
Quarterly highlights
Spam through Google services
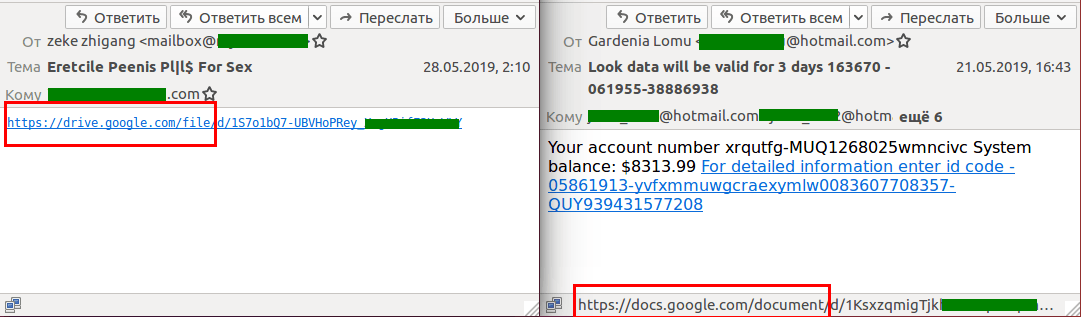
In the second quarter of 2019, scammers were making active use of cloud-based data storage services such as Google Drive and Google Storage to hide their illegal content. The reasoning behind this is simple: a link from a legitimate domain is seen as more trustworthy by both users and spam filters. Most often, such links point to text files, tables, presentations, and other documents containing text and a link, say, to an advertised product or phishing page.
Also this past quarter, cybercriminals actively used Google Calendar to send out invitations to non-existent meetings, adding phishing links to fields filled out by the organizer.
Through Google Photos, fraudsters shared photos accompanied by a comment containing information about a money transfer and a contact email address. It’s a traditional scheme: before receiving the promised money, the victim is asked to pay some kind of “service fee”, whereupon the attackers vanish into thin air.
Google Forms, a tool for creating forms and surveys, was also actively used by cybercriminals to harvest users’ personal data and send commercial spam.
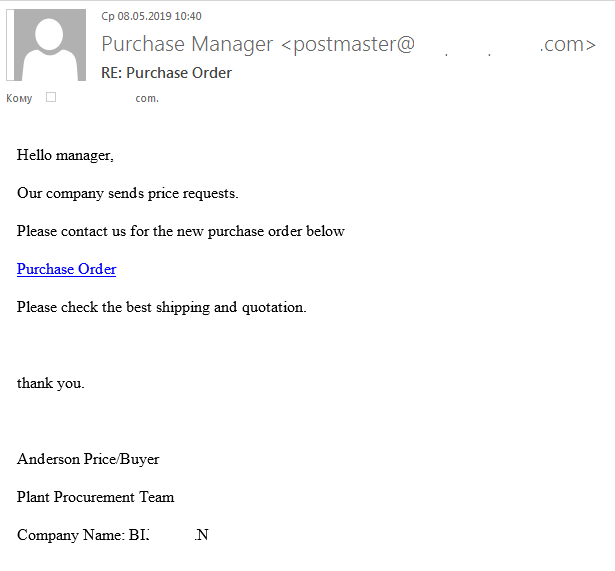
Bitcoin ransomware targets businesses
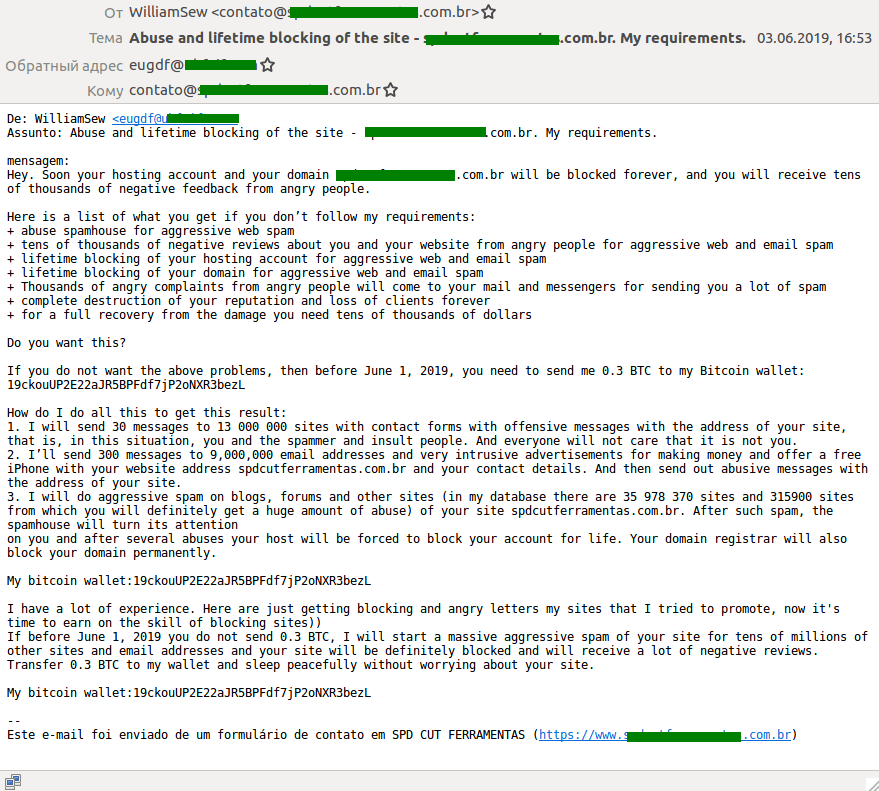
Until recently, the main blackmailing tool of cryptocurrency-hungry scammers was sextortion. However, their attention gradually began to switch from individual users to companies, which began to receive threats of reputational harm to their website.
Once more, it’s very straightforward. A request for the transfer of 0.3–0.5 bitcoin (around $4,200) is sent to the company’s public email addresses (or via its online feedback form). In case of refusal, the cybercriminals threaten to send abusive messages supposedly from the victim company through the contact forms of 13 million websites, as well as to mail out aggressive spam in the company’s name to 9 million email addresses. After that, they claim that the Spamhaus Project will recognize the victim’s website as a source of spam and block it forever.
Global sporting events
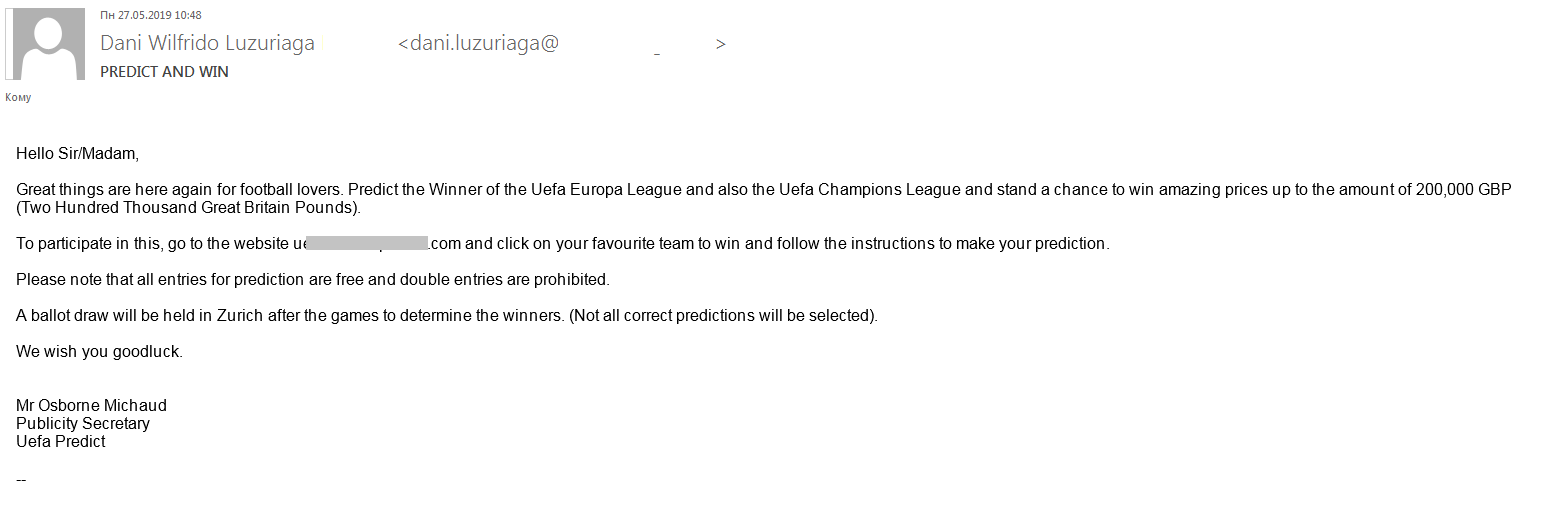
Major sporting events attract not only millions of fans, but also numerous scammers looking to exploit them. As such, in Q2 we detected a spam mailing timed to coincide with the 2019 UEFA Europa League Final in Baku. Recipients were asked to guess the winner of the match and earn the chance to win up to £200,000.
For this, they had to follow the link in the message, provide some personal data, and predict which team would win. The information collected could then be used for fraudulent attacks and more spam mailings. There’s also an extended version of this scheme: after some time, the victim receives a notification that their prediction was correct and their winnings are ready for collection — for which a small fee is required, naturally.
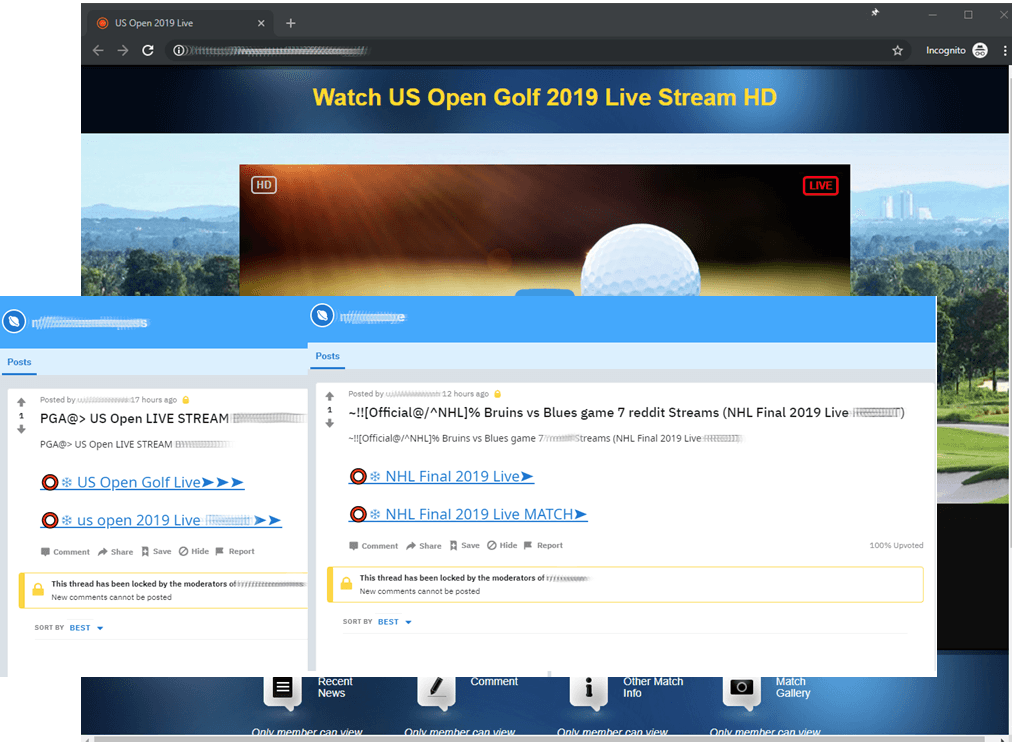
But scammers did not limit themselves to soccer fans. Q2 saw equally stellar golf and hockey tournaments in the shape of the Stanley Cup and the US Open.
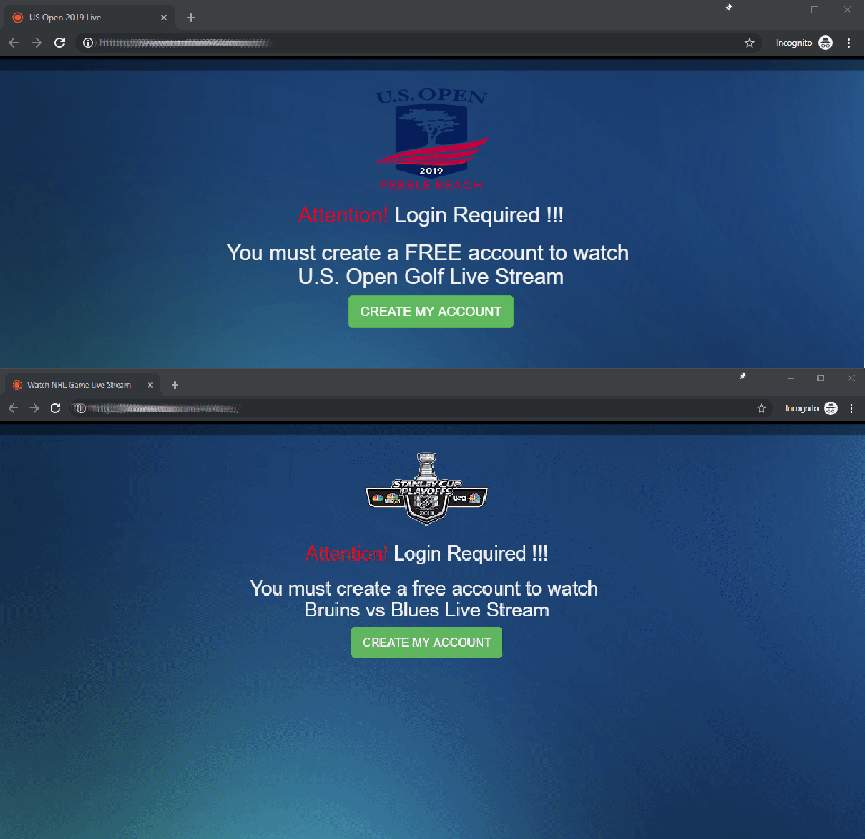
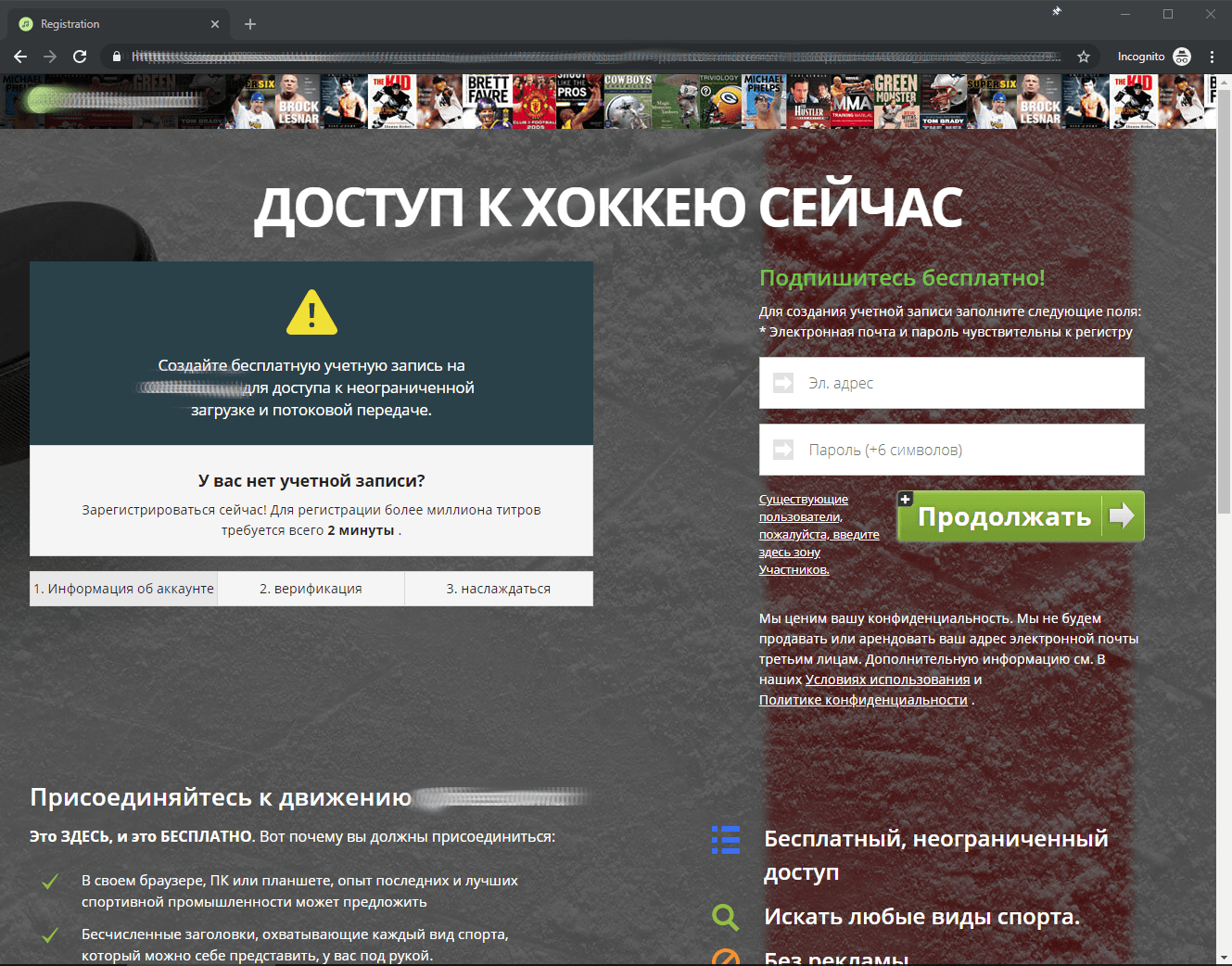
Users were invited to watch broadcasts of these events, which, soon after starting, were blocked by a window prompting to set up an account:
On clicking the Create My Account button, a page opens asking to provide an email address and create a password:
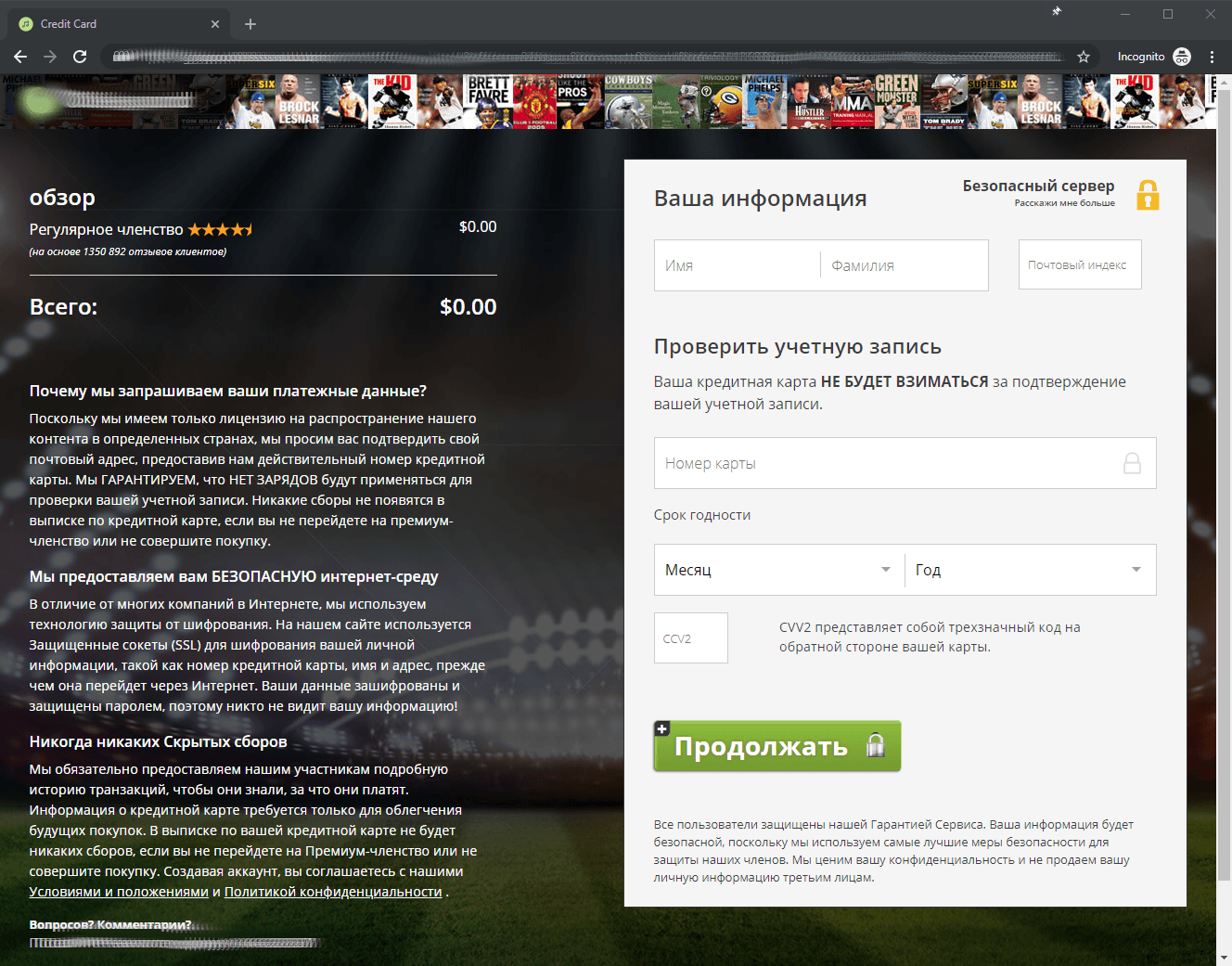
However, on filling out all the fields and clicking the Continue button, the victim is required to verify the account, for which some more personal information is required — namely, bank card details.
The fraudsters report that the money will not be debited from the card, rather the payment data is needed simply for verification, since customers should supposedly be located in a country where the website is licensed to distribute such content. But even if you decide to undergo this “verification,” you won’t see the end of the match, of course. Instead, your data and payment information will be in the hands of the scammers.
Global TV and movie premieres
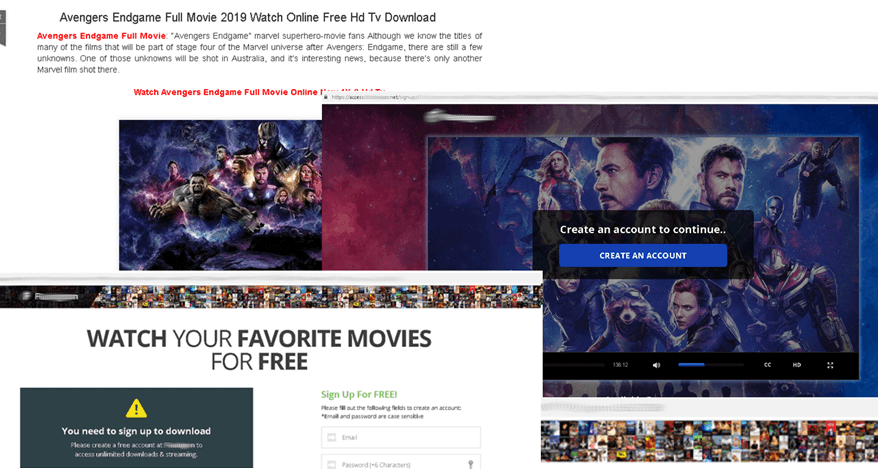
As we already wrote several times in past reports, fraudsters keep a close eye on world events and adapt their schemes to them. We found a ruse similar to the previous one, aimed at fans of the Marvel Cinematic Universe ahead of the release of the latest Avengers installment:
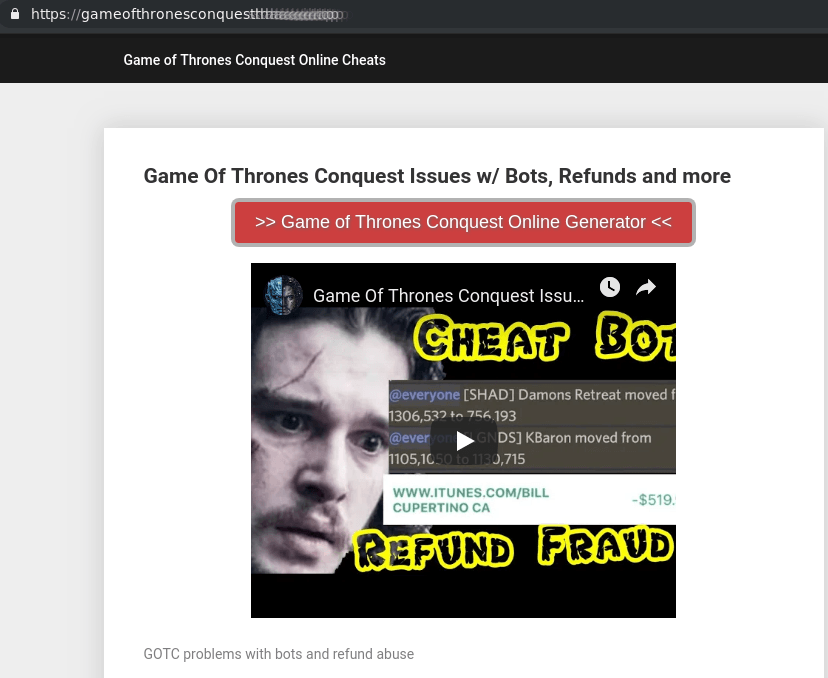
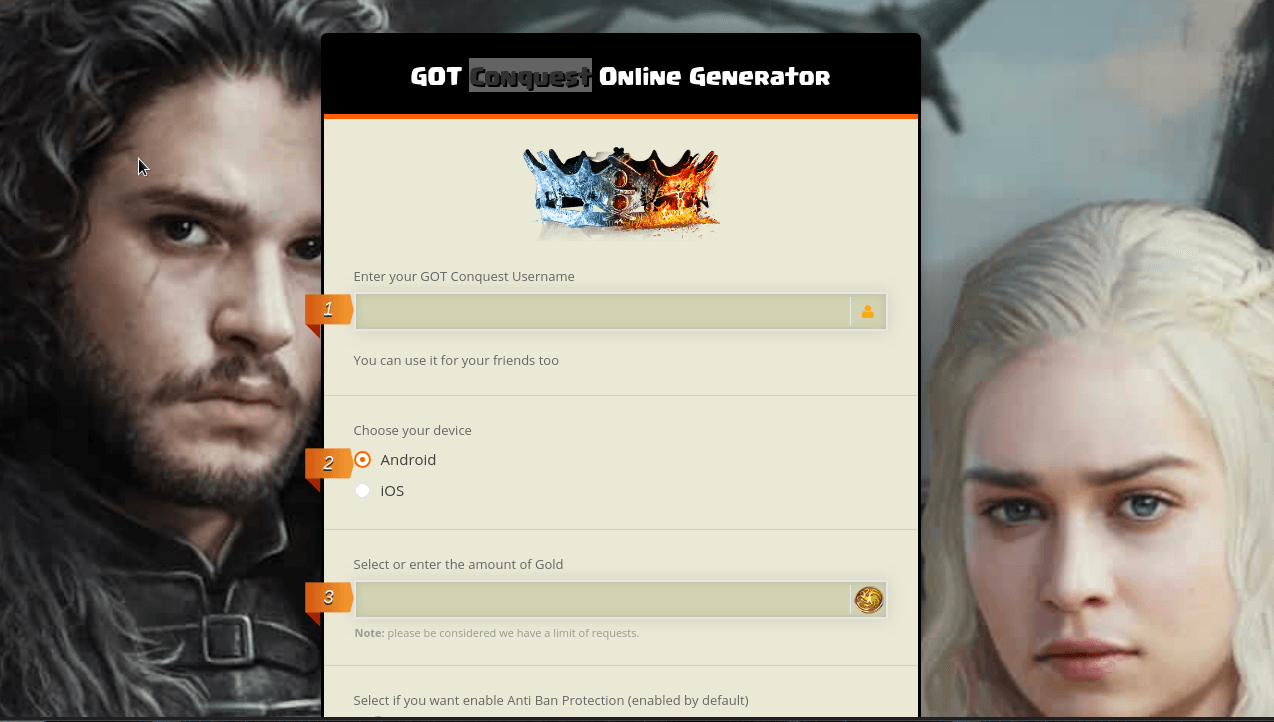
But Q2 wasn’t all about Avengers. It also witnessed the long-awaited premiere of the last season of Game of Thrones, and our statistics showed that the following week the number of scam resources mentioning the series increased fourfold against the month before the release. One of the most common fraudulent schemes was simulating the generation of codes for Game Of Thrones Conquest, a spin-off mobile game.
To get a code, the user had to fill out a form, specifying the number of coins that they would like to receive in the game.
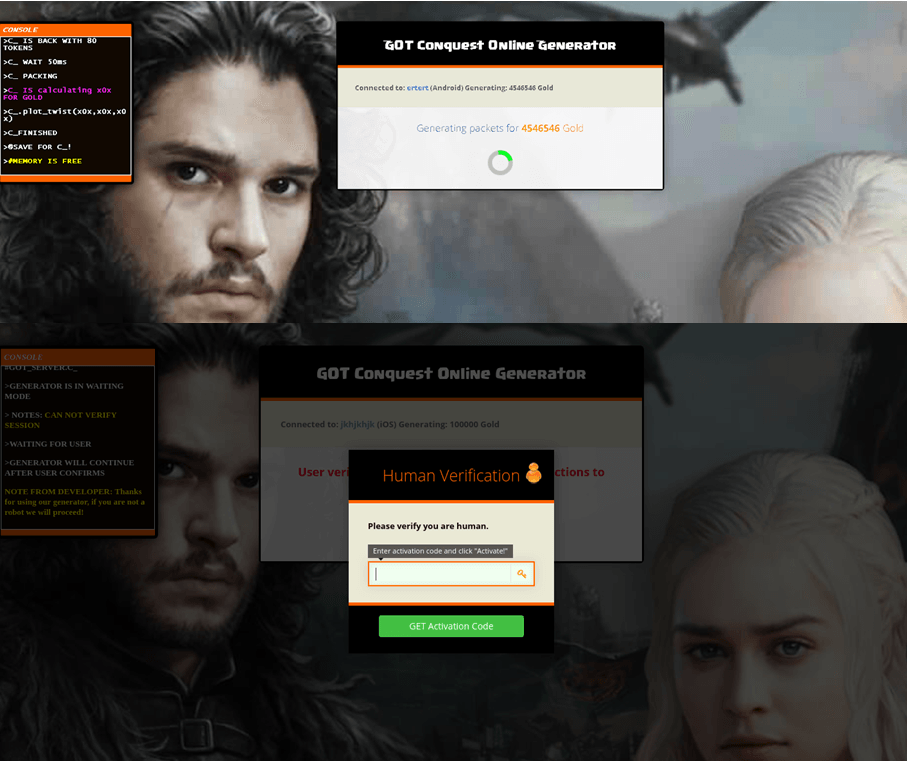
After completing all the fields, the system goes into “code generation” mode. For the sake of authenticity, on-screen messages appear about connecting to servers and the like.
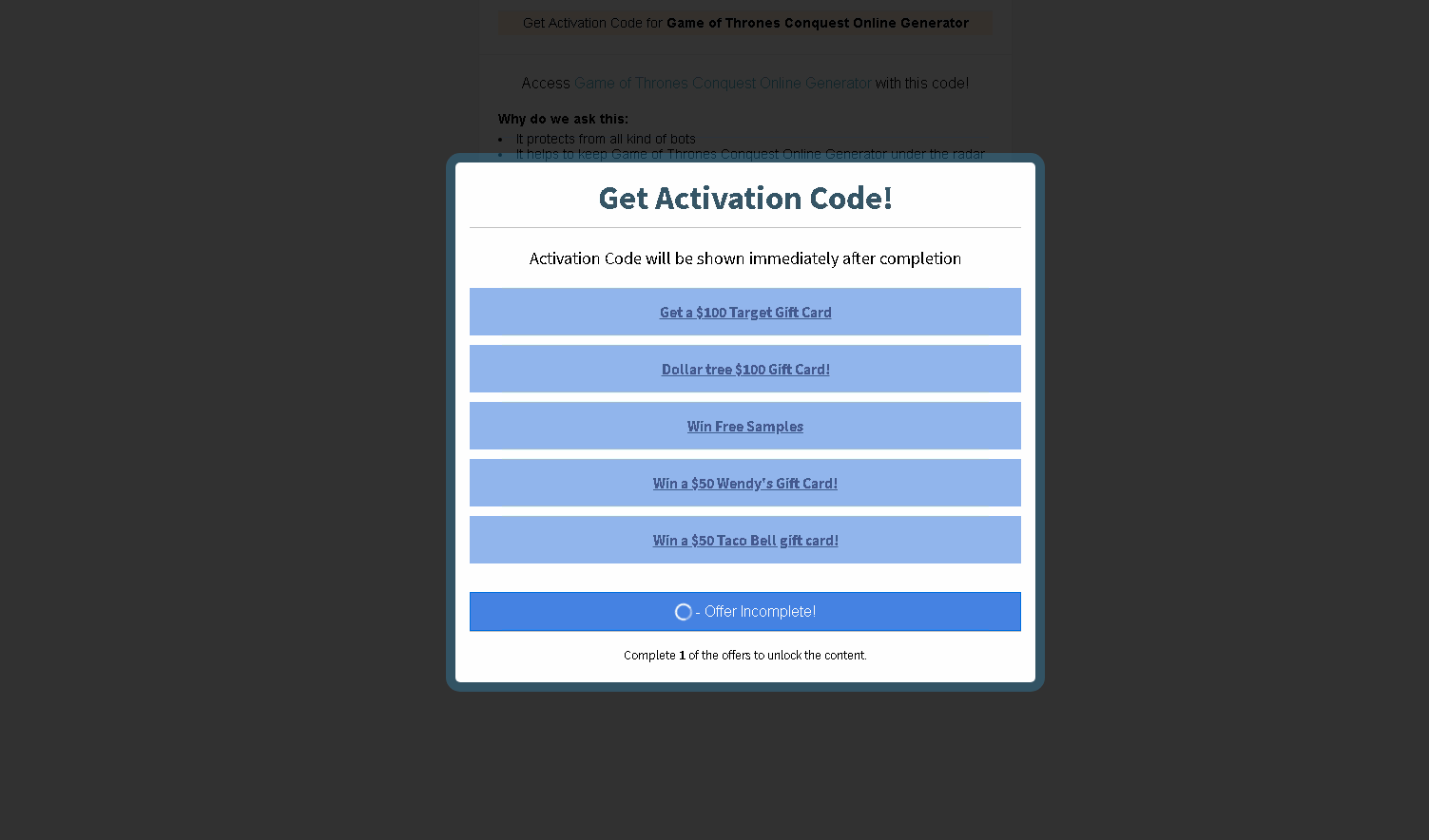
The generated code is not shown to the user until non-robot status is confirmed. This requires clicking a link and completing some kind of task.
At this point, the user might be asked to take a survey, play a lottery, provide details (phone number, postal address), subscribe to a paid SMS service, install adware (which redirects all user searches, harvests information about online activity, and resists deletion), or do something else. The nature of the task is determined by the partner network, one of whose sites the user is redirected to. The network, for its part, is selected based on the country of residence: it should match the regional language and local advertising laws.
The upshot is unpleasant, but predictable: the victim is either led around various partner sites until they tire of filling out forms and playing lotteries, or they are rewarded with a random set of symbols that has nothing to do with a genuine code and only mimics the format.
Tax refunds
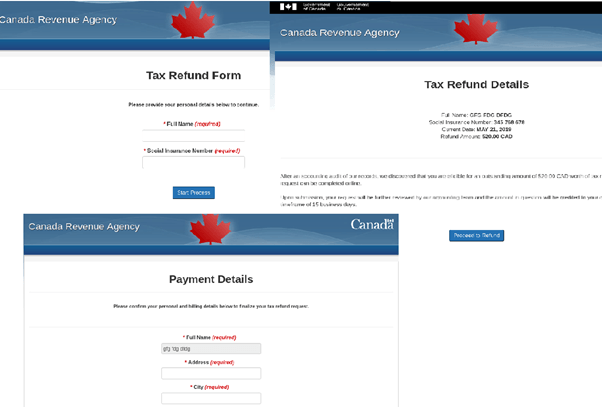
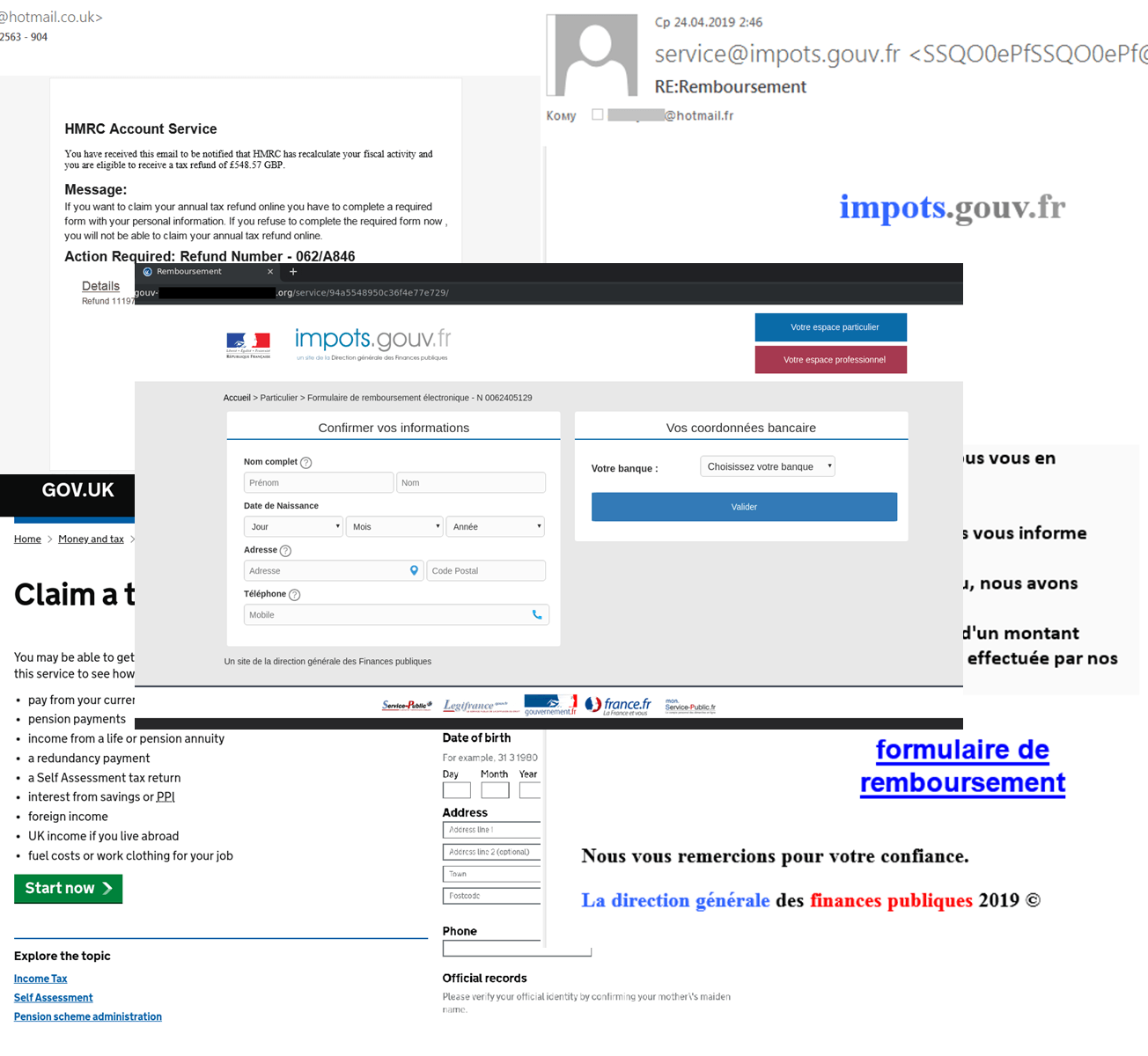
The second quarter of the year sees the deadline for filing tax returns and tax refund applications in many countries. This is utilized by scammers who capitalize on users’ carelessness and fear of missing the deadline. Phishing emails are sent out saying that the user is entitled to a tax refund (large enough to arouse interest). The reason given for the rebate might be a standard law procedure or a system error.
Some mailings employ a well-known technique whereby the user is given a limited amount of time to take action. For instance, in an email seemingly from HMRC (Her Majesty’s Revenue and Customs, the UK tax service), victims had to follow the link and fill out the form immediately, while fake CRA (Canada Revenue Agency) letters were giving the recipient 24 hours, otherwise a tax refund would not be possible.
Phishing pages at the end of links in such messages are aimed at stealing various personal information: account passwords, answers to secret questions, names of close relatives, their dates of birth, full information about bank cards, including CVV code, and much more. In some examples, on clicking a link, a chain of actions had to be completed, such as entering basic information (name, social security number), followed by more detailed data, and then at the final step specifying bank card numbers.
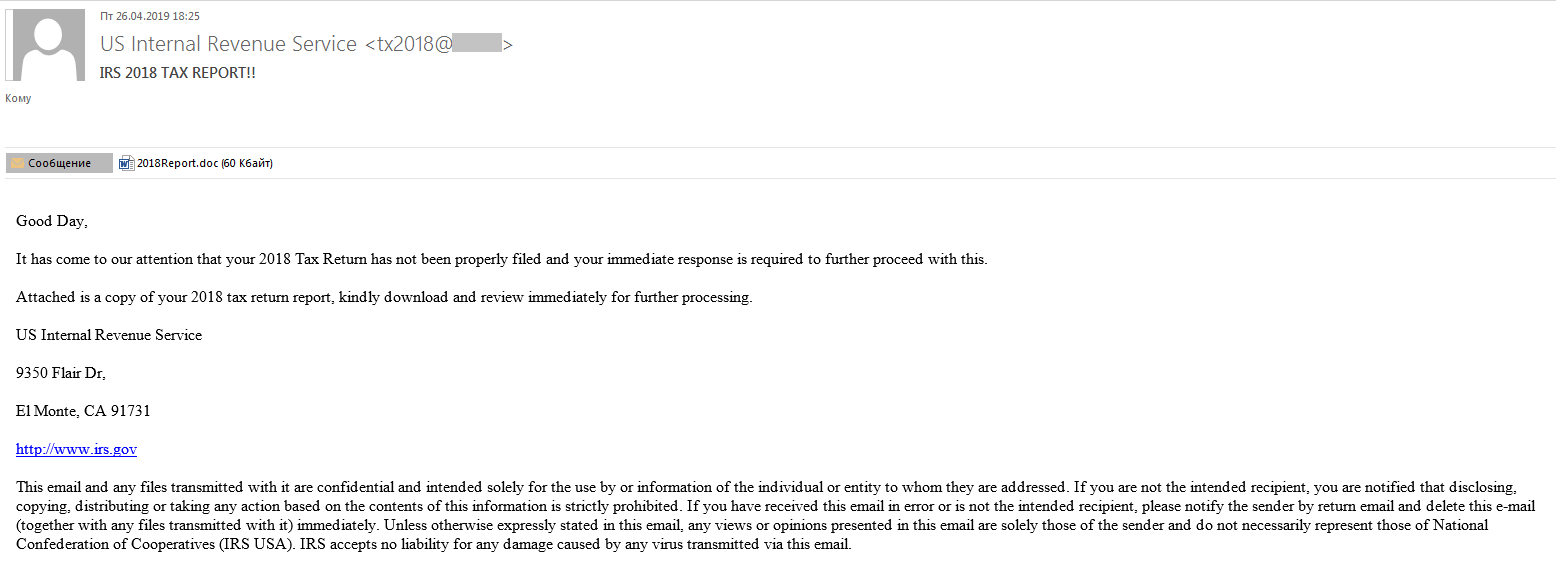
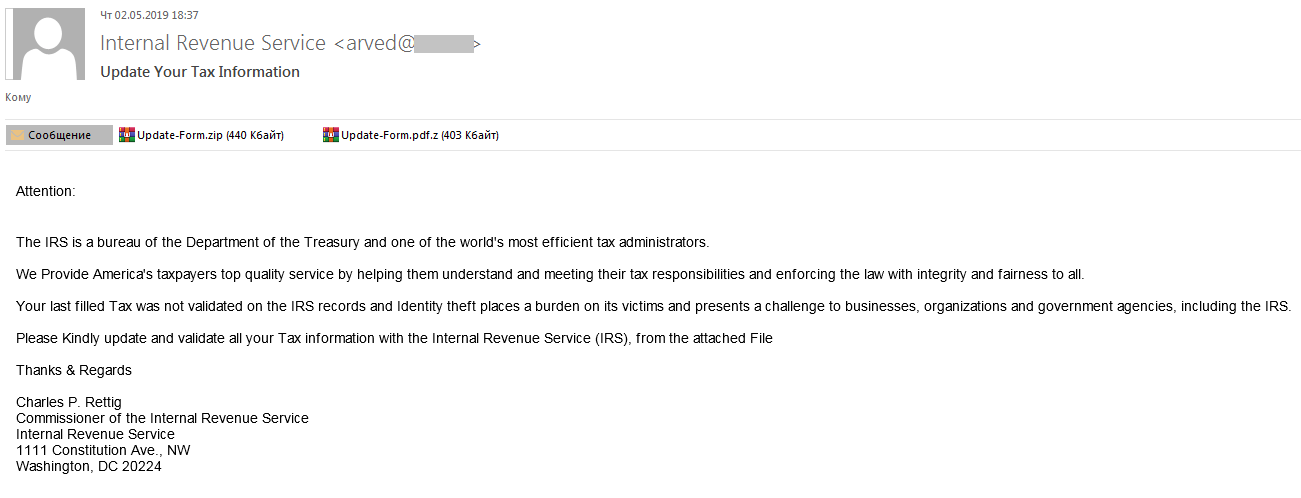
Besides phishing links, scammers also sent malicious attachments. Cybercriminals tried to convince users to open them by citing errors in the return form that were in need of urgent correction. The malicious file, detected as Trojan-Downloader.MSOffice.SLoad.gen, was disguised as a copy of the return form. If the user gave permission to run the macro, another malicious executable was downloaded and launched.
Another bulk email attachment was detected as Trojan.Win32.Agentb.jofi, a multifunctional backdoor that provides remote access to the infected machine. Its capabilities include monitoring keystrokes, stealing passwords for browsers and Windows accounts, recording video from the computer’s webcam, and executing commands received from C&C servers.
Tourist phishing
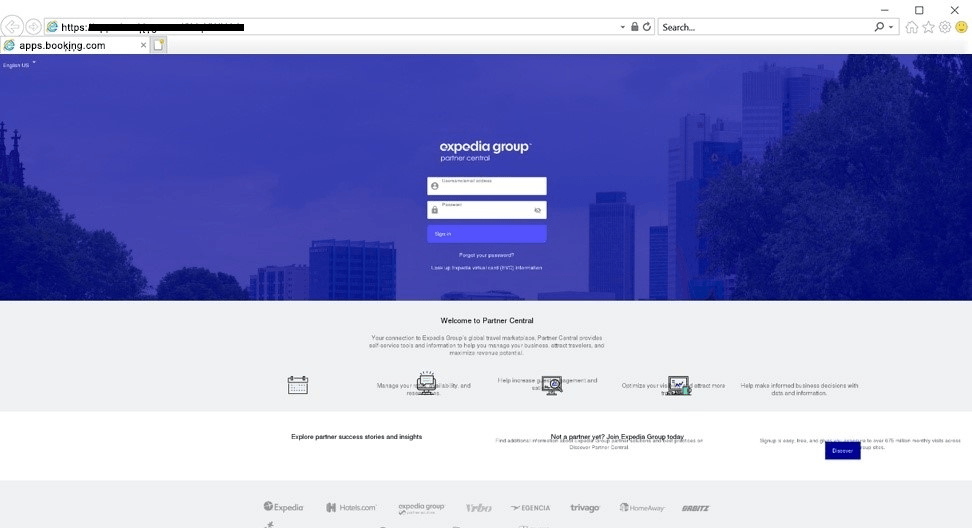
In anticipation of the summer holidays, we registered an increase in the number of phishing mailings aimed at travelers. Everything was in play: Airbnb emails with accommodation offers at tempting prices, phishing sites mimicking Booking.com, fake travel sites, and so on.
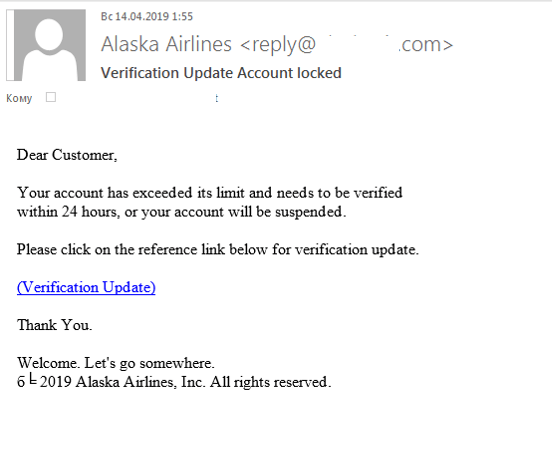
Neither did attackers ignore airlines — both large international carriers and small local firms. For example, here’s a mailing we detected informing customers that their account has exceeded some kind of limit and requesting confirmation of account data within 24 hours.
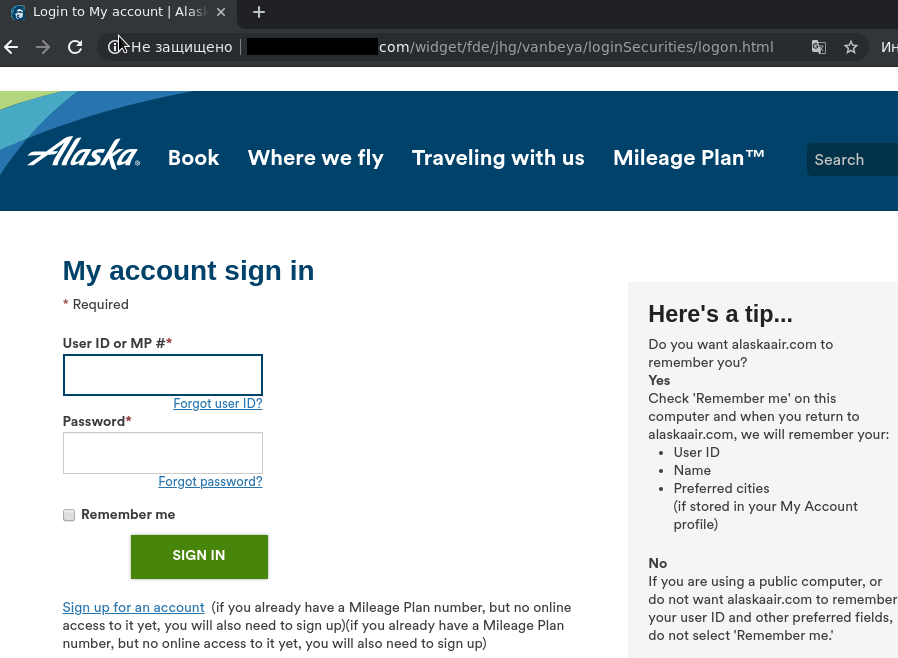
Those who swallowed the bait and clicked the link were redirected to a fake site where they were prompted to fill out an “authorization” form. The data, of course, went straight to the attackers.
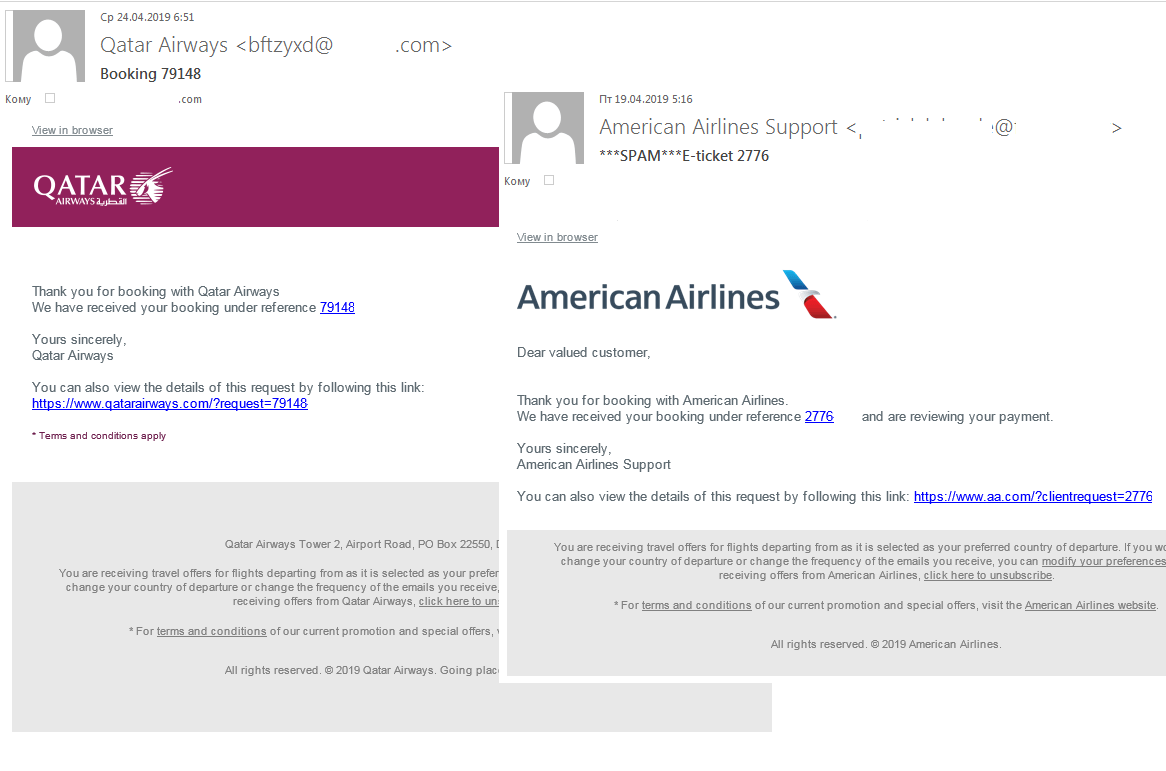
Messages in another scam mailing scheme looked like official ticket booking confirmations. The fraudsters used the same phishing link for the booking number and the “view details” option. However, instead of the promised data, the user was taken to a page specially set up to steal personal information.
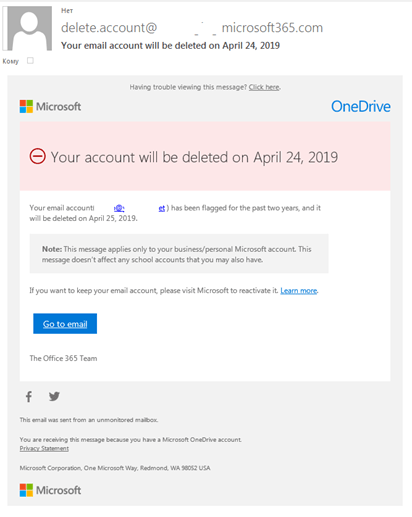
Phishing emails supposedly from email services
The vast majority of scam emails aimed at stealing login credentials for email services imitate messages from the email services themselves. Scammers try to make their fake messages as believable as possible: the sender’s address is similar to the real one, the message uses the correct logos, and there are links to official resources as well as signatures.
The email text, the scammers also try to make convincing. It usually starts by reporting some kind of problem with the victim’s account, followed by a description of what needs to be done, which entails either following a link or opening an attachment. To intimidate the recipient further, mention is made of what can happen to the account in case of failure to perform the specified actions (deletion, suspension), with specific time frames.
Atypical examples are also encountered: the message might be disguised as business correspondence (usually such messages contain a malicious attachment), and the text may not mention email accounts at all. On clicking the link in such an email, the user is taken to a page where they are asked to enter email account details in order to view a (nonexistent) document.
Statistics: spam
Proportion of spam in mail traffic
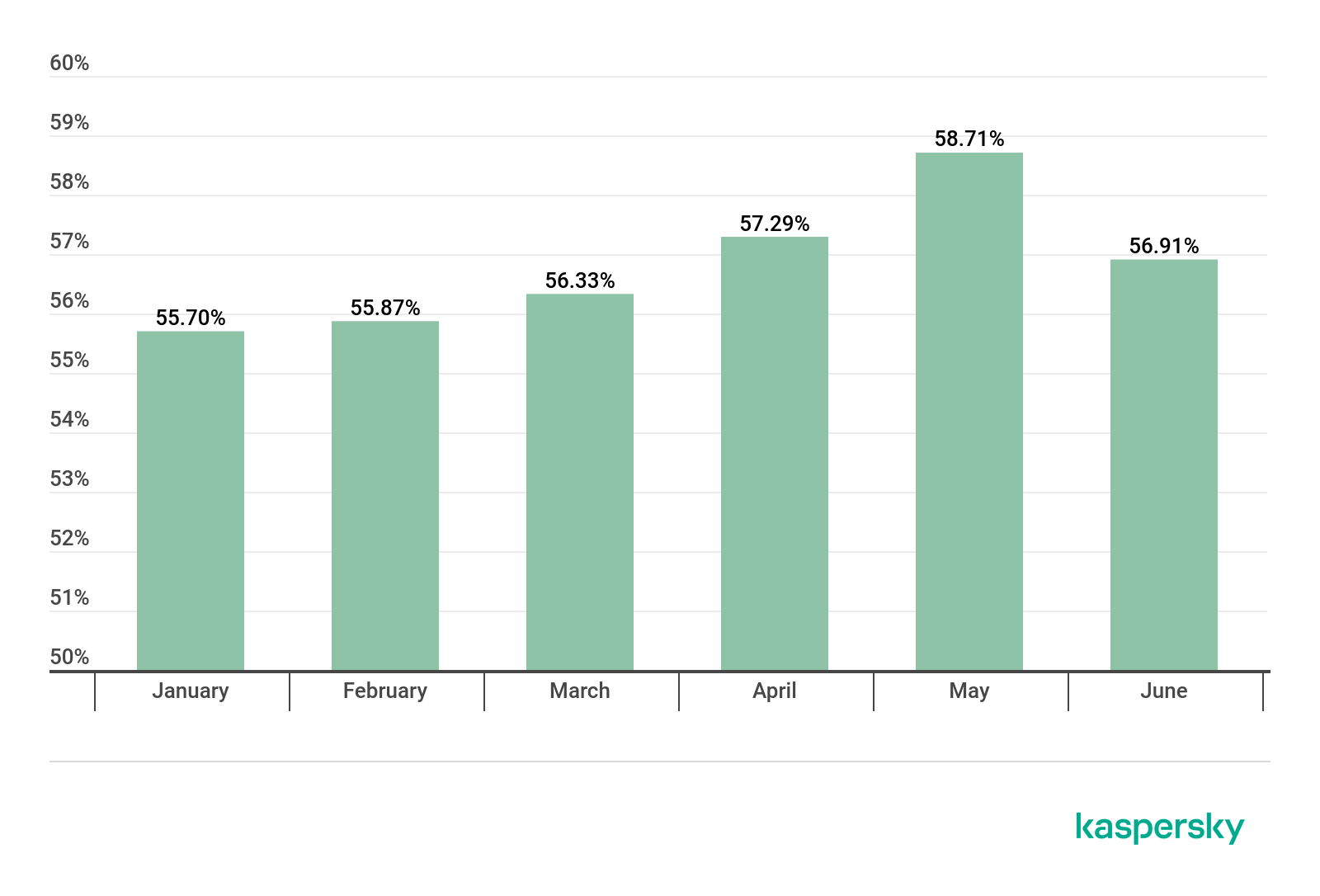
Proportion of spam in global mail traffic, Q1 2019 – Q2 2019
In Q2 2019, the largest share of spam was recorded in May (58.71%). The average percentage of spam in global mail traffic was 57.64%, up 1.67 p.p. against the previous reporting period.
Sources of spam by country
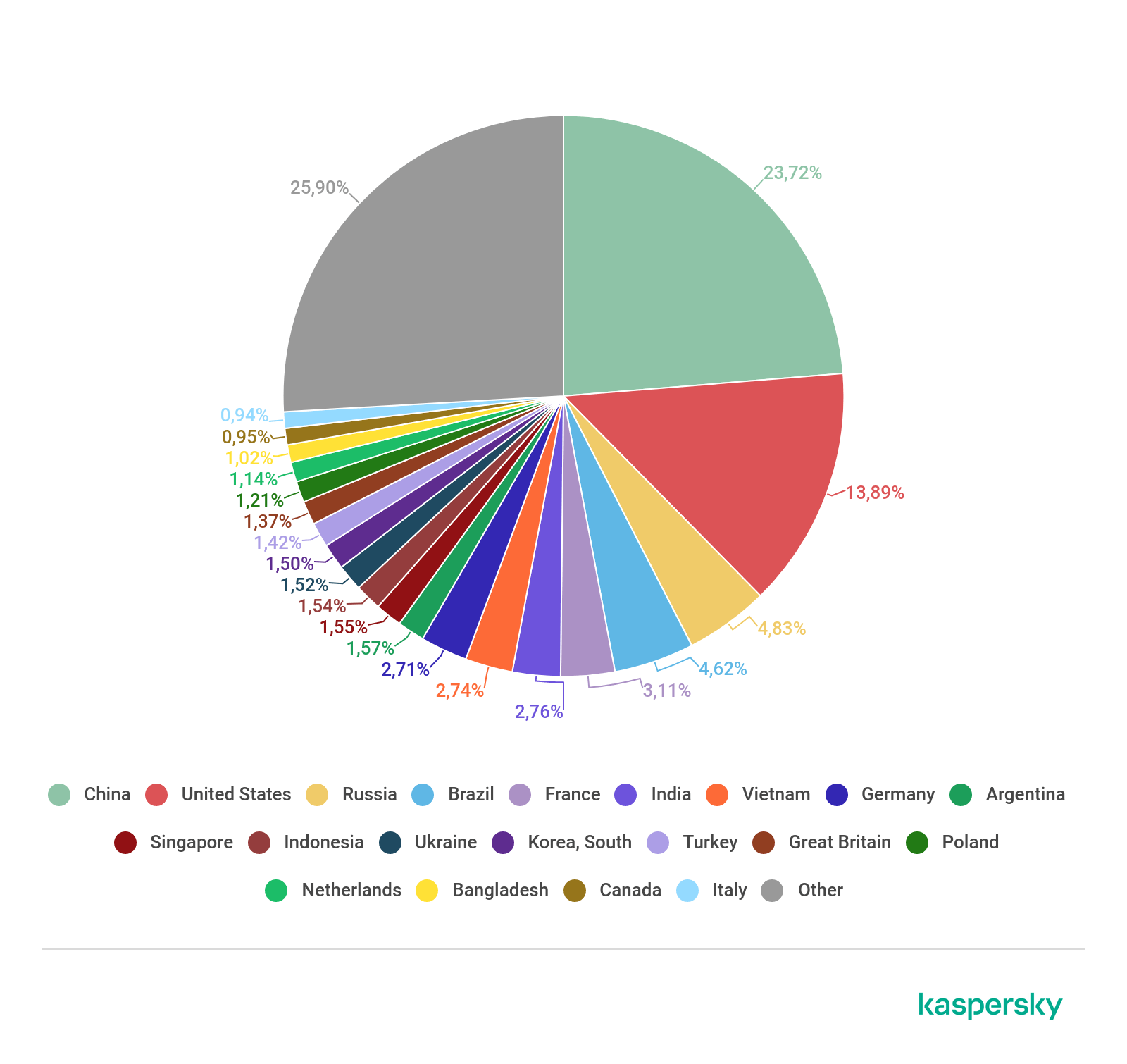
Sources of spam by country, Q2 2019
The top lines in the list of spam sources remain the same: in first place was China (23.72%), the US came second (13.89%), Russia remained third (4.83%), and Brazil took fourth (4.62%) — only the fifth line differs from last quarter: France (3.11%) pushed Germany out of the Top 5.
Spam email size
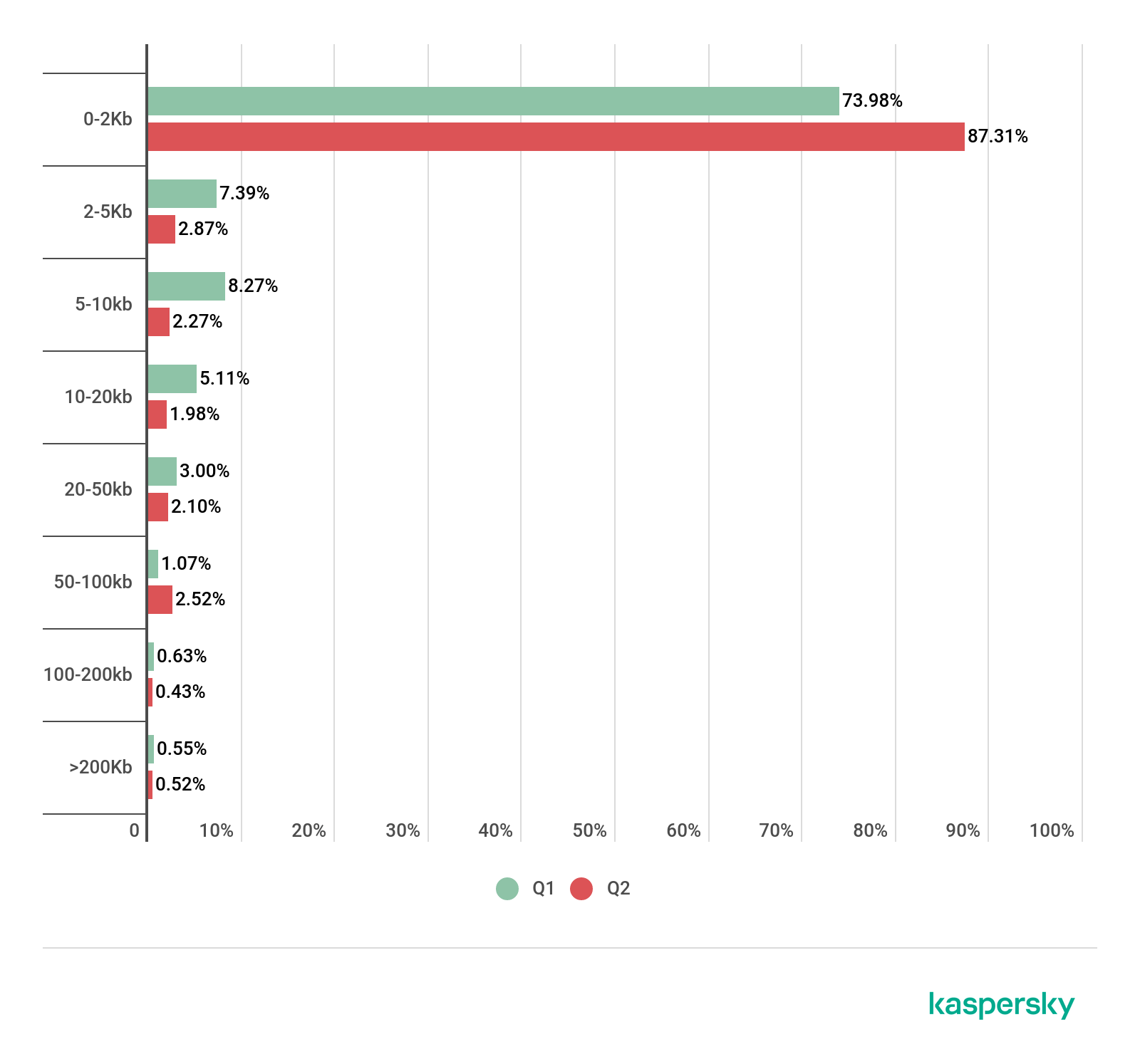
Spam email size, Q1 and Q2 2019
In Q2 2019, the share of very small emails (up to 2 KB) in spam rose against Q1 by 13.33 p.p. to 87.31%. Meanwhile, the share of 5–10 KB messages fell by 4.52 p.p. to 2.27%. Messages 10–20 KB in size were fewer in numbers than most other ones: their share was 1.98%, down 3.13 p.p. on last quarter. The proportion of 20–50 KB messages amounted to 2.10%, versus 3% in the previous reporting period.
Malicious attachments, malware families
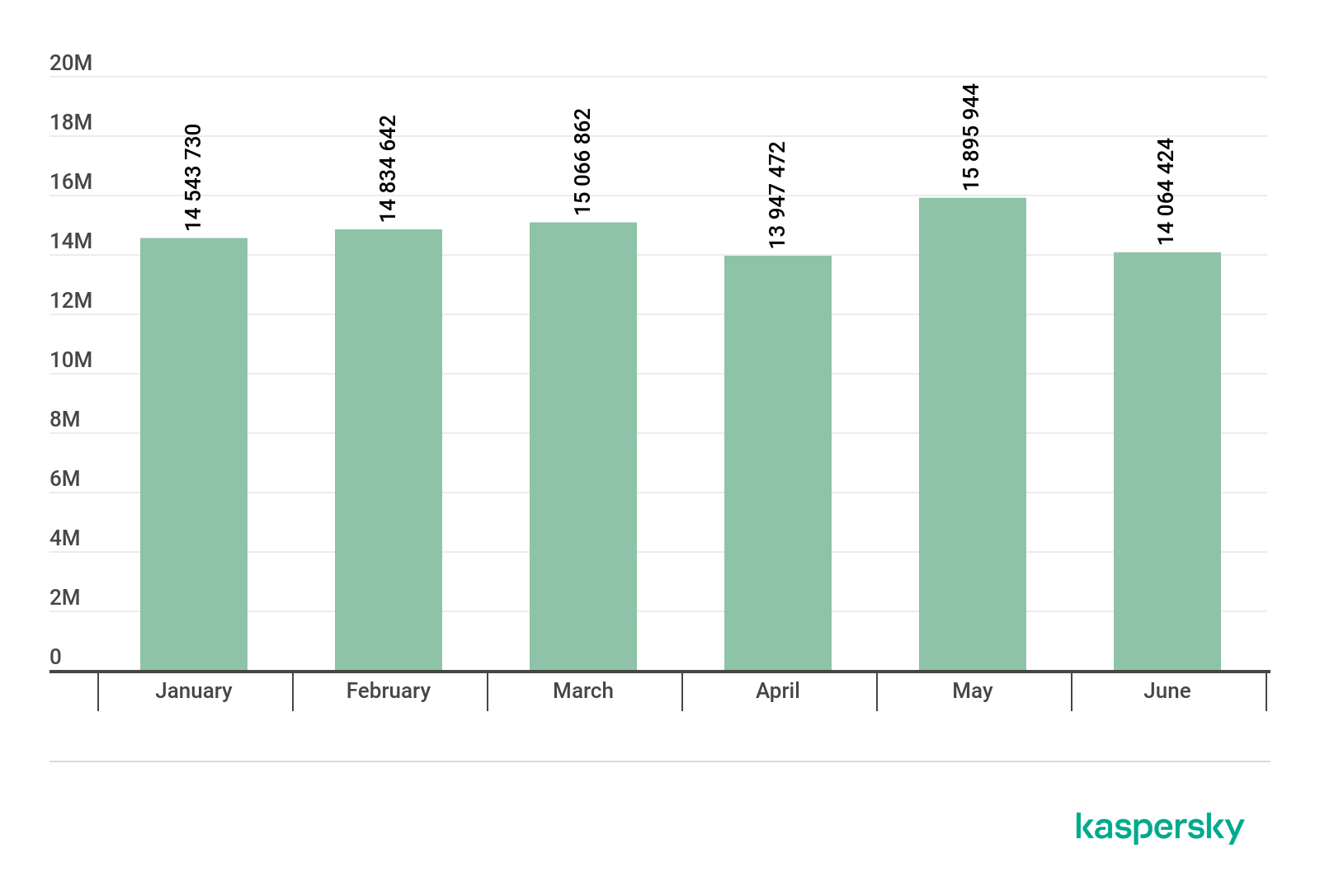
Number of Mail Anti-Virus triggerings, Q1 2019 – Q2 2019
In Q2 2019, our security solutions detected a total of 43,907,840 malicious email attachments. May was the quarter’s hottest month with almost 16 million mail antivirus triggers, while April was the coolest (2 million fewer).
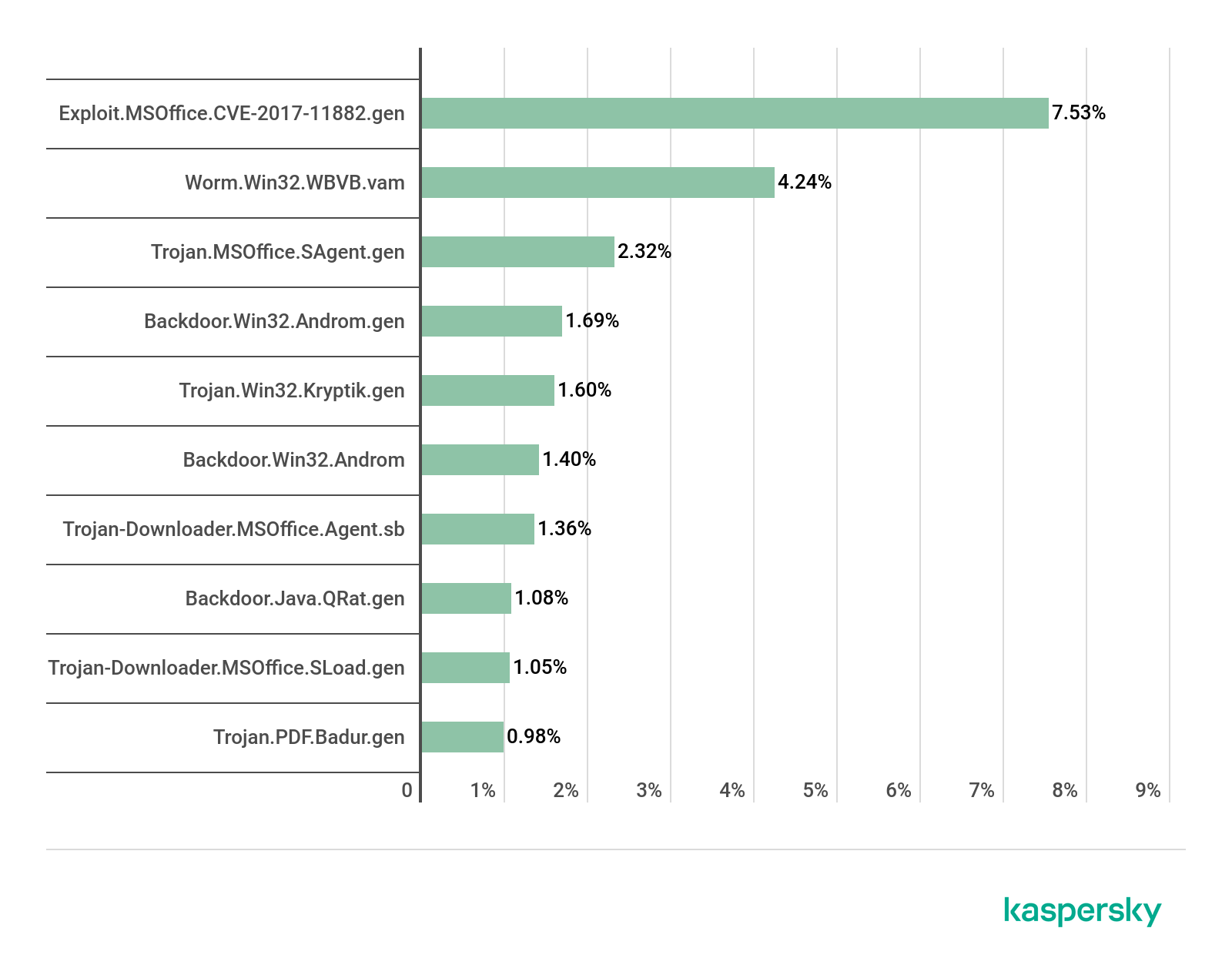
Top 10 malicious attachments in mail traffic, Q2 2019
In Q2, the malware Exploit.MSOffice.CVE-2017-11882.gen (7.53%) came first in terms of prevalence in mail traffic. In second position was Worm.Win32.WBVB.vam (4.24%), and Trojan.MSOffice.SAgent.gen (2.32%) took third.
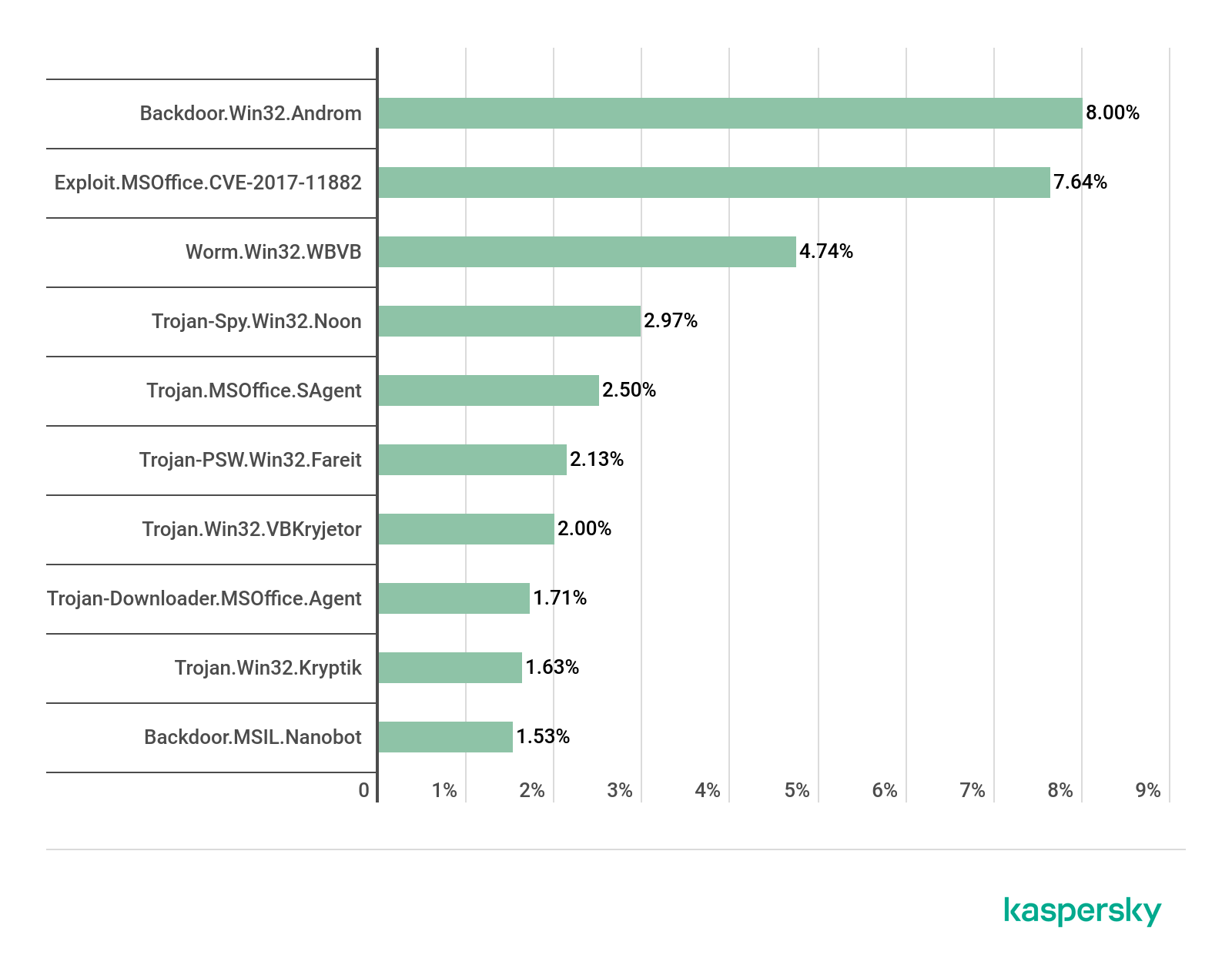
Top 10 malware families in mail traffic, Q2 2019
Looking at malware families, we see a slightly different picture. In first place is the Andromeda bot family (8.00%), whose individual members took only fourth and sixth places in the malware Top 10. Close behind is the Exploit.MSOffice.CVE-2017-11882 family (7.64%), a set of exploits for the Microsoft Office suite. In third place is the Worm.Win32.WBVB family of worms (4.74%), written in Visual Basic.
Countries targeted by malicious mailshots
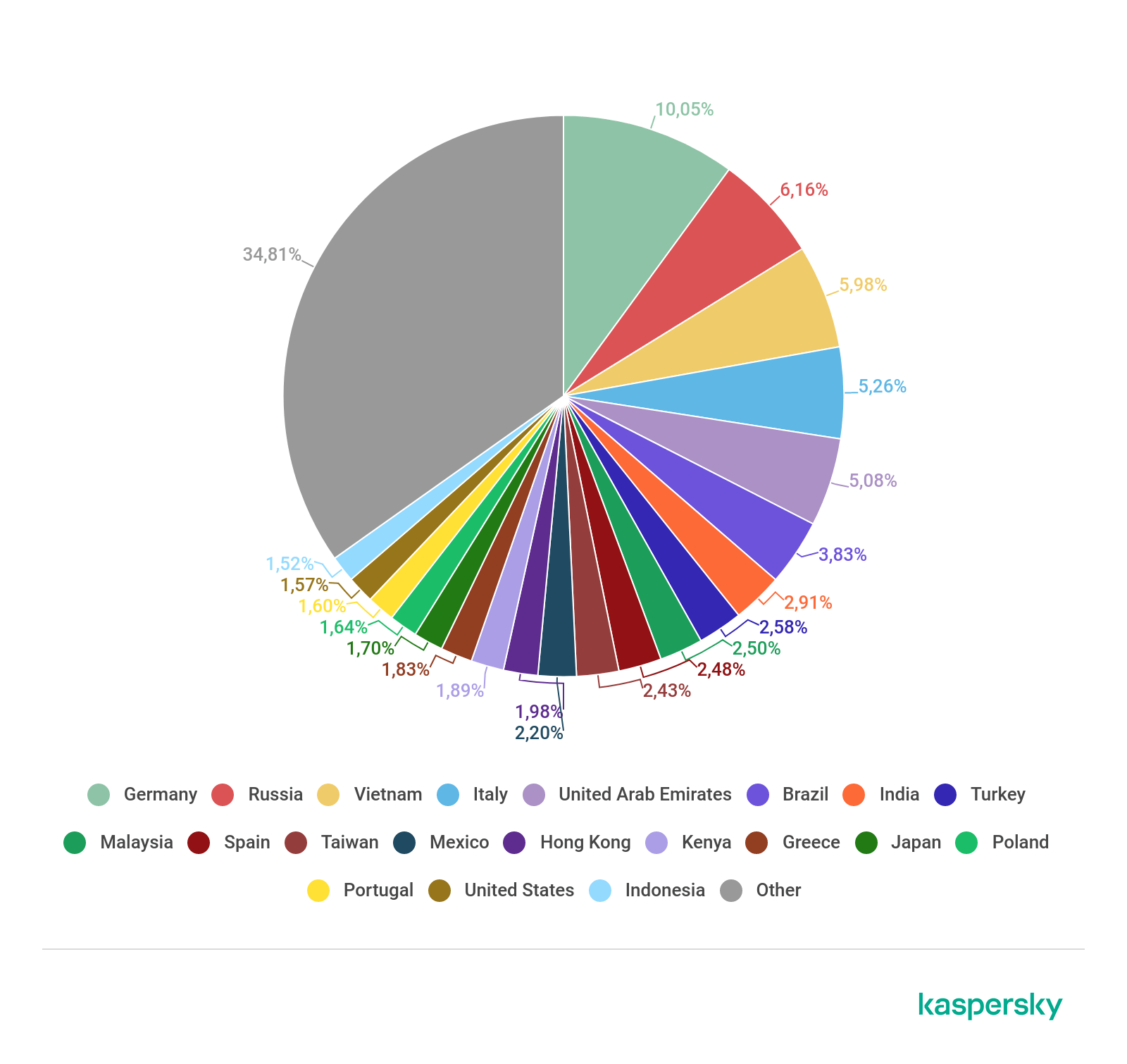
Countries targeted by malicious mailshots, Q2 2019
Germany continues to occupy top spot by share of mail antivirus triggerings, posting 10.05% this quarter. Russia finished second (6.16%), nudging Vietnam (5.98%) into third.
Statistics: phishing
In Q2 2019, the Anti-Phishing system blocked 129,933,555 attempts to direct users to scam websites. 12.34% of all Kaspersky Lab users worldwide experienced an attack.
Attack geography
The country with the largest share of users attacked by phishers in Q2 2019 was Greece (26.20%), up from sixth place in the quarter before having added 10.34 p.p.
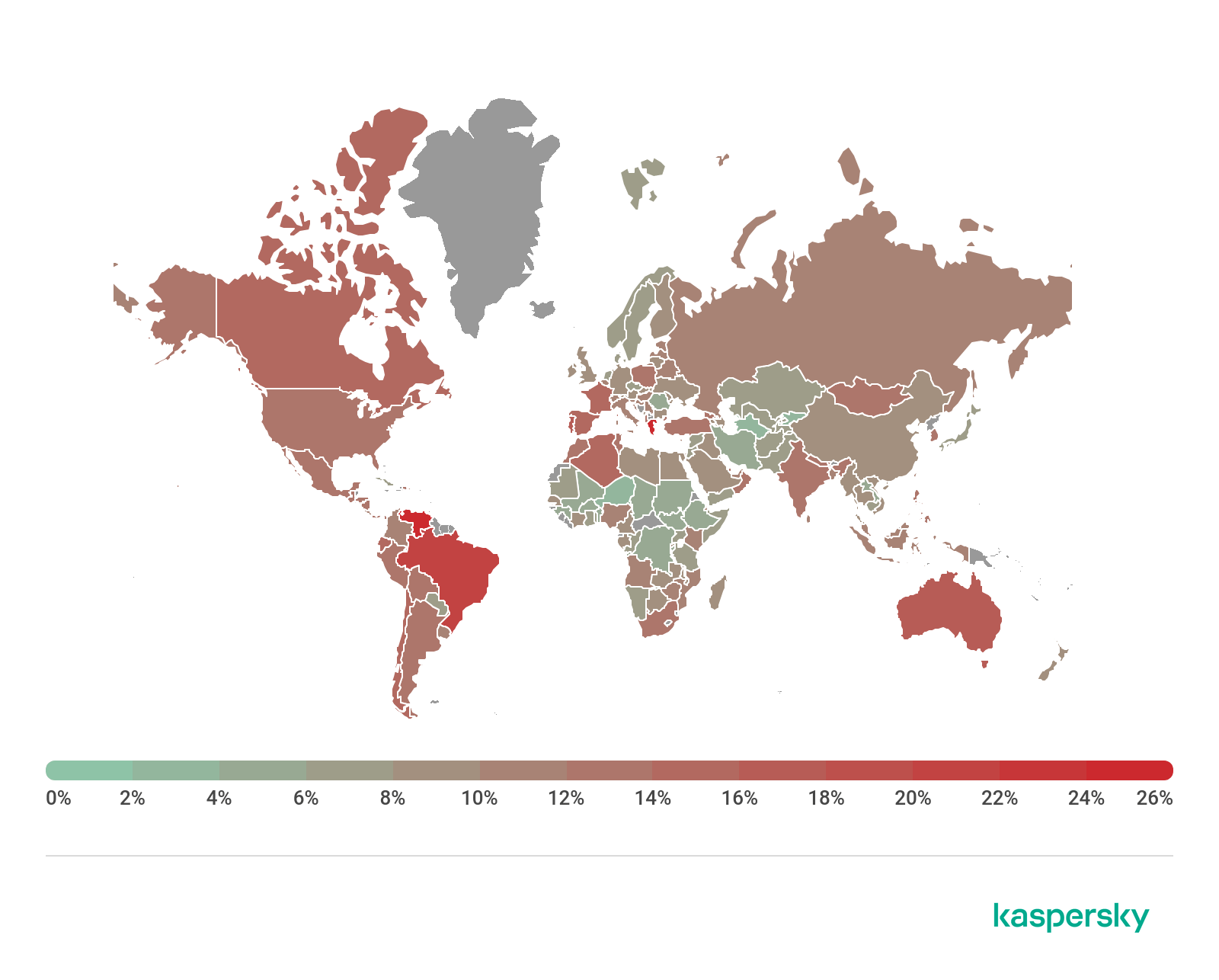
Geography of phishing attacks, Q2 2019
Greece is followed by Venezuela (25.67%), which rose to second from fifth, adding 8.95 p.p. Brazil came in third (20.86%), falling from first place, despite losing less than 1 p.p. Australia (17.73%) failed to medal this time around, while Portugal (17.47%) rounds off the Top 5.
| Country | %* |
| Greece | 26.20% |
| Venezuela | 25.67% |
| Brazil | 20.86% |
| Australia | 17.73% |
| Portugal | 17.47% |
| Spain | 15.85% |
| Algeria | 15.51% |
| Chile | 15.47% |
| France | 14.81% |
* Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky Lab users in the country
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Lab’s Anti-Phishing component. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
This quarter, credit organizations retain first place by number of attacks — the share of attacks on banks amounted to 30.68%, which is almost 5 p.p. more than last quarter.
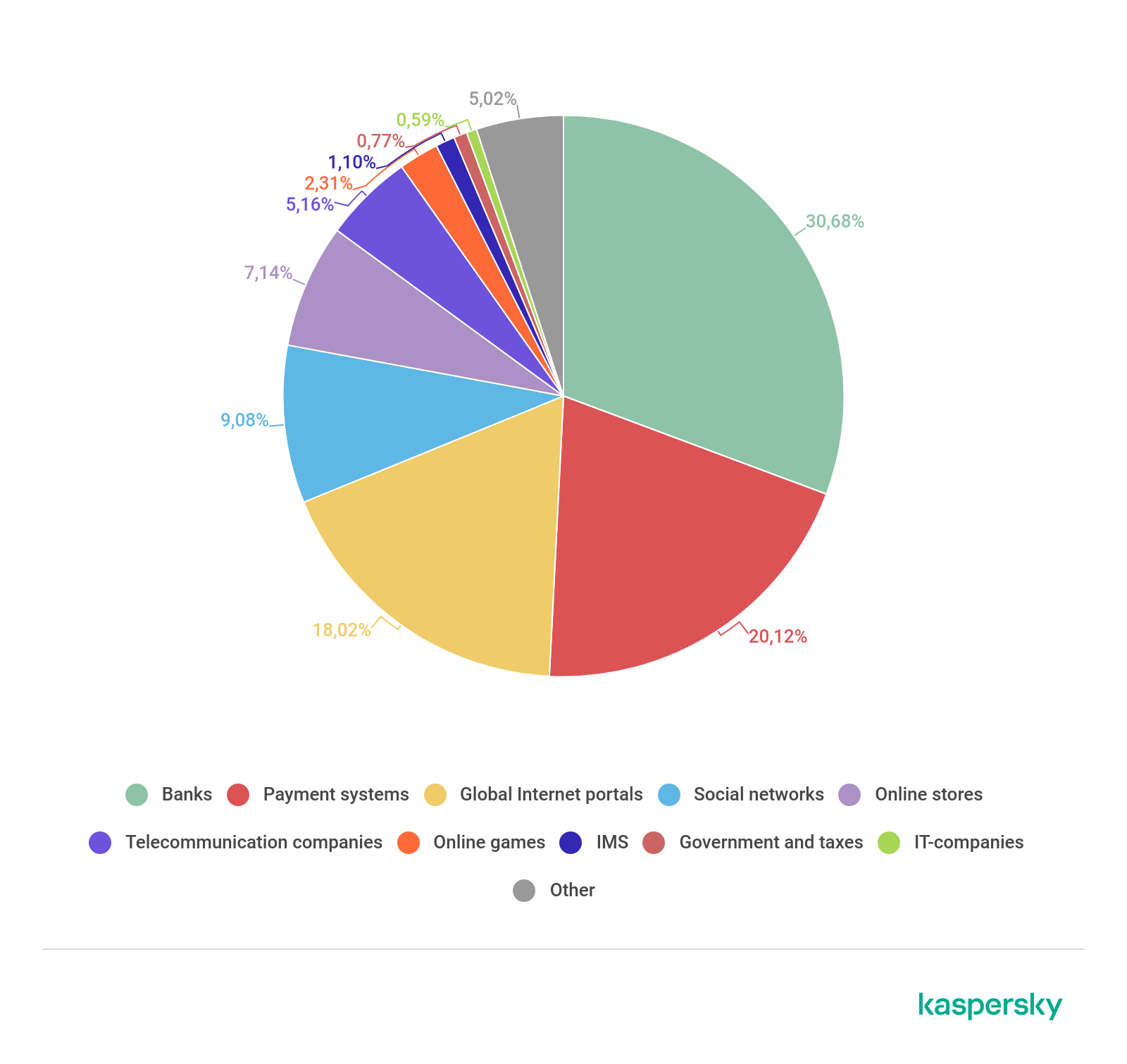
Distribution of organizations subjected to phishing attacks by category, Q2 2019
In second position was payment systems (20.12%), and global Internet portals (18.02%) took third place.
Conclusion
In Q2 2019, the average share of spam in global mail traffic fell by 1.67 p.p. to 57.64%, while the Anti-Phishing system prevented more than 130 million redirects to phishing sites, up 18 million on the previous reporting period.
First place in the list of spam sources went to China with a share of 23,72%. Top spot by number of mail antivirus detections was claimed by Germany on 10.05%. Throughout Q2 2019, our security solutions detected a total of 43,907,840 malicious email attachments. The most prevalent malware in mail traffic was Exploit.MSOffice.CVE-2017-11882.gen with a share of 7.53%, while Backdoor.Win32.Androm, with an 8% share, was the most common malicious family.
Cybercriminals continue to look for new ways to deliver spam and improve old ones. In Q2, they used popular Google services to distribute spam. Blackmailers are also trying out new methods. Alongside threats to ordinary users, attempts were made to blackmail companies by threatening to send spam mailings in their name.
Apart from that, as before, scammers are alive to the zeitgeist and quickly adapt their schemes to high-profile events.





















Spam and phishing in Q2 2019