
Spam in the spotlight
In December, spammers continued to honor the traditions of the season and tried to attract potential customers with a variety of original gift and winter vacation offers, taking advantage of the approaching holidays. As usual, they also advertised seasonal goods and services. The news of Nelson Mandela’s death also inspired new scam emails during the month.
Spammers also actively exploited the financial crisis. Capitalizing on news about the possible consequences of the crisis, spammers tried to make the services advertised seem as attractive as possible, as well as attract potential clients.
New Year spam
In December, when millions of people are looking for and buying presents for their friends and families, the demand for specific goods and services skyrockets. Some companies and individuals resort to spam to attract new customers and increase sales.
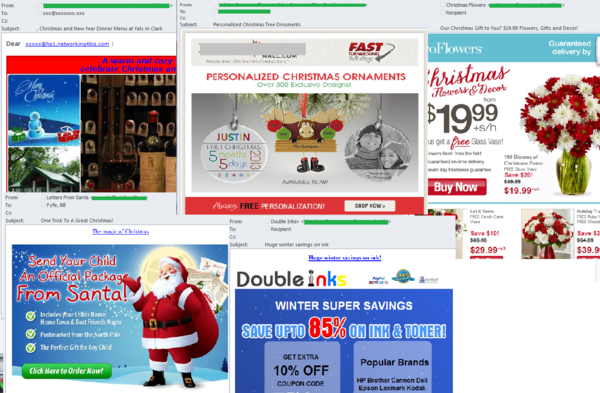
In the run-up to 25 December, offers for goods and services, as well as advertisements for Santa Claus letters for children, made up a significant part of spam traffic. In December, advertisements for discounted flowers, which are usually seen in the run-up to Saint Valentine’s Day and Mother’s Day, were unexpectedly sent in association with Christmas. Spam that advertised personalized inscriptions and images on goods was present as well, but in December the merchandise took the form of Christmas tree ornaments.
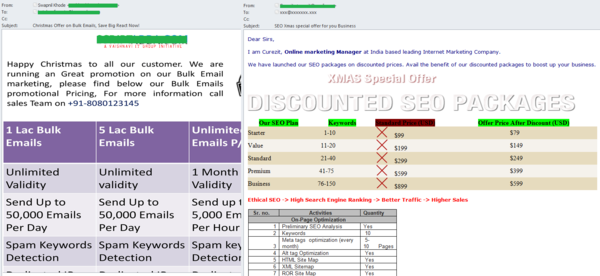
In December, companies offering bulk email marketing and SEO services tried to attract new customers with Christmas discounts.
Nelson Mandela’s ‘Nigerian’ attorney
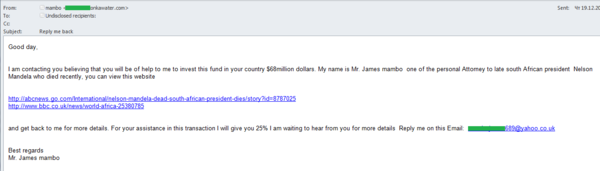
Nelson Mandela, the eighth President of South Africa, died at the age of 95 in early December. This tragic event could not fail to attract scammers, and in the middle of the month we detected the first related ‘Nigerian’ spam mailing. The message, written by phishers on behalf of the late president’s personal attorney, included standard tricks designed to deceive recipients, such as requests to help with investing millions of dollars, promises of abundant rewards and links to well-known news sources. The scammers promised to provide all the details to the victims after receiving a reply to their message. The return address was an account registered with a free email service.
Crisis-related spam
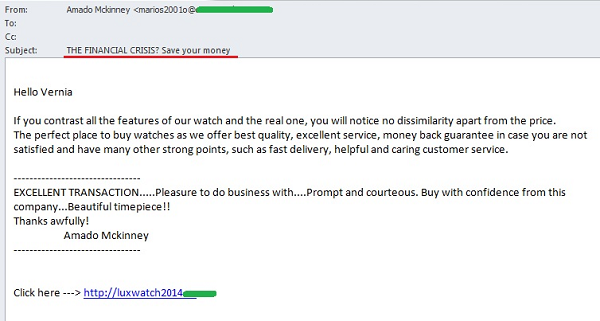
Many countries are experiencing the effects of the unstable economic situation, and the word ‘crisis’ can often be found in the mass media. This was a subject that the authors of numerous spam mailings tried to exploit in December. In messages written in English, the crisis was used as a pretext for offering cut-price luxury watches. Such messages included links to newly-created domains, which typically had the string ‘luxurywatch’ in their names and which redirected visitors to websites of online stores selling replica watches.
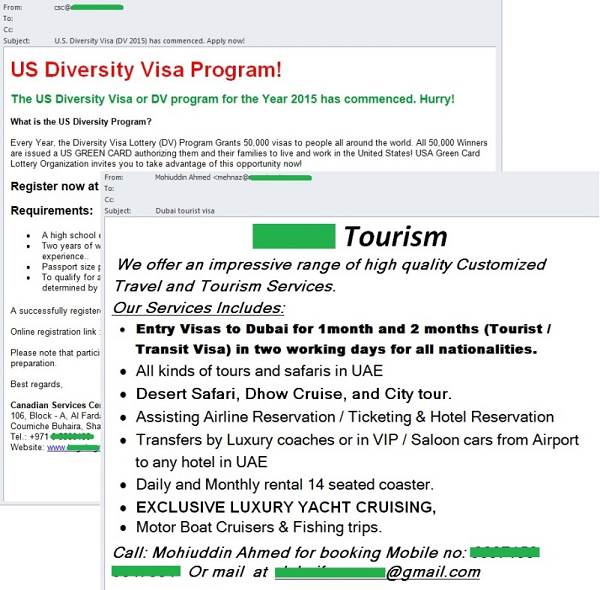
Visas and travel
For those who failed to plan their winter holidays in advance, spammers promised to get visas to any country at short notice without having to visit a consulate in person.
The authors of English-language spam came up with a variety of ways to supposedly simplify visa formalities, such as last-minute purchase of vacation packages or participation in lotteries. It is worth noting that such messages were sent on behalf of organizations that are in no way related to the official consular authorities of any countries.
Geographical distribution of spam sources
Proportion of spam in email traffic
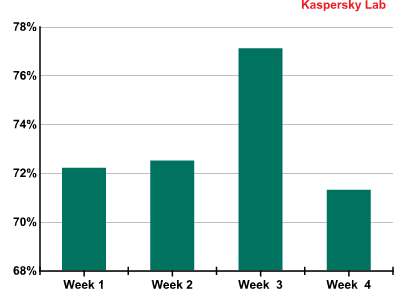
Proportion of spam in email traffic
The highest levels of spam were recorded around mid-December, when spammer activity peaked due to the coming holidays. By the end of the month, we saw spammer activity decrease and the average proportion of spam in email traffic for the whole of December was 73.3%.
Spam sources
Towards the end of the year, the amount of spam sent worldwide and its geographical distribution remained stable. Neither the list of countries where spam originated nor the proportion of unsolicited emails sent from these countries changed significantly. In December 2013, China ranked highest among spam sources (23.1%). It was followed by the United States (19%). South Korea came third (13.9%). In December, these three countries accounted for 56% of all spam sent worldwide.
As in November, fourth position was taken by Taiwan (6.5%), followed by Russia with 5.4%. The Top 10 was rounded off by Romania, which accounted for 1.6% of spam sent worldwide.
The proportion of spam sent from Canada (0.8%) was half of that in November, pushing the country down four positions to 14th place.
The largest increase in the proportion of spam was seen in Spain (0.7%) and Israel (0.7%), with both countries entering our ranking in December.
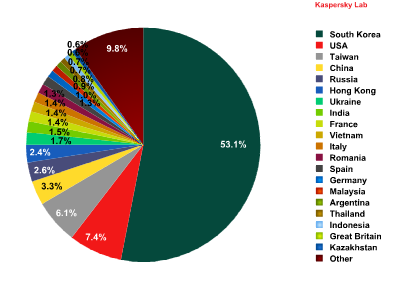
Sources of spam in Europe by country
December’s statistics showed that South Korea was the leading source of spam in Europe, accounting for 53.1% of all spam received in the region. This was a fall of almost 3 percentage points (pp) compared to the previous month. The second largest source of spam in Europe was the United States (7.4%); the proportion of spam from the US increased by 2 pp, pushing the country one position higher in the ranking. Taiwan (6%), which was in second place in November, dropped to third.
A 2.1 pp increase in the proportion of spam sent from China pushed the country to fourth place, seven positions up in the ranking. Russia remained in fifth place (2.7%).
Tenth position was taken by Vietnam (1.4%). This country’s share fell slightly – by 0.9 pp.
A slight increase in spammer activity was recorded in Italy, where the proportion of unsolicited mail was 1.4%. It is also worth noting a small increase in spammer activity in Spain: in December, the country entered our ranking with a 1.3% share.
Among regions, Asia remains the leader (56.6%) in spam distribution, even though its share is 2 pp lower than the previous month. It is followed by North America (19.9%), whose share increased insignificantly by 0.3 pp. The third position is taken by Eastern Europe (13.7%), followed by Western Europe (4.4%) and Latin America (2.5%). The share of the Middle East region is 2.4%.
Malicious attachments in email
In December, the Top 10 malicious programs distributed via email looked like this:
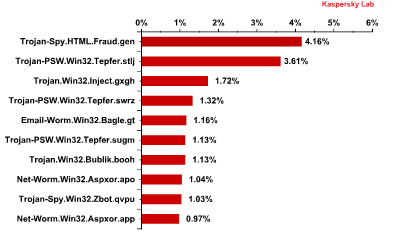
TOP 10 malicious programs distributed via email
Trojan-Spy.HTML.Fraud.gen, which has stubbornly remained at the top of the ranking for months, is still number one. As we wrote before, this piece of malware from the Fraud.gen family is a fake data entry HTML page that is sent to users by email, disguised as an important message from large commercial banks, online stores, software companies etc.
The second, fourth and sixth positions in the ranking are occupied by Trojan-PSW.Win32.Tepfer.stlj, Trojan-PSW.Win32.Tepfer.swrz and Trojan-PSW.Win32.Tepfer.sugm, respectively. These are spyware programs which steal browser cookies and passwords, as well as passwords for FTP clients and email accounts. The stolen data is sent to cybercriminals.
Trojan.Win32.Inject.gxgh is in third place. This malware secretly installs a malicious extension for Google Chrome and Mozilla Firefox on victim machines. The extension intercepts search queries for many search engines, sends them to the cybercriminals’ server and then spoofs the search results, showing fake results created by the criminals instead of those produced by the search engine.
The fifth position is taken by our old acquaintance Email-Worm.Win32.Bagle.gt, an email worm which sends copies of itself to all email addresses found on an infected computer. The worm also downloads files from the Internet without the user’s knowledge. Email-Worm.Win32.Bagle.gt uses its own SMTP library to send infected messages.
December’s eighth and tenth positions were taken by Net-Worm.Win32.Aspxor.apo and Net-Worm.Win32.Aspxor.app, respectively. Aspxor is a spam-sending network worm. It can automatically infect websites, download and execute other software, collect valuable data on the computer, such as saved passwords and credentials for email and FTP accounts.
Ninth position was taken by Trojan-Spy.Win32.Zbot.qvpu. Zbot/Zeus is a family of Trojans designed to attack servers and user machines and intercept data. Although the Trojan can perform a variety of malicious activity, it is most commonly used to steal banking data. It can also install CryptoLocker, a malicious program which encrypts user data and then demands payment for decrypting it.
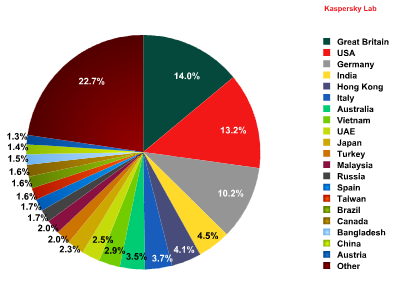
Distribution of mail antivirus detections by country
The UK has been the country with the highest number of mail antivirus detections since November (14%). The country’s share in December was up 1.7 pp. The share of the United States (13.2%) was also 3.1 pp higher than in November, taking the country to second position in the ranking. As a result, Germany dropped to third with a result 1 pp lower than the previous month.
Russia’s share of the total number of mail antivirus detections worldwide was down to 1.7%. The shares of other countries did not significantly change in December compared to the previous month.
Special features of malicious spam
It is increasingly common for scammers who send malicious emails to use the names of well-known electronics or software companies in the sender field. The idea is simple: if a message comes from a reputable company, it is much more likely to lure users into opening the malicious archive.
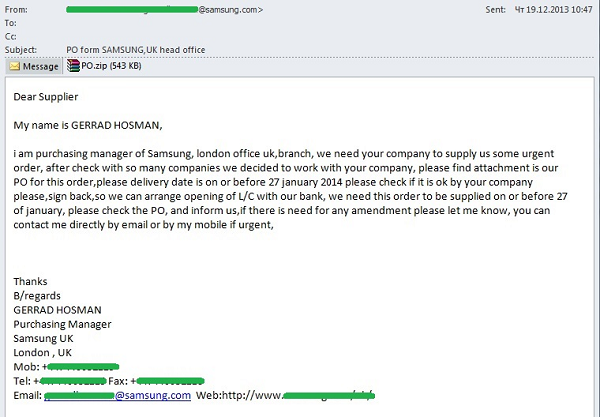
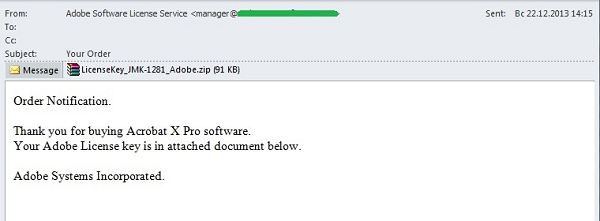
In December, we saw a large number of messages sent on behalf of Samsung, a major manufacturer of telecommunications equipment, household appliances, audio and video devices, as well as on behalf of Adobe, a US software developer.
Emails sent on behalf of Samsung were supposedly written by one of the company’s managers. In the messages, the ‘manager’ wrote that he needed to arrange for certain goods to be supplied at short notice and that, after a long search for an intermediary, the recipient and his/her company was selected. The order for the goods to be supplied was included in the attached file. The deadline for completing the paperwork, making the payment and supplying the goods was also specified in the message. The message included the manager’s auto signature with all the relevant contact details. In reality, the file attached to the message was a malicious program detected by Kaspersky Lab as Trojan-Spy.Win32.Zbot.qzpl. This is a Trojan Spy from the Zbot/ZeuS family, designed to steal the user’s confidential information.
Messages on behalf of Adobe imitated a purchase confirmation for one of the company’s software products and supposedly included the license key required for its activation. A virus scan showed that, instead of an activation code the archive attached to the message included a worm detected by Kaspersky Lab as Net-Worm.Win32.Aspxor.apo. This is a worm from the Net-Worm.Win32.Aspxor family, which is used by cybercriminals to send spam. It can also infect websites, download and execute software and steal data from the user machine.
Phishing
In December, the ranking of organizations attacked by phishers did not change significantly.

Distribution of the Top 100 organizations targeted by phishers, by category
The ranking is based on Kaspersky Lab’s anti-phishing component detections, which are triggered every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
As before, in December first place was held by social networking sites (26.9%), which continue to lose ground (-0.4 pp). The shares of email services (19.5%) and search engines (16.6%) increased slightly and these categories remained in second and third positions in the ranking respectively.
Financial and e-pay organizations (15.8%) remained in the fourth position in the ranking, the category’s share down by 0.3 pp compared to the previous month.
The telephony and internet service providers category once again changed places with the IT vendors category, placing these categories in 5th and 6th positions, respectively. This was the result of the share of IT vendors (6%) going down and that of telephone and ISPs (8.5%) going up by 2.4 pp.
The shares of online games, government organizations and mass media were slightly smaller than the month before; in December these categories were in 8th, 9th and 10th positions, respectively.
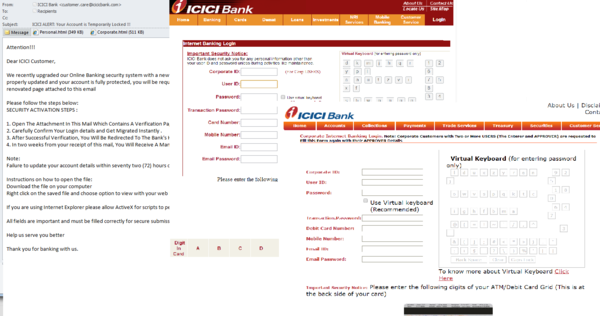
Some banking organizations are targeted by phishers with unenviable regularity. In December spammers yet again sent fake official notices on behalf of Indian bank ICICI. According to the message, the security system of the online banking service had been upgraded and the user needed to log on to provide some newly-required information. This was followed by step-by-step instructions requiring that the user open the HTML attachment, enter the required information and confirm it. The message had two such attachments, one for corporate customers, the other for individuals, but they had identical fields to be filled in. The data entered on these phishing pages was sent to cybercriminals, giving them full access to the user’s account.
To convince recipients that the message was legitimate, the attackers used a sender address which looked similar to the bank’s official address. In addition, the message included detailed activation instructions, something that is rarely found in phishing emails. In addition, the design of the phishing pages attached to the message imitated that of the bank’s official website.
Conclusion
The proportion of spam in global email traffic was up by 0.8 pp in December, reaching 73.3%. The amount of spam in circulation in January will probably be smaller, since early January is a quiet time for spammers: many botnets are offline during the holidays and user activity is down, too.
As we predicted, the amount of holiday-related spam peaked in December. In 2013, New Year and Christmas spam was even more varied than before and included new offers. At the same time, the amount of graphic spam related to the winter holidays remained high.
Spammers used the death of Nelson Mandela in December as one more opportunity for sending ‘Nigerian’ letters on behalf of the late president’s colleagues in order to defraud users of their money. We expect that scam emails related to this sad event will continue to be sent in January.
In December, the Social Networking Sites category remained in the leading position among the Top 100 organizations attacked by phishers, its share down by 0.4 pp. It was followed in the ranking by email services and search engines, whose shares were slightly higher than the month before. Conversely, the share of financial organizations, which were in the fourth position in the ranking, was lower than in November and amounted to 15.8%. The ranking is unlikely to change significantly in January.
As regards malicious spam, in December scammers used the names of global electronics and software companies, as well as those of financial organizations and social networking sites, to lure victims into opening the malicious attachments.






















Spam in December 2013