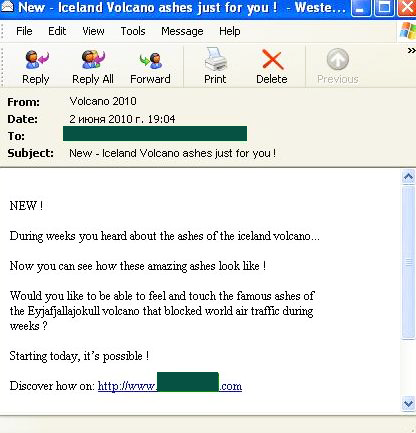
The link in the email led to a website from which a user could buy a small bottle filled with grey sand and a certificate confirming that the grey material was genuine ash from the volcano with the unpronounceable name.
Conclusion
In June, the amount of spam decreased slightly compared to the previous month.
Brazil reentered the Top 10 prime distributors of spam.
Phishing emails mostly targeted the users of PayPal.
The share of emails containing malicious files increased by 0.5 percentage points. For the first time in the history of the Top 10 most popular malicious programs distributed via email, 40% were not designed to work on the Win32 platform. The majority of malware in June’s Top 10 consisted of HTML pages containing JavaScript. That is why they were most often distributed as HTML attachments to emails. It’s not easy to make a long term forecast, but there is a good chance that in the nearest future distribution of such bulk emails will continue.
The World Cup theme was actively exploited by spammers worldwide.



















Spam report: June 2010