
Over the last few months we have seen a series of very similar targeted attacks being blocked in our Linux Mail Security Product. In each case the documents used were RTF and the exploit was CVE-2012-0158 (MSCOMCTL.OCX RCE Vulnerability).
The attacks seem to be from the same group and most appear to be sent from Australia or Republic of Korea. The sender IP addresses vary but many are sent via mail.mailftast.com. This domain is registered in China:
|
1 2 3 4 5 6 7 8 9 |
REGISTRANT CONTACT INFO liu runxin No.1,Nanjing Road Shanghai Shanghai 200001 CN Phone: +86.2164415698 Email Address: <span class="mail">lishd2011@163.com</span> |
The documents are in three categories:
- The first group of documents are related to articles on the Men-s Health website. These are some example filenames:
12345EAT FOR BETTER SEX.docHow to last longer in bed.doc6 Awkward Sex Moments, Defused.doc9 ways to have better,hotter,and more memorable sex.doc10 Ways to Get More Sex.doc - The second group are military related:
123Stealth Frigate.docThe BrahMos Missile.docHow DRDO failed India's military.doc - The third set have Cyrillic filenames:
1234приоритеты сотрудничества.docСписок участников рабочей группы(0603-2013).docСписок кадров.docПриглашение МИОМ ТЕЙКОВО 2013.doc
Most weeks we will see one topic from categories 1 and 2 and several using Cyrillic filenames. The exploit, shellcode and malware used tend to be the same. The only real different is the decoy documents displayed when the exploit runs.
Here are two examples from last week:
Stealth Frigate.doc
EAT FOR BETTER SEX.doc
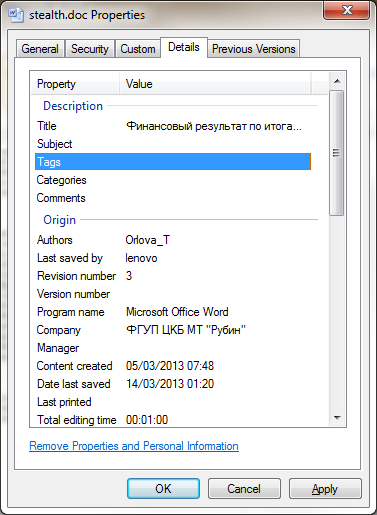
The metadata for the decoy documents is the same and it looks like it hasn-t be updated for a while.
The title translates as ?The financial result for the first 9 months of 2012¦ and the company name relates to a Russian submarine manufacturer.
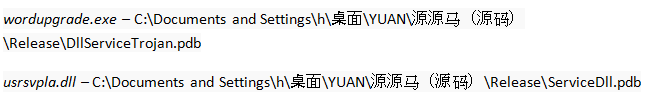
When the exploit runs it creates and executes a file called wordupgrade.exe. This executable drops a DLL called usrsvpla.dll into the system32 directory and modifies the WmdmPmSN (Portable Media Serial Number Service) registry key to load the DLL into svchost.exe.
Both wordupgrade.exe and usrsvpla.dll contain the PDB path:
The malware installed by these documents is a variant of Enfal/Lurid. We are detecting wordupgrade.exe as Trojan-Dropper.Win32.Datcaen.d and usrsvpla.dll as Trojan.Win32.Zapchast.affv. Our colleagues from Trend have previously described this malware in their papers.
The samples seen last week contact a C&C server at yui.bcguard.com. This domain has the same registration details a mailftast.com above.
Below are the IP addresses of these domains:
|
1 2 |
yui.bcguard.com - 208.115.124.90 (China) mail.mailftast.com - 142.234.156.3 (US) |
There are several other domains registered to ?liu runxin¦:
|
1 2 3 4 5 6 |
timmf.com bcbtheory.com bellbuttons.com atmdzxgs.com coffeeibus.com cymdbd.com |
Conclusion
The malware used in these attacks is not very advanced or new (Enfal variants have been seen as far back as 2006). However, the attacks are very regular, so it is probably safest not to open attachments related to these topics.




















Military Hardware and Men-s Health