
Spam in the spotlight
In November we saw a large number of spam messages offering seasonal and full-time jobs. This comes as a surprise for this time of the year: the labor market is experiencing a “low season” as the end of the fiscal year approaches. This type of spam often didn’t contain any specific information about the potential employee or the vacancies offered. Quite a lot of the November spam was related to the winter holidays and planning the coming Christmas and New Year holidays. Besides, there was holiday spam related to Thanksgiving Day and Remembrance/Veterans Day. And lastly, the spammers continued their regular practice of sending spam related to tragic events, and sending fraudulent messages asking for monetary aid to help the victims of the typhoon in the Philippines.
The holidays continue
In November, spammers, on behalf of small and medium businesses, vigorously promoted discounts on merchandise and services associated with Veterans Day, commemorated on 11 November in the USA, and tried to attract attention with regular references to sales and opportunities to save money. For example, in the messages advertising car dealership sales, the promoted discounts were presented as a tribute to US war veterans.
Neither did spammers fail to pay homage to Thanksgiving Day, popularly commemorated in the USA and some other countries on the last Thursday of November: this date was also used to advertise merchandise and services. Some spam messages attracted recipients’ attention not only by using the name of the holiday in the subject field but also with the vivid design including a picture of a turkey – the main symbol of the Thanksgiving Day – and some interesting facts about the bird. Spam messages sent in November advertising drugs and massive discounts on electronic devices were also associated with Thanksgiving Day.
The message contents and topics were not always related to the content of the page which the user was directed to after clicking the ad link. For example, the link in one spam message we detected led to an MP3 file which was allegedly designed to help the user to survive a “turkey apocalypse”; in fact, the user landed on a site advertising male potency pills.
The preparations for the festive season are gaining momentum, and the amount of New Year and Christmas spam are rising accordingly. As Christmas approaches, small and medium-sized businesses offer a wide diversity of goods and services – from Christmas tours to mail stamping equipment. Alongside adverts for traditional cards, we have also seen offers to design video greeting cards that include a corporate logo and greetings from the client company. The spammers also remembered all those children who wait for presents and a letter from Santa Clause; one of the spam mailings that we discovered advertised online orders for such letters.
Please donate to cybercriminals
It is very common to see spammers exploiting tragic high-profile events to make money. Every now and then we come across spam messages that exploit news about terrorist attacks, natural and manmade disasters to cajole money from users. The fraudsters often send messages in the name of various humanitarian organizations or say that they are cooperating with them to render assistance to the victims. In November 2013 the fraudsters sent so-called Nigerian letters in the name of the Red Cross and asked recipients to donate money to help the victims of the recent typhoon in the Philippines.
To avoid raising suspicions, the fraudsters did not ask for a specific sum of money this time, but said that even a small amount would be a huge contribution. The letter was sent from a fake Red Cross address, and included contact information of a fake Red Cross representative – a phone number and an email address registered in a completely different domain. It should also be noted that it is very rare for fraudulent spam message to include a link to an HTML page with details about the incident and the donation details. However, the November messages provided a link leading to a page with videos of the disaster and money transfer details. To convince the recipient of their good intentions, the fraudsters added a link to the official Red Cross website.
Illusive vacancies
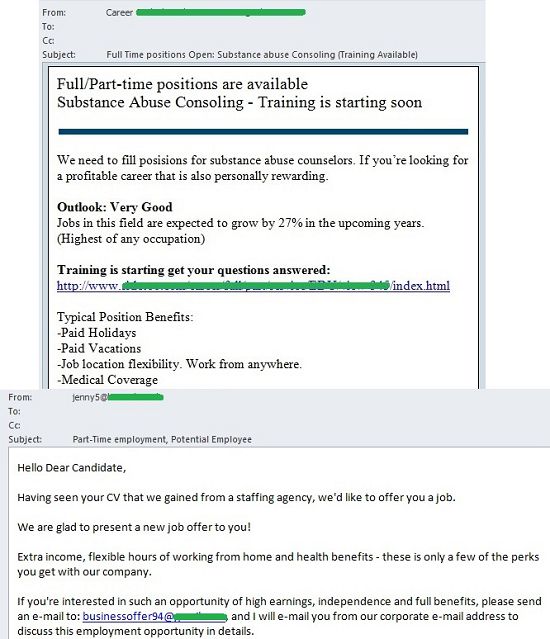
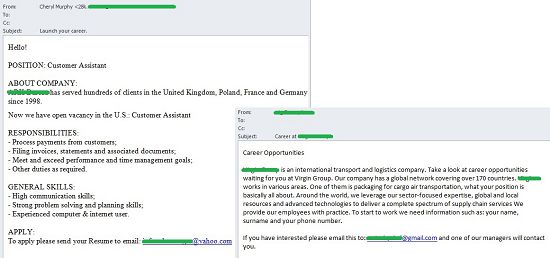
Typically, late autumn and early winter is a slack period in the labor market. At this time companies are looking to balance the books before the end of the year and making plans for the coming year, so they are not as active in searching for new employees. However, this November we saw a large number of spam messages with job offers. These were anything but official vacancy notifications from renowned online recruitment agencies, however.
These were typically anonymous letters which informed the recipient about open vacancies. The job offers were very attractive, and the potential employee could choose between full and part-time employment. However, the letter often did not include a description of the vacancy itself; to find out the details, the user had to write to a specified email address that was different from the sender’s address. The recipient was asked to send his/her response letter and CV to an address that changed from letter to letter, while the contents of the messages remained unchanged.
Some of these messages, however, did in fact contain the name of a specific company that was looking to recruit new employees and a short description of its core activities. Some of the senders of such letters claimed that they found out the recipient’s personal information from a resume provided by an unnamed HR agency. The message also included main requirements and a proposed compensation package.
Winter holidays
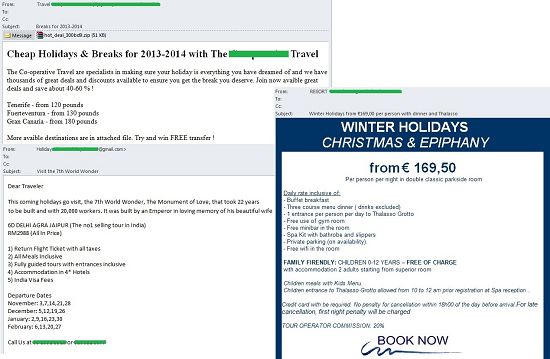
The Christmas and New Year holidays are approaching, and many people try to take their vacations at this time. This the reason behind the usual surge in spam messages in late autumn, advertising all kinds of Christmas trips and tours. This November was no exception.
Along with adverts for last-minute tours to beach destinations that are traditionally popular at this time of the year, we observed a lot of offers for classical winter holiday destinations, including snowboarding and snowmobile tours, mountain skiing, excursions and ski tours through forests.
Geographical distribution of spam sources
Proportion of spam in email traffic
During the first three weeks of November the proportion of spam in all email traffic increased gradually; however, it dropped towards the end of the month, producing a monthly average of 72.5%.
Sources of spam
In November 2013, there was no significant change to the list of countries where spam originates. China, which generated 23.3% of global spam, came out on top once again, with its share increasing by 2 percentage points in November. The USA ended November in second place, accounting for 18% of global spam, followed by South Korea (14.5%) and Taiwan (6.7%). Russia (5.4%), whose share grew 1.4 points, remained in fifth place.
There was a small drop (-1 percentage point) in Ukraine’s 2.9% contribution to global spam. In November, Ukraine fell one place to 8th. Canada’s share also dropped slightly (-0.4 percentage points), which resulted in it dropping out of the Top 10 and Japan (+0.9 points) taking its place in 9th.
The Top 10 was rounded off by Romania (1.6%) which moved up three places after its share rose by 0.2 percentage points.
South Korea was the leading source of spam received in Europe in November, accounting for 56% of all spam in the region. For South Korea this was an increase of 4.7 percentage points compared to October. The second biggest source was Taiwan (6.4%) whose share fell by 1 percentage point. In third place was the USA (5.5%) whose share increased by 1.4 percentage points.
Hong Kong’s contribution to European spam increased slightly (+0.4 percentage points), moving it up from 6th to 4th place in the ranking. Singapore (+0.6 percentage points) also moved up three places to 8th.
By contrast, the share contributed to European spam by Russia (2.5%) dropped 2.7 percentage points of and saw it drop from 3rd to 5th place. Similarly, Ukraine’s share (2.3%) fell 1.2 percentage points, leaving it in 7th place. Both Kazakhstan (-0.6 percentage points) and Italy (-0.8 percentage points) exited the Top 10.
Tenth place in November’s rating was taken by Romania (1.3%). Romania’s contribution to overall European spam has changed only slightly (-0.1 percentage points).
There has been no change to the global balance between spam sources by region. In November, the leading regions for spam generation were, as before, Asia (+2.6 percentage points), North America (+0.5 percentage points) and Eastern Europe (-2.3 percentage points). Next came Western Europe (-0.7 percentage points) and Latin America (-0.02 percentage points).
Malicious attachments in email
In November, the Top 10 malicious programs that spread via email looked like this:
Trojan-Spy.html.Fraud.gen continued to occupy the top position in the ranking. This malware takes the form of a fake data entry HTML page, with the data entered by the user being sent directly to the attackers. Trojan-Spy.html.Fraud.gen is distributed via email, disguised as notifications from major commercial organizations, banks, online stores, etc.
The infamous Bublik malware family did not yield ground in November, occupying four positions (2nd, 3rd, 8th and 10th) in our ranking again. Each of the four Bublik malicious programs on November’s Top 10 are run-of-the-mill Trojan downloaders which download malicious files to user machines and then launch the files that are downloaded.
Fourth place is taken by Email-Worm.Win32.Bagle.gt, a virus-worm distributed in email attachments. Upon infecting a computer, it sends itself to all email addresses found on it. Its main function is to download files from the Internet and launch them without the user’s knowledge.
In 5th and 6th places are Trojan.Win32.Buzus.ofhx and Trojan-Spy.Win32.Zbot.qsec -programs used by cybercriminals to steal a variety of bank information from user computers, such as online banking credentials. As a rule, this type of malware does not manifest its presence in the system in any way, making it much more difficult to detect on infected machines not protected by antivirus software. Moreover, this malware family uses rootkit technologies for self-defense, masking their executable files and processes.
The entry in 7th place – Trojan-Ransom.Win32.Gimemo.blyq – is a spy program that steals browser cookies, as well as passwords for FTP and email clients, subsequently sending the stolen data to cybercriminals.
In November, the UK ranked top (12.3%) based on the number of mail antivirus detections triggered there – 2.4 percentage points higher than in the previous month, pushing back Germany (11.2%) and the USA (11.2%) to 2nd and 3rd respectively.
For other countries on the list, the proportion of detections did not change significantly. It is perhaps worth mentioning Qatar (1.5%), which was a newcomer to the TOP 20 countries in November. The proportion of mail antivirus detections in Russia was down to 1.9% in November.
Special features of malicious spam
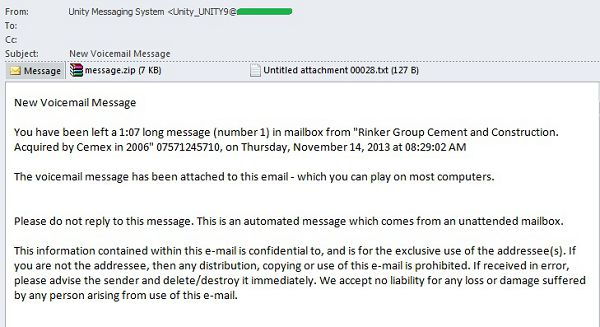
In November, spammers actively sent malware disguised as voicemail messages. In most cases, the text of the messages detected by us followed the same template: “You have been left a XX minutes XX seconds long message in mailbox from company/user N on date, time. The voice message has been attached to this email – which you can play on most computers.” The voice message was supposedly packed in a ZIP archive, usually named message.zip, which in fact contained malware.
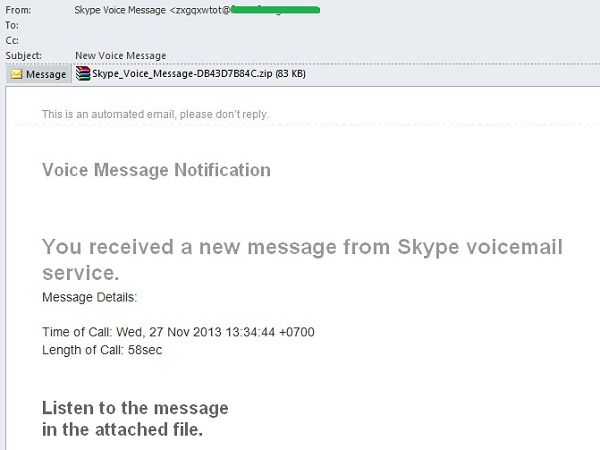
The same trick – using voicemail notifications as a disguise – was used to send spam on behalf of Skype, a major messaging and video calling service. In this case, Skype Voice Message was used as the sender name, but the sender address had nothing to do with the popular service and seemed to be an automatically generated string of characters. Message details also listed the time and date, as well as the length of a supposed call. The message was meant to be listened to by opening a ZIP archive attached to the message, namedSkype_Voice_Message-DB43D7B84C.zip. In reality, the archive contained malware detected by Kaspersky Lab as Trojan-PSW.Win32.Tepfer.sjsm. This is a spyware program, which steals browser cookies, as well as passwords for FTP and email clients, subsequently sending the stolen data to its cybercriminal owners.
Phishing
In November, the ranking of organizations attacked by phishers did not change significantly.
Categories of organizations targeted by phishers are ranked based on detections registered by Kaspersky Lab’s anti-phishing component each time a user attempts to follow a phishing link, regardless of whether or not the link is in a spam email, or on a website.
As in the previous month, Social Networking Sites (26.9%), whose share fell by 1.3 percentage points, leads the top three categories, followed by Email and Instant Messaging Services (19.2%) and Search Engines (16.5%), both with slightly higher percentage figures compared to October.
Financial and E-pay organizations (16.1%) remained in 4th place, although the proportion of attacks on organizations in this category is increasing. In November, the increase was 0.7 percentage points.
The share of IT Vendors (9.2%) is up by 2.2 percentage points. As a result, this category has risen to 5thplace in the ranking, pushing Telephone and Internet Service Providers, whose share decreased by 2.9 percentage points in November, down to 6th place.
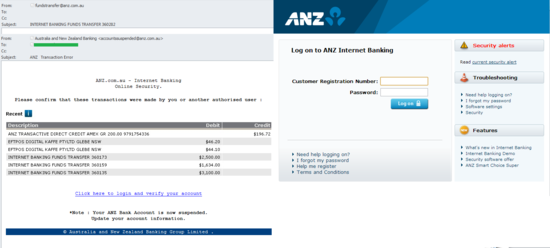
In November, phishers were once again active attacking customers of the Australia and New Zealand Banking Group. Emails in the same mailing had different addresses in the From and Subject fields and different phishing links, but the same content. The recipient was asked to confirm that the transactions listed in the message were performed by that person rather than somebody else. The email included an account authentication link which actually led to a phishing page, the design and contents of which imitated the relevant page of the banking group’s official website. The data entered by the user on the phishing page was of course sent to cybercriminals.
To prevent a fake notification from looking like a traditional scam, in which potential victims are threatened with having their accounts blocked from the very start, this time the phishers placed the warning at the end of the message. Note that this information is easy to miss if one doesn’t read the message carefully. To make the warning look legitimate, the From field included in the company’s official domain name and the message ended with the bank’s auto signature.
Conclusion
The proportion of spam in global email traffic has not changed, amounting to 72.5% in November. The geographical distribution of spam compared to the previous month did not change significantly either.
As we predicted, spammers actively sent holiday-related spam, including images, in connection with the celebration of Christmas and the New Year. They also actively exploited Thanksgiving Day and Veterans Day – holidays that are popular in Western countries – to advertise weight loss and erectile dysfunction drugs, while companies tried to lure new customers with holiday discounts on goods and services. In December, preparation for the forthcoming holidays will be at its most hectic, and the amount of Christmas and New Year spam will also reach its peak.
Despite the quiet time in the labor market, many spam mailings contained offers for potential job applicants across the globe. Because of the approaching holidays and the related vacation season, we have also seen many offers for vacation packages and mountain-skiing trips. We expect this kind of spam to continue being sent after the holidays, probably throughout January.
The series of scam emails exploiting headline-making tragic events continued in November. This time, the spammers tried to defraud people of their money by pretending to be collecting donations for victims of the typhoon in the Philippines.
In November, a significant proportion of messages containing malware constituted fake incoming voicemail notifications. Specifically, cybercriminals targeted Skype, the popular video calling service.
The ranking of organizations targeted by phishers has not changed significantly. The share of social networking sites was smaller than the month before, but the category retained its position at the top of the ranking. As we predicted, the number of attacks on financial institutions continues to grow. In the busy period before the holidays it is worth being especially vigilant when it comes to messages from online stores, booking services as well as banks and e-payment systems. In the weeks before the holidays there’s a surge in the number of purchases and financial operations made over the Internet, which is why scammers send out more phishing messages in the hope that the recipients aren’t as attentive as usual.



























Spam in November 2013