
Kaspersky Anti-Spam protects users all over the world. Our Anti-Spam Lab processes more than one million messages caught in our traps every day. Content filtering, technical header analysis, unique graphical signatures and cloud technologies all combine to ensure users are protected, with our analysts creating new signatures 24/7.
Q1 2012 summary
The quarter in figures
- In Q1 of 2012, the share of spam in mail traffic was down 3 percentage points compared to the previous quarter, averaging 76.6%.
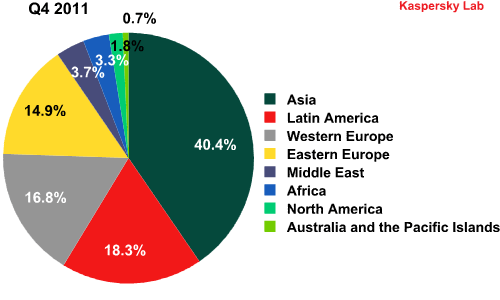
- Asia (44%) and Latin America (21%) remain the most prominent sources of spam.
- The proportion of emails with malicious attachments grew by 0.1 percentage points compared to Q4 2011 and averaged 3.3%
- The share of phishing emails averaged 0.02% of all mail traffic.
Holiday spam
The first quarter of the year was packed with holidays and, of course, spammers tried to make the most of it. Be it Valentine’s Day, International Women’s Day, St. Patrick’s Day or Easter – it seems there’s no holiday that won’t get a spammer working overtime.
In most cases, “holiday” spam was limited to themed advertisements for medications, fake designer goods and so on that aimed to persuade users they really needed those particular goods as holiday presents. It was mostly partner spam, which becomes especially active in the run-up to holidays – particularly, for example, partner programs offering flowers.
Political spam on Runet
As expected, in Q1 2012 spammers continued to spread political spam on the Russian Internet. As was the case in the previous quarter most of it was emails of an extremist nature. There was also political spam distributed on behalf of the Communist party (though it is never entirely clear whether these mailings are genuine or fake).
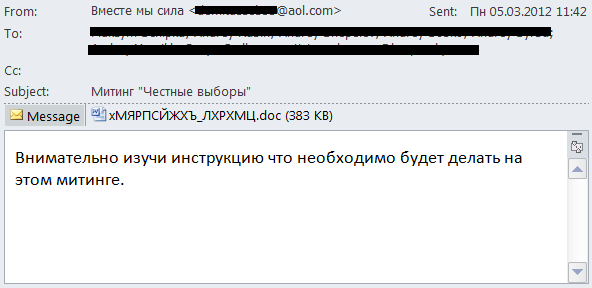
However, there were other types of political spam. For example, one mass mailing invited recipients to read instructions on how to behave at demonstrations. The message included an attached .doc file which started running macros while it opened. As a result users ended up with a Trojan program designed to disable the Windows OS on their computer.
We cannot say for sure if the fraudsters exploited the meeting as a popular theme or whether it was a targeted attack on opposition-minded users. However, this malicious program was not typical of commercial malware – it did not steal passwords, it did not upload bots, etc. Its only task was to disable the infected computer.
Spammer methods and tricks
Malicious mass mailings
Spammers who specialize in spreading malware are especially creative in the sphere of social engineering. Apart from attempts to grab the attention of political activists, we registered some other scams.
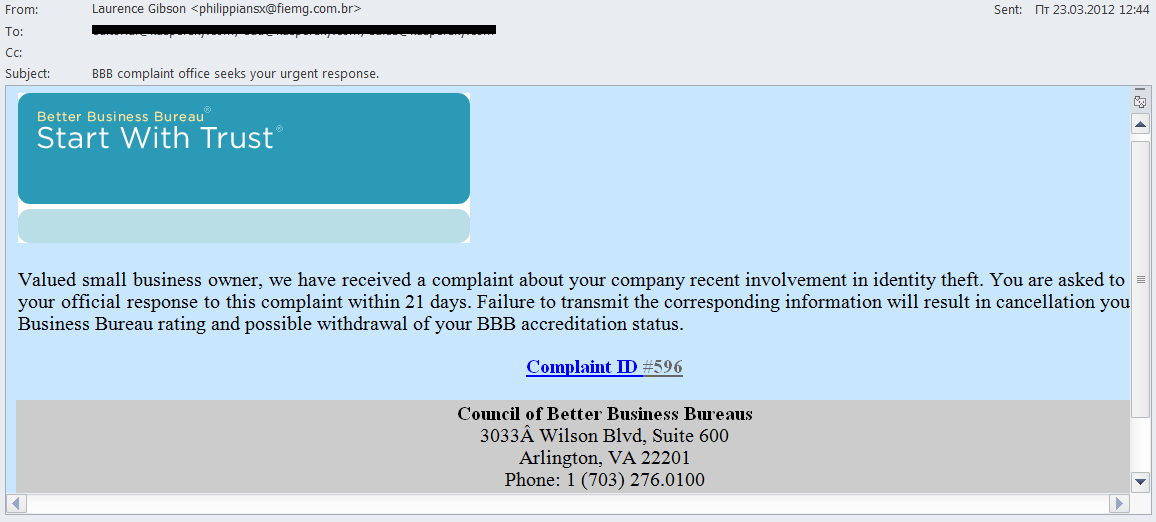
A mass mailing containing fake notifications from NACHA was followed by messages from the Better Business Bureau (BBB), a privately held company which provides consumers and businesses in the US and Canada with information about companies including comments, complaints, statistical data, ratings, etc. The info is supposed to help people decide whether to purchase or invest.
The mass mailing mainly targeted small and middle-size businesses. The email informed the company that a complaint had allegedly been received by the bureau. Then the fraudsters applied a classic method of intimidation – if the company did not officially respond to the complaint, its BBB rating would be at risk. In fact, when the user clicked the link he entered a hacked site with a built-in script which redirected him to the malicious site containing the notorious BlackHole exploit pack.
A similar scheme was used for
another mass mailing that imitated a message from an airline. The user was invited to check-in online to a US Airways flight.
The link in the email led the user to a site containing a script which redirected him to a malicious site with the aforementioned BlackHole exploit pack. If the exploits managed to find a vulnerable program on the user’s computer, a ZeuS/Zbot modification was installed on the machine.
Other malicious mass mailings imitated financial news, job offers, bank notifications and information from social networking sites, etc.
Computer fraud
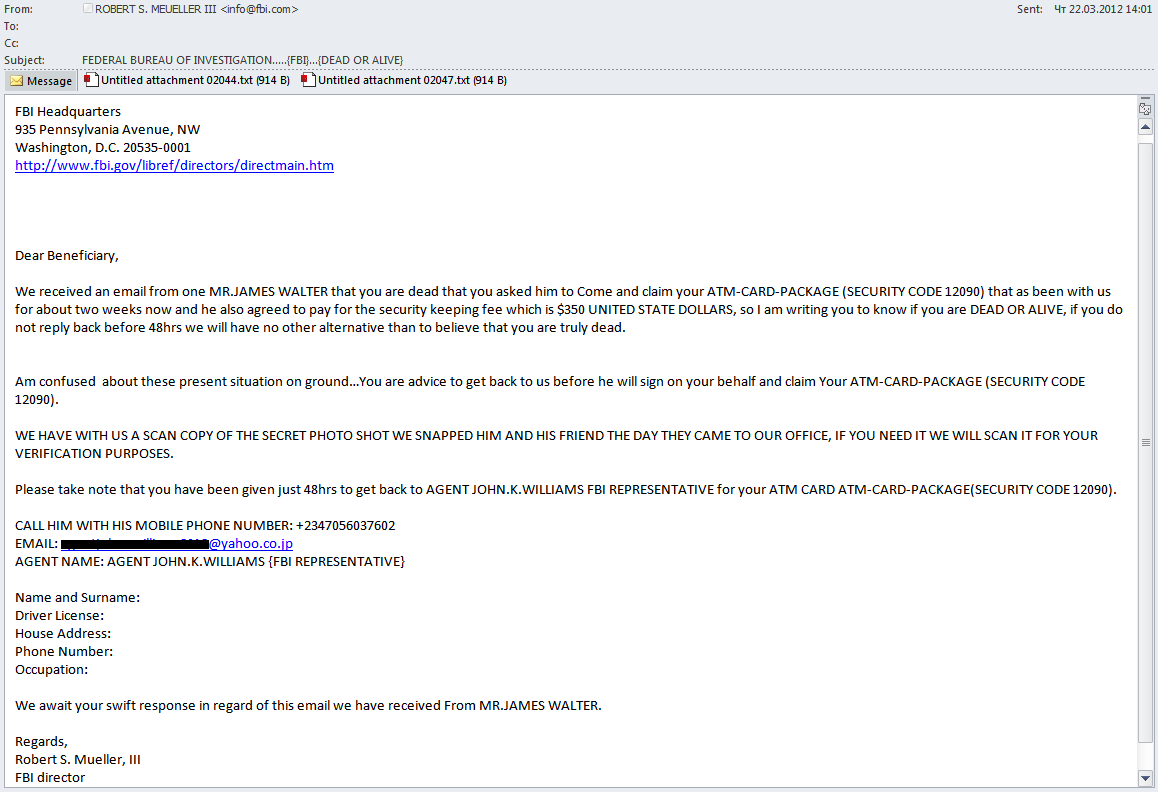
In Q1 2012 the fraudsters also gave way to their imagination. “Nigerian” spammers again promised users millions of dollars, this time from the late Gaddafi. They also posed as an FBI director trying to verify users’ personal details.
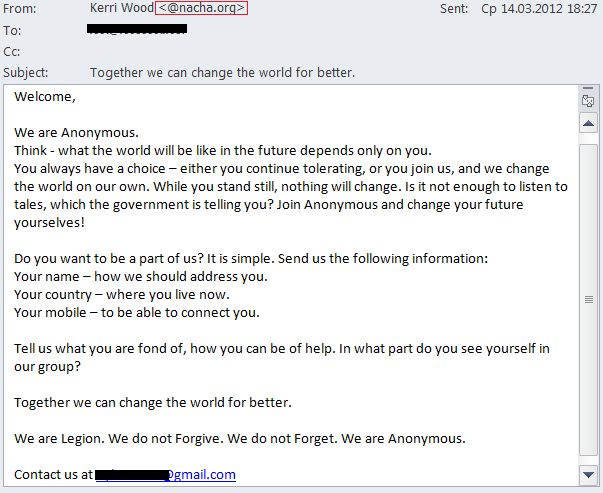
We were especially interested in a mass mailing allegedly sent on behalf of Anonymous. The pseudo-Anonymous spread this email designed in the style of the famous hacker group, using phrases typical of the “original”. Their message encouraged recipients to support their protest against the actions of various governments. To show support, users only had to send their name, country and mobile phone number to the address indicated in the email.
Here the fraudsters are playing on the popularity of the hacker group. Their request to send them your name and the phone number may seem harmless enough, but they can exploit this information at will, for example, subscribing the phone owner to a paid service.
Noticeably, the ‘From’ field in the mailing contained the Nacha domain. It is unlikely that the fraudsters really wanted to associate their mailing with the activity of this organization. More likely the people who sent these emails had previously distributed malicious emails imitating news from Nacha and simply forgot to change the fake ‘From’ field in the template issued to the bots.
Statistical summary
The proportion of spam and the closure of botnets
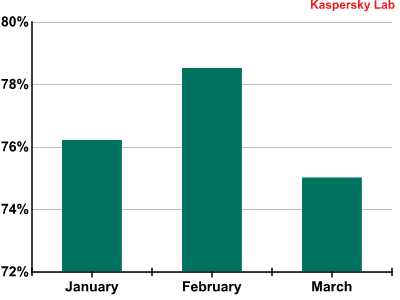
In Q1 of 2012 the level of spam in mail traffic fell 3 percentage points compared to Q4 2011 and averaged 76.6%.
Proportion of spam in mail traffic in Q1 2012
The drop in the percentage of junk emails was in no little part down to the combined efforts of Kaspersky Lab and the CrowdStrike Intelligence Team, HoneyNet Project and Dell SecureWorks research groups. Their work resulted in the neutralization of the second version of the Hlux/Kelihos peering botnet. According to our data, the botnet included over 100,000 infected computers. Hlux was first noticed in December 2010, shortly after the closure of big botnets such as Pushdo/Cutwail and Bredolab. In September 2011, its first modification was deactivated, but the fraudsters quickly created a new version with extended functionality and even before the month was out the bot reappeared online. In March 2012 this version was neutralized.
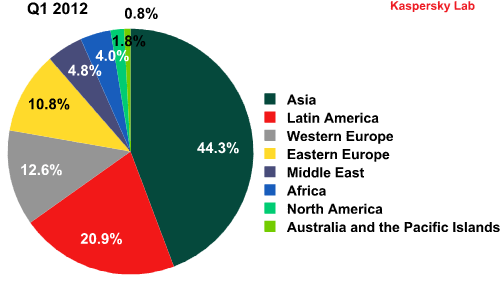
The geography of spam
2011’s major trend continued in Q1 2012: the share of spam coming from Asia (+3.83 percentage points) and Latin America (+2.66 percentage points) is increasing, albeit slowly. Africa’s (+0.67 percentage points) and the Middle East’s (+1.09 percentage points) contribution is also growing. Although the volume of spam originating from the latter two regions is not very big yet the growth dynamic is clear. The proportion of spam distributed from Africa and the Middle East increased by 20 and 29.6 percentage points respectively compared with Q4 2011.
Sources of spam by region in Q4 2011 and Q1 2012
The shares of Western and Eastern Europe continue to decrease and in Q1 2012 amounted to 23.43% of the total volume of global spam (-8.35 percentage points). After the closure of Hlux we can expect further changes in the geographical distribution of spam sources.
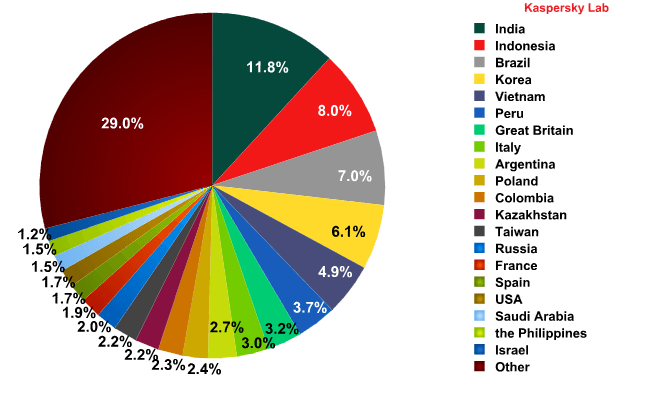
Sources of spam by country
In Q1 2012 India remained the most active spam distributor. Next came Indonesia and Brazil. The shares of the countries in the Top 20 did not change significantly, with all fluctuations within a range of 1 percentage point.
Sources of spam by country in Q1 2012
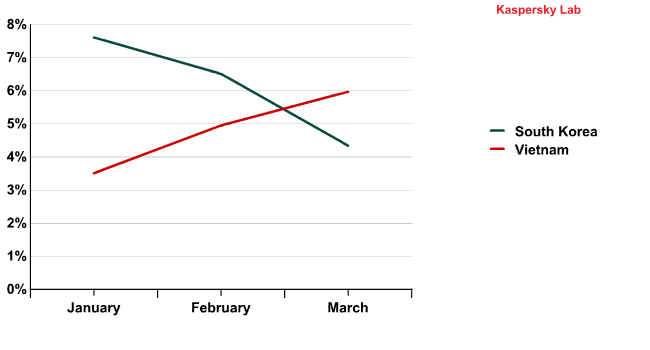
Interestingly, although countries in the same region usually have similar peaks and troughs in spam distribution, each Asian country seems to have its own dynamics. For example, the trends demonstrated by South Korea and Vietnam – both in the top five distributors – were almost opposite.
The dynamics of spam distribution from South Korea and Vietnam (Q1 2012)
This suggests that infected computers in these countries are hooked up to different botnets. It is not surprising: at the moment Asia is an attractive region for botmasters, and completely different botnets may have computers from the region in their networks.
Emails with malicious attachments
Proportion of emails with malicious attachments
In Q1 of 2012 the average proportion of emails with malicious attachments increased by 0.1 percentage points, reaching 3.3%. The graph below shows the distribution of malicious spam by month.
The percentage of spam with malicious attachments in Q1 2012
As can be seen from the graph, there was a peak in January – over 4% of all emails contained malicious attachments. In February and March the proportion of malicious spam accounted for 2.8%.
January’s high can be explained by the long New Year holidays in Russia and the low level of business activity in the other three weeks of January. Obviously, due to a shortage of orders many botmasters started spreading spam messages for partner programs, giving preference to pharmaceutical spam and malicious code.
Perhaps the decrease in the amount of malicious code in mail traffic recorded in February and March was temporary and we can assume that in the second quarter the share of malicious mailings will increase. It is worth recalling that in order to distribute malware, spammers use both malicious attachments and malicious links. Thus, the decrease in the amount of malicious attachments in mail traffic does not always mean there’s a decline in the share of malicious mailings per se.
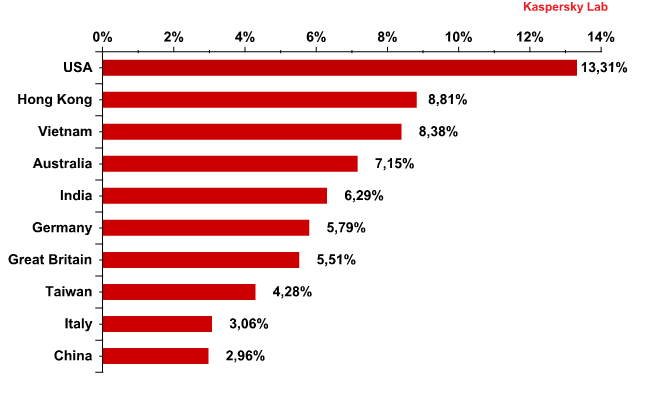
Email antivirus detection levels for different countries
Email antivirus detection rates for different countries in the first quarter of 2012 were as follows:
Email antivirus detection levels in Q1 2012
The amount of email antivirus detections registered on the territory of last year’s leader, Russia, accounted for just 2%, keeping it out of the Top 10 in Q1 2012. The USA topped the rating although there was little change in the level of antivirus detections there – up by 0.5 percentage points. Hong Kong doubled its previous result to climb to second in the rating.
In our annual spam report for 2011 we mentioned that throughout the year email antivirus detections in the USA and India operated in inverse cycles: the more malicious emails that were detected in the USA, the fewer were recorded in India, and vice-versa. In Q1 2012, however, this link was not evident.
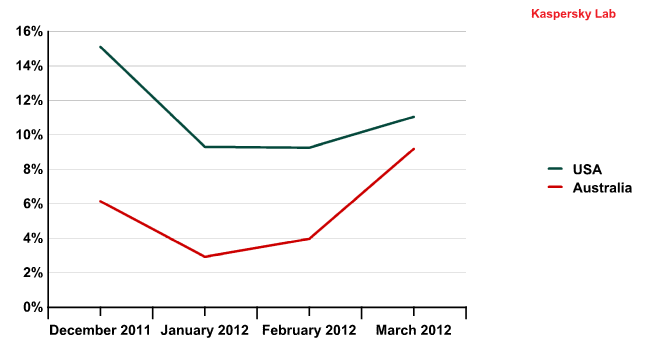
In our spam report for Q3 2011 we noted that the detection rates in the USA and Australia were more or less synchronous, which may be down to the similar Internet landscape of these countries. This trend continued in Q1 2012.
Email antivirus detection activity in the US and Australia in December 2011 – March 2012
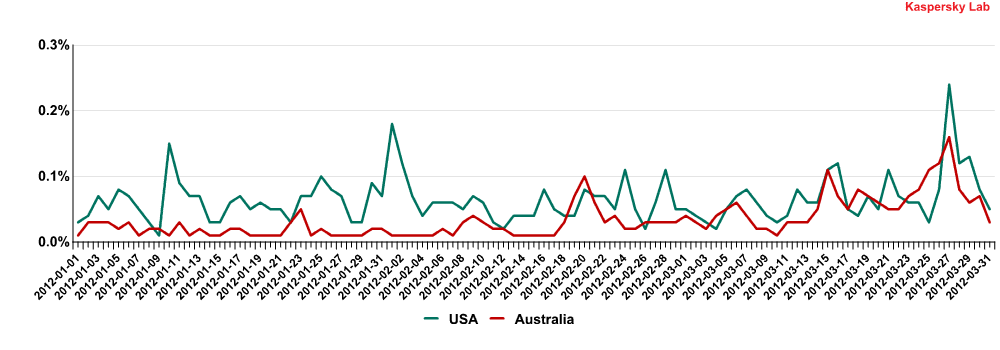
A more detailed analysis revealed a close correlation between local peaks in email antivirus detections in these countries throughout March.
Email antivirus detection activity in the US and Australia by day (March 2012)
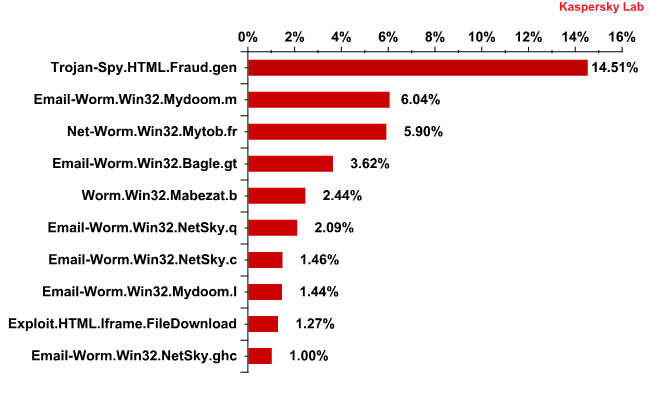
The Top 10 malicious programs distributed via mail traffic
Trojan-Spy.HTML.Fraud.gen remained the most widely-distributed malicious program in Q1 2012 accounting for 14% of all detections. This Trojan uses spoofing technology and imitates an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password. The data entered on the page is sent to cybercriminals.
The Top 10 malicious programs distributed via mail traffic in Q1 2012
Email-Worm.Win32.Mydoom.m once again came second. This mail worm as well the similar Mydoom.l (in 8th place) have only two functions – to harvest email addresses and send copies of themselves to these addresses. The three representatives of the Email-Worm.Win32.NetSky family occupying sixth, seventh and ninth places respectively have the same functions, while Bagle.gt, yet another mail worm in fourth place in the rating, in addition to the usual functions also downloads malicious programs from the Internet.
Noticeably, the distribution of mail worms is completely uncontrolled in that their mechanism is not connected to any commands from their “masters”. The families presented in the rating have been spreading via mail traffic for several years and most likely became unprofitable for their creators long ago. In addition to the phishing program Trojan-Spy.HTML.Fraud.gen, cybercriminals are distributing new modifications of various Trojan downloaders or Trojan droppers.
Very often malicious mailings pass through so quickly that the appropriate entries have no time to appear in antivirus databases. In this case, the Email Anti-Virus blocks the malicious attachment with the help of proactive methods. In the first quarter of 2012 11% of all programs blocked by the Email Anti-Virus were detected proactively.
Additionally, it is important to remember that in order to spread malware, spammers use both malicious attachments and malicious links.
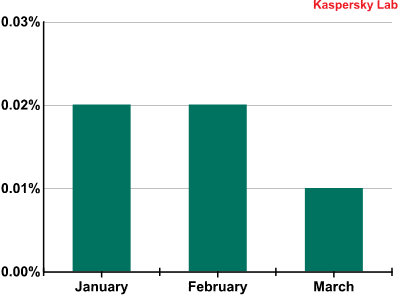
Phishing
In the first quarter of 2012 the volume of phishing emails decreased slightly and accounted for just 0.02% of all mail traffic.
The percentage of phishing emails in mail traffic during Q1 2012
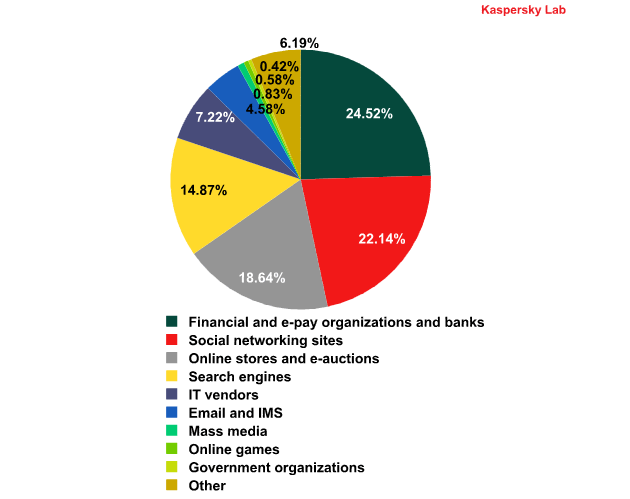
This year saw the start of Kaspersky Lab’s new listing of the top 100 organizations targeted by phishers, grouped by category. More detailed information about each category is available
here.
Top 100 organizations, by sphere of activity, targeted by phishers in Q1 2012 (based on anti-phishing component detections)
The rating is based on our anti-phishing component detections activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In Q1 2012 the distribution of phishing attacks by organization was rather stable. Among noticeable shifts was the increase in the number of attacks on Amazon in January. In the first month of the year the Online stores and e-auctions category occupied second position in the rating. However, in February it was replaced by the Social networking sites category, which saw its position bolstered by a surge of attacks on Facebook. That site has been the single most targeted site for the past two months.
According to KSN, phishing links are clicked from mail clients in about 70% of cases, which means email remains the main distribution channel for phishing links.
Conclusion
The amount of spam in mail traffic is decreasing which is encouraging. This is largely due to active anti-botnet campaigns from different independent organizations. However, experience shows merely closing botnets is not enough to effectively combat threats. Joint efforts in cooperation with the law enforcement agencies, as well as investigation and legal procedures are required. Work in this direction is underway. For example, several financial institutions in the United States, together with Microsoft, filed a lawsuit against the owners of the ZeuS botnet accusing them of violating various laws from CAN-SPAM (the U.S. law against spam) to the RICO Act – Racketeer-Influenced and Corrupt Organizations Act.
The geography of spam remained unchanged compared with the previous quarter. However, we should not expect it to remain stable: as a rule, the closure of botnets drastically changes the geography of spam sources, as cybercriminals try to organize new botnets in safer (and more profitable) places.
Although the percentage of malicious attachments in spam has decreased, it still remains high. Moreover, many malicious emails contain links to sites with exploits that are used in drive-by attacks, rather than attachments. Such links use various redirects to sites containing exploit-packs – sets of exploits designed to find vulnerabilities in popular applications such as Java, Flash Player and Adobe Reader installed on a user’s computer. The people behind such spam mailings are usually very creative, making use of various social engineering methods.
At the moment it can be dangerous both to click the link in a spam message and to open an attached file (even if it’s just a text document). In addition, some modern malicious programs are designed so that is dangerous even to open a spam email itself. We once again recommend users to update their software and delete spam messages without opening them.























Spam in Q1 2012