
July in figures
- The percentage of spam in email traffic in July was up only 0.1 percentage points and averaged 71.2%
- The level of phishing decreased by more than half compared with June, and averaged 0.0012%
- Malicious attachments were found in 2.2% of all emails, an increase of 0.4 percentage points compared to the previous month
Spam in the spotlight
Hot topics in spam
In July, we continued to record mass mailings in which spammers exploited interest in the big events of the month. For example, the much-anticipated birth of the Royal baby in Britain and the spy scandal involving Edward Snowden did not go unnoticed by the spammers. Attackers kept with tradition to send out emails with malicious links imitating messages with links to breaking news.
In addition, interest in these events was exploited to draw attention to spam advertising. For example, the excitement around the birth of the Crown Prince was utilized in advertising printing services and advertising equipment. In honor of the event the company offered discounts for roller stands.
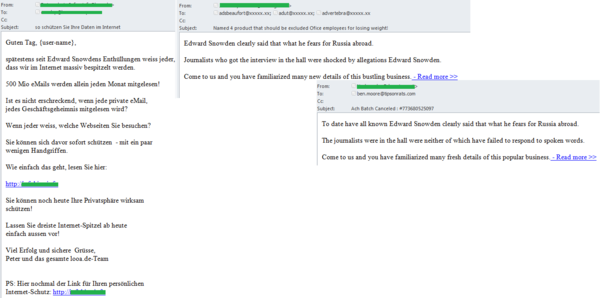
The scandal involving the former U.S. intelligence officer Edward Snowden was used by the spammers to advertise weight loss products. The trick was that these goods were not even mentioned in the theme of the email and the text of the message offered to learn the details of Snowden’s story rather than the methods of losing weight. However the link to the “details” contained in the email led to an advertising page.
A more appropriate use of Edward Snowden’s name was recorded in a German-language mass mailing advertising IT security solutions. The users were urged to buy the advertised product because Snowden’s revelations proved that espionage on the Internet was widespread.
Ramadan
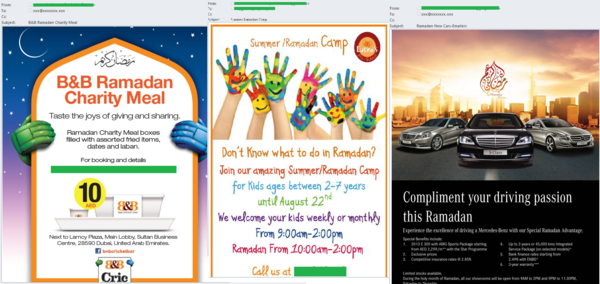
In 2013, the Muslim holy month of Ramadan began in early July. Every year we register mass mailings exploiting this theme. This year was no exception – we received several English-language mass mailings including not only traditional Ramadan advertisements of night restaurants and food but also offering automobiles and summer holidays for children.
New stars of “Nigerian” letters
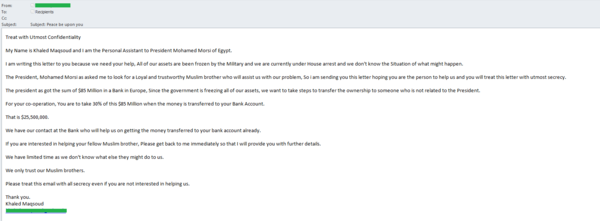
Traditionally the most popular authors of “Nigerian” letters are relatives or associates of famous rich people who are either dead or going through tough times. In July, Egyptian President Mohammed Morsi was overthrown. Within a few days we registered a fraudulent mass mailing exploiting his story.
The email, allegedly written by the former secretary of the ex-President, claimed that all Morsi’s accounts had been frozen, that the former President and his secretary were under house arrest and that Morsi is looking for a Muslim who could transfer the president’s funds from a European bank into his own account. As a reward, of course, a tempting amount of money is offered. However, the traditions of “Nigerian” letters suggest that victims will not only be disappointed when the riches fail to materialize, they are likely to be left out of pocket as the scammers con money from them on some spurious pretext.
A rare type of fraud
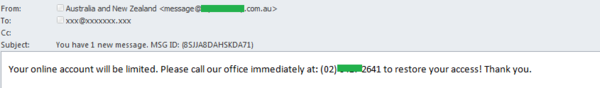
In July, we received an email which utilized seldom seen kind of fraud. The users received notifications allegedly sent from the Australia and New Zealand Banking Group informing him that the access to their accounts had been restricted. To restore access recipients had to call the phone number contained in the email. The risks are obvious: it could be a high-tariff number which will drain money from callers, or it may be an attempt to extort banking information over the phone.
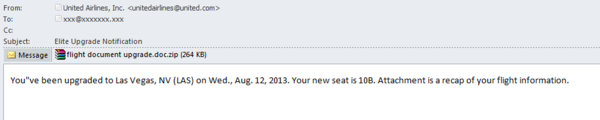
Malicious summer spam
In summer tourist spam is highly popular and we continue to register malicious mailings supposedly sent on behalf of various airlines. In July, it was a fake notification from “United Airlines”. The users were informed that seat numbers on an upcoming flight had been changed and the updated flight information was available in the attached archive “flight document upgrade.doc.zip”. The archive contained an executable file under that name, which is detected by Kaspersky Lab as Backdoor.Win32.Vawtrak.a.
This backdoor is used by the fraudsters to steal passwords stored on browsers as well as passwords for FTP and email clients. This malware also sends screenshots of the user’s desktop and gives cybercriminals full access to the infected computer, allowing the attackers to download and run various files on it.
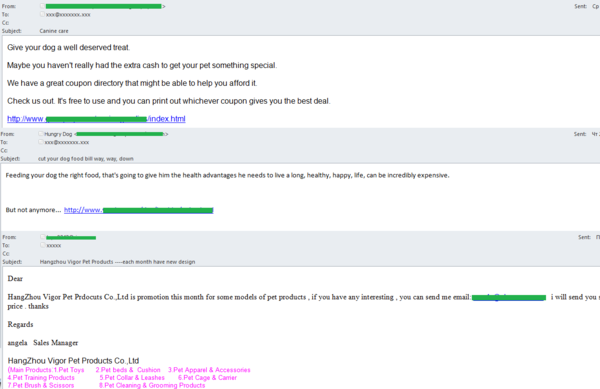
Goods and services for pets
In July, we also recorded mass mailings advertising services and goods for pets. People all over the world treat their pets as family members so the demand for goods and services for them is high. This demand generates offers which are often promoted via spam mailings both Russian and English.
English-language spam mostly advertised pet products and cheap food.
The geographical distribution of spam sources
In July there was no significant change among the leading sources of worldwide spam.
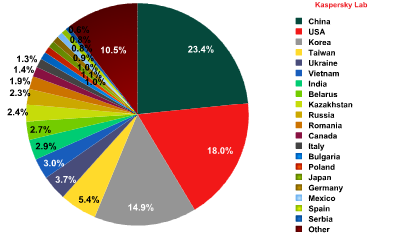
Sources of spam around the world by country
China remained in 1st place with 23.4% of all distributed spam, a slight decline from the previous month (23.9%). The USA came second, contributing 18% to the world spam flow, up 0.8 percentage compared to June. South Korea was 3rd after a small increase (+0.4 percentage points) averaging 14.9% in July. Totally, these three leaders produced over one third of the world spam.
In July, India moved up from 10th to 7th position (3%) having increased its share by 0.4 percentage points. Japan reduced its contribution by the factor of nearly three – from 2.7% to 0.96% (-1.74 percentage points) which dropped this country to 16th position from 9th back in June. Russia re-entered the Top 10 with 2.3% of spam originating from there.
Noticeably, Romania’s share grew by 0.6 percentage points averaging 1.9% and climbing from 14th to 11th place in the rating.
In July, the Top 20 sources of spam sent to European users looked like this:
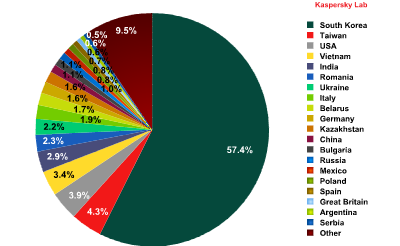
Sources of spam in Europe, by country
In July, there was little change among the leaders in this rating. South Korea remained the leading source of spam sent to European users (57.4%): its share grew by 2.1 percentage points. The growth trend may remain in the coming month. Taiwan (4.3%) and the US (4%) came 2nd and 3rd respectively.
Italy (1.9%) fell from 2nd place to 8th: in July, this country produced 4.8 percentage points less spam compared with the previous month.
Germany was back on the list: the contribution of 1.6% of spam sent to European users moved it to 10th position in July’s rating.
Asia (55.2%) remained the leading source of spam by region although its share decreased by 2.1 percentage points from June. As in the previous month, the Top 3 also included North America (19.4%) and Eastern Europe (14%): the amount of spam originated from these countries grew by 0.7 and 1.1 percentage points respectively.
Malicious attachments in email
In July, malicious attachments were detected in 2.2% of emails, an increase of 0.4 percentage points from June.
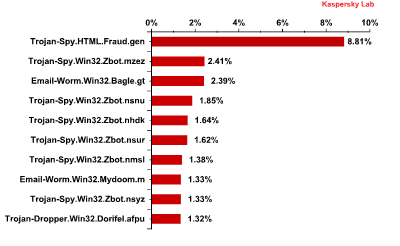
Top 10 malicious programs spread via email in July 2013
In July, Trojan-Spy.html.Fraud.gen remained the most widespread malicious program (+2.9 percentage points). This malicious program appears in the form of HTML pages which imitate the registration forms of well-known banks or e-pay systems and are used by phishers to steal user credentials for online banking systems.
Six out of ten positions in the rating were occupied by representatives of the ZeuS/Zbot family. This is one of the most popular Trojan-spies and its modifications have been spreading in large numbers via email over the last few years. This Trojan was designed to steal users’ confidential information including their credit card credentials.
Fraudsters most often use Zbot in fake notifications sent allegedly by banks, online stores, social networking sites or popular delivery services. These notifications are designed to lure the recipient into opening the malicious attachment.
Zbot family modifications accounted for 23.4% of all malicious programs distributed via email in July 2013
Email-Worm.Win32.Bagle.gt. came 3rd, dropping one position from the previous month (-0.1 percentage points). Like most mail worms it self-proliferates to addresses in the victim’s address book. It can also contact a command center and download other malicious programs onto a user’s computer.
Email-Worm.Win32.Mydoom.m (+0.14 percentage points) was in 8th position. In addition to self-proliferation it sends hidden search requests to search engines such as Google, Yahoo, Altavista and Lycos. The worm compares the addresses of the sites displayed on the first page of the search results with the addresses which it has downloaded from the fraudsters’ servers. Having found the match, it opens the link on the search engine page thus increasing the site traffic and sites’ ratings in search results.
Trojan-Dropper.Win32.Dorifel.afpu. completed the Top 10. Its main functionality is to carry out commands from a remote server as well as downloading and running other malicious programs.
Interestingly, SMS-Flooder.AndroidOS.Didat.a occupied 15th position . This was the first time a malicious program for Android appeared so far up the ranking. The SMS-Flooder.AndroidOS.Didat.a functionality allows the launch of mass SMS mailings. The growing amounts of malware for Android were expected and are in line with the trend forecasting the future growth of this type of malicious programs.
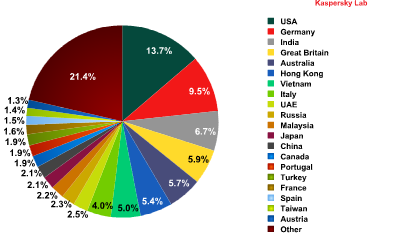
Distribution of email antivirus detections by country
After June’s anomaly the regular leaders regained their positions: the USA was in 1st place (+4.1 percentage points) followed by Germany (+1.7 percentage points) and India (+0.8 percentage points).
The UK moved up from 8th to 4th position pushing Australia into 5th place.
The share of antivirus detections for other countries did no vary significantly.
Phishing
The percentage of phishing emails in the global spam flow decreased by more than half compared with June, accounting for 0.0012%.
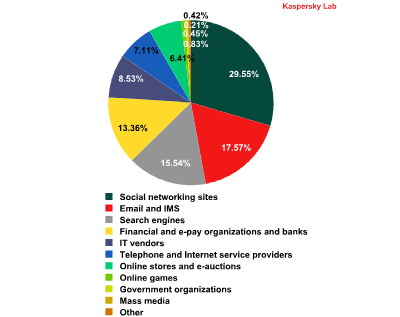
The distribution of the Top 100 organizations targeted by phishers, by category*
This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In July, social networking sites continued to be the most attractive target for phishing attacks although their share fell 1.7 percentage points and averaged 29.6%.
The share of attacks on Email and Instant Messaging Services increased by 4.4 percentage points, pushing this category up from 4th to 2nd place. Search Engines (15.5%) and Financial and E-pay Services (13.3%) both fell one position to 3rd and 4th respectively.
The list of organizations occupying 5th to 8th places remained unchanged: the contribution of IT vendors (8.5%) and Internet providers (7.1%) dropped only 1 percentage point from June while the share of Online Stores (6.4%) and Online games (0.83%) slightly increased.
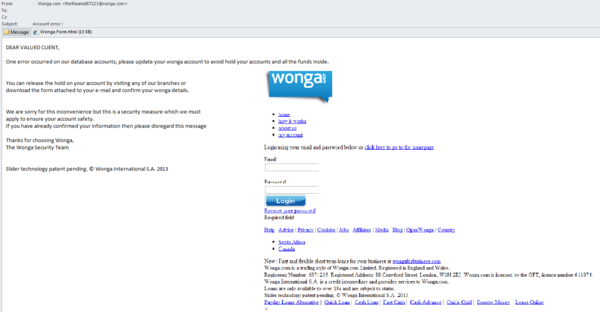
In July, British credit system Wonga was used as the basis of a typical phishing attack. A fake notification sent on behalf of the company informed recipients of a problem with the account database. If users failed to update their accounts they would be blocked. These updates could be made in any company office, or by downloading and filling the attached form and sending it by email. The message contained the enclosed html document where users had to enter their email addresses and the passwords to their accounts. This information gives scammers full access to accounts, and the money within.
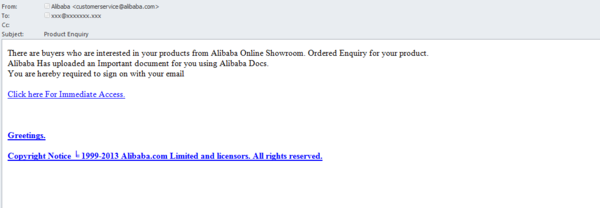
The Alibaba group of online companies became a new target in July. Fake notifications on behalf of the company were sent to the suppliers of goods offered by the online store Alibaba Showroom. The message claimed that customers were interested in the goods on the site. To see an important document, the recipient of the email had to login using the link in the message. In fact the link led to the fake phishing page containing fields for the victim’s email address and password.
Conclusion
In July, the share of spam in mail traffic still exceeded 70%.
Summer is a holiday season when Internet activity falls, both for advertisers and users. As usual, in summer spammers usually have fewer orders. That is why they readily switch to the distribution of partner spam including malicious mailings. In July, the share of malicious attachments in email traffic exceeded 2%. At the same time the most popular malicious program distributed via email were Trojan-spies developed to steal financial information: for example, Zbot family modifications accounted for 23.4% of all malicious programs distributed via email in July 2013.
In July’s Top 20 a malicious program for Android occupied 15th place. This was the first time a malicious program for this platform climbed so high. The number of Android-based smartphones and tablets continues to grow. We expect a further increase in both the number and diversity of malicious programs for Android in email. Most likely, programs distributing text messages will be soon joined by the Trojans developed to steal confidential data. We advise users to act now to protect their desktop computers and mobile devices.
July was rich in hot news. As usual, spammers exploited interest in these events by distributing emails which contained malicious links masked by news reports. The fraudsters did not ignore the world’s most important events either: the email traffic saw the classic “Nigerian letters” written on behalf of the supporters of Mohammed Mursi, the ousted President of Egypt.
The decline in Internet activity in the summer months has probably contributed to the reduction in the level of phishing emails in mail traffic. Among the organizations most often attacked by phishers there was a rise in attention towards Email and Instant Messaging Services, but not as dramatically as in June. Most likely it is temporary and can be explained by the holiday season. In August, the percentage of attacks involving Email and Instant Messaging Services may remain high but in September the situation will probably change.























Spam in July 2013