
Spam in mail traffic
The percentage of spam in mail traffic is still on the rise. In the first quarter this year, spam represented an average of 88% of all mail traffic.
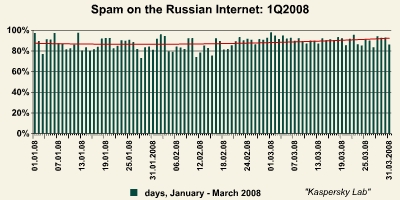
Spam on the Russian Internet: 1Q2008
The largest fluctuations in spam volume were observed in January (from 73.1% to 97.3%), but by mid-February, spam strengthened its position and locked in no lower than 80% of all mail traffic. The lowest spam figures were recorded at 73.1% on 28 January, while the high for the first quarter was seen on 1 March when spam reached 97.8% of all mail traffic.
Since the beginning of this year, the share of graphical spam in unsolicited correspondence has been increasing; it reached 28% in the first quarter of 2008.
In late 2007, graphical spam accounted for just 14% of spam email, and graphical spammer was expected to become more common in 2008. Using images is a preferred spammer method, which is particularly prevalent among large spammer companies (in emails advertising Viagra, for example) which have access to powerful servers and extensive botnets. The constantly changing images used in conjunction with the information sent by spammers can definitely make it more difficult for some spam filters to analyze the contents of spam messages.
Spam by category
This quarter, the top spam categories were:
- Medications and health related goods and services (32.5%).
- Education (13.3%)
- Travel and tourism (7.2%).
- Computers and the Internet (4.5%)
- Adult content spam (4.3%)
During the first quarter this year, the top five categories of spam included a lineup typical for the Russian Internet, with Medications and health related goods and services in the lead. There was one exception: fifth place featured the Adult content category (advertising for a variety of pornography and dating sites). In 2006-2007, this category of spam was usually at the bottom of the list and accounted for just 2% of all spam. However, in late 2007 and early 2008, adult content spam unexpectedly climbed 5% and closed the first quarter of this year at 4.3%.
Adult content spam pushed the Electronic advertising services category (ads for spamming services) out of the top five. The percentage of that category had reached 6% toward the end of 2007, and fell to 3.7% in the first quarter of 2008. Why are spammers not advertising their services as frequently? Does that mean that we can expect spam levels to decline? Unfortunately, the answer is no. The percentages of the different spam categories have dropped, but this is not because spammers have started to think about whether or not their actions are legal.
As a rule, spurts of activity in advertising for spammer services are related to a decline in orders for mass mailings and are designed to securing new clients. Only major spam outfits that deal in marketing advertise their services regularly. It is this kind of “scheduled” advertising that makes up the majority of spam which falls into the electronic advertising services category, which fluctuates between 3-4% of all spam. Unfortunately, a percentage of 3.7% indicates that spammers have plenty of orders and no lack of clients.
In the first quarter of 2008, a great deal of spam was observed which advertise fake luxury goods. There were so many of these spam messages that we had to define this as a new category in March when it reached 9.1%. Clearly, the volume of such spam is related to the growing popularity of these goods in Russia.
This type of spam is widespread in the US, and now we are seeing a larger amount of the same kind of spam in Russian as well. The primary difference is that in English-language spam, most of the goods advertised are watches (Rolex, Omega, etc.), while the assortment on the Russian Internet is larger. Some mailings advertise several different products in one spam message.

AND GIFTS!
Vertu is the most luxurious telephone in the world, sought after by those who truly
appreciate beautiful things:
all of the latest achievements in cutting-edge technologies are combined in this brilliant
masterpiece
Replicas of Vertu”s luxury mobile phones and wristwatches are ten times less inexpensive
than originals!
Models:
Vertu Signature
Vertu Mini
Vertu Signature Full Pave
Vertu Constellation and Ascent – NEW!
Watches: Vacheron Constantin, Patek Philippe, Rado, Omega and many more!
[PHONE NUMBER]
Click here for a gift catalog on our website
There is one factor that is particularly interesting when surveying spam categories on the Russian Internet in the first quarter of 2008: the absence of any political spam, which as a rule is generally widespread in the period ahead of elections. A burst of activity in this category was observed last year before the elections to Russia’s State Duma. We expected to see a similar surge in political spam prior to the Russian presidential elections on 2 March 2008. However, this did not turn out to be the case. Political spam has been practically nonexistent so far this year (save for calls to sabotage the elections with slogans such as: “REFUSE TO ELECT BUREAUCRATS, ELECT YOURSELF! LET THEM VOTE AGAINST EACH OTHER!!!).”
Nevertheless, the elections did not pass without being targeted by scammers. Under the pretext of a sociological survey, spammers asked Internet users to state who they were planning to vote for at the elections by sending a text message to a short code. The scammers conveniently neglected to mention that sending a text message would cost each user a few dollars, and that they would be pocketing some of that money. (See the section on the criminalization of spam to learn more about short codes and how they are used by scammers.)
Spammer techniques: masking email text using html tags
Masking is a tactic that has been used by spammers practically since the emergence of automated spam. Spammers add “extra text”, which changes constantly, to every message in the mass mailing. This text is either not visible to the recipient, or formatted in such a way to prevent the user’s attention from being drawn to it. This technique is used so that a spam filter will treat each individual message in the mass mailing as unique.
More often than not, spammers will add a random sequence of letters or words at the end of an email, or text that is the same color as the background used in the email in various places throughout the body of the text.
Early this year, spammers started to add random text with html tags. Comment tags – which define the color of the text and other features – are used in such cases. Most mail clients see these tags as auxiliary, and they are consequently not shown to the recipient. As a result, the recipient only sees the advertising text, which, from a filter’s point of view, is just a small portion of the message text.
One example of a message using this approach, showing what the recipient will see, is given below:
Для ее получения зайдите на сайт www.postcard.ru/card.php?2897238793и
нажмите на ссылку “получить открытку”
Служба рассылки открыток POSTCARD.RU
————————————————
You received an postcard.
To get it follow to web-site www.postcard.ru/card.php?2897238793 switch to english
and click on “get my postcard”
Postcard service POSTCARD.RU
But a filter will see something like the message shown below (masking tags have been highlighted in red). This email demonstrates that the links that the user sees are different from the address of the pages which the links actually lead to (shown in purple):
и нажмите на ссылку ‘получить открытку’
Служба рассылки открыток POSTCARD.RU
————————————————
You recieved an postcard. To get it follow to web-site www.postcard.ru/card.php?2897238793
switch to english and click on ‘get my postcard’
Postcard service POSTCARD.RU
On one hand, such a large amount of garbage text will create a problem for spam filters that do not have a component which filters content. On the other hand, it helps make the email readable for recipients, without irritating them with meaningless additional text. It is likely that spammers will continue to use this technique in combination with other masking methods.
The criminalization of spam
Despite the fact that the percentage of fraudulent spam was relatively low at 2.5% at the end of the first quarter this year, the actual volume of criminalized spam is far higher. The computer fraud spam category does not encompass all spam that can be described as criminalized. Criminalized spam also includes fake and counterfeit goods and medications, unlicensed software, etc., which fall into other categories, and therefore do not contribute to the total volume of computer fraud spam.
Over the first three months of this year, the most surprising aspect of the criminalization of spam is not the quantity of it, but rather the extent to which it has seeped into other areas. Such spam can generally be divided into three main groups:
- fraudulent spam: spammers use a variety of methods to try to steal money from Internet users;
- spam used by cyber criminals in order to spread malicious programs;
- spam with offers of an illegal nature.
Phishing, also known as Nigerian scam emails or 419 email, fall into the first group. These are false notifications informing the recipient that they have won the lottery and other spam emails which employ fraudulent means to extort money.
The second group includes spam with infected attachments, spam which contain links and the suggestion that the user should download the (infected) file (usually an .exe file) or containing links that lead to infected websites.
The third group includes any emails that advertise illegal products or services. As a rule, such messages may contain offers to conduct illegal actions on the Internet or software and databases needed to carry out such actions (organizing DDoS attacks, selling spam software and databases of confidential data, and offers to send malware).
A separate example is “black PR”, which is used to launch attacks on competitors with the aim of sullying their reputation. which give a negative view of competitors Incidents in the first quarter of 2008 included attacks on the newspaper Kommersant and the SB-GARANT insurance company.
The sections below address different types of criminalized spam.
Extorting money from Internet users
It is important to keep in mind that the methods being used by spammers to extort money are becoming more ruthless. In addition to the now typical offers to help save a beautiful Nigerian bride or invest money in some crazy get-rich-quick scheme, Internet users are now being subjected to what is, effectively, blackmail. For example, in the first quarter of 2008, some users received an email where the author presented himself as a hitman hired to kill the recipient, but who would be willing to drop the assignment if the recipient paid him $4,000.

Similar emails have previously been detected in Western mail traffic. They were likely sent to Russian Internet users simply because their addresses were found in a spammer database. It is highly unlikely that a typical Russian Internet user would take it seriously if he received an email from an English-speaking hitman regarding an order to have him “rubbed out.”
Russian scammers frequently imitate their Western counterparts. The well known Internet scam which uses fake notifications of lottery winnings is now quite widespread on the Russian Internet. For example, typical “lottery” scams will be translated from English into Russian using machine translation:
Below is an example of a Russian-language version of a fake lottery notice. The text is effectively nonsensical and shows hallmarks of having been machine translated from the English language message in the second image:
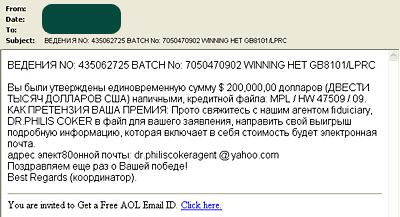
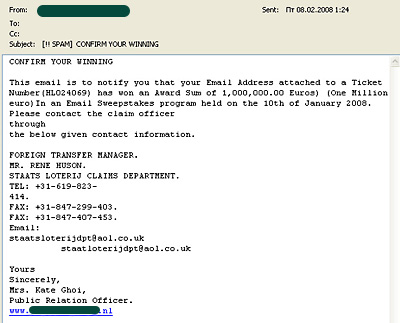
Like anyone else, Internet users need to use their common sense. If you haven”t taken part in a lottery, then you can”t possibly win it. There are no lotteries that draw winners from random email addresses or telephone numbers. These types of emails are sent exclusively by scammers.
However, the Russian Internet has recently been the site of more than just classic ploys from the Western segment of the Internet. Malicious users have successfully developed new means of swindling money out of Russian-speaking users. For example, fraud in which text messages are sent to short codes is currently very common on the Russian Internet.
Short codes are leased out by cellular operators and people are charged money when they send a message to these short codes. Most of the money taken from mobile accounts in payment for texts sent to short codes is passed to the party leasing the code.
Many people do not realize that funds will automatically be withdrawn from their account when they send a text to a short code. Scammers take advantage of that fact by leasing short codes and then sending out spam which invites recipients to send a “free” text message to the leased code. Spammers use a variety of offers to persuade Internet users to send text messages: promises of free Internet access, monetary prizes, and threats that a user’s email account could be blocked if he does not send a text message. More complicated tactics are used in which an email contains a link to the spammer’s site (under the pretense that the site is where the user can claim his winnings) and the user is asked to send the SMS from the site.
One example of this type of email is mentioned above – the message in which spammers asked recipients to send a text message to indicate who they were planning to vote for. And below is another example of the creativity of Russian scammers: in false notifications of lottery winnings, the lucky “winner” is asked to send a text message to a short code in order to find out what prize s/he has won.
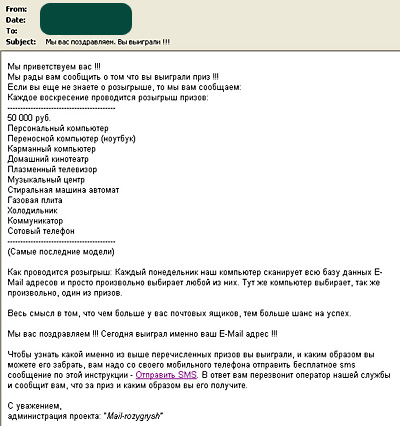
We are pleased to inform you that you have won a prize!!!
If you still don”t know about this giveaway, here are the basics:
Each Sunday, we hold a prize giveaway. You may have won:
————————
50,000 rubles
A personal computer
A laptop computer
A PDA
A home theatre system
A plasma-screen television
A stereo sytem
A new washing machine
A steam iron
A refrigerator
A communicator
A mobile phone
———————–
(The latest models)
How does it work? Each Monday, our computer scans the entire database of email
addresses and simply selects a few of them. The computer also randomly selects one of
the prices.
The more email addresses you have, the more chances you have to WIN!
Congratulations!!! Your email address was the winner today!!!
In order to find out exactly which of the above prizes you have won, and how you can
claim your price, please use your mobile phone to send a free text message based on
the instructions at Send Text Message. Our operator will call you back and inform
you of your prize and how to claim it.
Sincerely,
Mail Prize Administration
Spreading malware via spam
Malicious users may take advantage of spam emails to spread links to malware. These emails tend to imitate notifications from well-known email clients. For example, a falsified email from the Mail.Ru administration asked users to download a free version of the Mail.Ru Agent. As an additional temptation, the email offers bonus minutes for mobile phone users.
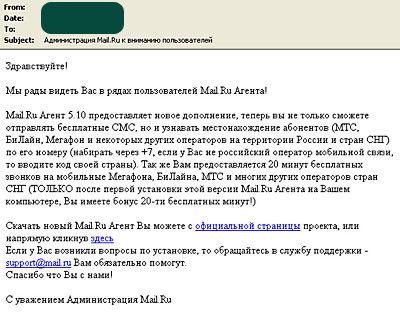
We are pleased to see that you are a user of Mail.Ru Agent!
Mail.Ru. Agent 5.10 has new features, and now you can send free text message and learn
about the location of subscribers (MTS, BeeLine, Megafon and several other
operators in Russia and the CIS) based on their numbers (dial through +7, or if you
do not have a Russian mobile provider, then dial through your country’s code). You
will also receive 20 minutes of free talk time on contracts under Megafon, BeeLine,
MTS and many other providers in the CIS (ONLY after installing this version of
Mail.Ru Agent on your computer can you claim the 20 minutes of free talk time!)
You can download the new version of Mail.Ru Agent from the official website, or just
click here.
If you have any questions about installation, please contact our tech support at
support@mail.ru, and we will be glad to help you.
Thank you for your support!
Sincerely,
The Mail.Ru Administration
Many virus attacks take place during holidays. In particular, many unsuspecting Internet users fall victim on St. Valentine’s Day by clicking on the e-greetings sent to them and unknowingly downloading a malicious program. Although “funny valentines” are originally the invention of Western spammers, Russia’s malicious users have also used this tactic. Below is an example of one Russian-language valentine with a link that, when clicked on by recipients, will lead to a Trojan (Trojan.Win32.Agent.fkn) being downloaded to the victim machine.
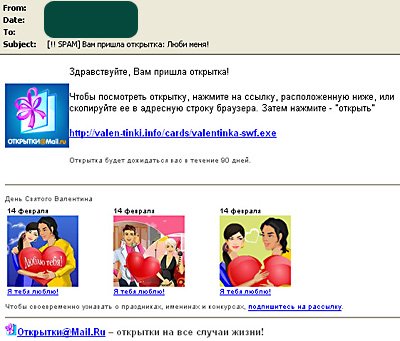
It is important to remember that if you find a link in an email, you should be cautious and make sure that the link that you see matches up with the webpage that it leads you to. And of course, you should never download .exe attachments.
Spam offering illegal goods and services
In terms of the third group of criminalized spam — advertisements for illegal goods and services — there is quite a wide range of offers: conducting DDoS attack, phone flooding, selling spam database addresses, making promises to teach users how to write viruses, and more.

tools, he won’t be able to compete.
Our services will remove the following tools from your competitors:
1) Website
Blocking a website for one week: $999
Take advantage of our 20-minute test blocking.
You can also one day of blocking for $150 in order to demonstrate our effectiveness.
2) Phone flooding (an enormous amount of phone calls exceeding the capacity of the
phone service)
One week: $850
20-minute test flood: free
One day: $150
You can just imagine the organization without a working website or telephone. The sheer
scale is clear.
Your competitor”s expenses for phone and Internet services will also skyrocket.
* — prices for websites presume an average static site (80-90% of websites)
** — prices for websites for phone flooding presume a phone number with 1-3 lines
** — Payment is to be processed by WebMoney (online accounts and card accounts)
We can also “settle” things be Eail, ICQ, text messaging, etc.
Read your girlfriend’s emails on Mail.Ru -just $150.
More at ICQ contact:
In addition to online illegal activities, spammers also offer very specific offline services, such as offering to recover sums of money from debtors.
Conclusion
The results of the first quarter of 2007 have not been altogether encouraging: the total share of spam in mail traffic is on the rise, while spam is as varied as ever and is becoming increasingly criminalized.
Today”s spam has evolved significantly beyond its first incarnation, which was basically cheap advertising written for small companies with small budgets by starving students. Mass mailings are now conducted by large spam cartels with colossal capabilities and resources. Almost all developed countries have adopted laws against spam, and spammers are perfectly aware that their actions are illegal. At the same time, spammer services are being used more and more frequently with openly criminal intent.
Nevertheless, the Russian Internet is still an environment in which a relatively large amount of spam is sent, and where those ordering spam services are legitimate companies with legitimate commercial operations. It”s to be hoped that such companies will find other, legal ways to advertise and market their goods and services and that they will come to acknowledge that using spam does nothing to enhance a company”s reputation.
Quarterly summary
- The percentage of spam in total email traffic is on the rise and has settled at an average of 88%.
- Spammers are actively using graphical spam.
- The amount of spam advertising copies of luxury products has increased markedly.
- Spammers continue to come up with new ways to bypass filters.
- The criminalization of spam is becoming increasingly wide-ranging.




















Spam evolution: January – March 2008