
Recently the security of public cloud services has been a major topic of discussion on the Internet. While service providers assure us that there’s nothing safer than the ‘cloud’, security companies have already managed to discover various kinds of threats in the cloud.
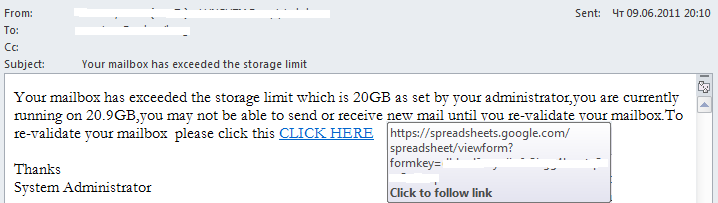
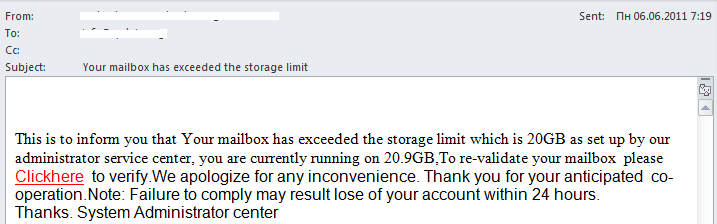
In the meantime, spammers are managing to keep up and have started making more active use of free remote resources. For instance, we recently came across the following phishing messages for harvesting email passwords:
A particularly attentive user will quickly recognize them as fakes due to a number of formal attributes:
– impersonal address;
– while the ‘From’ field contains one domain, the link in the letter body leads to another;
– typos (“Clickhere” written as a single word);
– impersonal signature (“System Administrator center”);
– threats to close the account if the user does not follow the link within a certain period of time –
a typical phishing ploy.
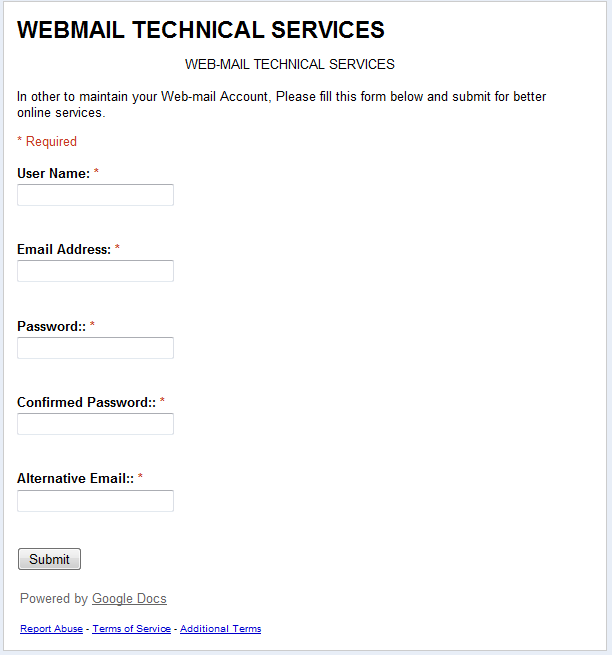
Even more interesting is the fact that the link leads to a phishing page, which is not located at a normal address but at spreadsheets.google.docs – a free service for creating spreadsheets on remote Google servers. The user is asked to fill in a form which includes fields such as ‘Email Address’ and ‘Password’. If users click the ‘Submit’ button, they send the data directly to the phishers.
This service provides cybercriminals with free space to place their fake pages. Even worse, this sort of page will appear to be quite genuine to unsuspecting users: first, it is located at a well-known resource, and, secondly, the connection is made via https, which supports encryption.
Of course, I clicked on ‘Report Abuse’ where some (but not all) of these types of pages have already been closed. This, however, is not the solution to the problem on a global level: cybercriminals are certain to continue using cloud services, which are ideal for their activities.
So, once again, I would like to urge users to be very careful and not to click on suspicious links.



















Phishing in the clouds