
Back in April we detected a program for smartphones running Symbian S60 2nd edition (not-a-virus:Porn-Dialer.SymbOS.Pornidal.a) which calls premium-pay numbers to get access to pornographic material.
Today we added detection for a new variant of the program – not-a-virus.Porn-Dialer.SymbOS.Pornidal.c. Just like its predecessor, this application can be harmful for two reasons:
- if you install software like this and don’t pay attention to what you’re doing, you won’t know that the program will call premium-pay numbers;
- the program could be modified by cybercriminals to result in a clearly malicious program.
This new variant doesn’t really differ that much from the previous one – it’s also got a EULA – except that it works on devices running Symbian S60 3rd edition and has a digital signature.
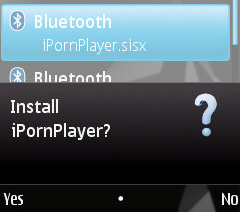
Once the install file (iPornPlayer.sisx) has been run, there’s a message about conditions of use:
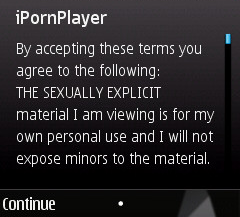
Agree to these, and more files get installed:
|
1 2 |
private10003a3fimportappsiPornPlayerrec.rsc sysbiniPornPlayer.exe |
Although the numbers which the program calls are different from the numbers in April’s app, they’re still in pretty much the same countries:
|
1 2 3 4 5 6 7 8 9 10 11 |
+438208***** (Austria) +239980***** (San Tome and Principe) +438107***** (Austria) +423662***** (Lichtenstein) +252302***** (Somalia) +417731***** (Switzerland) +674444***** (Nauru) +226505***** (Burkina Faso) +881842***** (Global Mobile Satellite System) +881942***** (Global Mobile Satellite System) +438209***** (Austria) |






















Porn dialers for smartphones, part 2