
The quarter in figures
- The percentage of spam in total email traffic decreased by 2.4 percentage points from the second quarter of 2013 and came to 68.3%.
- The percentage of phishing emails grew threefold and accounted for 0.0071%.
- Malicious attachments were detected in 3.9% of all emails – 1.6 percentage points more than in Q2 2013
Back to basics
In Q3 2013, spammers indulging in the stereotypical promotion of medications to improve potency were especially creative, combining social engineering techniques with tricks to bypass spam filters.
In one mass mailing they used the following method: the email subject used a string of symbols designed to resemble the word ‘Viagra’, while the text was limited to a single link to a pharmaceutical site.
This minimalist approach helps to bypass content filtering. There are no keywords to be found, since the word ‘Viagra’ cannot be read by the filter even though it is obvious to a human reader. Since each email found a different ‘code’ for Viagra, it wasn’t enough to simply add a new keyword to the database either. Since UTF-8 includes symbols from all languages – including very rare ones. Most languages have their own unique letters, modifiers and symbols even when they are based on the familiar Latin alphabet. As a result there are more than 100 symbols which could be read as the letter ‘a’. It’s not surprising that there are hundreds of millions of different potential combinations which could spell ‘Viagra’.
Another mass mailing sent on behalf of popular email or social networking resources encouraged recipients to register, read a new message or respond to a delivery failure. However, clicking the link sent users to a compromised website which redirected them to an online store selling medications to increase potency.
The authors of the mass mailing imitated notifications from many companies, including Apple, Yahoo, Google, Amazon, eBay, Twitter, Instagram, Skype, etc. The spammers did not put a lot of effort into these messages: the fake emails sent on behalf of different companies were designed using the same template; only the company name was changed.
Interestingly, this approach (fake notification, link to a compromised site and a redirect to the final site) is often used by spammers distributing malicious code. This type of spam is spread via partner programs where the spammer profits from every user who clicks the link and ends up with an infected computer. The terms for advertising mailings are the same, except that here the spammers earn a commission on pills sold via the distributed links. This means that the attackers use the same tactics for different partner programs. In Q3 we registered cases using the same mass mailing for two different partner programs: the links in the emails led to different resources depending on the region or the time of day. For example, users in countries where medications are only available with a prescription were redirected to a Viagra site while all other recipients were redirected to a fraudulent or malicious resource.
Yet another spam mass mailing exploited social engineering techniques (fake notifications from a popular resource) and link obfuscation.
The emails imitated notifications from a Google Message Center service. The body of the message contained the link to the Google domain. In fact, the spammers just used the Google.Translate service to mask their own websites: they made a request to translate the website addresses. The fraudsters did not require any real translation as the sites were initially English-language and were translated into English.
The spammers used yet another trick: some characters in the link (different in each email) were replaced for the corresponding hexadecimal equivalent in ASCII. The browser easily recognized the obfuscated link and opened the appropriate site, but for spam filters each link looked unique.
News and malware
Q3 2013 was rich in events which generated public interest, such as the birth of the royal baby in the UK, the FBI hunt for Edward Snowden and the railway accident in Spain. All this news was used by fraudsters to distribute malware.
The malicious emails registered by Kaspersky Lab in Q3 2013 came in various forms but mostly imitated mass news mailings. However, the links contained in all emails led to compromised websites which redirected users to a page with one of the most popular exploit kits – Blackhole. Once users reach the website, Blackhole starts searching for vulnerabilities in their software. If it finds any, it downloads several malicious programs, including Trojan spyware designed to steal personal data from victim machines.
In October, the author of Blackhole, going by the nickname Paunch, was arrested in Russia. The future of this set of exploits is not clear. Either somebody else will take over the management of the Blackhole kit, or spammers will migrate to other sets. Either way, it’s likely that there will be fewer examples of these malicious “news” mailings.
Statistics
The percentage of spam in email traffic
The percentage of spam in total email traffic during the third quarter this year came to 68.3%, down 2.4 percentage points from the second quarter.
This decrease, however, cannot be seen as the start of a trend; the percentage in the third quarter was only 0.3 points lower than the average January-to-June indicators
Sources of spam by country
In Q3 the top three spam sources remained unchanged: China (-0.9 percentage points), the US (+1.2 percentage points) and South Korea (+2.1 percentage points). The total share of these three countries accounted for 55% of the world’s spam traffic.
As in the previous quarter, Taiwan came 4th in the rating (+0.1 percentage points).
It is followed by Russia (+1.3 percentage points), whose share increased more than 1.5 times.
Interestingly, Russia’s growing contribution coincided with a fall in the levels of spam coming from other former Soviet republics – Belarus (-0.9 percentage points), Ukraine (-0.9 percentage points), Kazakhstan (-1.5 percentage points) – while in Q2 2013 these countries produced far more spam than Russia.
However, this does not necessarily mean the spammers are organizing new botnets: such fluctuations might be caused, for example, by swapping from one existing botnet to another when spreading large-scale mailings.
Sources of spam by region
In Q3 the rating of the top sources of spam by region did not undergo any major changes from the first two quarters of 2013. The share of the regions remained almost the same too.
Asia remained the number one regional source of spam (+0.2 percentage points). It is followed by North America (+1.9 percentage points) and Western Europe (-0.2 percentage points).
The share of the other regions did not vary significantly.
Noticeably, there is not always a correlation between where spam is sent and where it is produced. For example, a lot of African spam goes to Russia; that originating in South Korea is often sent to Europe, while spam from Western Europe is distributed evenly around the world.
The size of spam emails
As seen from the diagram, the percentage of small spam emails weighing in at under 1 KB is growing from quarter to quarter. The majority of these emails contain hardly any text. They only include a link, which usually leads to the redirecting site or to a short link service which makes each email unique. These emails create problems for spam filters and, due to their small size, can be sent quickly and in huge quantities.
Malicious attachments in email
The level of malicious attachments in the third quarter was 1.6 percentage points higher than in the second and came to 3.9% of all mail traffic.
Trojan-Spy.HTML.Fraud.gen topped the rating of the most popular malicious program spread by email in the third quarter this year. This malicious program is designed to look like an html page used as a registration form for online banking services. It is used by phishers to steal financial information.
As in the previous quarter, Email-Worm.Win32.Bagle.gt came second. This email worm, unlike others, can send copies of itself to the contacts in a user’s address book and also receive remote commands to install other malware.
Our Q3 rating includes two Mydoom family worms which occupy 3rd and 4th places. These malicious programs are designed to harvest email addresses from users’ address books. This method of collecting addresses means your email address might fall into the fraudsters’ hands even if it isn’t publicly available. The Mydoom family is very old, but it continues to work effectively on computers where software has not been updated. Email-Worm.Win32.Mydoom.m can send hidden search requests to search engines. It compares the addresses of the sites displayed on the first page of the search results with the addresses which it has downloaded from the fraudsters’ servers. Having found a match, it opens the link on the search engine page thus increasing search results ratings for specified sites.
Representatives of the ZeuS/Zbot family occupied 5th, 6th, 7th and 9th places. These malicious programs are designed to steal confidential information – usually bank card details – from computers.
Trojan.Win32.Llac.dleq finished the quarter in 8th place. This program’s main task is to spy on the user: it collects information about software (mostly, about antivirus programs and firewalls) installed on the computer, about the PC itself (the processor, the OS, the disks), it intercepts web camera images and key strokes (keylogger), and harvests confidential data from various applications.
Trojan.Win32.Bublik.beyb came 10th. This Trojan’s main functionality is to secretly download and install new versions of malicious programs on victim computers. It appears in the form of an .EXE file with an Adobe PDF document icon.
The distribution of malicious programs spread by email in Q3 2013 is as follows:
In Q3 2013 the ZeuS/Zbot family took the lead. It is followed by the Tepfer family although none of its modifications entered the Top 10. This type of Trojan was designed to steal passwords for user accounts. The Fraud family of Trojans is in 3rd place, with Trojan-Spy.HTML.Fraud.gen the individual leader.
The Bublik family was 4th. Fifth place was occupied by the Androm family, which downloads and runs malicious files on victim computers.
The list of countries most frequently targeted by malicious emails has undergone some changes since the second quarter of the year.
The US is still number one in the rating (-0.2 percentage points). Germany moved up from 3rd to 2nd place while Russia fell to 9th place (-8.6 percentage points), closer to its usual placing. The UK completed the Top 3 with an increase of 2.8 percentage points.
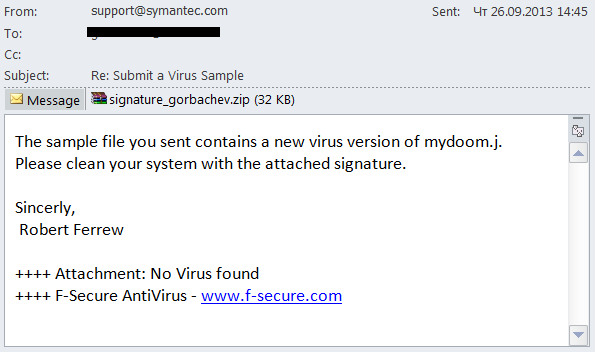
In Q3 2013 we came across one very interesting mass mailing – the fraudsters imitated a reply from the technical support service of a large antivirus company.
The email informed the user that the file which had allegedly been sent for analysis, turned out to be malware. The “technical support engineer” even named the verdict (in our example, mydoom.j) and suggested using the attached signature to disinfect the computer. However, if users (who probably didn’t send any samples in the first place) opened the attachment, they would find a malicious program detected by Kaspersky Anti-Virus as Email-Worm.Win32.NetSky.q.
Interestingly, the spammers made a mistake: the address in the From field used the official address of Symantec’s technical support service while the auto-signature in the email named another antivirus company – F-Secure.
Phishing
In Q3 2013 the percentage of phishing emails increased threefold from the previous quarter and accounted for 0.0071%.

Distribution of the Top 100 organizations most frequently targeted by phishers,* by category – Q3 2013
* This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In Q3 notifications from social networking sites were most frequently imitated in phishing emails. Messages sent on behalf of email services and search engines were in 2nd and 3rd places. In fact, these two categories are difficult to separate as many major companies combine search engine and webmail functions.
In total, these three categories represented over 60% of all attacks in the Top 100 organizations most frequently targeted by phishers. This figure shows that the monetization of phishing is largely based on the sale of stolen account credentials, which can be used in turn to distribute spam across their contact lists.
Financial and e-pay organizations and banks came 4th in the list of phisher targets. This does not imply that phishers are less interested in banks. It is more likely that attacks on individual institutions are rarely on such a large scale as to get them into the Top 100.
Conclusion
In Q3 2013 spammers actively used both old and new tricks to bypass filtering as well as social engineering techniques to persuade users to click the necessary links. For example, one of the most common malware distribution tricks is to use high-profile news stories and design emails in the form of newsletters. Some tricks, such as fake emails sent on behalf of a well-known Internet resource, were considered especially effective and used in various partner programs. For example, a link in an email imitating a notification from Facebook could, at different times, lead to a site advertising medications or to a site containing exploits.
However, the arrest of the Blackhole exploit kit creator has shown that cybercriminals do not go unpunished, even in Russia with its relatively weak legislation against cybercriminals. We will continue to follow the developments in this case.
Q3 2013 saw little change in the leading spam sources by country. On a regional level there was even less change. It seems that the location of botnets is relatively stable, or at least there is a lull in the active relocation of botnets.
Despite the slight decline in the share of spam in email traffic, the proportion of malicious spam grew more than 1.5 times compared to the previous quarter. The majority of the malware spread via email targeted user logins, passwords and confidential financial information.
As for the phishers, their most attractive targets were user accounts for social networking sites, email and other resources.































Spam in Q3 2013