
Users of Orkut – the large social network in Brazil are again a target of attacks – this time the problem was malicious Apps, small applications that can be added in the user’s profile and executed directly in the browser. Some apps were able to do a redirection when loaded in the user’s profile, leading to phishing pages. Simply visiting an affected profile was enough to be redirected; no other user interaction was needed. During these attacks we collected and blocked more than 50 phishing domains used in this malicious scheme – it’s believed that approximately 150,000 profiles had their IDs stolen.
Currently more than 16,000 apps are available to be installed in a Orkut profile – and some bad guys were able to publish malicious apps in the Apps Directory, even while Google reports that all of them are checked before publishing. One of the main malicious apps used in these attacks was “ChateTVOnline”, an app that promises the ability to watch TV channels:
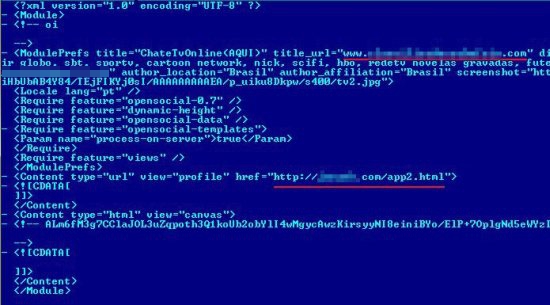
In the source code of the app it is possible to see the main cause of the problem: when installed in a profile it’s possible to run external code, not hosted on Orkut servers. It allows the developer to make redirections to phishing domains:
After being installed in the user’s profile the malicious app will run every time someone enters the profile and the redirection will occur. All the accounts stolen were used to spread the attack, adding automatic scraps, which are short messages, in some communities asking other users to install the malicious app or to visit the affected profile.
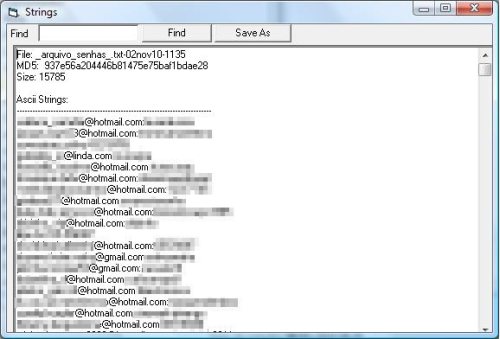
Around 50 phishing domains were used in this malicious scheme. In just one of them, goooble.com.br, a typosquatting of google.com.br we found more than 440 users ID stolen:
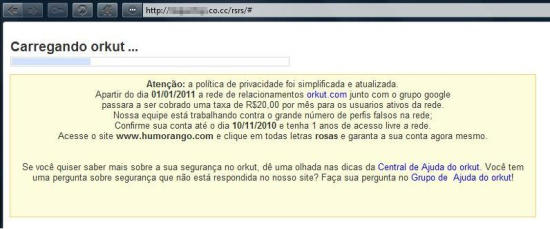
In a variant of the first attack we found other malicious scheme asking for money: it redirected the affected user to a page asking him to pay a ransom of R$ 20,00 (around 12 dollars) to deliver his profile:
We reported these malicious apps to Google and they removed them. All domains used in these attacks are blocked by Kaspersky Antivirus and our users are protected.






















Social apps, security problems