
Spam in the spotlight
After the September cold snap we recorded a lot of mass mailings about offers to cut heating bills and keep homes warm. They often appeared in both Russian and English-language spam. A large proportion of September mass mailings offered auto insurance services and adverts for printing services, particularly calendars for 2014. Festive spam in September was mainly in English and was dedicated to Halloween.
Halloween spam
Every year in the run-up to Halloween we register a large number of spam mailings related to this popular holiday. As always, English-language spam advertises carnival costumes while the familiar mass mailings offering fake brand-name handbags enticing recipients with Halloween pumpkins and promises of supernatural discounts. Small and medium-sized businesses enthusiastically joined the holiday campaign with spooky-themed spam emails advertising their goods. Of course, the name of the holiday was used in the Subject field of the emails to attract attention.
In September, we recorded French-language mass mailing dedicated to Halloween. Spammers sent out messages advertising carnival costumes and various Halloween accessories.
Spammers and saving
Autumn brings the first frosts and heating and electricity costs increase. This seasonal fact was actively exploited by spammers. Many September mailings offered different ways to keep homes warm and reduce utility bills.
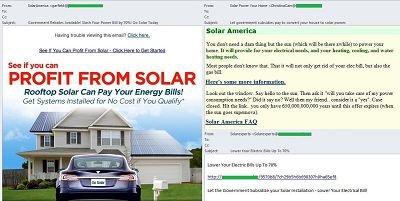
English-language mass mailings along these lines mostly advertised the installation of specialized solar panels. These messages arrived in different formats: some contained a short piece of text, others a colorful banner.
All messages contained a long link leading to a newly registered domain which varied from email to email. After a series of redirects these links led users to a site describing a US government program of subsidies for the installation of solar panels, or to a blank site containing links to companies which could install solar panels or sell related equipment.
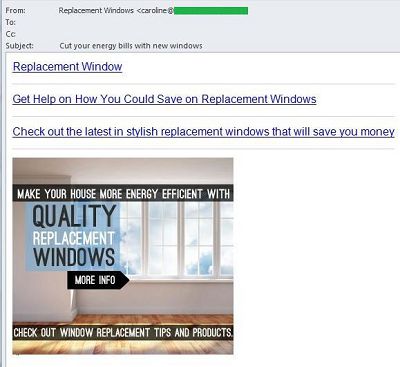
September also brought several mass mailings about the installation of insulated windows, promising to save warmth and cut energy costs. These messages contained long links which, after a series of redirects, led the user to the website of the store providing more details and waiting to take orders.
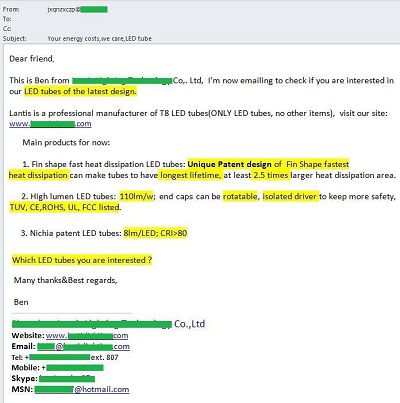
There were also mass mailings from manufacturers of LED lamps, who also played on the cost-cutting theme. Such emails usually arrived on behalf of a company manager and provided his contact details. The company’s products were described in detail in the message text, and there was a link to a company website. These emails closely resembled business correspondence, but they were addressed to generic recipients rather than specific individuals. The sender address was a random set of characters which, of course, differed from the contact email addresses indicated in the email.
Motor insurance services
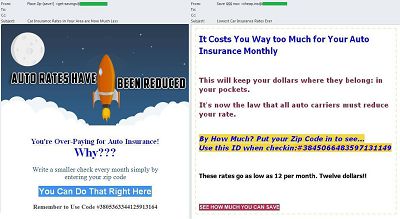
English-language spammers used auto insurance offers to lure users into handing over personal information. The message headings promised simple ways to significantly reduce motor insurance costs. The links contained in the emails led to a newly created website which redirected victims to another resource that had nothing to do with insurance services. This site invited users to answer three questions and win a MacBook Air, iPhone or iPad. After answering the questions and selecting the preferred prize, users had to enter their personal information – name, address, zip code, phone number and email address. In other words, under the pretext of a valuable prize, the scammers tried to obtain contact details from their victims.
The geographical distribution of spam sources
In September 2013, the percentage of spam in email traffic was down 1.4 percentage points and averaged 66.2%. The Top 3 sources of world spam were unchanged: China remained in 1st place with 22% of all distributed spam, an increase of 1 percentage point from the previous month; the USA came 2nd, having distributed 18% of world spam, a decline of 1 percentage point compared to August; South Korea was 3rd, averaging 14% (+1.4 percentage points). In total, these three countries accounted for 54% of global spam.
As in August, Taiwan occupied 4th place, contributing 6% to the world spam flow, up 0.8 percentage points.
India’s share grew by 2 percentage points, accounting for 5% and moving it from 8th to 5th overall.
As forecasted, Japan broke into the top 10 most active distributors of global spam: its contribution of 2.4% lifted it to 9th place. Canada completed the Top 10 with a share of 2% that pushed it up two places.
Belarus and Germany saw their shares decline: Belarus (0.8%) fell six places and Germany (0.7%) also dropped out of the Top 10.
The other Top 10 members maintained their positions in the rating with negligible fluctuations in their contributions.
In September, South Korea remained the leading source of spam sent to European users (54%) even though its share dropped by 6 percentage points. It was followed by Taiwan (5.6%) and India (4.8%). India’s share grew by 2.7 percentage points, moving it up from 6th to 3rd place.
Last month 3rd place was occupied by the US (3.6%). In September, it dropped to 6th place although its share decreased negligibly – only 0.3 percentage points.
Russia (4.3%) and Vietnam (4.1%) remained in 4th and 5th places respectively. However, the total percentage of spam originating from these two countries increased by 1.5 percentage points.
In September, the Top 10 included Malaysia (1.2%). Two other Asian countries, Japan and Hong Kong, also produced a greater share of spam compared with the previous month – their figures increased by 0.6 and 0.9 percentage points respectively to account for 1.2% and 1% of spam sent to European users.
Meanwhile, September’s spam flows from Germany (0.7%) fell 0.8 percentage points, which resulted in it dropping down to 17th place in the rating.
In September Asia (59%) remained the leading regional spam source having increased its contribution by 4 percentage points from the previous month. North America (20%) and Eastern Europe (12%) also maintained their 2nd and 3rd places, although their figures changed compared with August: North America’s share grew by 2 percentage points while Eastern Europe’s share went down 2 percentage points. Western Europe (4%) and Latin America (2.4%) came 4th and 5th respectively.
Malicious attachments in email
In September, the Top 10 malicious programs spread via email saw major changes and included five newcomers.
Trojan-Spy.html.Fraud.gen remained the most widespread malicious program, a position it has held for several months in a row. To recap, Fraud.gen belongs to a family of Trojan programs which use spoofing technology: these Trojans imitate HTML pages and are distributed via email appearing in the form of notifications from major commercial banks, e-stores, software companies, etc.
Four of the five newcomers in September’s rating – 2nd, 3rd, 6th and 9th – were malicious programs of the Bublik family. Their main functionality is unauthorized download and installation of new versions of malware on victim computers. Once the task is fulfilled, the program does not remain active: it copies itself into the %temp% file imitating an Adobe application or document.
Email-Worm.Win32.Bagle.gt was in 4th position. This mail worm is an executable file distributed in the form of email attachments. Like most mail worms it self-proliferates to addresses in the victim’s address book. It can also download other malicious programs onto a computer without the user’s knowledge. To spread malicious messages, Email-Worm.Win32.Bagle.gt uses its own SMTP library.
Yet another September newcomer, Trojan-PSW.Win32.Fareit.xvf, came 5th in the rating. This malicious program is designed to steal logins and passwords from compromised computers. It downloads its own updates without being rooted in the system and imitates an Adobe application or document.
Trojan.Win32.Llac.dleq was in 7th place. This program’s main task is to spy on the user: it collects information about software (mostly, about antivirus programs and firewalls) installed on the computer, about the PC itself (the processor, the OS, the disks), it intercepts the web camera images and key strokes (keylogger), and harvests confidential data from various applications.
Email-Worm.Win32.Mydoom.l was 8th in September. This network worm with backdoor functionality is spread as an email attachment via file sharing services and writable network resources. It harvests email addresses from infected computers so they can be used for further mass mailings. The worm also connects directly to the recipient’s SMTP server.
Yet another worm, Email-Worm.Win32.Mydoom.m, completed September’s Top 10 most widespread malicious programs. It scans MS Windows address books and the Internet Explorer browser cache to find addresses for new victims. In addition to self-proliferation it sends hidden search requests to search engines thus increasing the traffic and ratings of sites downloaded from the criminals’ servers.
The Top 3 countries targeted most by malicious emails remained unchanged: Germany (12.67%) came first again followed by the US (11.33%) and the UK , which saw its share rise to 9.98% this month.
Russia remained in 9th position although the percentage of antivirus detections in the country dropped to 2.6%.
Also worthy of mention is the fact that Saudi Arabia (2.41%) entered the Top 10 in September.
Special features of malicious spam
Fraudsters don’t often target Internet and telecommunication providers. However, in September 2013 we registered several malicious mass mailings which exploited the names of international companies doing business in this sphere.
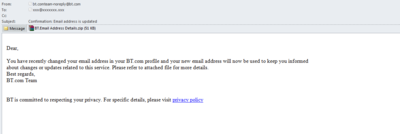
British telecommunication company BT Group was invoked to distribute Trojan-Downloader.Win32.Dofoil which downloads and executes malicious software on computers. The fake message stated that the recipient had recently specified a new email address which would, in future, be used to deliver notifications and updates. For more detailed information the recipient was asked to open an attachment, which in fact was a hidden Trojan. In order to convince the recipient of the legitimacy of the email, the attackers used a sender’s address which seemed legitimate at first glance and a link to the company’s official website. However, the absence of a personal address and the attached executable file BT.Email Address Details.pdf.exe should have alerted users to the risk of fraud.
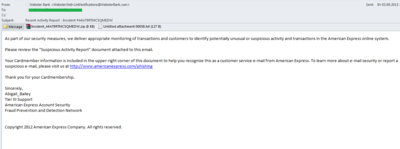
Fake notifications from the banks are not uncommon. In September, we registered a malicious mass mailing allegedly sent on behalf of Webster bank. This time, the message read that the company was monitoring all customer transactions to identify suspicious activity in the payment system. The email included the attached Trojan downloader Trojan-Downloader.Win32.Angent disguised as a report from the bank. To make their emails look more legitimate, the fraudsters sent them from a fake address similar to the official one and the body of the email contained a link to the official site of the company, as well as the Auto Signature.
Phishing
The most attractive targets for phishing attacks did not vary significantly in September. Social Networking Sites continued to top the list (28.1%).
This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
The share of Email and Instant Messaging Services (18.1%) increased 0.8 percentage points meaning this category remained 2nd. Search Engines (16%) came 3rd with a slight drop of 0.1 percentage points.
The share of Financial and E-pay Services (14.9%) increased by 1 percentage point and saw this category equal last month’s 4th place.
IT vendors lost 0.5 percentage points and swapped places with Telephone and Internet Service Providers whose share rose (+0.6 percentage points): these two categories occupied 5th and 6th places respectively.
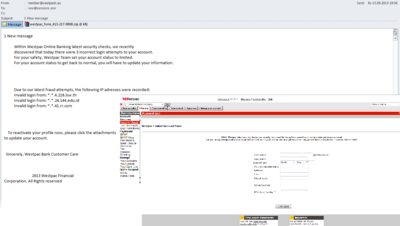
In September, the attention of the phishers was again focused on major banks in Australia and New Zealand. In July 2013 we registered a mass mailing containing fake notifications sent on behalf of the Bank of Australia and New Zealand Banking Group. This time, the phishers tried to trick the clients of Westpack, one of the leading banks of Australia.
The attackers did not even take the trouble to invent something new to cheat the victims – they just used a time-tested trick. The fake email informed the recipient that the security system of the online banking service had registered three unauthorized attempts to enter the account and, according to security rules, had blocked access. To unblock the account, the user had to open the attached file. The archive Westpac_form- 413- 217 -9908.zip contained an HTML page requiring the user’s personal information. Once all the fields were filled in, the data was passed over to the fraudsters.
The phishing page used the colors and the logo of the official website of the bank, but it was not an exact copy. However, if the user clicked on a link on the phishing page to enter one of the site pages, the official site of the bank opened in a separate window. To trick the user, the phishers also provided detailed account information, such as IP addresses that were allegedly used for unauthorized attempts to enter the password.
Conclusion
In September, the proportion of world spam in mail traffic continued to decline and reached 66%. As always the spammers focused on advertising seasonal goods and services. For example, the number of offers related to energy saving and insulating buildings increased significantly. September mass mailings exploited the theme of popular holidays – this time they were about Halloween and New Year. Next month the share of Christmas spam will obviously grow.
As expected, the proportion of attacks on social networking sites decreased while the share of attacks on financial and e-pay services grew. However, these changes were negligible and the rating of the organizations most often targeted by phishers did not see much change. Most likely both of these trends will continue in October. Also in September scammers tended to shift their attack vectors away from banks and delivery services and towards various telecommunication companies.

























Spam in September 2013