
The quarter in figures
- The percentage of spam in total email traffic increased by 4.2% from the first quarter of 2013 and came to at 70.7%.
- The percentage of phishing emails in total mail traffic fell by 0.0016% and came to 0.0024%.
- Malicious attachments were detected in 2.3% of all emails – that’s 1% less than in Q1 2013.
Spammer methods and tricks
Different types of spam generate different amounts of revenue for spammers. Your typical advertising mailing for a small business will bring in a certain amount of money, while advertisements for Viagra, for which the spammer earns a commission for each client who clicked on the link in the email and made a purchase, is paid at a different rate. However, the biggest profits are generated from malicious spam. An infected computer is worth considerably more than a Viagra purchase. Spammers are particularly interested in making sure that a malicious program gets onto a computer; perhaps that is why malicious spam often resorts to using a variety of tactics and social engineering.
Malicious emails targeting corporate users
Many emails with malicious attachments were addressed to corporate users this past quarter.
Absolutely all of these types of emails were disguised as auto-replies, i.e., delivery failure notifications, or notifications of the arrival of an email, fax, or scan.
These emails do not use any one specific type of social engineering tactics – threats or ways to lure users with the large sums of money they could get if they open the attachment. However that is exactly what makes these emails seem less suspicious. Malicious users expect corporate employees to skim over the details, assume the email is legitimate and open the attachment – releasing a malicious program.
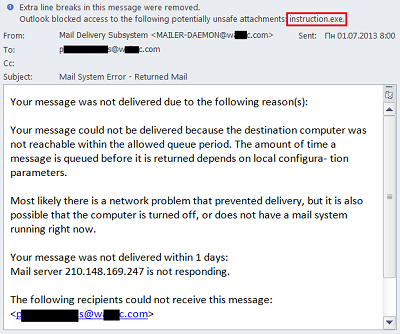
The email is allegedly from an email server and is designed to look like a Delivery Failure notification.
The email allegedly was generated by the MAILER-DAEMON of the recipient’s email domain, and appears to be a standard non-delivery notification. It suggested writing an email to postmaster@ with any questions. Meanwhile, the attachment contained an executable file (the names vary: instruction.exe, mail.scr, and others) detected by Kaspersky Lab as Email-Worm.Win32.Mydoom.m.
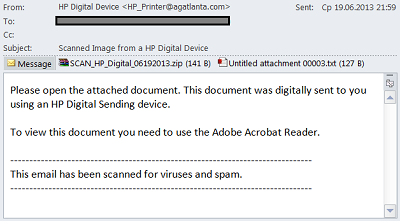
Many other malicious emails were fake automatic notifications of the arrival of a new scan or fax document.
Naturally, the attachments to these emails also contained a variety of malicious programs. Remarkably, many of these fakes were designed to look like messages from an HP device, or the JConnect service – a fairly common program in the business community. The emails were sent to corporate addresses, and not to free email addresses. And in fact, a company employee is going to be more likely to trust an email if the company where he works uses that brand of equipment or service provider.
Next, of course, another sophisticated spammer trick is to bring up data security. One of the emails Kaspersky Lab saw this past quarter imitated a message from Citigroup and told recipients that they had an encrypted message waiting for them.
But the attachments didn’t contain a message – instead, it was the Trojan classified by Kaspersky Lab as Trojan-PSW.Win23.Tepfer.nblo.
These emails do not look like anything out of the ordinary, nor do they seem suspicious at all, especially to frazzled multitasking company employees. Only the attachment’s .exe extension would give rise to any suspicion and might put recipients on the defensive.
Keep in mind that malware targeting corporate users is spread using different tactics. Company employees need to remember that malicious code can be planted into office documents, and caution should be used when dealing with any email attachments.
Emails from popular resources
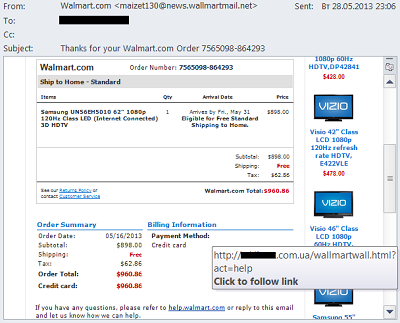
We have previously written about emails that imitate notifications from social networks, stores, airline emails, etc. There are still a lot of these emails out there. Readers may be interested to know that Walmart is now on the list of stores being impersonated by spammers in their fake notification emails.
These fake emails inform the recipients of their alleged recent purchases from that store. The links in the emails take users to hacked sites that redirect them to a malicious website seeded with exploits.
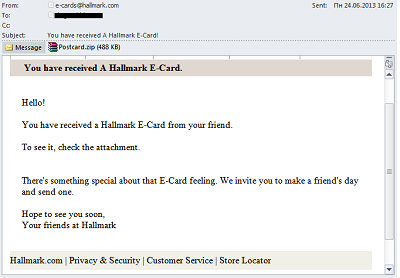
Malicious eCards
Previously, eCards with malicious attachments were sent out by malicious users for each major holiday -but lately, malicious eCard sightings have been few and far between. However, this past quarter, Kaspersky Lab again detected these malicious mailings, this time targeting the prominent American greeting card company Hallmark.
This attachment was detected by Kaspersky Lab as Trojan.Win32.Buzus.liez.
Random Text
In addition to malicious eCards this past quarter, Kaspersky Lab also detected another long-forgotten tactic. In Q1 2013, one of the tricks used by spammers was “white text,” which is essentially random text added to the bottom of an email, where the color of the text is the same as the background color. This quarter, spammers used more or less the same trick; they added random text, but this time they didn’t even bother to make it “invisible,” but instead just separated it from the main body of text with a large number of empty lines. All of the texts were taken from various news stories. For example, while an email might start out with a bright photograph advertising a certain good or service, if the recipient scrolled all the way to the bottom, he would find an excerpt of a news story on Hugo Chavez, the Boston Marathon, or the war in Korea in fine print.
Statistics
The percentage of spam
The percentage of spam in total email traffic during the second quarter this year came to 70.7%, or 4.2% higher than in the first quarter. This increase, however, cannot be seen as the start of a trend; the percentage in the first quarter was an exception to the rule, with a month-by-month low of 58.3% in January, while all other months showed spam percentage indicators at or near 70%.
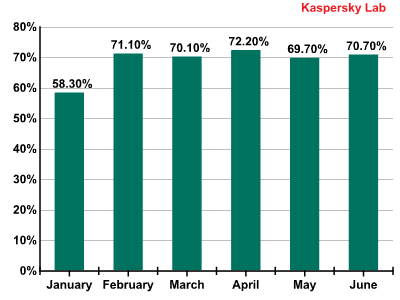
The percentage of spam in email traffic, H1 2013
These slight changes in the percentage of spam in mail traffic point to a certain level of stabilization after the sharp rises and falls seen in recent years.
Sources of spam
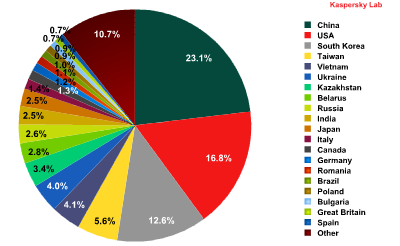
The distribution of sources of spam by country, Q2 2013
The countries that are the top sources of spam are the same as before, although their percentages have changed slightly: China is down by 1.2%, the US is down by 0.9%, and South Korea’s percentage is lower by 3%.
The amount of spam sent originating in Taiwan and Vietnam rose slightly (1.6% and 1.1%, respectively), which ranked in 4th and 5th places.
The situation with some former Soviet republics is also interesting. In three of them – Ukraine, Kazakhstan, and Belarus – the percentage of outgoing spam surged and in the second quarter, these countries ranked 6th, 7th, and 8th places in the Top 20 sources of spam, pushing Russia down in the ratings. We also hasten to point out that not only did these three countries demonstrate an increase in outgoing spam all at the same time, but the dynamics of these upward movements were also very similar, peaking in May.
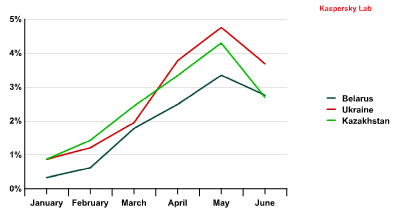
The changes in the percentages of spam originating in Belarus, Ukraine, and Kazakhstan during the first six months of 2013.
This could indicate the emergence of new botnets in these countries or the infection of web hosting services from which spam is sent.
Remarkably, when we look at sources of spam by region rather than by country, the geography is different altogether. In Europe, a lot of spam comes from South Korea (47.9%), and the percentage of spam sent from Korea to other regions is quite low. From China, most spam targets Asia-Pacific (64%) and the US (21.2%), while Europe and Russia see little to no spam coming from China. Most US-based spam ends up in the US (51.6%), and in Russia, spam arrives from Taiwan (12.2%), Vietnam (9.4%), and Ukraine (9%).
Sources of spam by region
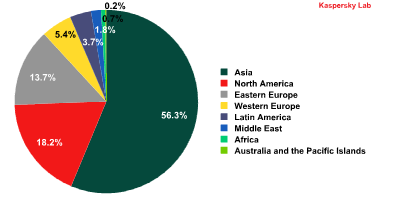
The distribution of sources of spam by region in Q2 2013
As far as the top sources of spam by region are concerned, the ratings did not experience any major changes from the first quarter, although the percentages of specific regions did change a bit. Asia’s percentage rose by 4.5%, and remains the number one regional source of spam. Eastern Europe’s percentage increased by 2.6%, primarily due to greater activity in Ukraine and Belarus.
The percentage of spam originating in Western Europe was 3.7% lower, as was the percentage of spam originating in South America (-2.4%), which reached a new record low. Readers may remember that just two years ago, South America ranked second in terms of the amount of spam originating in that region. Other regions with changes are the Middle East (-0.2%), Africa (-0.6%), and Australia and Oceania (-0.04%).
The size of spam emails
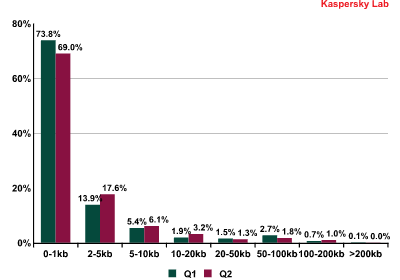
The size of spam emails: Q2 2013
The majority of spam emails are still very small, weighing in at under 1Kb. The number of these smaller-sized emails increased from the first quarter by 4.8% and amounted to 73.8% of all spam mails. Incidentally, there was also a slight increase (+0.94%) in the percentage of emails weighing in at between 50 and 100 Kb. This size is used primarily in emails with attachments, including malicious attachments.
Malicious attachments in email
The amount of malicious attachments in the second quarter was lower than in the first by 1% and came to 2.3% of all mail traffic.
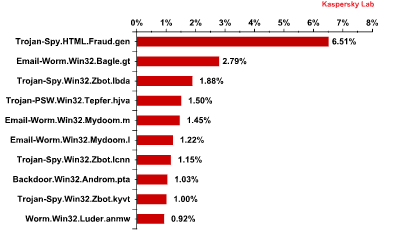
The Top 10 malicious programs spread by email in Q2 2013
The most prevalent malicious program spread by email in the second quarter this year was the same as in the first quarter: Trojan-Spy.HTML.Fraud.gen. Readers may recall that this malicious program is designed to look like an html page used as a registration form for online banking services. It is used by phishers to steal users’ financial information.
Email-Worm.Win32.Bagle.gt held onto its second place from first quarter. This email worm, unlike others, can send copies of itself to the contacts in a user’s address book and also receive remote commands to install other malware.
One of the modifications of the notorious ZeuS/Zbot program – Trojan-Spy.Win32.Zbot.lbda – ranked in third place in the second quarter. ZeuS/Zbot is designed to steal different types of confidential information from user computers, including credit card data among other things.
Trojan-PSW.Win32.Tepfer.hjva was in fourth place. This malicious program is designed to steal passwords for user accounts.
Further down the list there are several more email worms and another two modifications of the ZeuS/Zbot Trojan. Another malicious program featured in the Top 10 is Backdoor.Win32.Androm.pta. These types of malicious programs allow malicious users to control infected computers without users noticing a thing. They can, for example download other malicious files and launch them, send a range of data from the user’s computer, and take other actions. What’s more, computers infected with these programs are often integrated into a botnet.
Note that some malicious programs have many modifications, although their actions aren’t very different from one another. That is why Kaspersky Lab also publishes graphs of the most prevalent malware families, which provide a clearer picture of the distribution of malicious attachments spread by email.
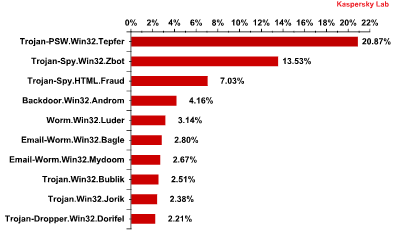
The Top 10 families of malicious programs spread by email in Q2 2013
Over 40% of malicious programs sent by email are ultimately designed to steal personal information, including financial data.
The list of countries most frequently targeted by malicious emails has undergone some changes since the first three months of the year.
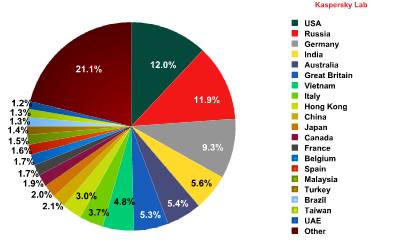
The distribution of email antivirus detections by country in Q2 2013.
Despite a slightly smaller percentage (-1.2%), the US is still in first place. Meanwhile, Russia skyrocketed from 7th to 2nd place (+8.3%) when it comes to the percentage of email antivirus detections, which increased several times over in Russia. This surge took place during June, when the percentage of email antivirus detections in Russia reached 29.3%. The most commonly found malicious families in Russia turned out to be Net-Worm.Win32.Kolab and Trojan-GameThief.Win32.Magania. Kolab is a family of malicious programs that operate as backdoors that prevents antivirus programs from functioning and receives remote commands from malicious users. The programs in the Magania family were designed to steal usernames and passwords for the online game Maple Story, but can also function as a worm (and are spread via USB drives).
As a result of the sharp rise in Russia’s percentage, Germany was pushed out of second place and into third (-1.9%). India and Australia remained in the same places from the first quarter, although their percentages were slightly lower (-0.9% and 1.1%, respectively). The percentage of email antivirus detections in other countries experienced very minor changes.
Phishing
The percentage of phishing emails in total mail traffic during the second quarter this year fell by 0.0016% and came to 0.0024%.
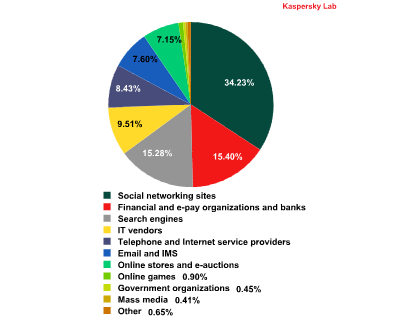
The distribution of the Top 100 organization most frequently targeted by phishers,* by category – Q2 2013
* This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
The general distribution of organizations targeted by phishers did not undergo many changes from the first quarter. The number of attacks launched against social networks fell by 3.3%, and the percentage of attacks against financial organizations increased by 1.2%, pushing that category into second place in the ratings.
The percentage of attacks targeting Internet providers was up by 1.8%, and attacks against email providers rose by 2%. Readers might note that the quarterly rise in phishing attacks launched against email services is related to the sharp rise in the number of attacks that were launched in June, which amounted to 13.2%. The percentage of attacks targeting other organizations varied by less than 1%.
More and more often these days, phishers are wary of relying solely on the human factor and are less willing to wait for users to enter their own data. Instead, malicious users are now sending out malicious emails seeded with Trojans that steal usernames and passwords, including for online banking accounts.
Malicious attachments aren’t only found in emails masquerading as forms for Facebook and other popular online resources – they can also be found in emails disguised as official bank messages.
This email was put together in a careless manner – note the synonyms placed together in parentheses, a typical error in spam programs. However, the rest of the text would not cause users to be particularly suspicious. Even the attached file does not have an .exe extension or even an .exe file in an archive, which most users would immediately see as suspicious. But the innocent-looking .doc file contains an exploit classified by Kaspersky Lab as Exploit.MSWord.Agent.dj, which targets a vulnerability that could allow it to infiltrate a computer’s security system and download malicious programs that steal personal user data.
Conclusion
Since February 2013, the percentage of spam in email traffic has seen little to no change. This is the first period in which Kaspersky Lab has observed some stabilization in spam traffic, as there have been many sharp fluctuations in spam numbers over the past few years. Kaspersky Lab expects that the percentage of spam will remain at this level in the future.
Some changes did take place in the rankings of countries where spam originates. The percentage of spam sent from Ukraine, Belarus, and Kazakhstan rose substantially. This surge points to new botnets or infected web hosting services within these countries – and we are seeing more and more spam being sent from hosting services lately.
Among the threats that are spread by email, the most prevalent families are those designed to steal data to access user accounts (usernames and passwords), particularly for online banking services. The number of emails with malicious attachments addressed to users in Russia also increased considerably.
Recently, spammers have begun sending out emails with malicious attachments designed to look like automatic delivery failure notifications sent out by servers. Another common trick is to make malicious emails look like notifications from well-known online resources, and include links to malicious websites. Kaspersky Lab recommends that users continue to exercise caution – even when dealing with emails that appear to be legitimate.






















Spam in Q2 2013