
Recent trends
- In February the amount of spam in email traffic remained exactly the same as in the previous month, averaging 86.1%.
- Links to phishing sites were found in 0.87% of all emails, an increase of 0.06 percentage points compared to January.
- Malicious files were found in 1.18% of all emails, an increase of 1.11 percentage points compared with the previous month.
- In order to bypass filtering, spammers distributing medication-related material resorted to their old tricks.
Spam in mail traffic
The amount of spam detected in mail traffic averaged 86.1% in February 2010. A low of 80.5% was recorded on 15 February, with a peak of 90.8% on 21 February.

Percentage of spam in mail traffic in February 2010
Sources of spam
In February, the US maintained its position at the top of the table despite a decrease of 7 percentage points compared to January’s figure. India moved up to second place having distributed 8.8% of all spam, an increase of 2.7 percentage points compared with the previous month.
The most notable event in February’s Top 20 was the decrease in the amount of spam coming from Brazil (-4.7 percentage points), Russia (-2.5 percentage points) and China (-1.3 percentage points). Brazil fell from second position down to ninth.
The amount of spam originating from Korea and Vietnam doubled, making them third and fourth respectively (Korea +3.9 percentage points and Vietnam +2.5 percentage points).
Interestingly, February saw Japan, Israel, Thailand and Saudi Arabia – countries that normally account for less than 1% of all spam – make it into the Top 20.
The UK occupied twelfth place, distributing 2.24% of the total volume of spam.
Phishing
Links to phishing sites were found in 0.87% of all emails, an increase of 0.06 percentage points compared to January.
In February, PayPal (53.97%) and eBay (14.05%) remained the two most popular targets for phishers. HSBC (7.65%) and Facebook (6.05%) also maintained their third and fourth positions.

Organizations targeted by phishing attacks in February 2010
In February we recorded a phishing attack that was performed extremely carelessly. The message, sent on behalf of PayPal, required users verify their personal data. However, the fraudsters forgot to include the phishing link. Additionally, the PayPal logo was inserted unprofessionally – the recipients could only see a blue strip in the top left-hand corner instead of the picture.
The phishing attacks targeting Facebook users look very professional. Nobody could spot the forgery in the HTML version of the message. However, the link www.facebook.com.*********.com.pl that the user was supposed to click on has nothing to do with Facebook.
Malware in mail traffic
Malicious files were found in 1.18% of all emails, an increase of 1.11 percentage points compared with the previous month.
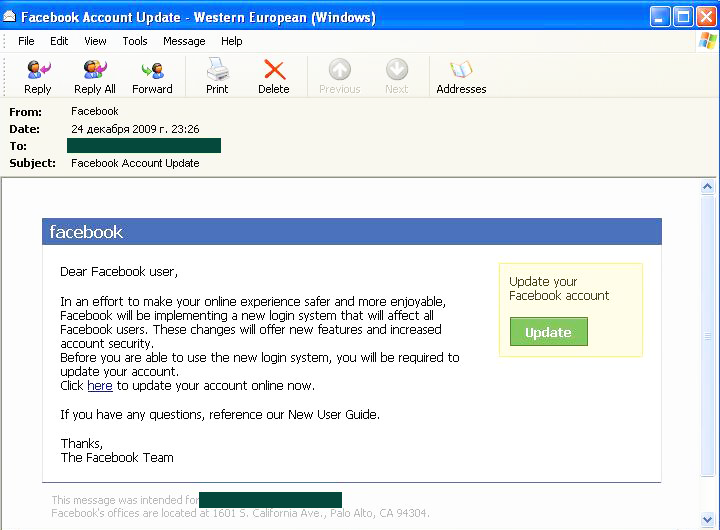
In February 2010, Facebook and HSBC attracted the attention of both phishers and fraudsters intent on distributing malicious programs. We recorded a bulk mail sent on behalf of Facebook in which users were asked to confirm their agreement to a new security policy which allegedly came into effect on that social network. The ‘agreement’ was attached to the email in the form of a zip archive. In fact, instead of a ‘user agreement’ the archive contained a malicious Trojan-Downloader program.
The mass mailing distributed in the name of HSBC did not contain any attachments. Following the best traditions of the phishers, the messages contained a link which the user had to click to confirm their online account activity. The link led to the hsbc.exe file (Backdoor.IRC.Zapchast.zwrc) which immediately tried to download itself to the victim’s computer.
Malware distributors also had the Amazon online store in their sights. The messages spread in the name of this organization offered the user a chance to view their prepaid order, the details of which were supposedly contained in the attached zip archive, which in fact was the executable file Trojan-Dropper.Win32.Agent.bqdn.
In February the fraudsters returned to their time-honored method of distributing malicious programs – sending out messages with sensational headings and texts trying to make users view the attached ‘video’. One such mailing purportedly contained scandalous photos of Britney Spears.
Interestingly, on St. Valentine’s Day we did not see the expected boom in e-cards. We presumed that the fraudsters would exploit the holiday to distribute their malware via fake e-cards, but the e-card spam just didn’t materialize.
Spam by category
The medication and health-related goods and services category, mostly advertising Viagra and weight loss pills, retained its lead among English-language spam with nearly 40% of the total volume of spam.
While advertising medications ‘for adults’, spammers exploited the theme of Valentine’s Day, stating that a night of passion was the best present that people could give each other for the holiday. The site of an online Canadian drugstore was consequently decorated in an appropriate style:

In the second half of February, spam mailings containing Viagra advertisements took on a rather original twist. As mentioned above, in February spammers showed interest in the popular Amazon online store and by exploiting fake Amazon notifications, the spammers distributed malicious attachments and advertised sites selling Viagra:

The link contained in the email certainly didn’t lead to Amazon.com! The user was in fact redirected to a webpage offering cheap medication.
The computer fraud category comes second in the English-language spam table, despite the amount of emails in this category decreasing slightly (-2 percentage points). The majority of messages contained fake lottery win notifications and Nigerian letters which exploited topical issues. In February the ‘Nigerians’ continued to collect money that they claimed was for the victims of the Haiti earthquake disaster, while innumerable lottery win notifications were distributed, many related to the World Cup.
Spammers advertising replicas of designer goods (-2 percentage points compared with January) stated that the best present for Valentine’s Day was a fake Rolex or other well-known brand of watch:
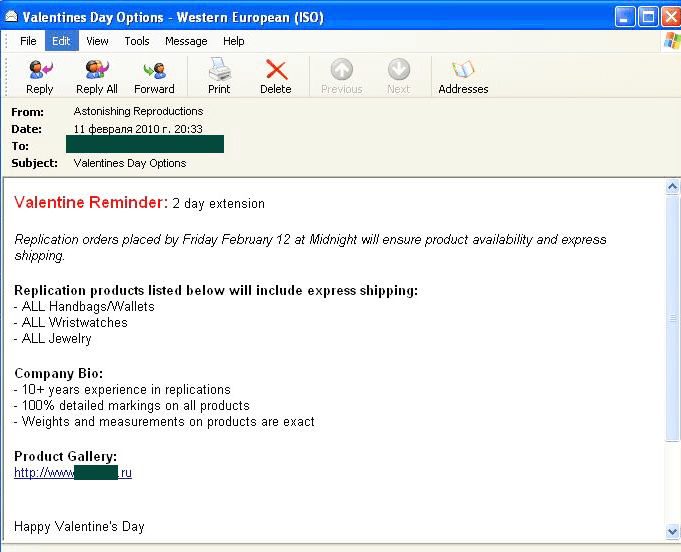
The share of the other goods and services category doubled when compared to the previous month (+4 percentage points). Many bulk mails advertised presents for St. Valentines Day. Spammers offered cheap flowers, a romantic message in a bottle, a Victoria’s Secret certificate, etc.
Spammer methods and tricks
Spammers advertising ‘medicinal’ goods proved to be most creative when finding ways to bypass filtering.
Links to the sites advertising weight loss pills and Viagra were sent in graphical attachments to emails, the pictures being hidden with background ‘noise’.
Additionally, in order to distribute Viagra on the eve of Valentine’s Day, spammers used a method that had already proved to be successful – creating background ‘noise’ with the help of figures:
Conclusion
The share of phishing emails in mail traffic remains the same as estimated. However, other threats await the user instead – including an increase in the number of malicious attachments and plenty of computer fraud spam.
February’s most noticeable event was the drastic decrease in the number of malicious links coming from the .cn domain region. This was caused by a tightening of the domain name registration rules in China. Now many bulk mails advertising Viagra or pornographic sites include links to domains registered in the .ru region.





























Spam evolution: February 2010