
One of the most complex tasks for the cybercriminals is to ensure their malicious code goes undetected by antivirus and achieves its goal. For this, they have invested a lot on more complex infection processes, going beyond the traditional phishing and using techniques where the malicious payload is hidden in encrypted files – even using a known file format. This is what we found in a new Brazilian Trojan in the wild: it tries to conceal the malicious files in a PNG image. And the attack starts with a simple phishing PDF.
Malware distribution
It looks like Brazilian cybercriminals follow the security news – this type of attack was publicized several months ago in the US and now they are using the same method in Brazil. The phishing aspect used in this campaign distributes a PDF attached to the email. The file is clean. The type of attack is the same as that used to distribute an executable file or a .ZIP file containing the .pdf extension in the filename.
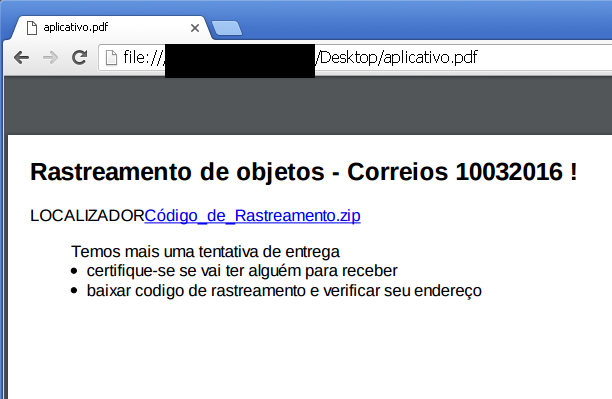
The attached PDF contains a text commonly used in mail content, while the link (see screenshot below) directs the user to the malicious file.
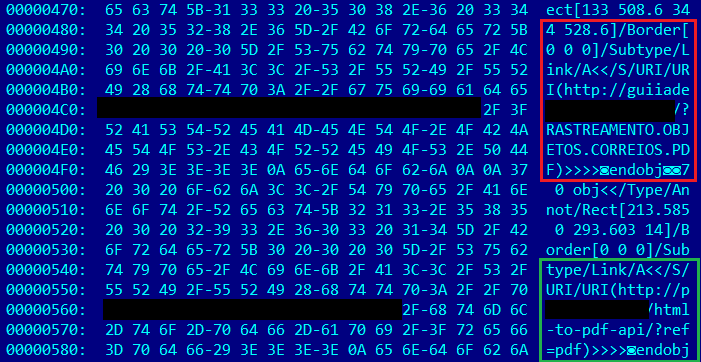
Closer inspection of the PDF content reveals the malicious link as well as the URL of the tool used to generate the PDF from HTML content.
The malicious payload
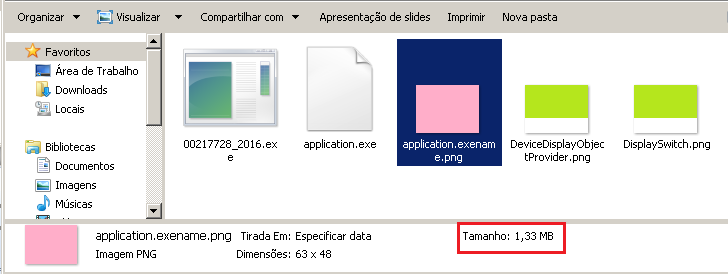
The link prompts us to download a malicious JAR which downloads a ZIP file containing other files. Among those files we found three without any extension, but containing a PNG (Portable Network Graphics) file header – a common image format. Usually the header shows the file type that will be used in order to open the file. Something similar to this was discovered some years ago in BMP files.
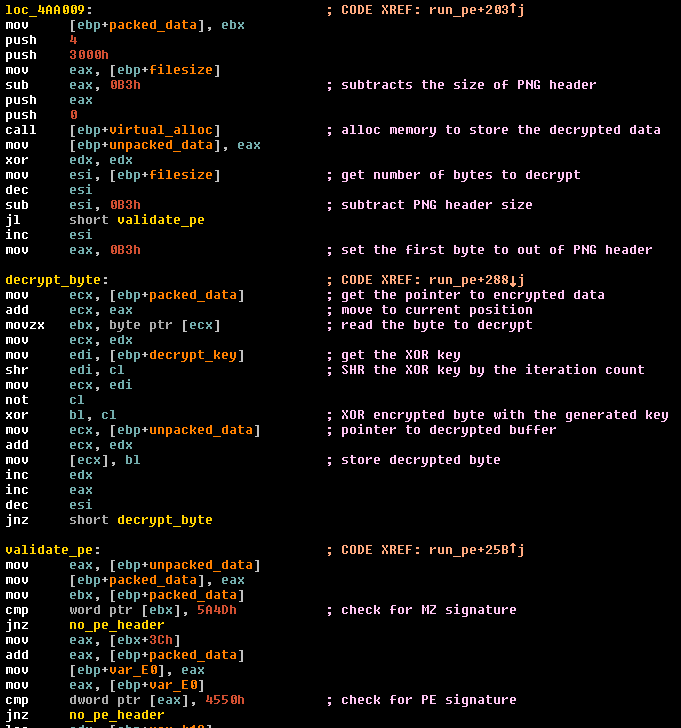
Looking at the file we can see that it is a solid color image of 63 x 48 pixels, but with a file size of 1.33 MB, which is too big for this specific image. Analyzing the binary that performs some operations on these files we identified the function that loads the PNG files to the memory:
This function is responsible for loading the PNG file to memory, decrypting and executing the extracted binary using a technique known as RunPE, where the malicious code is executed in the context of another process, in this case iexplore.exe.
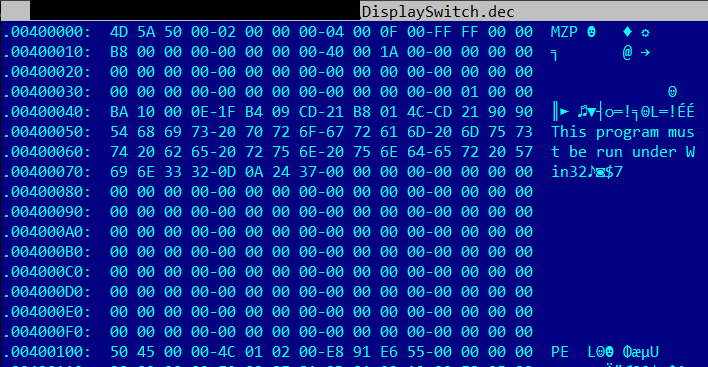
From this code we could identify that the PNG file was only 179 bytes (0xB3) – the remaining content is the encrypted malicious file.
Based on this we managed to write a script to decrypt the content of the PNG files.
By giving the key that can be found in the malware code we can successfully decrypt the files.
Conclusion
Brazilian attacks are evolving day-by-day, becoming more complex and efficient. It is there necessary to be wary of emails from unknown sources, especially those containing links and attached files.
Since the malicious payload hosted in the PNG file cannot be executed without its launcher, it cannot be used as the main infector; that is usually delivered to your mailbox, so it has to be installed by a different module.
This technique allows the criminals to successfully hide the binary inside a file that appears to be a PNG image. It also makes the analysis process harder for antivirus companies as well as bypassing the automated process to detect malicious files on hosting servers.
The files related to this attack are detected by Kaspersky Lab products as:
Trojan.Win32.KillAv.ovo
HEUR:Trojan.Win32.Generic
Trojan-Downloader.Win32.Banload.cxmj
Trojan-Downloader.Win32.Agent.hgpf
HEUR:Trojan-Downloader.Java.Generic
The URLs related to this attack are also blocked by Kaspersky Lab products.
PNG Embedded – Malicious payload hidden in a PNG file




















Mahhn
Very nice presentation/description. Thank you
Larry Saez
I got an unauthorized download called suspend_en.png in my tablet. Is it malicious? I have no idea where it came from or what to do to get rid of it.
Anthony Maw
Great article well explained. I note the screen shot of the decrypted content shows “This program must be run under Win32” – looks like Mac, Linux, or mobile device Android and iOS is immune at least to this kind of attack – the malware cannot run on those platforms it just downloads impotent binary files onto those device storage.
sei
Don’t be mistaken, the photo is only a vehicle for malicious code, any exploit can be used.
Robert
Thank you for the info sir. I followed an indeed link I received in an email which downloaded a PNG file. Not realizing it could potentially be harmful I open it to find it was the size of a pixel. I am on Android however so I hope this still holds true that I am safe from this particular type of attack.
Anon
Android, as can MacOS and Linux, any OS can be affected by this; this is just a delivery method, the exploits delivered can be tailored to specific OS of the attacker’s choosing.
rakesh
thanks for the use full information…..
have you any material or malware sample which hide inside .jpeg extension.
ike
Thiago, are you brazilian or portuguese? Very useful article, even to people with limited knowledge about this subject like me.
I am fascinated about this “new universe” tha internet baceme, even though my area of expertise is entirely different. I have a question, if you do’nt mind to answer… how long you guys have to study to get used to this as a second nature, as it seems is your case?
Sucess, “bon lavoro i buona fortuna”.
V
What are the names of the tools in your screenshots?
Dugan
~Well written with attention grabbing presentation!
I have a malware infection on multiple devices that is nearly undetectable and removable, surviving low level formatting of storage devices and transfers over a network like wild fire. The malware also doesn’t seem to be prejudice to OS’s as I see its presence on Windows, Linux and ARM platforms, which are installed on various devices i own. I have suspected that the malware resides in several .PNG files and possibly other visual based file formats such as .JPEG. files but have not able to confirm this suspicion until recently when I noticed an odd file size associated with a very small image file. I discovered the image file with my browser, using the page information and development tools, which showed me that the web page I was on was not secure and that changes had been made in the coding. I also noted that when looking at the file properties that there were multiple oddities in the naming convention, file permissions, security context and time stamps. The image file was stored locally on my PC however and was not part of the web page or browser.
I also believe the malware to be hidden in the content of multiple audio file but have not been able to confirm this suspicion. For nearly two years now, I have been unsuccessful in removing the malware or finding anyone who can help me. After reading this article, I am hopeful I have found help or someone who may direct me to an organization that can Thank you.
Srk
Hello,
Need an malicious image for my school project where I am feeding the image to an ai model for test purposes.
Securelist
Hi Srk!
We do not share samples, as they are provided by our customers and are confidential data.