
Recent trends
- The amount of spam in email traffic remains practically unchanged compared to March’s figure and averaged 83%.
- Links to phishing sites were found in 0.02% of all emails, a decrease of 0.01 percentage points when compared to March.
- Malicious files were found in 1.24% of all emails, an increase of 0.748 percentage points compared with the previous month. Rogue antivirus programs were actively distributed in spam.
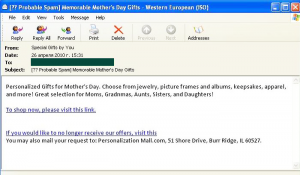
- In the run-up to Mother’s Day the Fake Designer Goods category regained its leading positions.
- In order to bypass filtering, fraudsters are using different pictures and randomly chosen parts of texts from literary works, as well as economic and political articles.
Spam in mail traffic
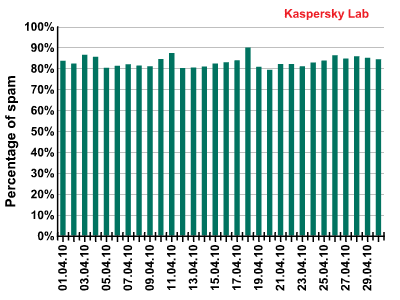
The amount of spam detected in mail traffic averaged 83% in April 2010. A low of 79.2% was recorded on 20 April with a peak value of 89.8% being reached on 18 April.
Spam in mail traffic in April 2010
Sources of spam
In April, the USA maintained its leading positions as the prime distributor of spam despite a decrease of 2.4 percentage points compared to March’s figure. The situation is likely to change in May because India is catching up with the USA – during April it distributed only slightly less (0.6 percentage points) spam than the USA. Vietnam is hot on the heels of the leaders – the share of spam originating from this country was over double, averaging 11.6%, which is only 0.7 percentage points behind the figure for the USA.
Russia almost dropped out of the Top 5 having distributed less spam compared with the previous month (-2.47 percentage points). It was replaced by Vietnam in third position. Italy showed up unexpectedly in fourth position, given that in March it only occupied 14th place.
In April, noticeable changes happened to spam flows from Romania (+1 percentage points) and Germany (-1 percentage points). Additionally, Saudi Arabia reentered the Top 20 taking 13th place with 2.2% of all the spam distributed.
The amount of spam distributed from the UK decreased slightly in April compared to the previous month, accounting for 2.29%.
Phishing
Links to phishing sites were found in 0.02% of all emails, a decrease of 0.01 percentage points when compared to March.
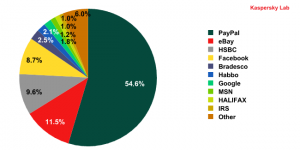
PayPal and eBay remain the most popular targets for phishers, with 54.6%, (+9.2 percentage points) for Paypal and 11.5% (-3.9 percentage points) for Ebay. In April, HSBC with 9.6% (+2.1 percentage points) and Facebook with 8.7% (+1 percentage points) swapped their previous month’s positions, to become third and fourth place respectively.
Organizations targeted by phishing attacks in April 2010
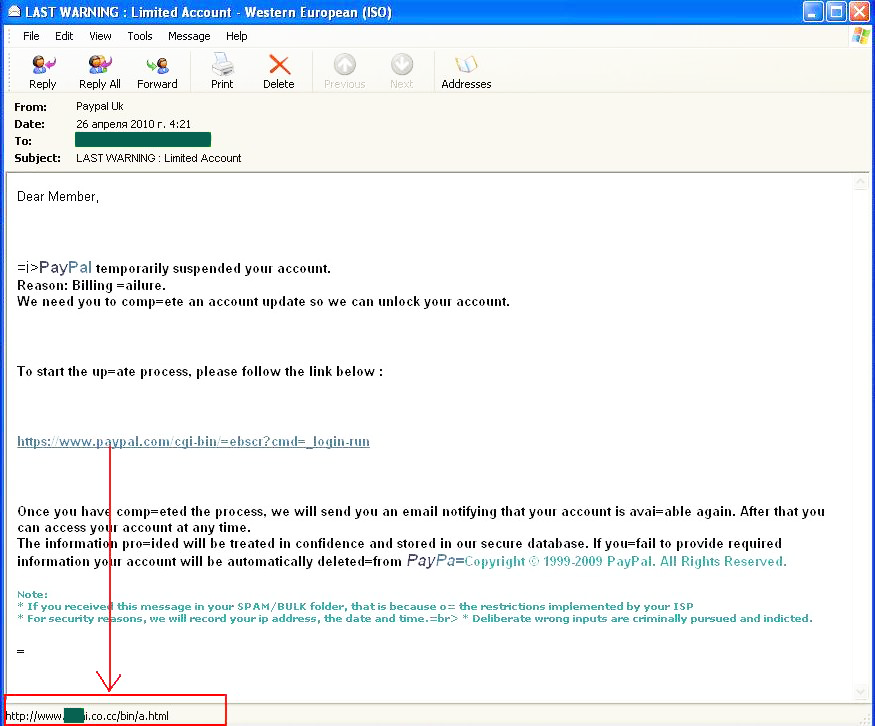
Among all of the phishing emails registered in April, one PayPal attack is worthy of special mention. Spammers used their standard trick of informing a user that their account had been blocked and in order to enable it again a user was required to follow a link to a site where they then had to enter their login and password.
It should be noted that the link in the email is a very skilful imitation of the link to the PayPal site. However, the address in the screenshot leaves no doubt as to where a user is in fact going to be redirected to.
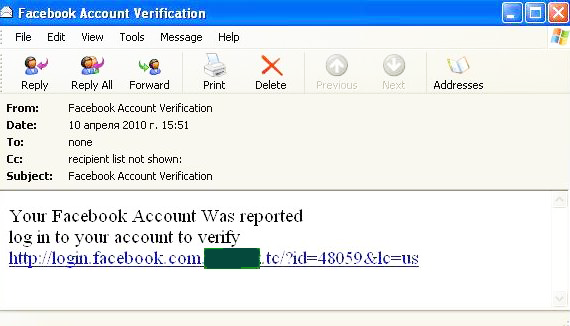
Facebook is once again the focus of the phishers’ attention. The emails aimed at parting the users of this social network from their login credentials were particularly laconic in nature:
Fraudsters did not even bother to hide the phishing link. Their carelessness suggests that users are not very observant. In truth, the phishers’ estimations are reasonably justified – unfortunately users all too often fall victim to the cybercriminals, even when the cybercriminal’s website is only a poor imitation of the real thing and should be completely obvious to the user.
Of course, phishers targeted other organizations besides those included in our rating. For example, a major attack on the Alliance & Leicester was registered in April.
The approach used for this attack is also well-known – the message informs the user about several registered erroneous attempts to access the system from their client ID. A user must verify their account to prove account ownership. Of course, an unwary user will verify their account on the phishing site and their credentials will very soon fall into the fraudsters’ hands.
Malware in mail traffic
Malicious files were found in 1.24% of all emails, an increase of 0.74 percentage points compared with the previous month.
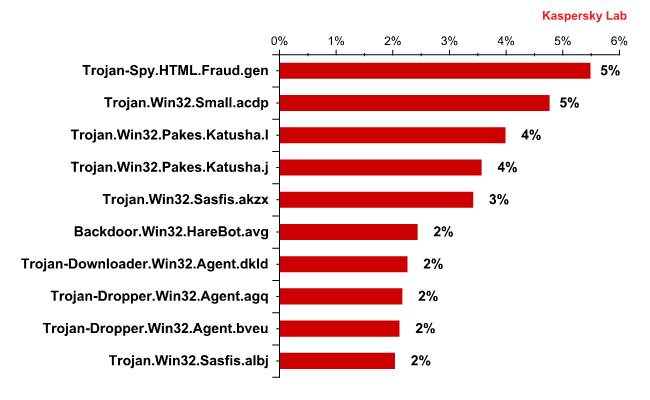
This month’s leader in the malware Top 10 is again Trojan-Spy.HTML.Fraud.gen. This Trojan’s main purpose in life is to collect users’ credentials. As before, over 45% of all the Trojans of this type originated from the UK. Another 11% of emails infected by Trojan-Spy.HTML.Fraud.gen were distributed from the USA.
Interestingly, seven out of April’s Top 10 malicious programs are in one way or another connected with rogue antivirus programs. For example, Trojan.Win32.Small.acdp, Trojan.Win32.Sasfis.akzx, Trojan-Downloader.Win32.Agent.dkld, Trojan-Dropper.Win32.Agent.bveu and Trojan.Win32.Sasfis.albj download or install other malware samples which in their turn download a rogue antivirus program to a user’s computer. The Trojan.Win32.Pakes.Katusha.j packer which comes forth in the rating is generally used for packing FraudTools, while its cousin, Trojan.Win32.Pakes.Katusha.l helps to pack Fraudload.
Trojan-Dropper.Win32.Agent.agq, which occupies 8th position in the malicious Top 10, is nothing but a porn dropper. When downloaded, this malicious program opens porn pictures and installs other malware on an infected computer.
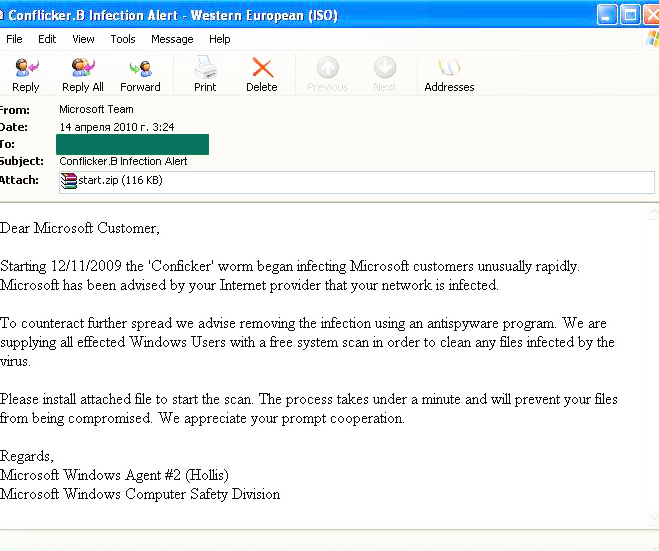
Additionally, April saw the distribution of bulk emails that contained ‘pure’ rogue antivirus programs. For example, Trojan.Win32.FakeAV.jo , 24th in the rating, was distributed as a genuine antivirus program which was allegedly recommended by Microsoft to treat the famous Conficker (Kido) Trojan. Interestingly, the word ‘Conficker’ in the header of the message became ‘Conflicker’.
Overall, nearly 60% of malicious programs belonging to the Trojan.Win32.FakeAV family were distributed in European countries, mostly Germany, Holland, France and the UK, but also in the USA and Japan. This can be explained by the fact that users in developed countries are more concerned about their computers’ security than the users in developing countries, which makes it easier for fraudsters to persuade them to download a rogue antivirus program.
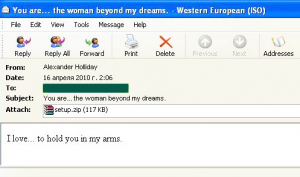
One batch of emails containing minimal text and headed ‘You are…the woman beyond my dreams’ and the message ‘I love…to hold you in my arms’ also had a ‘setup.zip’ archive attached with a setup.exe file that was in fact yet another offspring of the FakeAV family – Trojan.Win32.FakeAV.jw.
Such bulk emails usually contain an executable file named something like ‘My Fotos.gif’ which allows the true file extension to be hidden by relating it to the text in the message. It’s not completely clear what the spammer means by combining romantic text with the unmasked name of the executable file. Could it be that users are supposed to think that downloading the program will allow them to hold the woman of their dreams in their arms? Spammers probably think that users already know WHAT the attachment holds and expect them to click on the archive to see pictures of beautiful women.
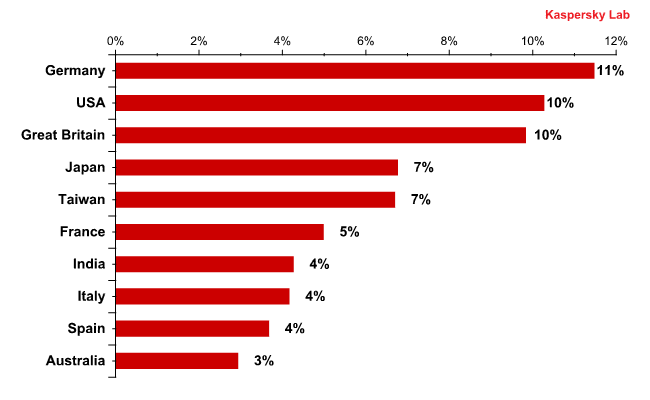
The graph below shows the Top 10 list of countries from which malware was distributed via email.
As we may see, the developed countries occupy the leading positions. This is caused by the fact that fraudsters have much more chance to obtain profit by attacking users from wealthier countries where each user has a credit card and an online banking or an e-pay system account.
Spam by category
The Medications and Health-Related Goods and Services category retained the lead for English-language spam. In April this category’s share averaged 30%, whilst for a time during the second half of the month it even exceeded 45-46% of the total amount of spam. In the ‘Spammer methods and tricks’ section we will describe the latest scam being used to distribute bulk emails advertising fake medication.
In April the Computer Fraud category again came second. Here’s a deplorable statistic: nearly 20% of all English and other European language spam comprised Nigerian letters, fake lottery win notifications or emails from ‘Nigerian brides’.
In the run-up to Mother’s Day spammers became more active, with many of them advertising fake designer goods. In April, the amount of such bulk emails averaged 16% of the total volume of spam, an increase of 3 percentage points compared with the previous month.
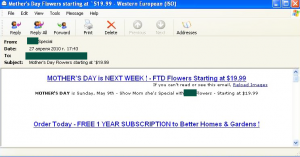
Mother’s Day also saw the distribution of bulk emails offering cheap flowers. These emails belong to the Other Goods and Services category whose share of the total volume of April’s spam was not very big – just over 4%.
The Personal Finance category’s share of western spam remains unchanged, accounting for about 7%.
Spammer methods and tricks
Distributors of Viagra continue perfecting their game in order to bypass filtering. In March they used a variety of different pictures followed by a large chunk of literary text. In April, they broadened the theme of the pictures used in the same bulk email. This time the images contained happy couples, girls, geishas and for some reason, tableware. All this was of course offered alongside the pills that they were advertising.
In April, bulk emails also contained spam text. In the left hand screenshot the text is printed on a white background and the width of the lines is random. In the two screenshots on the right hand side the background is grey and the lines are printed full-width. The texts are mostly literary in nature or reprints of economic or political articles. Sometimes they are just empty words making no sense at all.
Conclusion
In April, the situation generally remained stable with the percentage of spam in email staying relatively unchanged. India and Vietnam came very close to being the prime distributors of spam. If the amount of spam originating from these two countries continues to grow, they may soon topple the USA from its position as leader.
As was anticipated, the amount of phishing emails remained at a very low level, whilst contrary to our expectations the quantity of malware in mail traffic rose to the sort of levels experienced in February. Since the beginning of 2010 it has been fluctuating – it either decreases to 0.6-0.7% or rises to around 1.2%. Whilst such fluctuations cannot be called considerable, two interesting trends should certainly be noted: in April, malware mostly targeted users in developed countries, and spam was actively used to distribute rogue antivirus programs.
The spammers didn’t develop any new methods for bypassing filters during April; they just reworked their old tricks a little.























Spam evolution: April 2010