
As we mentioned in a previous blog post, every time there is news of global interest, cybercriminals try to exploit that interest for their own malicious purposes. The death of Osama bin Laden was no exception – it was used in spam as well as black hat SEO.
We have detected two spam mailings capitalizing on the news of Bin Laden’s death, both of which were used to distribute malware.
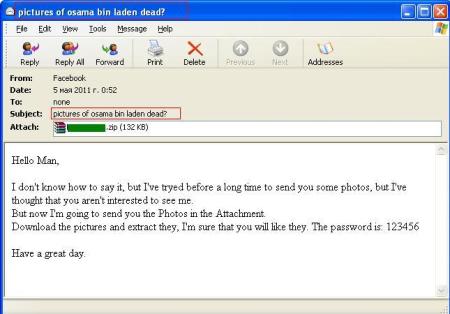
One included a password-protected ZIP archive. The message subject was: “pictures of osama bin laden dead?”
What is strange about the mailing is that the text was taken from a standard spam message which is supposedly sent by a girl who wants to introduce herself to a man and is asking him to have a look at pictures of her that are attached.
The archive contained malware detected by Kaspersky Lab products as Trojan-Dropper.MSIL.Pakes.b.
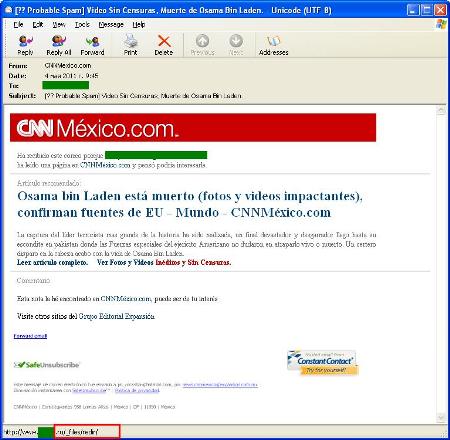
The other malicious mailing exploiting Bin Laden’s death included links supposedly to a video showing the moment he was killed.
The message was in Spanish and was designed to look like a news mailing from CNN News. However, instead of leading to the site of the well-known news service, links in the message took users to a page on a Russian domain which dropped Backdoor.Win32.Ruskill.v on the user’s machine.
Because a number of world events have been attracting the general public’s attention of late, spammers have increasingly been using ‘fake news’ to distribute malicious code.
I would like to urge users once again to be careful. Remember that your curiosity and carelessness could result in serious problems for your computer and the loss of personal data or even money.






















Spam and the death of Osama bin Laden