
Numbers of the year
- The share of spam in mail traffic was 52.48%, which is 4.15 p.p. less than in 2017.
- The biggest source of spam this year was China (11.69%).
- 74.15% of spam emails were less than 2 KB in size.
- Malicious spam was detected most commonly with the Win32.CVE-2017-11882 verdict.
- The Anti-Phishing system was triggered 482,465,211 times.
- 18.32% of unique users encountered phishing.
Global events and spam
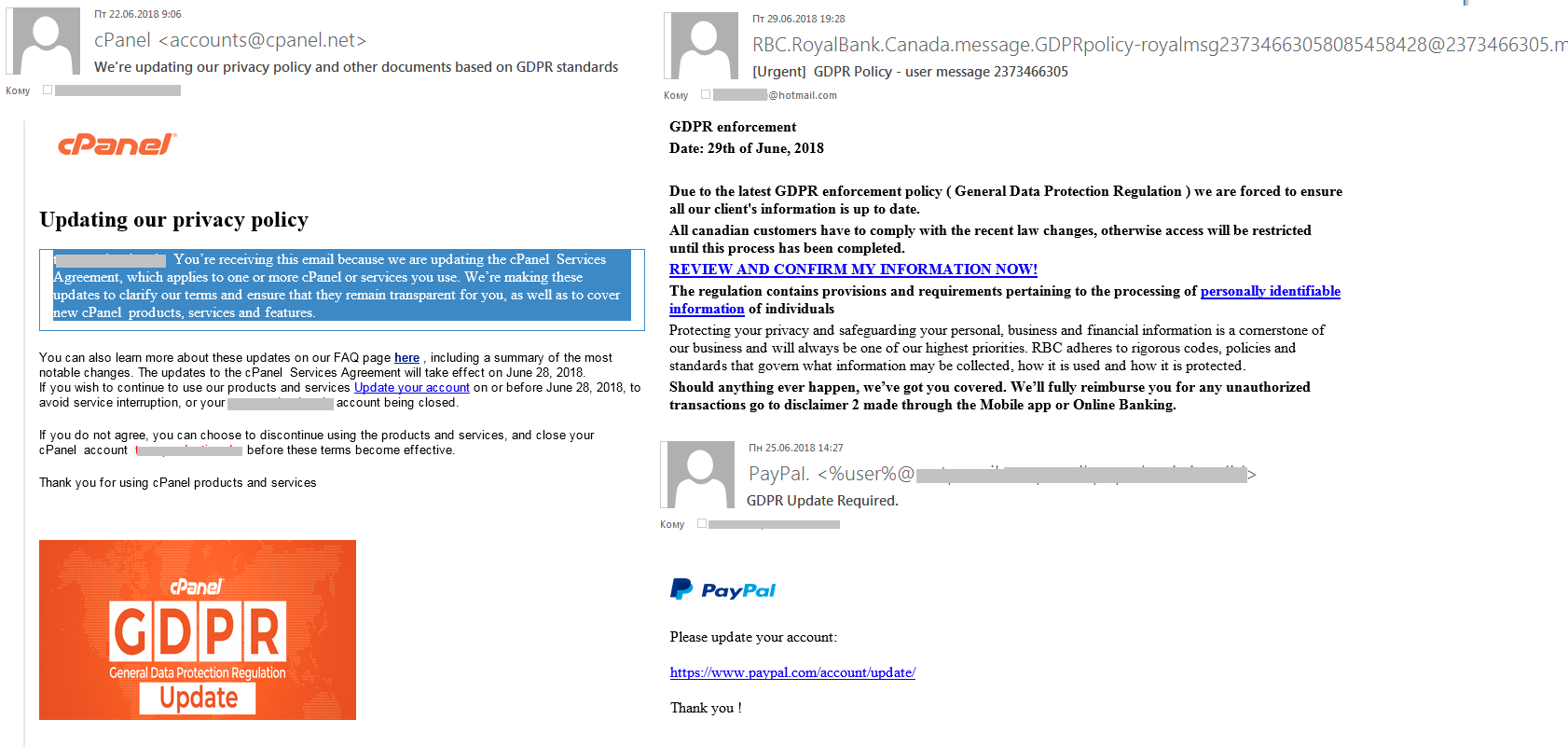
GDPR
In the first months of the year alone, we registered a great many emails in spam traffic connected in some way to the EU General Data Protection Regulation (GDPR). It was generally B2B spam — mostly invitations to paid seminars, webinars, and workshops promising to explain the ins and outs of the new regulation and its ramifications for business.
During this period, there was an upturn in legitimate mailings too. Following the requirements of the regulation, companies sent out notifications on the transition to the GDPR policy requesting user consent to store and process personal data. Unsurprisingly, scammers tried to take advantage. Seeking to gain access to the personal data of clients of well-known companies, they sent out GDPR-related phishing emails prompting to update account information. Users who followed the link in the message and entered the required data immediately had it stolen by the fraudsters. It is worth noting that cybercriminals were interested largely in the data of clients of financial organizations and companies providing IT services.
2018 FIFA World Cup
The FIFA World Cup was one of the main media events of the year, reaching far beyond the world of sport. Scammers exploited the World Cup topic using a variety of classic deception methods based on social engineering. Cybercriminals created fake FIFA partner websites to gain access to victims’ bank accounts, carried out targeted attacks, and set up fake login pages for fifa.com accounts.
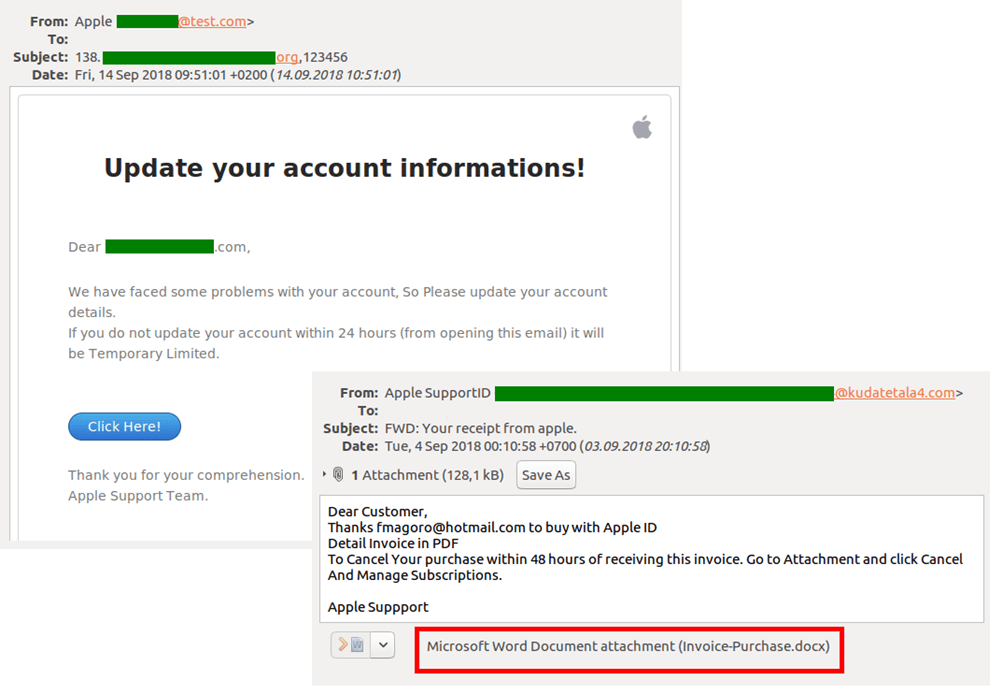
New iPhone launch
As is now customary, Apple’s unveiling of its latest device caused a spike in spam sent, supposedly, from Chinese companies offering accessories and replica gadgets. Such messages redirect the recipient to newly created, generic online stores, which willingly accept payments, but are not so great when it comes to dispatching goods.
The release coincided with a slight rise in the number of phishing messages exploiting the Apple brand (and its services), and emails with malicious attachments:
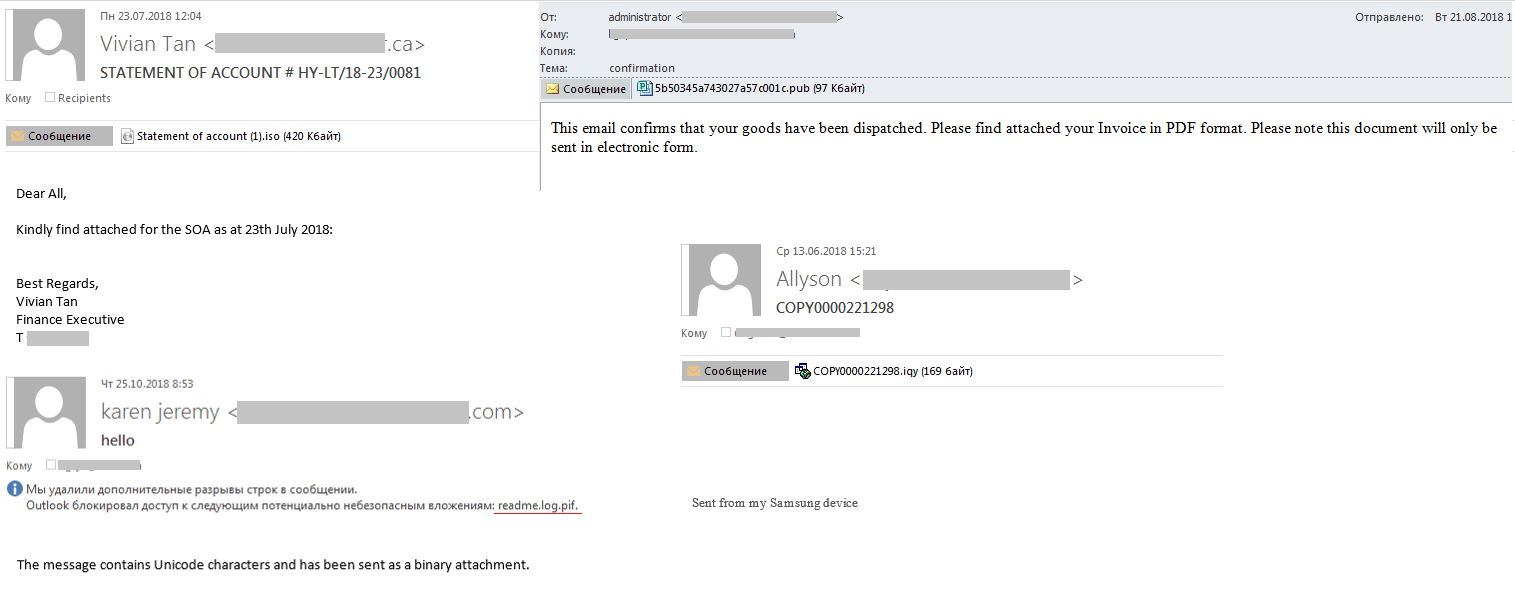
Malware and the corporate sector
In 2018, the number of malicious messages in spam was 1.2 times less than in 2017; Mail Anti-Virus was triggered a total of 120,310,656 times among Kaspersky Lab clients.
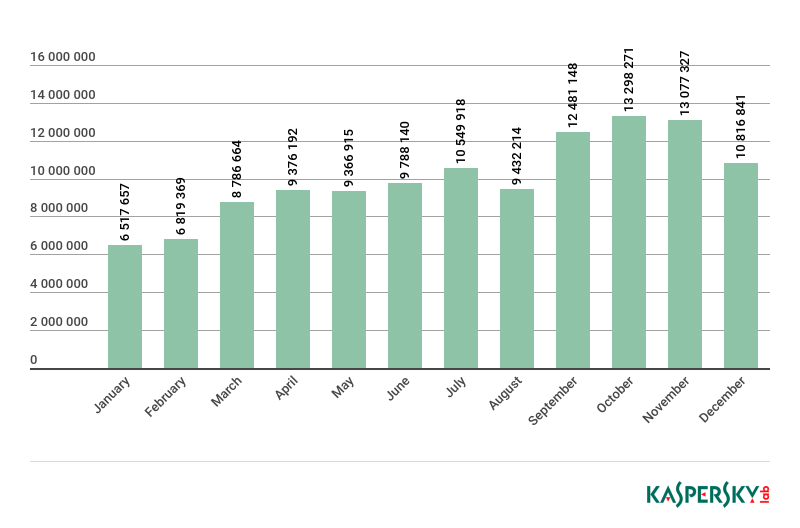
Number of Mail Anti-Virus triggerings among Kaspersky Lab clients in 2018
2018 saw a continuation of the trend for attention to detail in email presentation. Cybercriminals imitated actual business correspondence using the companies’ real details, including signatures and logos. To bypass security solutions (and convince users that files were safe), ISO, IQY, PIF, and PUB attachments were used, all non-typical formats for spam.
Credit organizations remain one of the most popular targets, and this trend is likely to continue in 2019. We also expect an increase in the number of attacks on the corporate sector as a whole.
New distribution channels
We have mentioned before that the distribution of phishing and other fraudulent content has gone beyond the scope of mailings. Scammers are not only testing new means of delivery, but getting victims themselves to distribute malicious content. Some of this year’s most massive attacks we registered in messengers and social networks.
“Self-propagating” phishing messages are similar to long-forgotten chain letters. They refer to non-existent giveaways or free lucrative offers, with one of the conditions for participation being to forward the message to friends or publish it on social media. At the start of the year, scammers used free air ticket lotteries as a bait, before switching to mailings supposedly from popular retail chains, restaurants, stores, and coffee bars. WhatsApp was the most common tool for distributing such messages.
Cryptocurrencies and spam
In 2018, far from waning, spammers’ interest in cryptocurrencies rose. Among the spam messages were fraudulent ones attempting to coerce potential victims into transferring money to cryptocurrency wallets.
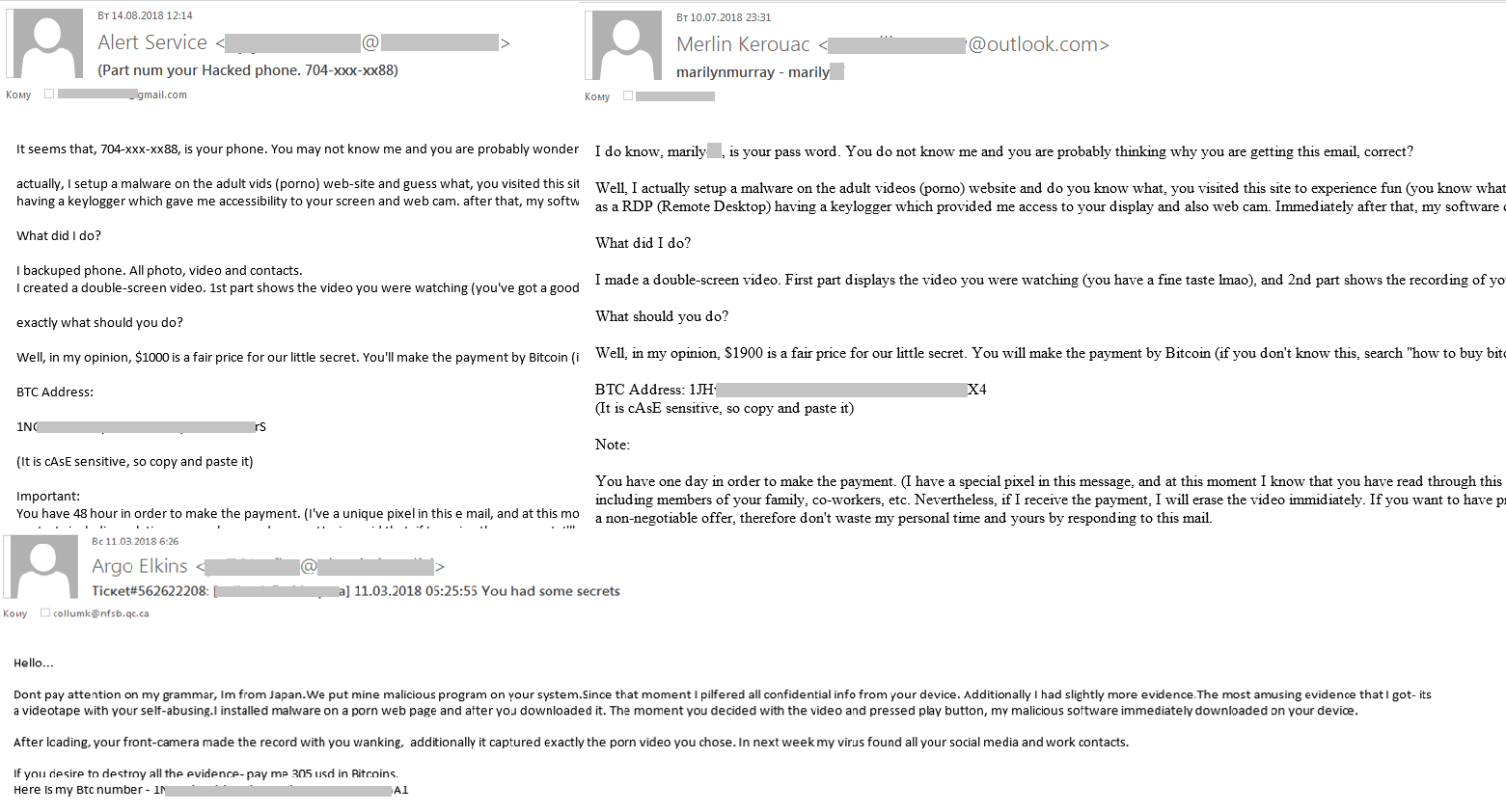
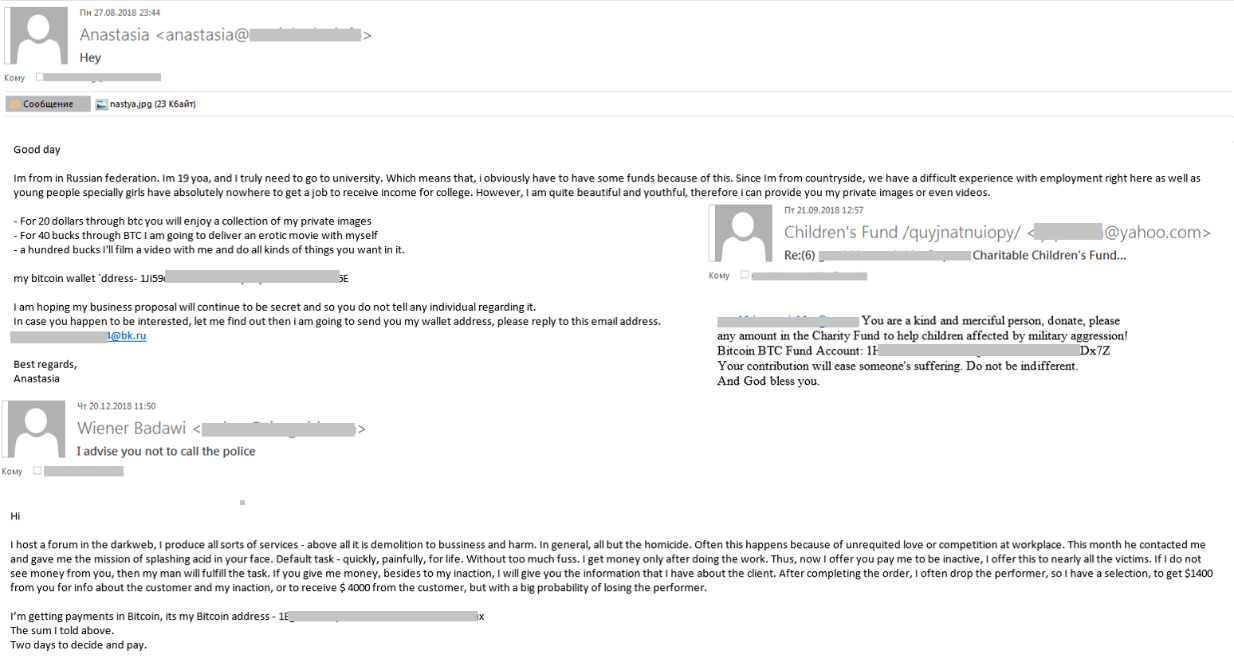
One of the most popular kinds of fraud seen last year was “sextortion.” This type of ransom scam is based on the claim to be in possession of private information of an intimate nature. To avoid disclosure, the victim is told to transfer money to the cryptocurrency wallet specified in the message, which often looks very convincing and uses the victim’s actual personal data: name, passwords, phone numbers, etc. Against the backdrop of endless news reports about personal data leaks, such threats, backed up by real details, cause victims to panic and give in to the cybercriminals’ demands. Last year, the ransom sum ranged from a few hundred to several thousand dollars.
Initially, the mailings were aimed at an English-speaking audience, but at the end of Q3 we registered a wave of messages in other languages: German, Italian, Arabic, Japanese, French, Greek, and others.
Neither did the scammers forget about other fraud methods. Over the year, we identified fraudulent mailings supposedly from large charitable organizations asking to help children by purchasing some data etc. All these schemes had a common thread: The money transfer was requested in cryptocurrency. It should be noted that such messages were very few compared with the mailings described above.
In 2019, spammers will continue to exploit the cryptocurrency topic. We expect to see more fraudulent mailings aimed at both extracting cryptocurrency and gaining access to personal accounts with various cryptocurrency services.
Phishing
Cryptocurrency
Cryptocurrency remains one of the most common phishing topics. In 2018, our Anti-Phishing system prevented 410,786 attempts to redirect users to phishing sites imitating popular cryptocurrency wallets, exchanges, and platforms. Fraudsters are actively creating fake login pages for cryptocurrency services in the hope of getting user credentials.
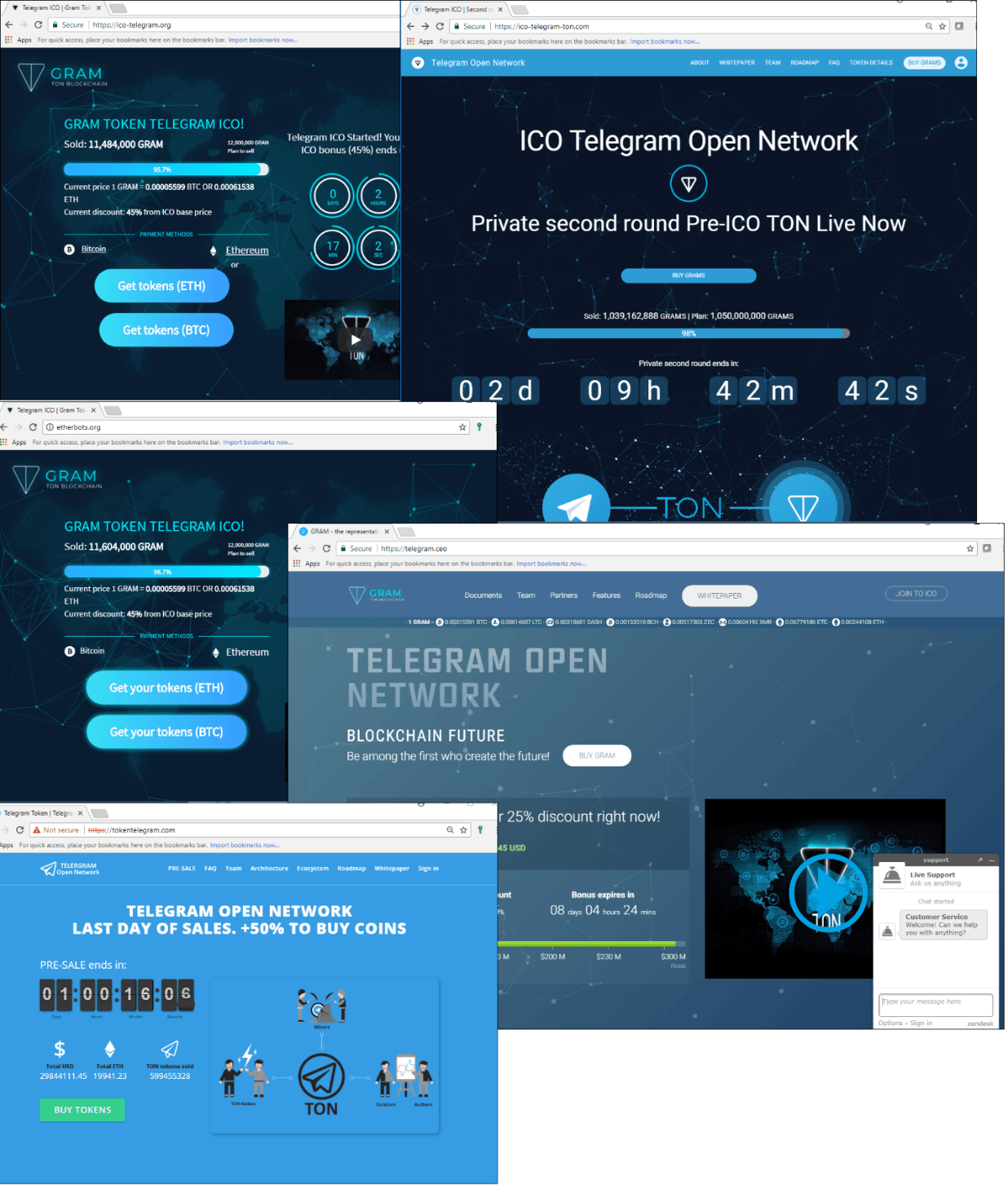
Another hot topic last year was fake ICOs. Scammers invited victims to invest in various initial coin offerings not only by email, but through social media posts as well. There was something for everyone: One of the scams, for example, targeted buzcoin, a cryptocurrency named after Russian singer Olga Buzova. The cybercrooks managed to get hold of the project mailing list and send fake presale invitations to subscribers the day before the start of the ICO. Before the bona fide organizers had time to sneeze, the attackers had scooped around $15,000.
But it was the blockchain project of Pavel Durov, TON, which had the dubious honor of most fakes back in early 2018. The cryptocurrency boom and rumors in late 2017 about an ICO from the creator of Telegram provided fertile ground. Many people believed the scammers and, despite warnings from Pavel himself on social media, transferred money to them.
Lotteries and surveys
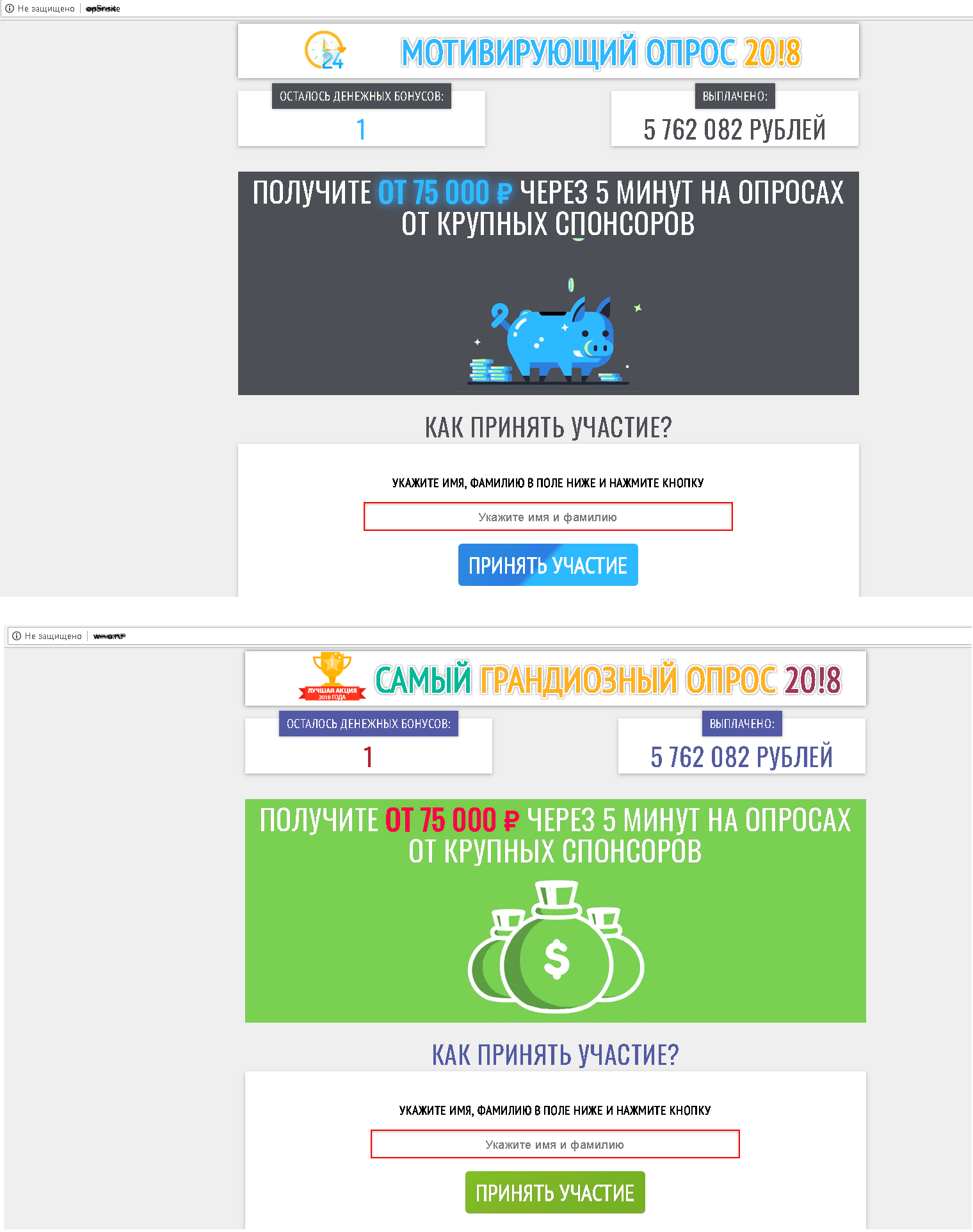
Another way to nudge victims into transferring money is via the promise of a guaranteed lottery win or a reward for taking part in a poll. In 2018, our security solutions blocked 3,200,180 attempted redirects to fraudulent websites offering lotteries or surveys.
To take part in the draw, users are asked to make a contribution: the more you give, the more you (supposedly) get. Survey scams work in a similar way. The victim is asked to transfer a sum of money to pay for “administrative costs,” after which the reward will be transferred, or so it is promised.
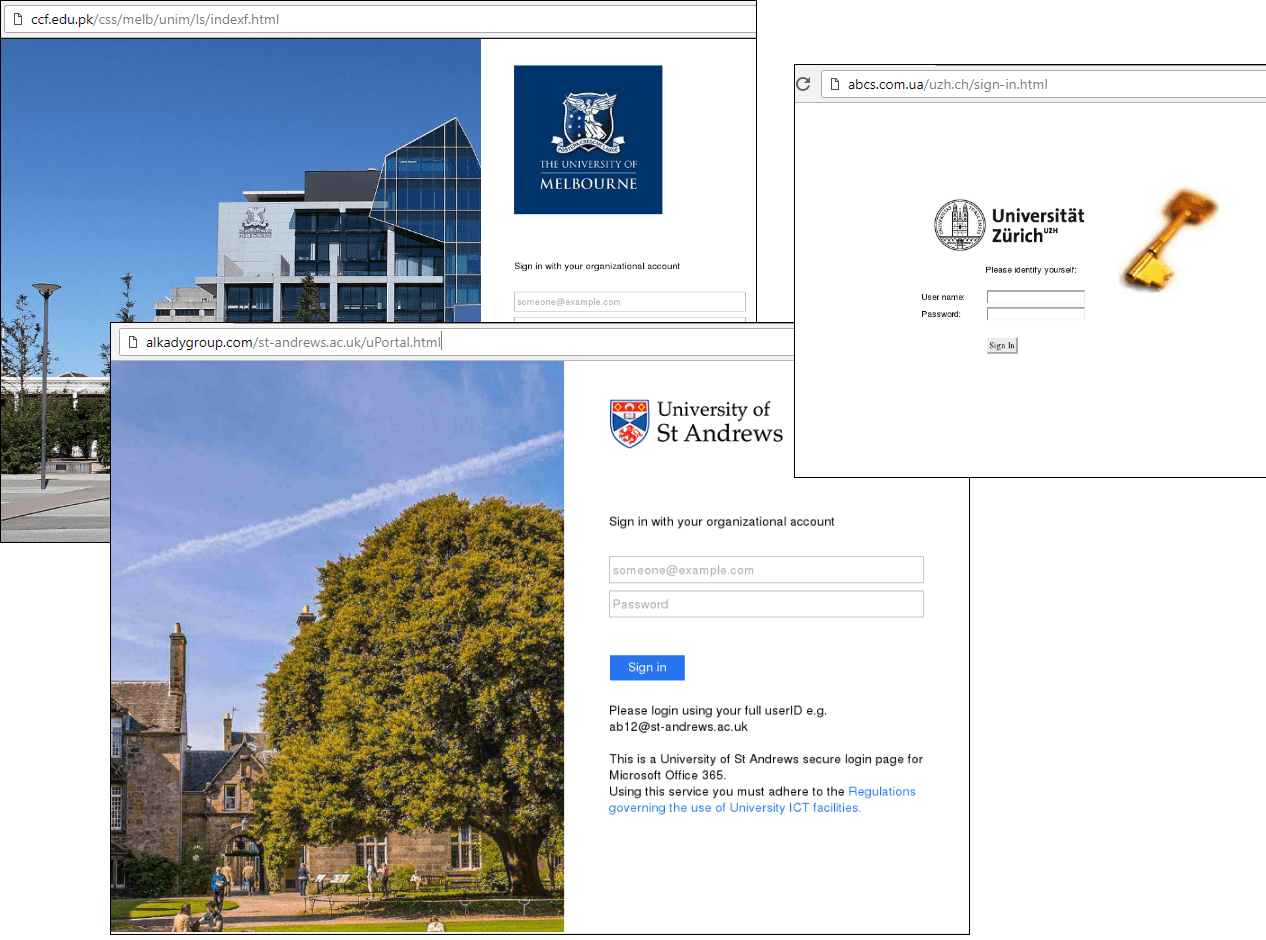
Universities
Phishers hunt not only for money, but also for knowledge: Over the past year, we registered phishing attacks against 131 universities in 16 countries. More than half (83) were in the US, followed by Britain (21), and Australia and Canada (7 each). One high-profile incident was the theft of millions of documents (including nuclear energy research) from several British universities.
Taxes
In Q1 (the last quarter of the financial year in many countries), we observed a large number of phishing pages imitating the websites of HMRC (UK), the IRS (US), and other countries’ tax authorities. Cybercriminals tried to finagle personal data, answers to security questions, bank account information, and other data from users. Some fake tax service sites distributed malware.
HTTPS
As we wrote a year earlier, the number of phishing pages on domains with SSL certificates has increased. Ironically, this was facilitated by the widespread adoption of HTTPS, since pages with a certificate (and padlock) are trusted far more. But getting hold of a certificate is not hard, especially for competent cybercriminals. The problem has taken on such dimensions that since September 2018 with the latest version of Chrome, the browser has stopped highlighting HTTPS sites with a green padlock in the address bar and marking them as “Secure.” Instead, the “Not secure” label is now assigned to sites without HTTPS.
Sales
Every year, November sees the start of the sales season. First up is World Shopping Day, followed by Black Friday. Cybercriminals prepare for such events in advance and commence their mass attacks long before the sales start. According to our statistics, the number of attempts to redirect users to fraudulent websites exploiting the sales topic starts to rise at the end of October.
Fraudsters use standard methods to extract personal data and money from victims, including fake websites mimicking popular online stores with huge discounts on expensive goods.
Statistics: spam
Proportion of spam in email traffic
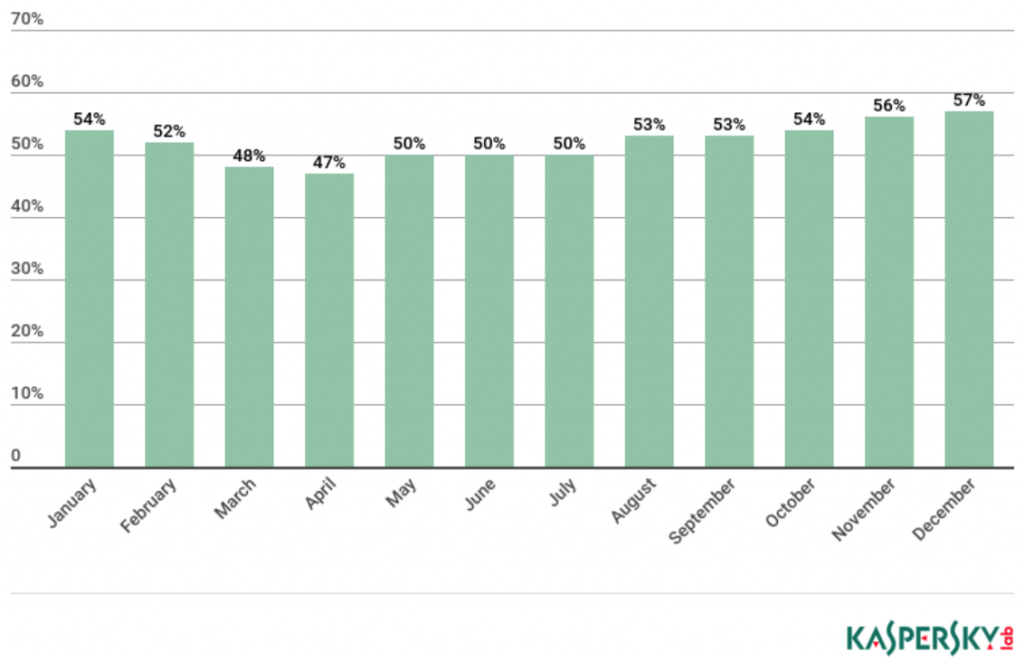
The share of spam in email traffic in 2018 decreased by 4.15 p.p. to 52.48%.
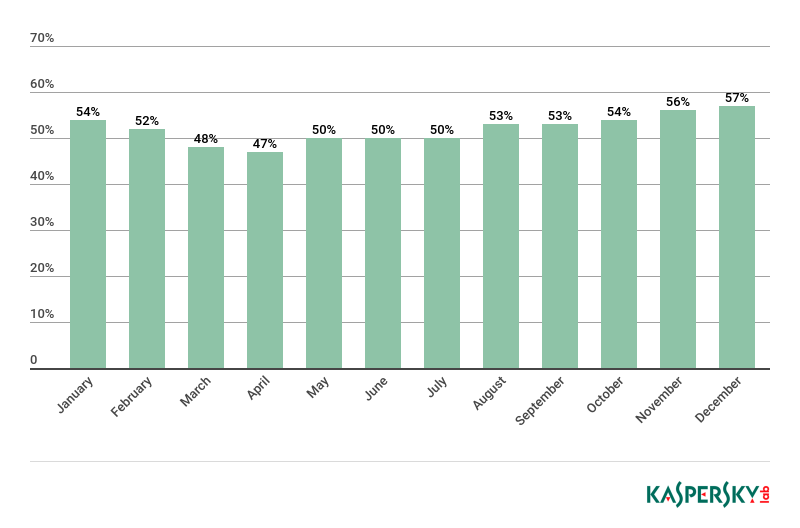
Proportion of spam in global email traffic, 2018
The lowest share (47.70%) was recorded in April 2018. The highest (57.26%) belonged to December.
Sources of spam by country
In 2018, China (11.69%) led the list of spamming countries, swapping places with the US and consigning the former leader to second place with 9.04%. Third position went to Germany (7.17%), which climbed into the Top 3 from sixth.
Vietnam, which ranked third last year, fell to fourth place (6.09%). It was followed by Brazil (4.87%), India (4.77%), and Russia (4.29%).
In 8th place, as in 2017, came France (3.34%), while Iran and Italy departed the Top 10. They were replaced by newcomers Spain, which rose from 16th to 9th place (2.20%, +0.72 p.p.), and Britain (2.18%, +0.59 p.p.).
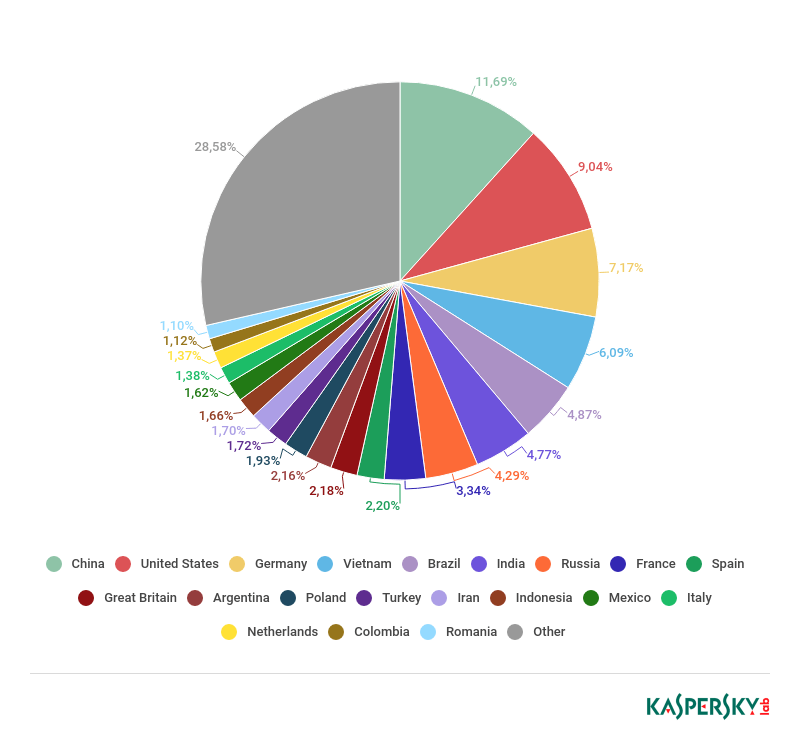
Sources of spam by country, 2018
Spam email size
In 2018, the share of very small (up to 2 KB) messages increased significantly. Despite quarterly decline, the annual figure came in at 74.15%, up 30.75 p.p. against the previous reporting period. The proportion of 2–5 KB messages also increased (10.64%, +5.56 p.p.).
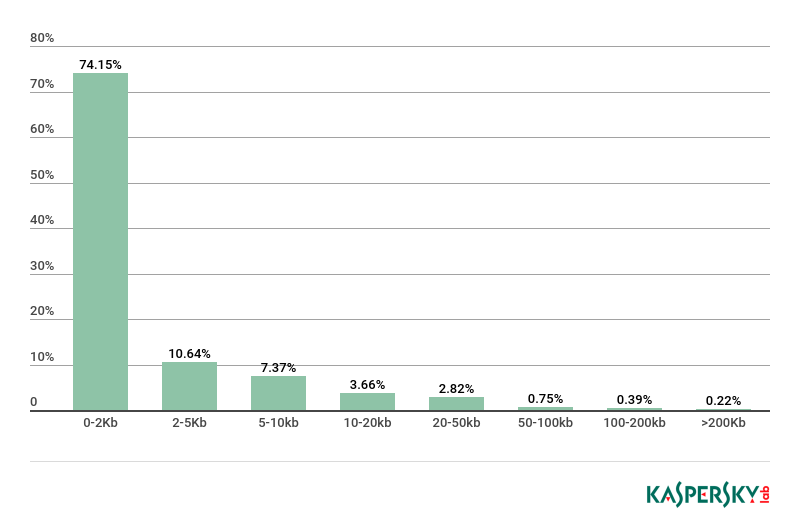
Spam emails by size, 2018
The volume of larger spam dropped significantly against 2017. The share of messages sized 5–10 KB (7.37%) decreased by 1.77 p.p. and 10–20 KB (3.66%) by 12.6 p.p. The share of spam messages sized 20–50 KB (2.82%) saw the biggest drop, down 18.41 p.p.
Malicious attachments in email
Malware families
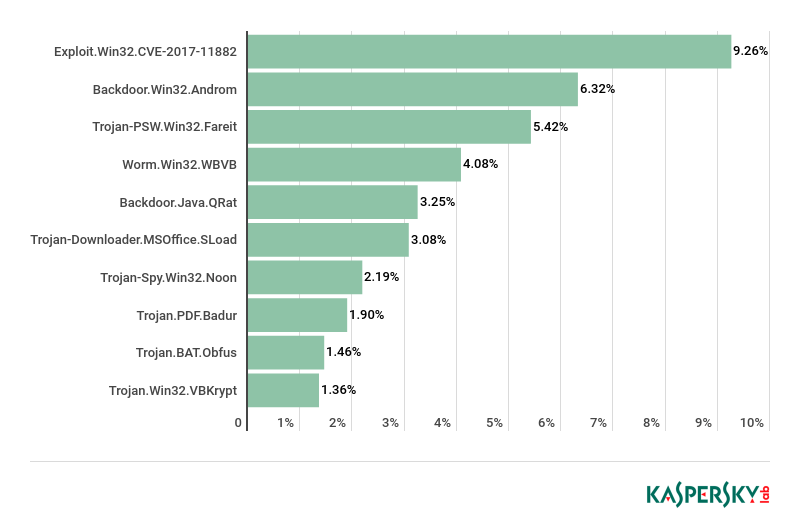
Top 10 malware families in 2018
In 2018, the most widely distributed malicious objects in email, assigned the Exploit.Win32.CVE-2017-11882 verdict, exploited a Microsoft Office vulnerability for executing arbitrary code without the user’s knowledge.
In second place was the Backdoor.Win32.Androm bot, whose functionality depends on additional modules downloaded at the command of the C&C servers. It was most often used to download malware.
The Trojan-PSW.Win32.Fareit family moved up from fifth to third place. Its main task is to steal data (cookies, passwords for various FTP, mail, and other services). The harvested information is sent to the cybercriminals’ server. Some members of the family are able to download and run other malware.
The Worm.Win32.WBVB family, which includes executable files written in Visual Basic 6 (in both P-code and Native mode) and are not trusted in KSN, remained in fourth place.
Fifth place went to the Backdoor.Java.Qrat family — cross-platform multi-functional backdoor written in Java and sold in the Darknet as a Malware-as-a-Service (MaaS) package. It is generally distributed by email in JAR attachments.
Trojan-Downloader.MSOffice.SLoad, a DOC/DOCX document containing a script that can be executed in MS Word, took sixth place. It is generally used to download and install ransomware on user computers.
The spyware Trojan-Spy.Win32.Noon ranked seventh.
The malware Trojan.PDF.Badur, which consists of a PDF document containing a link to a potentially dangerous website, dropped one place to eighth.
Ninth place was taken by the Trojan.BAT.Obfus family of malicious objects — obfuscated BAT files for running malware and changing OS security settings.
In tenth place, as in the previous year, was the family of Trojan downloaders Trojan.Win32.VBKrypt.
Countries targeted by malicious mailshots
As in previous years, first place in 2018 went to Germany. Its share accounted for 11.51% of all attacks. Second place was taken by Russia (7.21%), and Britain (5.76%) picked up bronze.
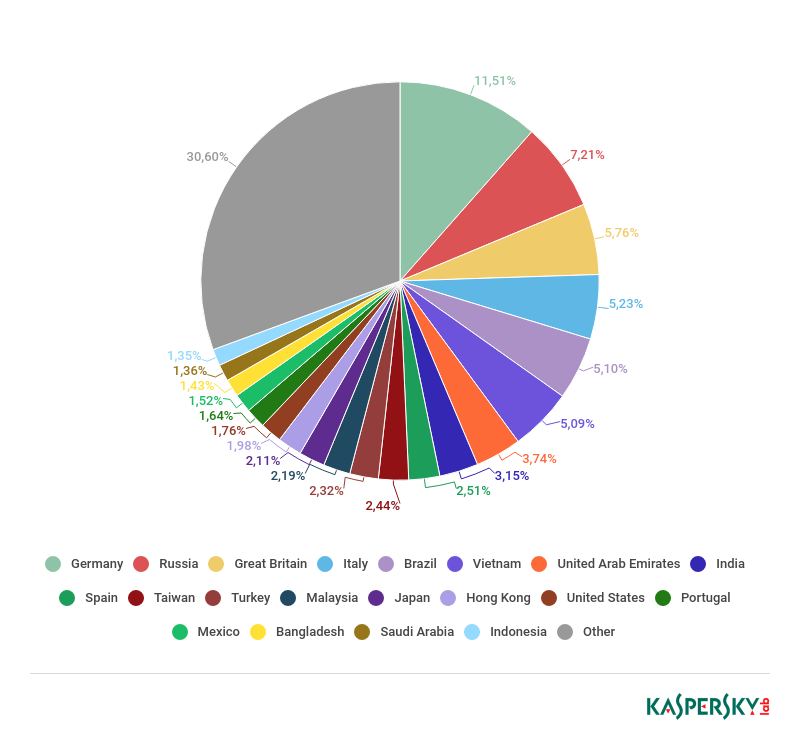
Countries targeted by malicious mailshots, 2018
The next three, separated by a whisker, were Italy (5.23%), Brazil (5.10%), and Vietnam (5.09%). Trailing Vietnam by 1.35 p.p. in seventh was the UAE (3.74%). India (3.15%), Spain (2.51%), and Taiwan (2.44%) rounded off the Top 10.
Statistics: phishing
In 2018, the Anti-Phishing system was triggered 482,465,211 times on Kaspersky Lab user computers as a result of phishing redirection attempts (236,233,566 more than in 2017). In total, 18.32% of our users were attacked.
Organizations under attack
The rating of organizations targeted by phishing attacks is based on the triggering of the heuristic component in the Anti-Phishing system on user computers. This component detects all instances when the user tries to follow a link in an email or on the Internet to a phishing page in the event that such links have yet to be added to Kaspersky Lab’s databases.
Rating of categories of organizations attacked by phishers
In 2018, the global Internet portals accounted for the lion’s share of heuristic component triggers. Its slice increased by 11.23 p.p. to 24.72% against the previous year. In second place came the banking sector (21.70%), down 5.3 p.p. Payment systems (14.02%) in 2018 ranked third.
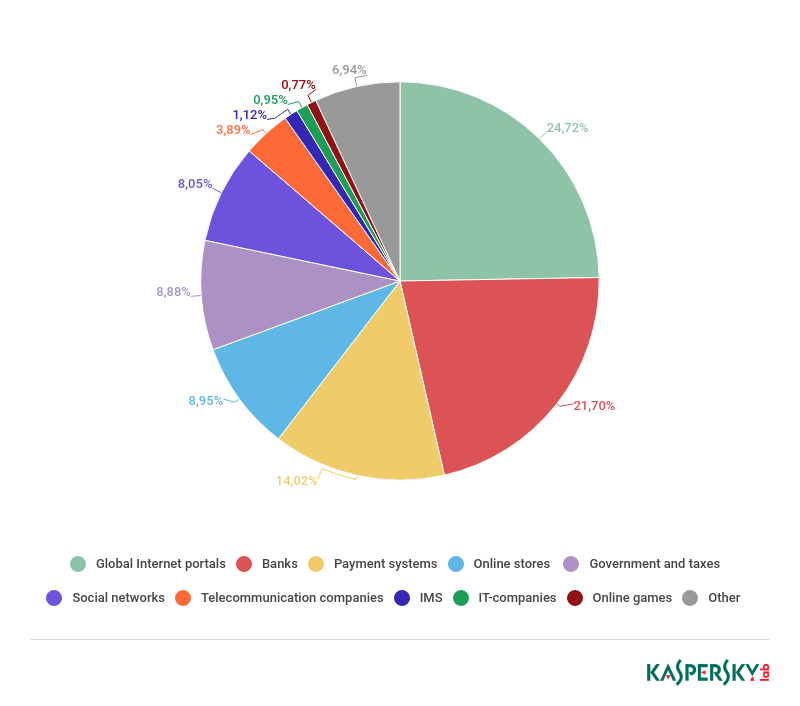
Distribution of organizations subject to phishing attacks by category, 2018.
Top 3 organizations under attack from phishers
This rating is made of organizations whose names were most frequently used by phishers (according to the heuristic statistics for triggers on user computers). It was the same lineup as in 2017, but rearranged slightly, with Microsoft in first place.
| Microsoft | 6.86% |
| 6.37% | |
| PayPal | 3.23% |
Attack geography
Countries by share of attacked users
Brazil (28.28%) remains out in front by percentage of attacked unique users out of the total number of users in the country.
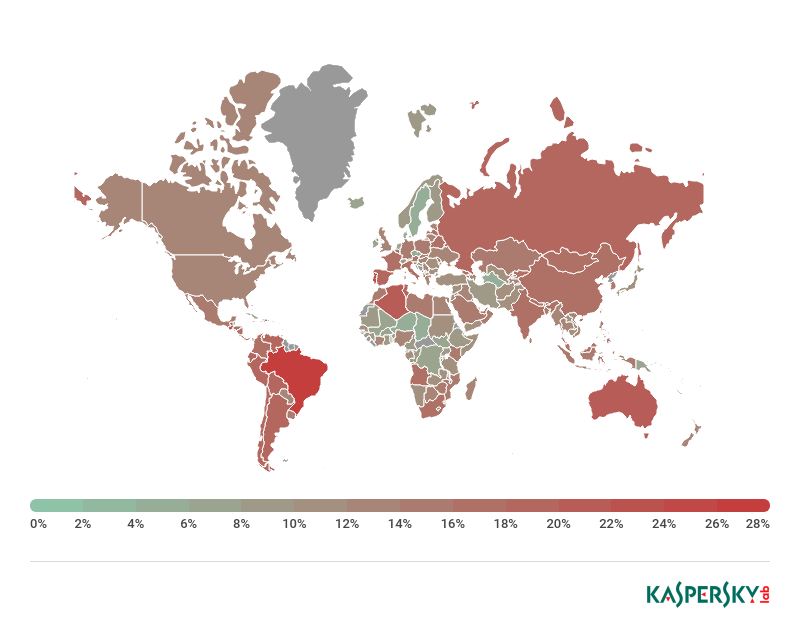
Percentage of users on whose computers the Anti-Phishing system was triggered out of all Kaspersky Lab users in the country, 2018
Top 10 countries by share of attacked users
| Country | % |
| Brazil | 28.28 |
| Portugal | 22.63 |
| Australia | 20.72 |
| Algeria | 20.46 |
| Réunion | 20.39 |
| Guatemala | 20.34 |
| Chile | 20.09 |
| Spain | 20.05 |
| Venezuela | 19.89 |
| Russia | 19.76 |
Top 10 countries by share of attacked users
Despite a slight drop of 0.74 p.p., Brazil (28.28%) remains top by number of attacked users. Meanwhile, Portugal (22.63%) moved up to second place (+5.87 p.p.), displacing Australia (20.72%, –1.79 p.p.).
Conclusion
2018 showed that cybercriminals continue to keep a close eye on global events and use them to achieve their goals. We have seen a steady increase in phishing attacks on cryptocurrency-related resources, and expect new scams to appear in 2019. Despite the fall in value and the lean times for the cryptocurrency market as a whole, phishers and spammers will try to squeeze everything they can out of this topic.
The past year also demonstrated that spammers and scammers will continue to exploit annually occurring events — new smartphone launches, sales seasons, tax deadlines/rebates, and the like.
There is also a trend toward the transition to new channels of content distribution: Cybercriminals in 2018 used new methods of communication with their “audience,” including instant messengers and social networks, releasing wave after wave of self-propagating malicious messages. Hand in hand with this, as illustrated by the attack on universities, fraudsters are seeking not only new channels, but new targets as well.























Spam and phishing in 2018