
December in figures
- The amount of spam in email traffic increased by 0.3 percentage points compared to November and averaged 77.1%.
- Phishing emails accounted for 0.14% of all mail traffic, a decrease of 0.26 percentage points compared to the previous month.
- Malicious files were found in 1.75% of all emails, an increase of 0.15 percentage points compared to November’s figure.
Spam in the spotlight
Russian spammer on trial
The legal war on botnets was once again thrust into the public limelight in December with criminal proceedings being instigated in Wisconsin (USA) in the case of Russian citizen Oleg Nikolaenko who is suspected of creating and utilizing the Mega-D zombie network, also known as Ozdok.
The botnet
The Mega-D/Ozdok botnet, which is believed to have been created by Oleg Nikolaenko, was until recently among the biggest botnets distributing spam. According to some estimates, at its peak the network numbered half a million infected computers. Experts claim that at certain times the network’s zombies could distribute up to 30-35% of all spam. The fight against this monster started in 2008, but it was only a year later in November 2009 that any results were achieved when numerous command centers were closed down. This only led to a temporary drop in the network’s capacity – by the beginning of December 2009 the botnet was back up and running at full capacity.
The botnet’s infected machines were used to distribute partner spam containing adverts for medications and fake designer goods.
Betrayed
When the Mega-D/Ozdok command centers were shut down in November 2009, Muscovite Oleg Nikolaenko was already the FBI’s prime suspect. They received information about him from one of his “associates” Jody Smith who in the summer of 2009 was himself under investigation. In August of the same year he began assisting law enforcement agencies.
Nikolaenko, however, was only arrested a year later in November 2010 during a visit to an auto show in Las Vegas.
Court proceedings
Nikolaenko is charged with violating US anti-spam laws (CAN-SPAM Act of 2003) and if found guilty, could face up to three years in prison or a fine of $25 000.
Nikolaenko denies any wrongdoing. His attorney tried to free him on bail, but the request was denied because the court had reason to believe the defendant would attempt to leave the country. The court’s decision is still pending. The next hearing is scheduled for February 2011.
Meanwhile, as Nikolaenko sits in prison, the volume of spam distributed via Mega-D, according to some experts, constitutes no more than 5% of all spam traffic.
In particular, the case of Oleg Nikolaenko demonstrates the shortcomings of Russia’s spam laws: it took a trip to the USA for an alleged major player in the spam business to finally face the prospect of prosecution.
WikiLeaks
Making sure the leaks spread
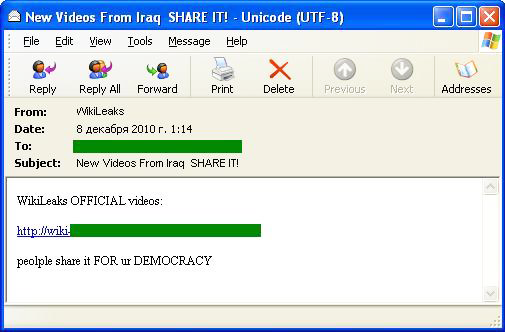
Recently, the WikiLeaks portal specializing in the publication of data leaks from government organizations of different countries has unsurprisingly become engulfed in a major international scandal. The portal has published thousands of confidential documents of a very sensitive nature for the world’s politicians. Naturally, WikiLeaks has its supporters and opponents. The former started actively spreading some major leaks in December.
They tried to publish links and extracts from WikiLeaks wherever they could. Spam was also utilized. In December, users received emails containing links and requests to pass them on in the name of democracy:
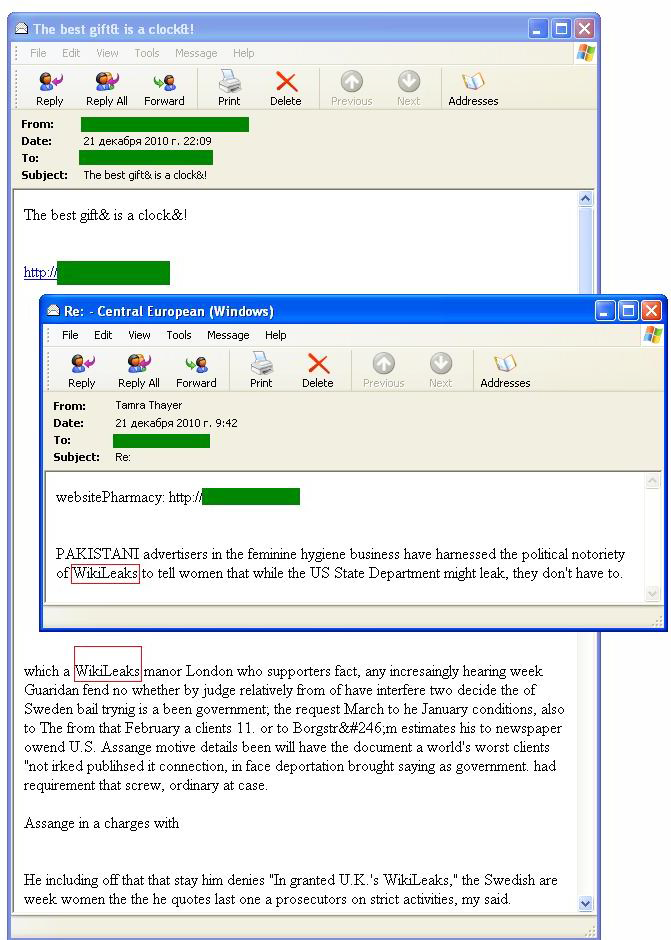
In addition to these messages we also came across snippets of compromising texts. However, there is no way of knowing how reliable these sources are: this could be spam distributed by supporters of WikiLeaks or false information from opponents.
WikiLeaks – the month’s hot topic
Surprisingly, the WikiLeaks issue was so popular in December that even the Christmas and New Year holiday season failed to live up to its usual popularity among spammers.
It is usual for spammers to exploit the current hot topic to grab the attention of their recipients. The types of issues or events can vary – the antics of celebrities to wars, elections or various holidays. In December the most popular topic is usually the holiday season. In December 2010 WikiLeaks kept Christmas and New Year company in the spammer popularity stakes.
Spammers mentioned the WikiLeaks name in background noise texts used to bypass spam filters. They were mostly quotes from material published on the site, or news about the portal itself. Interestingly, the word WikiLeaks was often inserted in links in another bid to evade the filters.
It remains to be seen whether the people distributing pharmaceutical spam are supporters or opponents of WikiLeaks; we only know that they have exploited the attention given to the leaks for their own purposes.
Statistical summary
Spam in mail traffic
The amount of spam detected in mail traffic increased by 0.3 percentage points and averaged 77.1% in December 2010. A low of 72% was recorded on 6 December with a peak of 85.2% on 12 December.
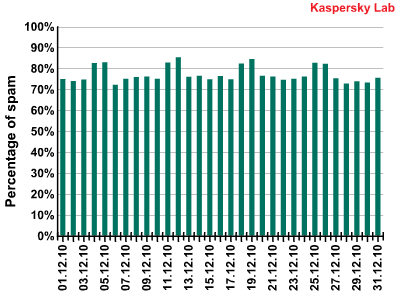
Spam in mail traffic in December 2010
Sources of spam
In December, India remained the single-most popular source for spam, accounting for 9.89% of the total volume of spam (-0.55%).
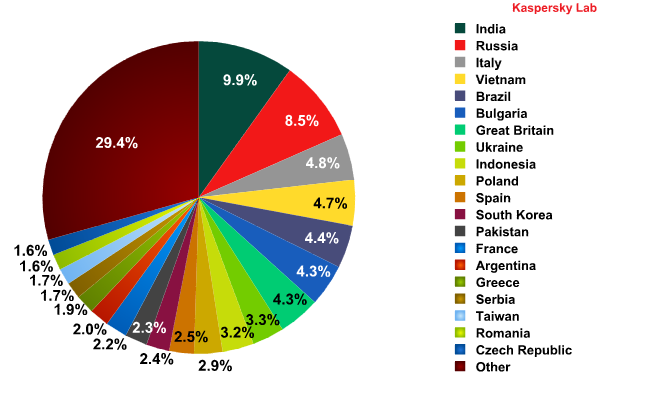
Sources of spam in December 2010
The most noticeable shift in the Top 20 most popular spam distributors affected Russia and Vietnam, which came second and fourth respectively in November. In December, they swapped the places: the amount of spam distributed from the territory of Russia increased by 2.9 percentage points while Vietnam’s contribution dropped by 4.11 percentage points.
Tellingly, three out of December’s Top 5 spam distributors – India, Russia and Vietnam – were among the Top 10 countries where mail antivirus detected malware most frequently in November, suggesting the cybercriminals who sent malware to those countries in November made use of infected computers for distributing spam in December.
There was also a drop in the volume of spam originating from the UK, France and Germany.
Malware in mail traffic
In December, malicious files were found in 1.75% of all emails, an increase of 0.15 percentage points compared with the previous month.
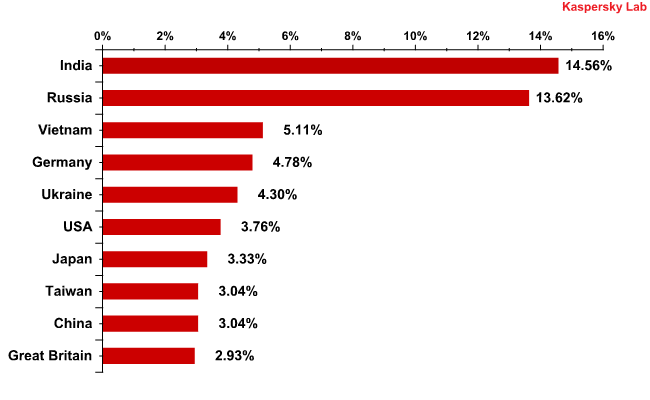
Countries where mail antivirus detected malware most frequently in December 2010
Like the previous month, most malware was detected in mail traffic received by users in India, Russia and Vietnam. European countries and the USA, which had been among the leaders of this rating for the last few months, fell to the lower end of December’s Top 10. The UK, which until October had been among the top three, fell to tenth place, accounting for less than 3% of all malware detected in email traffic. At the same time, cybercriminals sent quite a lot of malicious messages to Ukraine.
It is possible that such a shift is part of the initiative to transfer botnets from the West – where anti-botnet activity is threatening business – to the East where the legal pressure is not as severe.
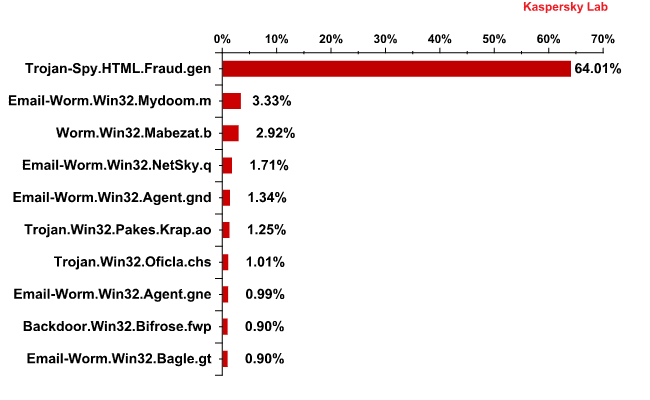
The Top 10 malicious programs distributed via mail traffic in December 2010
In December, Trojan-Spy.HTMLFraud.gen maintained its leading position in the list of Top 10 malicious programs distributed via mail traffic. This malicious program has been a long term Top 10 resident. It is designed to trick users into giving away confidential or financial data. This particular Trojan uses spoofing technology and appears in the form of an HTML page resembling the site of a well-known bank or e-pay system where the user is asked to enter a login and a password. This malicious program was particularly popular in December as the end of the year is always a time of increased spending in the run-up to the holiday season. At that time of year the average user has money in his online accounts and is busy Christmas shopping, making him an easy target for fraudsters of every type.
The majority of the other entries also make regular appearances in this Top 10 throughout the year.
Email-Worm.Win32.Mydoom.m was a permanent fixture in this Top 10 throughout 2010. This is a typical mail worm which scans the system searching for email addresses that can be used to send a copy of itself in the form of a message containing a fake email system notification about a delivery failure. In this case the main function of the program is the harvesting of email addresses. This worm’s signature was added to Kaspersky Lab’s antivirus databases in 2004. To read more about this malicious program click here.
Email-Worm.Win32.NetSky.q is also a regular in the Top 10. In all, five out of the ten most popular malicious programs distributed via mail traffic are mail worms. As the names suggest, Email-Worm.Win32.Agent.gnd and Email-Worm.Win32.Agent.gne also belong to this family. However, their functionality is more sophisticated compared to the aforementioned worms. They not only collect email addresses and distribute themselves via mail traffic but install other malicious programs once they penetrate a victim computer. These malicious programs are mostly Trojan downloaders which immediately try to gain access to Internet resources in order to download other malware.
Spam by category
In December, the popularity of spam categories followed the trends set in autumn.
Viagra’s banishment continued: the share of pharmaceutical spam decreased by 0.8 percentage points compared with the previous month and averaged 28.6%. The amount of spam distributed in the other categories was affected by spammers abandoning pharmaceutical spam and by the law enforcement activity surrounding botnets sending this type of spam.
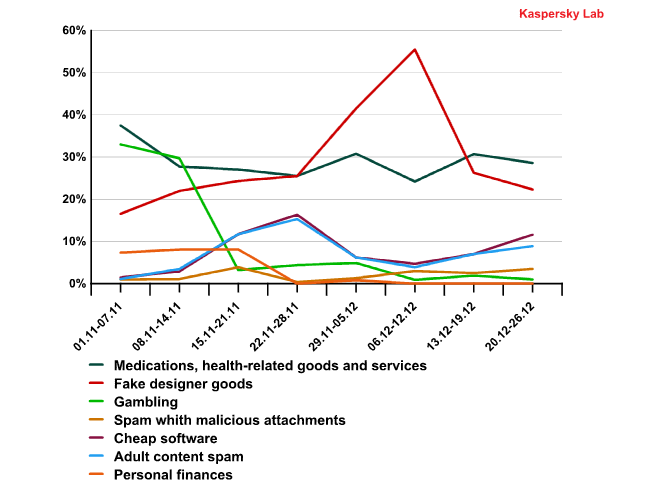
Spam by category in November-December 2010
The peak in the graph above reflects the popularity of a partner program offering fake designer goods. The spammers obviously decided that replicas of expensive watches and bags were a good idea for Christmas presents.
The festive season theme was actively exploited by the spammers. In the first week of December the share of emails that mentioned Christmas and New Year exceeded 6% and continued to grow. Holiday season spam averaged 20-25% of the total quantity of spam in December.
Conclusion
In conclusion, we would like once again to mention the results of the successful anti-botnet campaign in the West. The volume of spam distributed from the territory of the USA has not returned to former levels in spite of concerns by experts that it would be a temporary dip. The amount of spam originating from the UK, France and Germany has also started to drop. Meanwhile, the processes taking place in Eastern Europe and Asia are worthy of special mention. The countries of these regions are increasingly being targeted by malicious spam. It appears the cybercriminals are trying to transfer their zombie networks to those regions where law enforcement is either less successful or non-existent.
The interest in counterfeit medications on the part of Western law enforcement agencies as well as the Igor Gusev‘s case initiated in Russia clearly affected the various spam categories: spammers are still searching for a partner program that is as profitable as pharmaceutical spam used to be. The fact that spammers are actively advertising their own services demonstrates that those who have decided to start advertising for small and medium-sized businesses are still looking for clients.
The situation is unlikely to stabilize in January. Spam will continue to be redistributed among the various spam categories. The first month of the year is usually marked by a downturn in consumer spending and no single partner program will be capable of meeting the financial demands of the spammers following the demise of pharmaceutical spam. They will now have to search for a more effective area of activity and modify their tactics.






















Spam report: December 2010