
On March 4th we spotted a large number of unusual emails being blocked by our Linux Mail Security product. The emails all contained the same PDF attachment (MD5: 97b720519aefa00da58026f03d818251) but were being sent from many different source addresses.
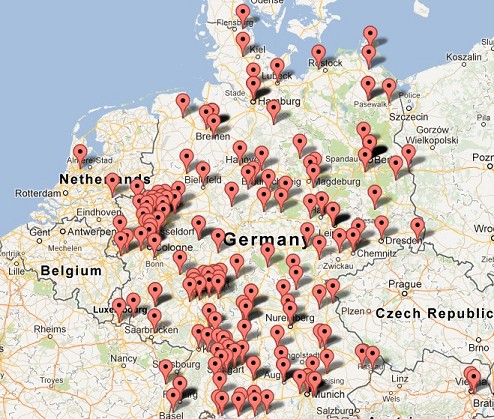
The emails were written in German and most were sent from German IP addresses. Below is a map showing the distribution of addresses:
The computer names referenced in the mail headers were often of the form Andreas-PC or Kerstin-Laptop (the names have been changed to protect the innocent) suggesting that they had been sent from German home computers.
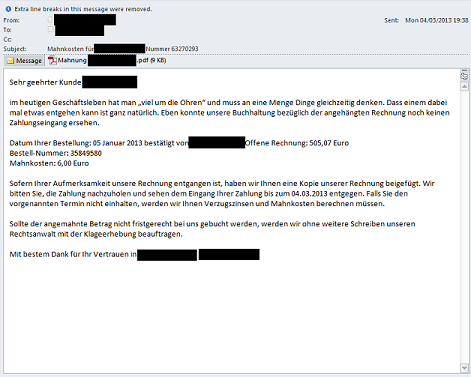
Below is an example email:
The PDF attachment names were of the form ?Mahnung recipents name.pdf¦ (Mahnung is German for ?reminder¦ or ?overdue notice¦) and the exploit used was CVE-2010-0188 (Adobe Acrobat libtiff Remote Code Execution Vulnerability). The PDF was blocked by Kaspersky ZETA Shield and is detected as Exploit.JS.CVE-2010-0188.e. The exploit is not easy to spot because it is hidden under two layers of JavaScript.
The second layer looks very similar to the JavaScript seen in several BlackHole Exploit Kit samples from last year. If the exploit is successful, it downloads an executable from seodirect-proxy.com/adobe-update.exe.
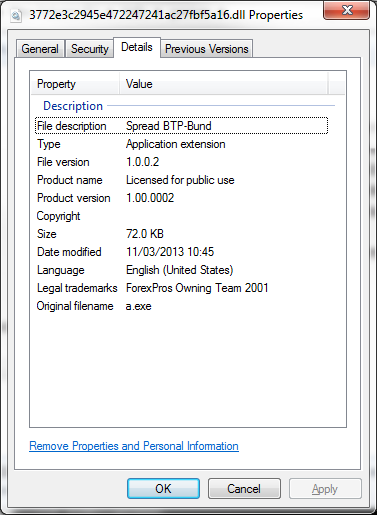
The downloaded malware (MD5: 3772e3c2945e472247241ac27fbf5a16) is detected by Kaspersky Lab as Trojan.Win32.Yakes.cngh. It contains various Italian strings (?lastoriasiamo¦, ?famiglia¦, ?badalamenti¦, impastato¦) which may be Mafia related. It also contains the following version information:
Apparently, BTP are Italian government bonds, Bund are German government bonds and ?Spread BTP/Bund¦ is a way of comparing the difference in yields.=
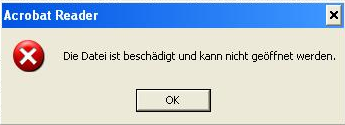
When the malware runs it displays the following error message:
It then installs itself in the temp directory with a random name (e.g. vlsnekunrn.pre) and attempts to contact zeouk-gt.com.
The Past
Looking back through our past feedback data, we noticed similar patterns on the 4th and 21st of several months.
February 2013
On the 21st February we blocked a large number of emails containing a very similar PDF attachment. This time the attachment names included the word ?Rechnung¦ (meaning ?invoice¦) and a date (e.g. Rechnung_201302.pdf and 2013_02rechnung.pdf). The senders were from a wide variety of countries including South Africa, United States, Australia and Japan. This time the computer names referenced in the mail headers looked randomly generated (e.g. ydopsgf and bxahwdkw) and interestingly, the headers also referenced the domain zeus3.hostwaycloud.com.
The decoded JavaScript for this exploit was almost identical to the sample above but the malware was downloaded from several URLs:
allgaeu-heimatwerk.de/biznessler/typo3/sysext/t3skin/host.exe
corcagnani.de/host.exe
kkc-hannover.de/modules/mod_search/helper.exe
capital-success.de/pg/helper.exe
January 2013
On 4th January the sample was called Rechnung201301.pdf and the malware was downloaded from the following URLs:
kohnle-gros.de/css/styleneu.exe
fairdealshop.co.uk/modules/mod_newsflash/helper.exe
emct.org.uk/downloads/server-stats.exe
November 2012
On 21st November the sample was called RECHNUNG000201211.pdf and downloaded the malware from:
rocketmou.se/stuff/corduroyshop/corduroyshop.exe
coachplay.co.il/mapa/images/mapa.exe
The Future
This seems to be a very well put together campaign and it doesn-t seem to be going away. So, if you receive an invoice on March 21st or April 4th, be extra cautious. Although, the authors may change their invoicing date, so it is better to be cautious all the time.





















Reminder: be careful opening invoices on the 21st March