
Recent trends
- The amount of spam in email traffic increased by 1.2% compared to August’s figure. The total average being 86.3% for September.
- Links to phishing sites were found in 0.84% of all emails, an increase of 0.25% when compared to August.
- Malicious files were found in 1.22% of all emails, an increase of 1.17% compared with the previous month.
- In order to bypass filters, spammers continue to favor the use of HTML charts. This trick proved quite popular and successful last month.
Spam in email traffic
The amount of spam detected in email traffic averaged 86.3% in September 2009. A low of 83.3% was recorded on 18 September with a peak value of 91.3% being reached on 27 September. Most noticeably, for the first time ever Kaspersky Lab’s records show that the quantity of spam received by users throughout September 2009 did not drop below 83%.

The share of spam in email traffic for September 2009
Malicious files were found in 1.22% of all email messages. This is an increase of 1.17% when compared to the previous month’s figure.
Malicious attachments in spam

Malware found in spam messages during September 2009
During September there was a major reshuffle of the Top10 malicious programs to be found in spam messages. The NetSky worm family, which was last month’s leader, lost its position this month. In August one third of all infected messages belonged to this family, whilst in September only one variant, the Win32.NetSky.q worm, remained in the Top10 – sitting at number 10 on the list.
The clear leader this month is the FraudTool Trojan family. Almost half of all infected messages contained these Trojan variants. As the name suggests, the Trojan installs a rogue antivirus program on the user’s computer. This type of malware appears to be very much in vogue at the present time.
Rather unexpectedly, first place in the Top10 went to Trojan-Downloader.Win32.Murlo.cba, a fairly old variant found in 28.5% of malicious spam message attachments.
Perhaps contrary to expectations, the Zbot Trojan family is rather poorly represented in the Top10 for September. Trojan-Spy.Win32.Zbot.gen took 9th place with just 0.81% of the infected messages. Trojan-Spy.Win32.Zbot.gen is a spy Trojan designed to steal a user’s confidential data. More information about this variant is available at https://threats.kaspersky.com/en/.
Interestingly, the Bredolab backdoor family, which was among the most popular malicious programs during August, has slipped out of the September Top10 completely.
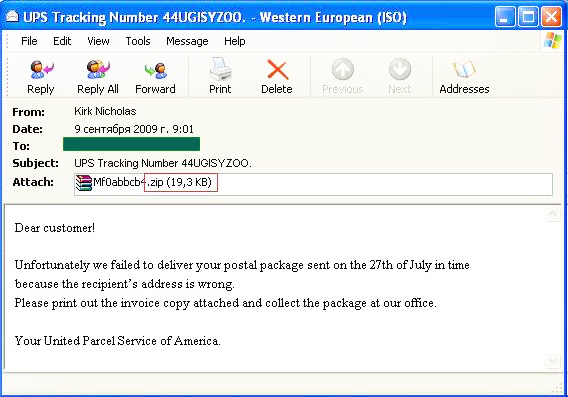
In order to distribute their malicious content, spammers fell back on one of their old methods, a zipped file attached to convincing-looking notifications supposedly from the respected courier firms DHL and UPS.
This type of spam first appeared between the end of May and the beginning of June 09. However, in September spammers started to use it more actively. Interestingly, September’s DHL-spam differs considerably from that of June’s. Firstly, in June DHL-spam targeted a German audience and was written in German. Secondly, in June it was not zipped – it was located on a web page with a link to the message.
During September the situation changed, with DHL-spam becoming UPS-spam’s ‘twin brother’, while the UPS-spam itself remained unchanged. This means that spammers are learning to use each other’s technological ruses.

Such emails were used to distribute various malicious programs, including attachments containing the Bredolab strain.
The same backdoor was also found in emails allegedly sent on behalf of Western Union. This is a prime example of the use of social engineering techniques. The body of the message informs the user about a supposed money transfer, whilst the attachment purports to contain the Money Transfer Control Number [MTCN] necessary to receive the money. It is not necessary to point out that the attachment in fact contains no such MTCN.
Another mass mailing attempt contained a zipped attachment with malicious content and also followed the format of mimicking a legitimate notification – this time from an online store. In truth, it was rather a poor attempt – with no store name, no address for the recipient, no contact details etc…
Phishing
Links to phishing sites were found in 0.84% of all emails, a decrease of 0.25% when compared to August. In September, PayPal regained its first place in the league of the most attacked organizations. The number of attacks rose considerably compared to August (+18.68%) and almost reached July’s figure (40.19% in July and 37.33% in September). eBay maintained its August level (+0.45%) occupying third place in the rating. Second place was taken by IRS, the American Internal Revenue Service, which drew 11.08% of all September’s phishing attacks. In fact these were not classic phishing attacks. Fake messages sent on behalf of the IRS contained malware of the Zbot variety (Trojan-Spy.Win32.Zbot). The previous month’s leader, CHASE Bank, which demonstrated an abrupt and unexpected rise in August, dropped to just outside the Top10 during September, remaining at 11th position. Its share of the total number of phishing attacks was only 2%, a decrease of 28% compared to August.

Organizations targeted by phishing attacks in September 2009
By the end of September, fraudsters had refined their techniques so that their phishing messages closely imitated PayPal’s legitimate mailings.
Phishers left the PayPal logos and general design of the message unchanged. In addition, the From field looked very much like the original. However, a careful user will immediately spot some subtle peculiarities. First of all, the links contained in the original message on the PayPal site led to legal resources. In the spammers’ messages these links were just inscriptions printed in blue and only a single link was active. Secondly, the news was dated December 2009, but the text itself referred to the “coming October”. Thirdly, the following phrase suggested that it may be a phishing attempt as opposed to the genuine article: “According to changes in the Service Agreement, any unverified account will be deleted from the system within 72 hours of the receipt of this communication.”
Finally, phishers trying to do their best to imitate the original design made yet another mistake by not including the letter “h” in “http”. As a result the browser couldn’t recognize the protocol and consequently did not redirect users to the phishing site. Luckily this prevented even the most inattentive user from sending their registration details to the fraudsters.
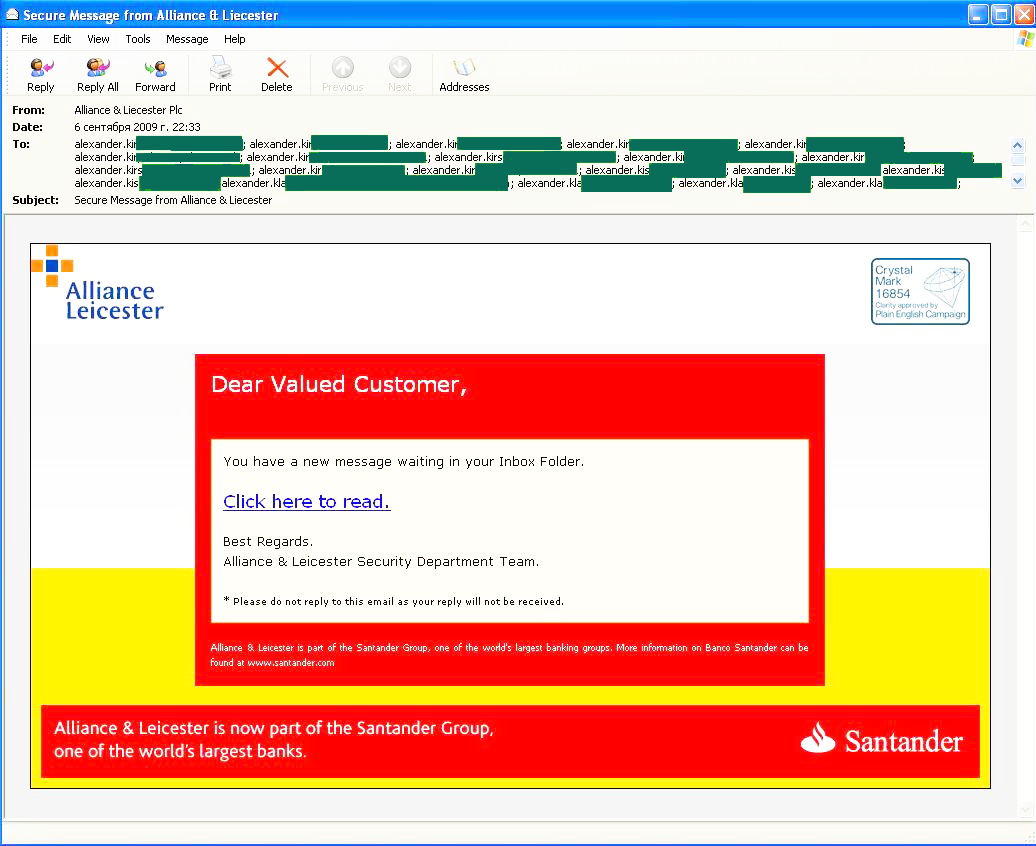
Another interesting phishing attack targeted clients of the Alliance & Leicester, a UK bank. Users received a message with the following content:
Needless to say, the link led to a phishing site which asked the user to enter their login and password in order to open the message. Oddly enough, in this case the phishers could not, or just did not bother, to mask the fact that it was a mass mailing. If the To field is examined carefully, it can be seen that the names of all the addressees began with ‘Alexander’.
In September, phishers unexpectedly displayed an interest in WOW accounts. This topic is covered in the following blog: https://securelist.com/.
Sources of spam
In September, the US regained the top position in the league table of countries that are key sources of spam. Almost one third of all spam monitored was of US origin (32.47%, an increase of 28.67% when compared with August). Brazil moved up to second place, distributing only half the spam it had in the previous month (5.97% compared to 11.8% in August). The Top10 also includes Vietnam (-2.61%) in third place, followed by Korea (-1.3%), China (+0.3%) and India (-3%). Poland, which occupied second place in August, returned to its July figures of 3.25% (-4.75%). The amount of spam coming from the UK increased by 0.1% and accounted for 2.1%, taking it up to 9th place.
Spam by category
The most popular English-language spam category was medication and health-related goods and services. In September, Viagra distributors increased their nefarious repertoire by offering ‘male’ pills in a mass mailing under a medical news heading.
However, each link in this “newsletter” led to a site advertising counterfeit Viagra.
In addition to traditional mailings offering Viagra or diet pills, other types of ‘medical’ spam was also recorded.
Fraudsters also actively sent out Nigerian letters. In addition to the usual schemes, the cybercriminals made reference to recent newsworthy events. For example, in the email below fraudsters use the theme of Somalian pirates and ask for help in transferring forfeited money.
With regards to English-language spam, the Other goods and services category proved a very popular area during September. For example, fraudsters launched a mailing offering free website analysis.
Original spam
Spammers offered to solve any financial problems to western users caused by the economic crisis with the help of online pawnshops. Below is a sample of this mailing.

The email offers the user an opportunity to sell their unwanted gold jewelry. However, the links lead to something completely unexpected:
This is a rogue antivirus program, a trick very much in vogue with cybercriminal elements at the present time. As can be seen in the screenshot, an offer is made to the user to scan and repair their computer with the help of this ‘tool’ for just $40.
The ‘antivirus program’ does not in fact do anything at all – either good or bad. It simply asks for $40!
Spammer methods and tricks
In September, English-language spammers repeated one of their more common tricks, colored HTML tables. However, they were created far less skillfully than those used last month.

Conclusion
September’s most remarkable aspect was the considerable growth in the number of infected emails. The spammers relied heavily upon their tried and trusted method of distribution – the imitation of notifications from major organizations and online stores.
































Spam evolution: September 2009