
Which web resources most often attract cybercriminals? It’s always those where they can reach the greatest number of users and deliver the maximum possible profits. Today, practically all internet users have an account with a social network (and often several with different networks), which makes these sites very popular with cybercriminals. Facebook is the most attractive social network: according to Kaspersky Lab’s statistics, fake sites imitating Facebook accounted for nearly 22% of all instances when the heuristic Anti-phishing component was triggered.
A useful account
On the face of it, hijacking social network accounts shouldn’t be that attractive for cybercriminals, as it doesn’t bring an immediate profit – we don’t keep our savings with Facebook, while the personal information placed on these networks is only interesting to our friends and loved ones. But that first impression may be misleading. In reality, there may be several reasons for cybercriminals to want illegitimate access to the accounts in Facebook or any other social network:
- To spread phishing links. For phishing purposes, it is more effective to use real hijacked accounts rather than to create ad-hoc bot accounts. It is much more likely that a person will click on a fake bank site if the link comes from his/her social network friend rather than from an unknown person.
- To spread malware. Just like with phishing links, social network users more readily download and open files coming from their Facebook friends.
- To send spam to the victim’s contact list and publish spam on the friends’ walls where it can be seen by other users.
- To practice fraud, such as extorting money from the hijacked account’s friends. The fraudster can send messages asking people to send money for help.
- To collect information on specific people. Such information can be later used to launch targeted attacks, such as targeted phishing.
- To sell hijacked accounts. Cybercriminals sell hijacked accounts to other cybercriminals who in turn use them to spread spam, phishing links or malware.
Hijackers most often use the last option on this list, making money by selling stolen data.
Statistics
According to data from Kaspersky Security Network in 2013, phishing sites imitating social network websites were to blame for more than 35% of cases when the Anti-phishing heuristic component was triggered. In total, we recorded over 600 million attempts by our users to access phishing sites. Sites imitating Facebook accounted for 22% of all phishing incidents.
The heuristic component of the Anti-phishing system is triggered when the user follows a link leading to a phishing page that has not previously been recorded in the Kaspersky Lab databases. It doesn’t matter how that link is followed: by clicking on a link provided in a phishing message, in a social network message or, say, as a result of some malware activity. When the heuristic component is triggered, the user sees a warning message about a possible threat.
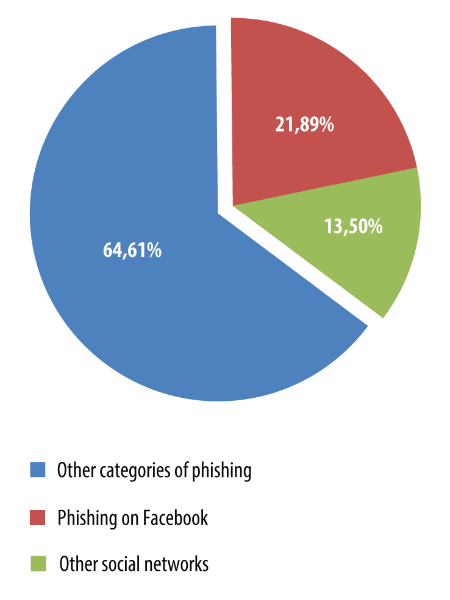
In 2013, fake Facebook pages accounted for 21.89% of all instances when the Anti-phishing heuristic component was triggered
In early 2014, the situation has changed somewhat: Yahoo took the lead for heuristic anti-phishing incidents. However, Facebook is still a top target for phishers: in Q1 2014, fake Facebook pages accounted for 10.85% of all instances when the Anti-phishing heuristic component was triggered.
Each day Kaspersky Lab’s products register more than 20,000 incidents when users attempt to follow links leading to fake Facebook pages.
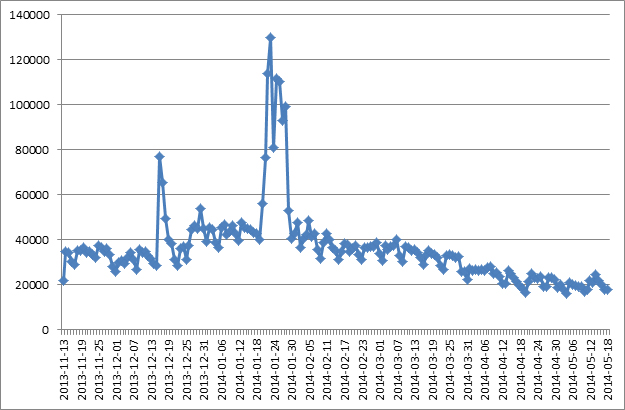
The daily number of instances when the heuristic component of the Anti-phishing system is triggered by fake Facebook page
Most incidents take place in the US (1,500 to 7,500 a day), Canada (1,000 to 2,500) and Germany (2,000 to 4,500). In Russia this number does not exceed 1,000 a day.
In 2013, 22% of users in India attempted to follow a link to a fake Facebook site, 14.56% in France, 10.93% in the US, and 1.5% in Russia.
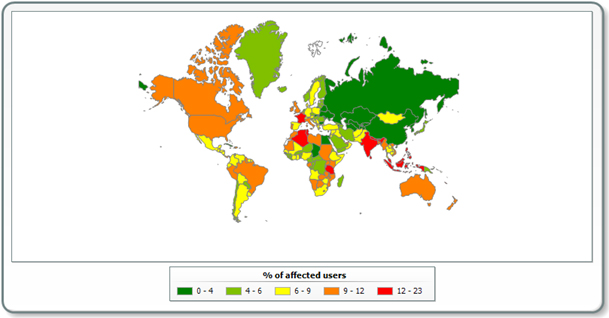
Percentage of users of who attempted to access a fake Facebook page in 2013 (from the entire number of Kaspersky Lab product users in the country)
Bait
How do users land on fake webpages? Cybercriminals have created a number of ways to entice their victims to pages with phishing content. They typically use one of the following to send links to phishing webpages:
- Letters imitating notification messages from a social network. These messages are sent from dedicated email accounts.
- Letters sent from compromised email accounts to associated address lists. This can be a message sent to friends, inviting them to follow a link to look at something interesting.
- Messages in social networks sent from ad-hoc fake accounts or from hijacked accounts.
- In forum messages.
- In search engine results.
- In banners with attractive pictures or in banners masquerading as a social network notification and placed on third-party resources by cybercriminals.
Users can also land on phishing pages if the computer or router was infected with malware that could, for instance, modify or replace the ‘hosts’ file, spoof the DNS or replace the content. This kind of malware is especially dangerous as they redirect users to phishing pages when they follow legitimate links to organizations whose sites are undergoing phishing attacks.
This is why users need to pay attention to the availability or non-availability of a secure connection whenever they open a webpage. Facebook uses the HTTPS protocol to transmit data. The absence of a secure connection even when the URL address is correct probably means that you are visiting a fraudulent site.
However, the correct URL address and the availability of a secure connection cannot always guarantee that you have not stumbled onto a fraudulent page. If in doubt, check that the certificate belongs to Facebook. Also, always pay attention to any notifications from the security software installed on your computer.
Email messages
Sending email messages is a popular method for cybercriminals to send links to phishing pages. These messages are often impersonal, i.e. contain no direct addresses to a specific person, and typically imitate a Facebook message notifying that a personal message has arrived, or that the user’s friends have registered in this social network. If users click on the link, they land on a phishing site prompting them to enter their credentials. Those credentials are immediately sent to the cybercriminals, and users are redirected to the real Facebook login page.
Cybercriminals often resort to intimidation, sending fake messages that threaten to block users’ accounts. To avoid that, users are instructed to follow a link provided in the message and enter their login credentials on the webpage. This approach relies on shocking the victim into carelessness.
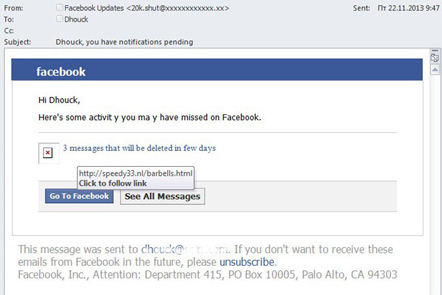
Below is an example of a fake Facebook message notifying a user of recent activities that s/he may have missed. If you position the cursor on the link, the popup window shows that it leads to an unknown address which is different from the official Facebook address. Interestingly, the cybercriminals use part of the recipient’s email address to address the user.
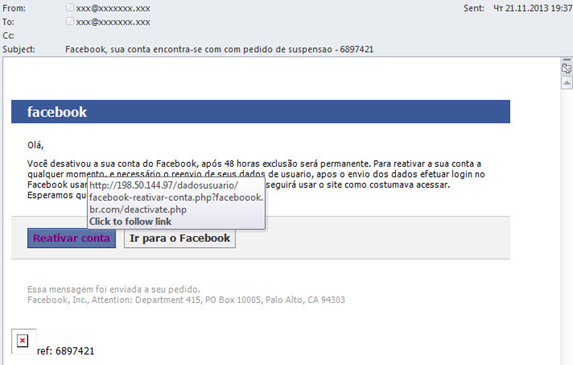
Here is another example of a fake message – this time in Portuguese. The recipient is warned that the account may be blocked soon. To avoid this, the user is advised to follow a link that supposedly leads to Facebook, and enter his/her credentials there. However, placing the cursor over the link shows that it leads to an unrelated site and not to Facebook.
Social networks
Often phishing messages are sent within the social network from compromised accounts registered by the friends of the potential victim. They typically imitate short personal messages and contain a question like “Is that you in this photo?” and a link to the “photo”. When users follow the link provided, they land on a fake Facebook login page that contains the standard message “Log in to continue”. If users don’t become suspicious and enter their credentials, their data will immediately be dispatched to cybercriminals.
All over the globe
Facebook’s global popularity means cybercriminals create fake web pages in a variety of languages: English, French, German, Portuguese, Italian, Turkish, Arabic and others.
Several examples of fake Facebook pages are given below. Pay attention to the address bar: cybercriminals often use words resembling “Facebook” in the URL address of the phishing page, trying to disorient inexperienced Internet users. At times, the URL does not have anything in common with the Facebook address even though the page design mimics that of genuine Facebook pages. Also, notice that no secure connection is available at these pages, which is a sure sign that that is a phishing resource.
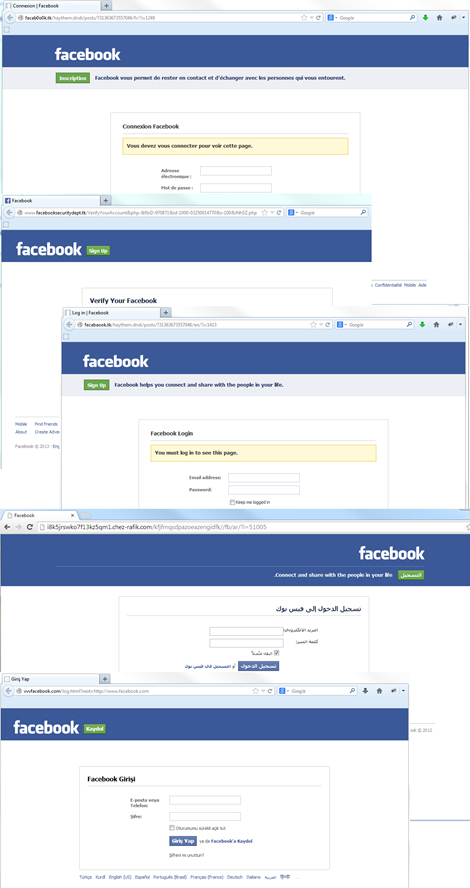
Examples of phishing sites imitating Facebook login pages
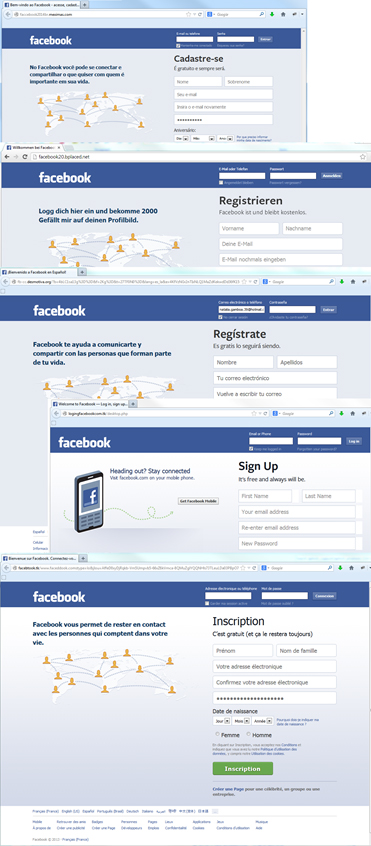
Examples of phishing sites imitating the main Facebook login page, containing a registration form requiring personal data
As can be seen in the examples, the phishing sites are designed to imitate Facebook’s login or registration page. The cybercriminals’ aim is obviously to collect personal data with which to gain access to accounts for further malicious actions.
Mobile phishing
Smartphone or tablet owners who visit social networks from their mobile devices are also in danger of losing their personal data. Cybercriminals create dedicated web pages for mobile browsers that imitate the Facebook app login procedure.
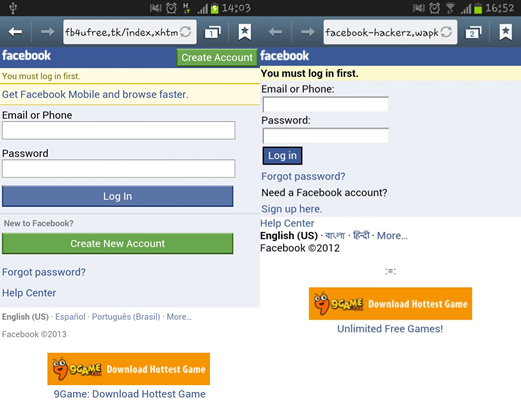
Examples of phishing sites mimicking Facebook for mobile browsers
Some mobile browsers hide the address bar while opening the page, which plays into the cybercriminals’ hands. This makes it much more difficult for the user to detect the falsification.
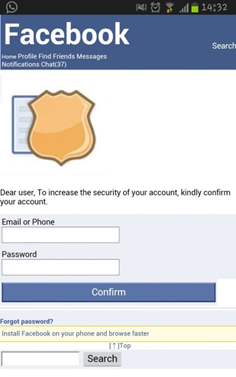
A phishing webpage with a hidden address bar
Malware programs which steal the owner’s personal data may also be active on mobile devices. This stolen information can include social network account credentials. As well as general purpose spyware, there are specialized mobile spyware programs specifically targeting social networks. For instance, a mobile Trojan can spoof the official Facebook application when the user launches it, so a phishing application will open. Also, there is a risk that the user may download a phishing application imitating the official Facebook mobile application.
Conclusion
When cybercriminals spy on social network accounts the main weapon is the carelessness of account holders and their lack of vigilance. Here are our recommendations:
- If you receive an email notification from Facebook or a message that your account may be blocked, or any other messages prompting you to enter your credentials after following a link or in an attached form,
- Compare the sender’s address with the address from which you usually receive notifications. If the address is different from the usual one, there is a good chance this is a phishing scam. However, even if the address looks legitimate, cybercriminals may have masked the sender’s real address.
- Never enter your credentials in attached forms. Facebook never asks users to enter their password in an email or to send a password via email.
- Place the cursor on the link and check if it leads to the official Facebook page. Moreover, you should manually type the Facebook URL in the address bar – cybercriminals are capable of concealing the addresses to which they are leading you.
- If you are redirected to a webpage (after clicking on a banner or following a link provided in an email or message, etc.), make sure the URL in the address bar is what you expect it to be.
- If you have manually entered the URL in the address bar, check it again after the page has loaded to make sure it has not been spoofed.
- Always check if a secure connection is available. If there is none, there is a good chance that you are visiting a fraudulent site, even if the URL address is correct.
- If suspicious emails and/or notifications start coming from your friend(s), try to contact them: their email or social network account may have been compromised or hijacked. If so, your friend(s) will need to change the password immediately.
Social network frauds






















linda kissane
after reading the article i was apprehensive about giving my information. I do analyze each message or advertising sent to my address but even then a small bump can be missed. Unfortunately they go to so many off the grid sites and then send them to everyone they know resulting in my gmail link to their mistake. I do try to nicely tell them to be careful about links and some they are offended. I try to smooth it over but it is a bummer. Having a website adds to the danger. My question is about the ” http ” and the secure ( I hope ) ” https “. The war on hackers and much worse and the endless new data that is being added everyday can be overwhelming so the bottom line is I am as careful as I can be. Right now I am trying to enter my new tablet to my Kaspersky paid protection. I also had a warning from Kaspersky about information that is needed from my account and it keeps on saying attempt has failed to download to fix my problem. Should I continue to try and login. I have tried 5 times and I know that is not good. Please advise me on what to do.
linda kissane
My comment was too long ( keywords ) so I need help with getting my Kaspersky Tablet account transferred to my new Tablet and after 5 tries I am open to attack so please advise.