
Fake notifications from mobile applications
The widespread use of mobile devices has triggered the emergence of email spam targeting smartphone and tablet users. We have already written about mass mailings containing malware for Android-based devices. Currently these programs are not appearing in huge numbers, but they are sent out regularly. In Q1 we saw yet another trend: fake notifications distributed in spam are now imitating messages from mobile applications. Spammers especially like the cross-platform mobile application WhatsApp: notifications sent on behalf of this application were used by spammers to spread both malware and standard adverts.
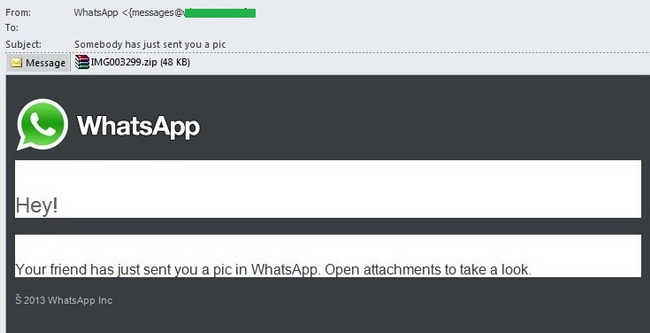
In January, we registered a mass mailing which supposedly contained an image sent to the recipient via WhatsApp. An alert user would have queried why this notification had arrived via email as the WhatsApp account is not directly associated with the email box. However, many users are used both to synchronization of their contacts and to the fact that messages from mobile applications can arrive via email so this notification would not surprise the majority of users.
In fact, the attached archive contained a malicious program detected by Kaspersky Lab as Backdoor.Win32.Androm.bjkd. It is a well-known backdoor whose main function is to download other malware onto the victim computer.
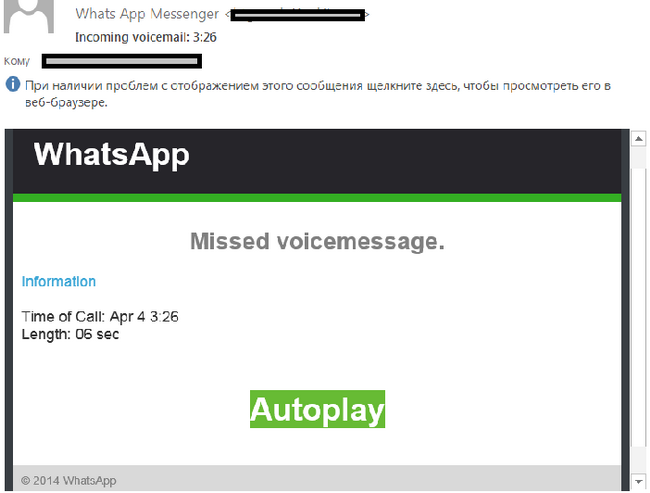
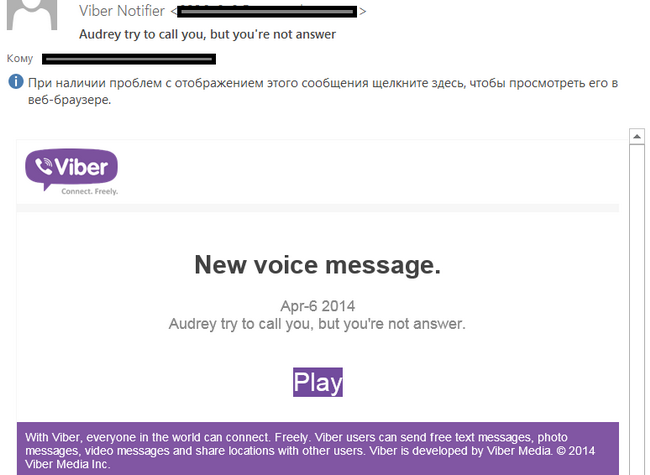
In March, we came across yet another mass mailing which also exploited the popularity of mobile applications. The recipient was informed about an allegedly missed WhatsApp voice message and was invited to click the link to hear it.
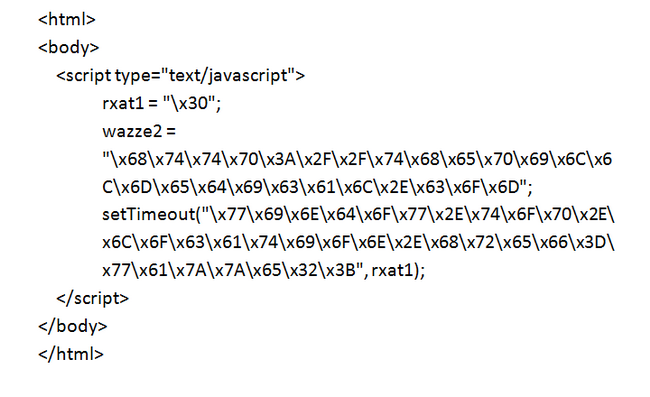
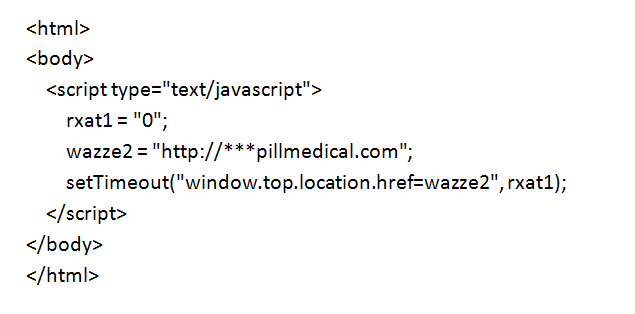
After clicking “Autoplay”, the user is directed to a hacked legitimate site that had been injected with the following Javascript:
Translating the hexadecimal gives:
This means the hacked site was a redirector, i.e., it redirected the user to another site, in this case to one advertising Viagra.
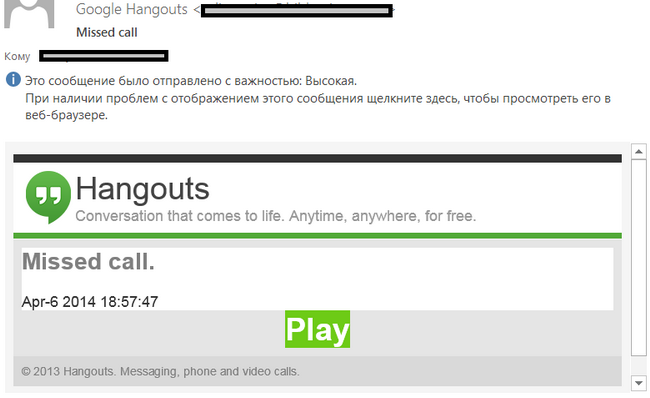
Noticeably, a similar scheme was used to distribute fake notifications from other popular mobile messengers Viber and Google Hangouts.
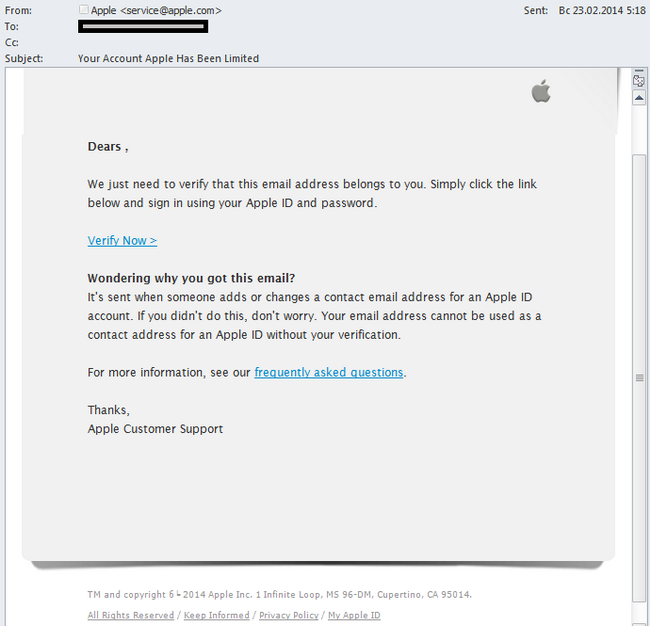
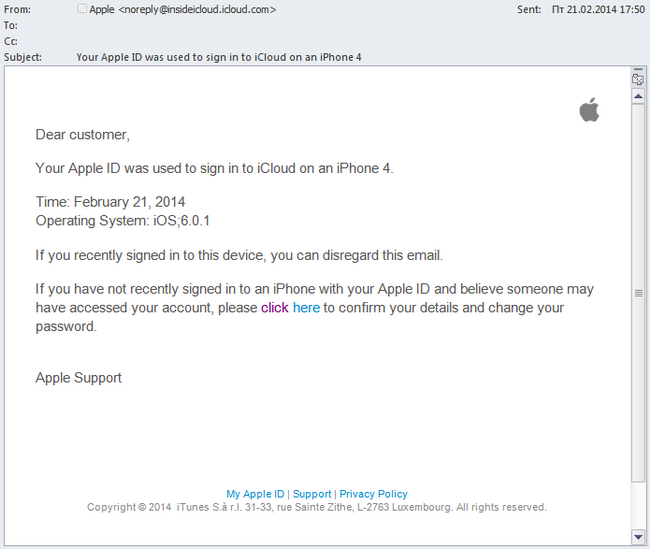
The rising popularity of mobile devices mean that phishing attacks aimed at stealing Apple ID are becoming more frequent:
In the first quarter of 2014, Apple ranked 17th among the organizations most often attacked by phishers.
Hot topics in spam: the Olympic games
In February, the Winter Olympic Games took place in Russia. Of course, this event attracted the attention of spammers, who used the theme in a variety of mass mailings even if the spam hype around the Games was slightly less than might have been expected. Chinese entrepreneurs offered different products decorated with the symbols of the Olympics, “Nigerian” scammers exploited the Olympic theme to lure money from users. We also registered several major mass mailings promoting replica watches “for a trip to the Olympics” and offering private helicopter services in Sochi.
Interestingly, this is not for the first time that spammer activity accompanying such a high-profile event has been subdued: during the Summer Olympics in London we registered fraudulent mailings about “Olympic” lottery wins while the Winter Games in Vancouver in 2010 were almost completely ignored by cybercriminals. Noticeably, during the football World Cup the amount of associated spam mailings is always higher.
In addition to the Olympic theme, spammers (mostly “Nigerian” scammers) exploited news events such as the death of the former Prime Minister of Israel Ariel Sharon. Fraudsters also continued to spread “Nigerian” spam supposedly sent on behalf of close friends of Nelson Mandela, South Africa’s former president, who died in December.
Spammer tricks: creating background noise with HTML tags
To create unique emails in a large mailing, spammers often create “background noise” in the text, i.e. adding random characters, words or text fragments. Obviously, the message becomes less readable and therefore less interesting for the user. That’s why spammers usually try to hide the random text from the user. These old methods, such as placing white text on a white background or simple separation of the “noisy” text from the main content by numerous line breaks, are still widely used by spammers even though these tricks are as old as spam itself.
However, some spammers are using more advanced techniques. One of them is to create background noise with HTML tags. This method ensures that the user will not see anything other than the main content while for the spam filter each email will be unique.
This is what the user sees:
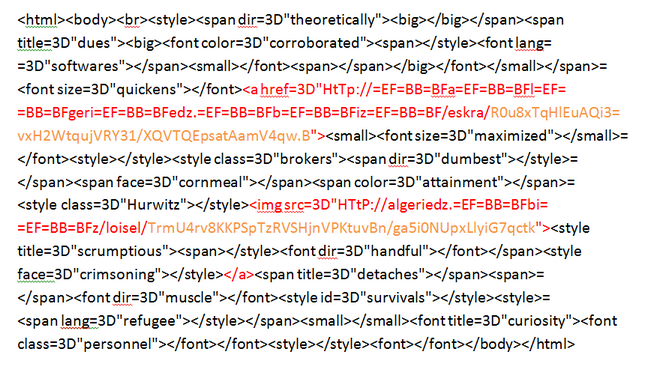
In the source code, the body of the email looks like this:
The HTML text is mostly meaningless, except for the links highlighted in red and images. In particular, we often see span tags with different attributes. This is a tag container used mainly for designing and/or assigning a unique identifier to a specific text fragment. In this case, there is no real text between the opening and closing tags, so these tags just create background noise in the email.
It’s worth noting that the link itself also contains noise. The sequence = EF = BB = BF is inserted several times in random places between standard letters. This sequence, in the hexadecimal system, refers to one UTF-8 character used to indicate the byte order of a text file. However, this is only true if it is used for its intended purpose and is placed at the beginning of the text. According to the Unicode specification, a character in the middle of the data flow should be interpreted as a “zero-width non-breaking space” (essentially, a null character). That means that an email client will simply ignore this sequence and open the link or download the image. However, for the spam filters each link will be unique. In addition, the last piece of the link (highlighted in orange) is also random.
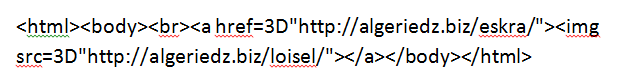
As a result, the “noiseless” source code of the email looks like this:
In terms of volume, the obfuscated part significantly exceeds the content part of the email. All this noise is randomly generated and is unique for each email in the mailing. Having opened the email in the mail client, the recipient only sees a perfectly designed message without any trace of any spammer tricks.
Statistics
The percentage of spam in email traffic
The percentage of spam in total email traffic during the first quarter this year came to 66.34%, down 6.42 percentage points from the previous quarter. However, compared with the same period of Q1 2013, the share of spam in Q1 2014 barely changed, falling by only 0.16 pp.
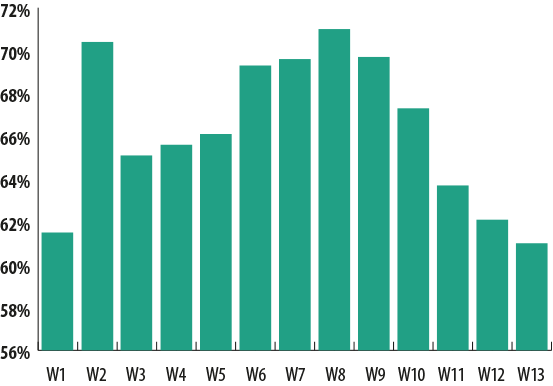
Percentage of spam in email traffic in Q1 2014
The level of spam fluctuated significantly during the quarter, reaching a low of 61% in the last week of the quarter.
Sources of spam by country
The geographical distribution of spam by country saw little change in Q1 2014.
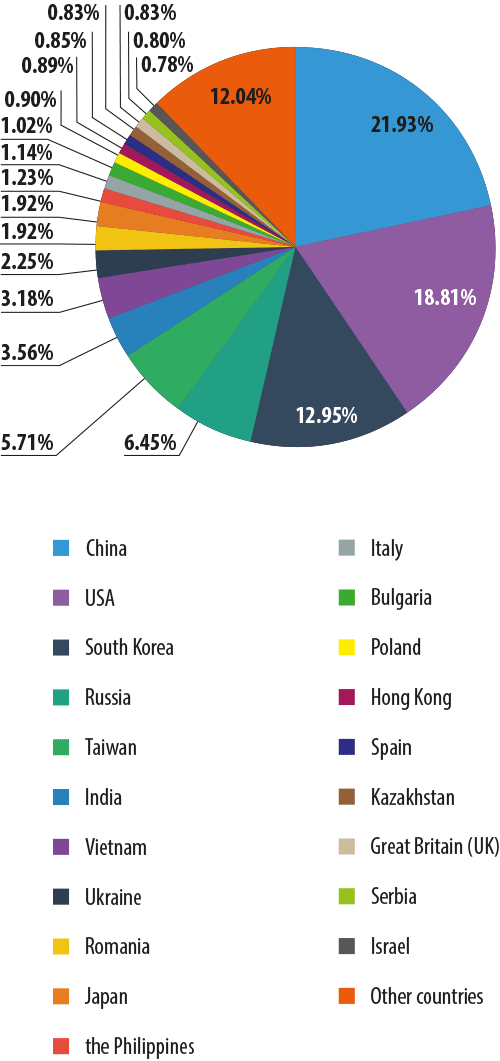
Distribution of spam sources by country in Q1 2014
The top three spam sources remained unchanged: China (-0.34 pp), the US (+1.23 percentage points) and South Korea (-0.91 pp). Russia outstripped Taiwan and moved to fourth place, one position up from the previous quarter (+0.34 pp)
The share of the other countries did not vary significantly.
Meanwhile, a shift in the second half of the Top 20 is more noticeable. The Philippines (+0.67 pp) climbed from 20th to 11th position. The share of Kazakhstan decreased by 0.76 pp which saw it fall from 11th to 17th place. Canada could not maintain its 10th place from the previous quarter and dropped to 27th – its contribution declined from 1.73% in Q3 2013 to 0.49% in Q1 2014.
Sources of spam by region
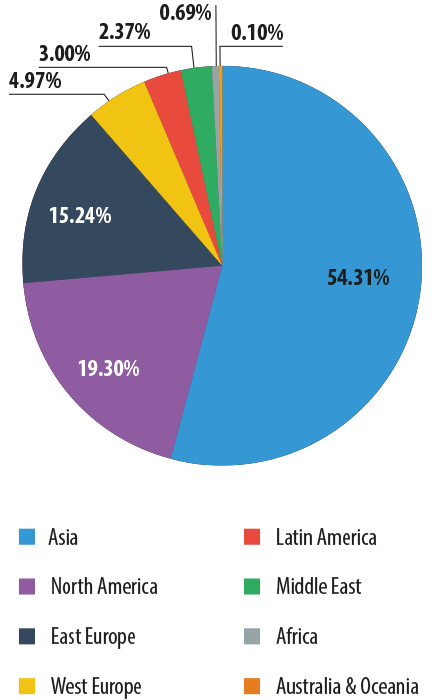
Distribution of spam sources by region in Q1 2014
In Q1 2014, the rating of the top sources of spam by region did not undergo any major changes from the previous quarter. Asia remained the number one regional source of spam although its share decreased by 3.2 pp. It is followed by North America (-0.01 pp). The share of the other regions grew slightly.
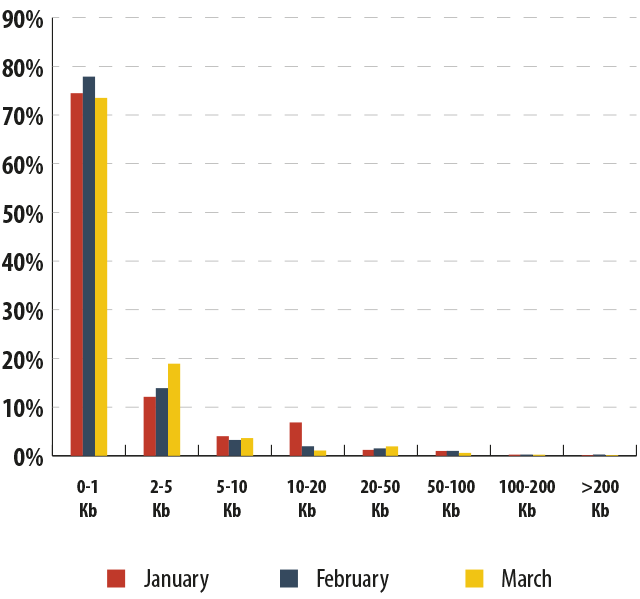
The size of spam emails
Small spam emails weighing in at under 1 KB are well ahead of their competitors.
In January we registered some growth in the proportion of 10-20 KB emails. This might be caused by holiday spam mass mailings which usually contain lots of pictures.
Malicious attachments in email
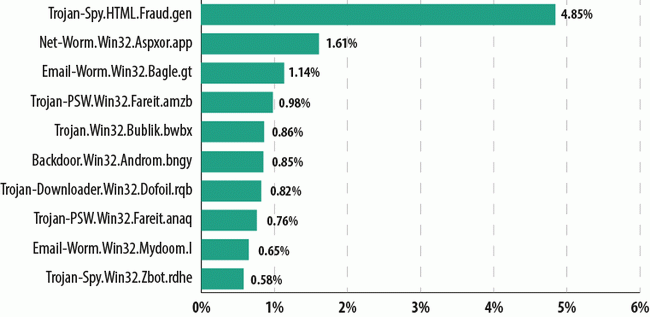
Top 10 malicious programs spread by email in Q1 2014
Trojan-Spy.HTML.Fraud.gen remained the most popular malicious program spread by email in the first quarter of the year. This malicious program is designed to look like an HTML page used as a registration form for online banking services. It is used by phishers to steal financial information.
In second and seventh places came the Net-Worm.Win32.Aspxor worms. These net worms are designed to spread spam. They automatically infect sites, load and run other programs, and collect valuable information stored on the computer such as passwords and other data to access email and FTP accounts.
Email-Worm.Win32.Bagle.gt, a long-time resident of the Top 10, came third. The main functionality of any worm is to harvest email addresses found on an infected computer. The Bagle worm can also accept remote commands to download malicious files from the Internet without the user’s knowledge.
Fourth and eighth places were occupied by Fareit family Trojans, which were most actively distributed in January. These programs were designed to steal user logins and passwords, launch DDoS attacks and download and run random software. The two samples from our rating could download and run Zbot Trojans. In addition, Fareit Trojans can steal Bitcoin wallets as well as other crypto-currency wallets (about 30 in total).
Trojan.Win32.Bublik.bwbx is in fifth. This program downloads other malware, specifically the Zbot family of Trojans, onto the victim computer.
Backdoor.Win32.Androm.bngy came sixth. The Andromeda family of malware consists of backdoors that allow cybercriminals to secretly control a compromised computer. Machines infected by these programs often become parts of botnets.
Email-Worm.Win32.Mydoom.l, a well-known mail worm, was ninth in the rating.
The Top 10 for Q1 was completed by a notorious Trojan from the Zbot family. Zbot is a family of Trojans that steal confidential user information. It can also install CryptoLocker , a malicious program that demands money to decrypt user data.
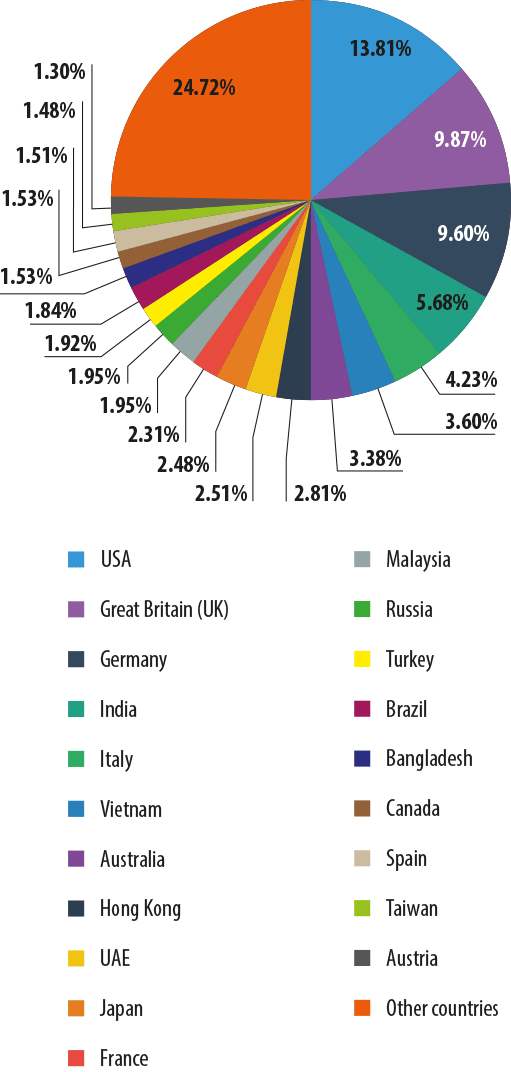
Distribution of email antivirus detections by country in Q1 2014
The list of countries most frequently targeted by malicious emails has undergone some changes since the third quarter of last year. The US’s share grew 3.68 pp while the contribution of the UK, Germany and Hong Kong decreased by 2.27, 1.34 and 2.73 pp respectively. As a result, the US, which was only third in the previous quarter, returned to the top of the rating in Q1 2014. The share of the other countries did not vary significantly.
Phishing
As of Q1 2014, we decided to merge two categories – Email and IMS and Search engines – in one Email and search portal category. These portals often have one common account which is responsible both for settings and search history; it is also a mail account as well as providing access to cloud services and other features.
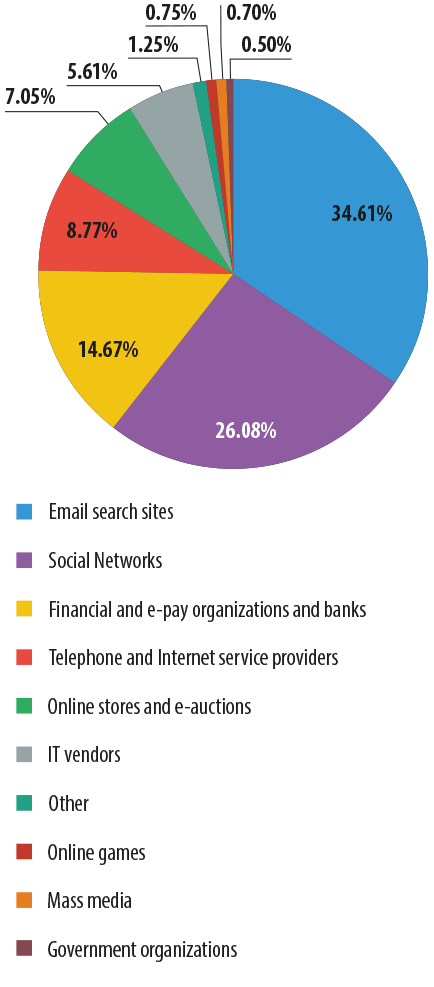
Distribution of the Top 100 organizations most frequently targeted by phishers,* by category – Q1 2014
* This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
As expected, the Email and search portals category topped the rating of the phishers’ most popular targets. Despite the fact that user accounts for the email and search portals offer many opportunities, most of these attacks are aimed at gaining access to the email service. As well as using email for their own purposes, attackers can scour its content for other logins and passwords. This, after all, is where many sites send log-in details if users forget their passwords – sometimes including all the information directly in the message body. Other sites go even further, sending the user an email containing the login and password immediately after he registers on the portal. To avoid the loss of confidential information, modern mail systems offer a method of two-factor authentication: in addition to the login and password, users have to enter a code sent to their phones by text message. Users should also delete any messages containing confidential information from their email account.
Social networking sites remain popular with phishers. Although they came second, their share dropped by 1.44 pp from the previous quarter.
The most noticeable growth was around Online stores (+2.47 pp). This was caused first of all by increased attacks on coupon services as well as on ticket agencies. The latter saw greater phishing activity in March.
The percentage of attacks targeting IT vendors slightly declined (-2.46 pp). The share of the other categories did not change significantly.
Conclusion
These days almost everyone has a “smart” mobile device and nearly every popular Internet resource has a mobile version. In addition, there are special mobile applications that are increasingly popular. Attackers are exploiting this popularity by spreading fake notifications from mobile applications. In future, this will only become more common. We also expect an increase in the volume of phishing mailings which target passwords for mobile app accounts.
Malicious applications for Android OS are being distributed via email, but so far they are quite rare. We can expect an increase in the amount of mobile malware in the near future.
The main goal of most malicious programs distributed via mail is to steal confidential data. However, in Q1 malware capable of spreading spam and launching DDoS attacks was also popular. Most popular malicious programs are now multifunctional: they can steal data from the victim computer, make the computer part of a botnet, or download and install other malicious programs without the user’s knowledge.
To bypass filtering, spammers continue to use a variety of tricks. One of the fastest-growing is creating “background noise” in messages with the help of HTML tags as well as obfuscating links in emails. The latest similar trick was to add a UTF-8 symbol to links. This symbol, when it is not placed at the beginning of the text, is interpreted as a null character. In fact, there are loads of such tricks in UTF-8 and the fraudsters make use of them every now and then.
The majority of phishing attacks targeted email accounts. Users are often lax when it comes to their email accounts: many of them use simple logins and passwords. We would like to remind users that a hacked email account can allow attackers access to all the information stored in your mailbox including other logins and passwords. We recommend you use strong passwords and two-factor authentication if possible.


















Spam in Q1 2014