
Spam in the spotlight
In April, holiday-themed mass mailings featured Easter, which was used not only to advertise spammer products, but by a variety of scammers who sent out fake lottery winnings notifications to Internet users and malware disguised as holiday e-greetings.
Scammers also mailed out offers to earn money from stock in American pharmaceutical companies – so-called pump and dump spam. Several large mailings advertised the services of a variety of medical institutions and dental clinics, as well as ways to break bad habits and rehab treatment for drug addicts and alcoholics.
Easter spam
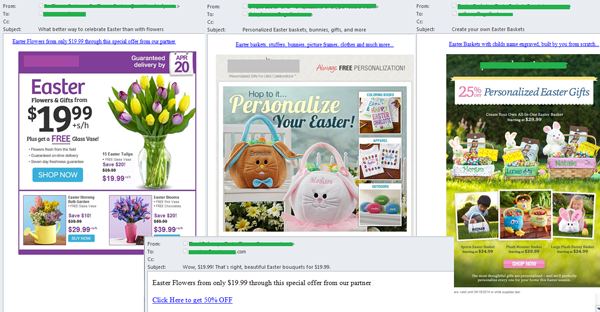
Easter is a major religious holiday for Christians of all branches of the faith, and is celebrated worldwide. Each year ahead of the holiday, email inboxes face a deluge of Easter-themed spam. English-language spam in April brought the traditional mass mailings from affiliate programs, which don’t change much from one year to the next, and offers for brand-name Easter products.
Spammers did not forget about their usual ads for losing weight and looking younger. Offers for rapid weight loss and anti-wrinkle treatments were remade to include an Easter theme and contained the name of the holiday in the body of the email.
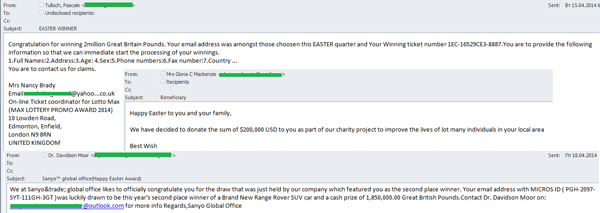
An Easter spin was also put into fraudulent emails about non-existent lottery winnings. The name of the holiday was used in the email subject line to attract the attention of recipients, while greetings at the start of the message were meant to convince recipients that the author had nothing but good intentions.
Playing the market
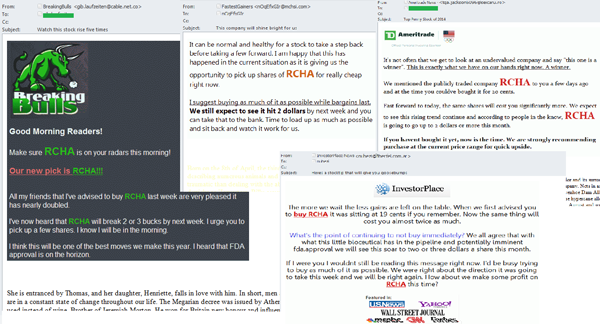
Last month, we saw a new wave of so-called pump and dump spam. The scammers behind these email mailings advertised offers to buy stock in a certain company at super low prices, which were allegedly meant to increase considerably in the near future. As a result, the demand for the stock in the company rose, the prices became artificially inflated – and the scammers would then sell off their stock in said company. The stock prices would then begin to fall, and the bamboozled investors were left with depreciated shares and lost their investments. As a rule, scammers tend to choose little known companies for these schemes, where the stock is traded on a secondary market. In April, they used Rich Pharmaceuticals, a US company.
The pump and dump spam emails that were detected were sent allegedly from a variety of companies offering investment and brokerage services to potential investors. In order to make the emails look like the real deal, the scammers used the logos from real companies and said that their emails came from those companies – even though the ‘From’ field in the email did not look like the official names. In order to make their fake emails harder to detect, scammers used graphics and random text at the end of the body of the email.
Spammers looking out for your health
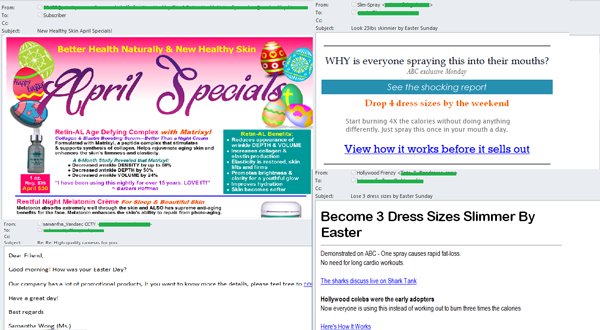
In April, medical goods and services spam focused on treatments for specific illnesses. For example, cures were offered for baldness and bladder issues; full medical exams were advertised, as were cures for forever-cures for diabetes, arthritis, and other illnesses. Most of the emails were designed as graphic files with links that would typically lead users to a fake website, where they would wait for a list of services offered, lists of specialty clinics, and price comparisons for a variety of services. These emails were all traced back to addresses registered on recently created fly-by-night domains.
Dental clinics used spam in April to advertise their services for inexpensive dental implantations from a variety of manufacturers.
Spammers against bad habits
April spam mailings offered smokers a way to kick their bad habit by switching over to smoking e-cigarettes. If a recipient were to click on the link in the spam email leading to the online store, he or she could order any quantity and any flavor of e-cigarettes. The body of the email also listed all of the advantages of using e-cigarettes over old fashioned nicotine.
In addition to fighting smoking addictions, spammers also advertised rehab programs from those suffering from drug or alcohol dependency. A standard email with these offers came from email addresses that were constantly changing and registered on newly created domains. The links in the emails lead to fake websites that contained offers for a variety of medical services, but which were not necessarily associated with addiction treatment.
Statistics
The percentage of spam in email traffic
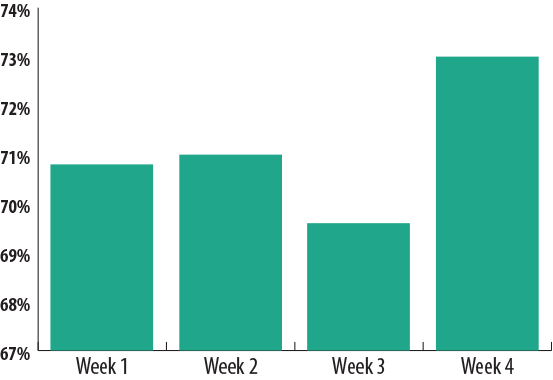
The percentage of spam in email traffic
On average, the percentage of spam in email traffic in April came to 71.1%, which is 7.6 percentage points more than in the March. The largest spam levels were seen during the last week of the month (73%), and the lowest levels were seen in the penultimate week (69.6%).
The geographical distribution of spam sources
At the close of April 2014, the top three sources of spam around the world changed somewhat from the prior month. China again took first place (24.1%) after its percentage changed just slightly, going down one half-percentage point. Next, South Korea took second place with 15.6% after taking third place last month; the amount of spam originating in that country increased by 2.4 percentage points. The US took third place with 12.1% after slipping nearly 5 percentage points, which also had an impact on the placement of other spam sources.
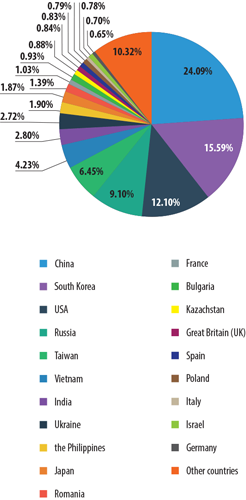
Sources of spam around the world
Russia and Taiwan both maintained their places in the Top 5 (9.1% and 6.5%, respectively). Russia’s percentage even increased by 2.5 percentage points.
An increase in the percentage of spam sent was also observed in Vietnam (4.2%), Ukraine (2.7%), and the Philippines (1.9%) – on average, the indicators of these countries rose by 0.6 percentage points. As a result, the Philippines took the 9th place ranking this past month. Readers may remember that in March, the Philippines was in 11th place.
Japan rounded out the Top 10 in April with 1.9%; the percentage of spam originating in this country barely changed at all, but the country’s ranking fell by one position. At the close of the month, we also saw Romania exit the Top 10 (1.4%).
Increased spammer activity was seen in France (1%), which made the Top 20 this past month – as high as 12th place. Germany also made the ratings in April (0.7%).
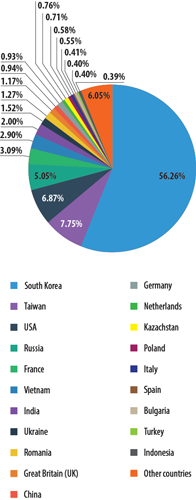
At the close of April, the leader of spam sources targeting European countries was South Korea, up 5.5 percentage points to 56.3%. Taiwan rose from third to second place in the rankings (7.8%) after climbing 1.8 percentage points. The Top 3 was rounded out by the US with 6.9%, or 0.7 percentage points less than in March.
Russia (5.1%) held its 4th place position firmly after gaining 0.8 percentage points. An increase in the amount of spam sent from France was also noted in France (3.1%), which jumped up from 19th place to 5th.
The amount of spam targeting Europe and originating from Ukraine (1.5%) and Romania (1.3%) fell by 0.3 percentage points and 0.4 percentage points, respectively. percentage points he UK took 10th place (1.2%) after dropping 0.5 percentage points over the month.
The amounts of spam originating in China, Poland, and Italy all dropped in April (2 percentage points, 0.3 percentage points, and 0.6 percentage points, respectively). In contrast, a slight increase in spammer activity was observed in Germany, where the percentage of spam was 0.9% at month’s end.
This month, our list of countries was joined by the Netherlands (0.8%) and Turkey (0.4%).
When it comes to regional sources of spam, Asia remains in the lead with 59.8%. Eastern Europe is next with 16.9%, switching places with North America, which fell from second to third (12.3%). Meanwhile, the percentage of spam originating in Eastern Europe increased by over 2 percentage points, while North America’s percentage fell by nearly 5 percentage points.
The regions of Western Europe (5.3%) and South America (2.9%) also saw increases in the amount of spam (0.6 percentage points and 0.5 percentage points, respectively).
Malicious attachments in email
The graphic below shows the Top 10 malicious programs spread by email in April.
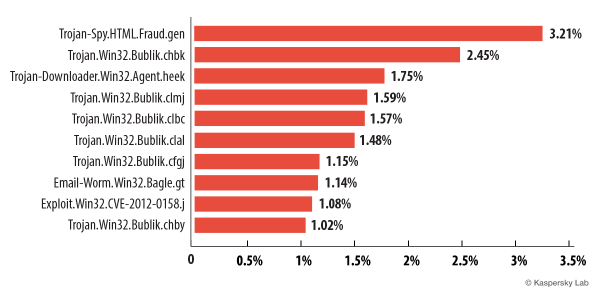
The Top 10 malicious programs spread by email
As is tradition, the list of malware spread by email is topped by Trojan-Spy.HTML.Fraud.gen. One would like to believe that after numerous publications and reminders of this threat, the number of users falling victim to it would be at a minimum. Readers may remember that this is the very threat that appears as an HTML phishing website and sends email disguised as an important notification from banks, online stores, and other services.
In April our Top 10 was joined by several representatives of the Bublik family. All of the threats from this family in the Top 10 are downloaded onto infected computers by a Trojan from the ZeuS/Zbot family (which we have mentioned numerous times in our reports). The threats in this family are designed to attack servers and user computers, and intercept data. Although ZeuS/Zbot is able to execute a variety of malicious actions, more often than not it is used to steal banking information. It can also installCryptoLocker, a malicious program that demands a ransom to decipher user data.
Trojan-Downloader.Win32.Agent.heek was in third place. This malware downloads Trojan spyware designed to steal financial information. Most of these programs target Brazilian and Portuguese banks.
The Email-Worm.Win32.Bagle.gt worm, which ranked 8th in April, added a bit of variety to the otherwise Bublik-dominated attacks in April. After infecting a computer, Email-Worm.Win32.Bagle.gt sends itself to all of the email addresses it can find on the computer. Its main objective is to download and launch files from the Internet without victims noticing.
Ninth position was occupied by Exploit.Win32.CVE-2012-0158.j, a DOC file which exploits a vulnerability in the mscomctl.ocx code in Microsoft Office to install and run malware.

The distribution of email antivirus detections, by country
The ranking of countries in terms of the number of email antivirus detections was led by the US in April with 11.73% (down by 0.28 percentage points from March). The UK (9.95%) and Germany (9.47%) were in second and third places, respectively.
The percentage of email antivirus detections increased by 2.13 percentage points in Brazil (total 4.13%), and as a result, that country rose to 5th place in the rankings. Russia’s numbers fell by 0.25 percentage points and fell from 16th to 20th place. Meanwhile, the percentage of email antivirus detections in other countries did not change much in April.
Special features of malicious spam
The day after Easter, malicious users sent out mass e-greetings in German using the names of users whose email accounts were likely hacked. The emails contained well wishes and an e-greeting (in an attachment) which was used to conceal Trojan-PSW.Win32.Fareit.aonw. Unlike other Fareit modifications, this threat is a bit less ambitious — it doesn’t steal passwords to software programs, but it does download and launch another Trojan, Trojan-Spy.Win32.Zbot.sbba, which is designed to attack servers and steal personal data.
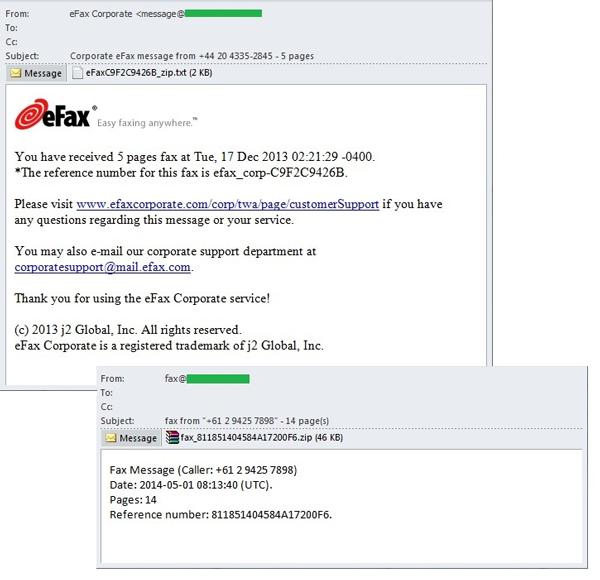
Also in April, Kaspersky Lab detected several large malicious attacks disguised as faxes sent by a well-known online fax service, eFax, which allows users to send and receive faxes as email attachments. The fake messages usually included a notification about an incoming fax, and to be more persuasive, it would indicate the number of pages in the fax. However, the zip file actually contained malware, specifically Trojan-Downloader.Win32.Cabby.a — a rather small Trojan downloader that carries a CAB file in its body with the document or graphic that is displayed to the recipient after launching. While the victim is busy viewing the attachment, Cabby stealthily downloads another threat. In the cases we observed, the secondary malicious program was from the same widespread ZeuS/Zbot family (Trojan-Spy.Win32.Zbot.shqe).
Phishing
In April, Kaspersky Lab grouped the organizations most frequently targeted by phishers into a category encompassing email clients, instant messaging clients, and search engines. At the end of the month, this category was at the top of the rating with 31.9%. Social networks were in second place with 23.8%, even after a 0.2 percentage points drop. Financial and payment organizations came in third with 13%, and had also declined 0.2 percentage points since March. The percentage of attacks targeting online stores (12.1%) fell by 0.8 percentage points. The indicators for other categories also underwent some slight changes which had no impact on their rank in the ratings.
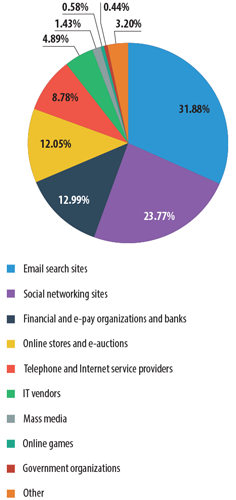
The distribution of the Top 100 organizations most frequently targeted by phishers, by category
This ranking is based on Kaspersky Lab’s anti-phishing component detections, which are triggered every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
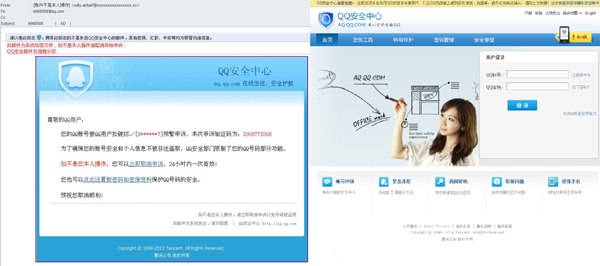
Large Chinese organizations are often the targets of phishers, and include Tencent, a telecom company that among other things offers tech support for an instant messaging client, QQ. Scammers tried to get client logins and passwords from their personal offices using a common trick. A fake notification would tell users that their account received a request to unlock the account. Since the alleged request was sent by a third-party user, account access had been locked to prevent the theft of personal information.
In order to decline the request, the user was asked to click on a link, which led to a phishing website. Incidentally, the notification was sent as a graphic, which helped it bypass spam filters and made the email look more legitimate.
Conclusion
The percentage of spam in global email traffic in April rose 7.6 percentage points and averaged 71.1%. The highest spam levels were seen in the last week of the month (73%).
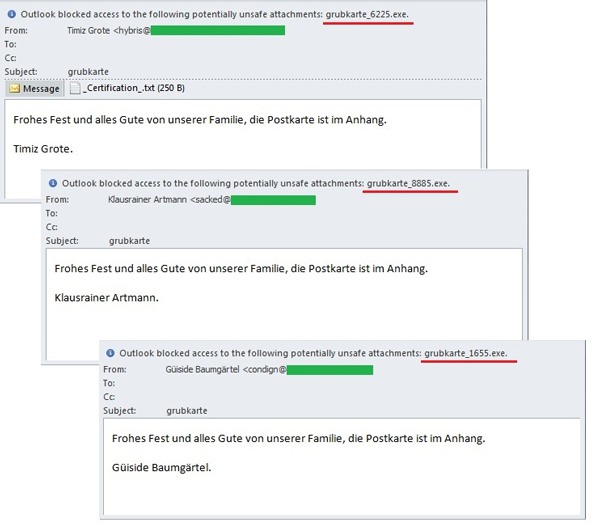
The amount of Easter-themed spam in April was as high as it could get. Spammers mainly send out offers for different Easter goods and services, in addition to goods and services that really had no direct relation to the holiday. Easter was even mentioned in fraudulent notifications about lottery winnings in order to draw the attention of potential recipients and attempt to trick them. Furthermore, during this wave of Easter activity, malicious users also sent out e-greetings with malicious programs.
The Top 3 sources of spam worldwide in April were China (24.1%), South Korea (15.6%), and the US (12.1%). Asia remained the number one regional source of spam last month (59.8%).
At the close of the month, we saw a new category — email clients and search engines — take the lead among the organizations most frequently targeted by phishers (31.9%). Social networks were in second place (23.8%), while financial and payment organizations were in third (13%).






















Spam in April 2014