
Continuing our investigation on the Osama’s death campaign, we were especially concerned about the potential distribution of malware on social networks, because of their speed of propagation. So we have been monitoring Twitter, getting some million tweets and a huge number of URLs too. No surprise here as during the last 24 hours the average was 4.000 tweets per second related to this topic. Here you can see how even Internet traffic was affected.
Analyzing these URLs, we found some interesting stuff.
The first one is a Facebook scam campaign posing as Osama’s death video:
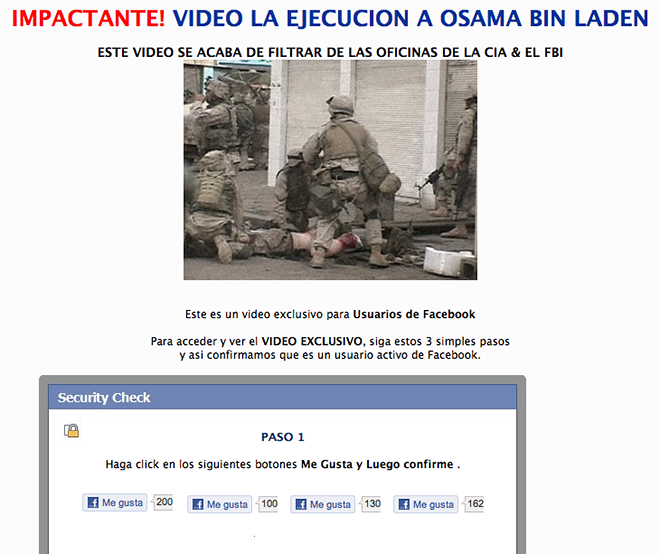
We have found this link being distributed in several tweets, especially among Brazilian users.
The second is malware being distributed, again as Osamas death video. In this case the link is not so subtle, including a .rar file in the URL.
It is interesting how the Twitter user distributing it also tried to do that posing as Fast and the Furious movie. In this case the distribution is very low.
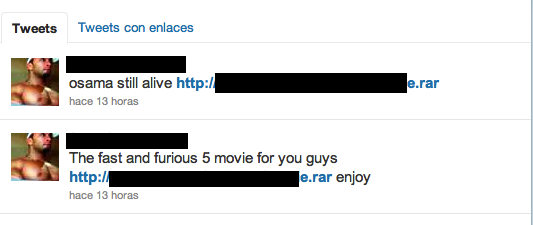
This malware is detected by our heuristic engine.
But the point is how malware reacts quickly to use major events for its distribution, registering domains and using social networks in the first hours. We will keep monitoring and analyzing them in order to protect our customers, but we urge you to be very careful to avoid these scams.
Update:
We have detected a new infection trend. In this case is a click-fraud-like campaign intended to redirect traffic to a site with publicity on it.
Below you can see an example showing how the campaign is being propagated. It is interesting to see how the trend topic changes in order to keep the campaign successful but below the radar. Also all the shortened URLs are different:
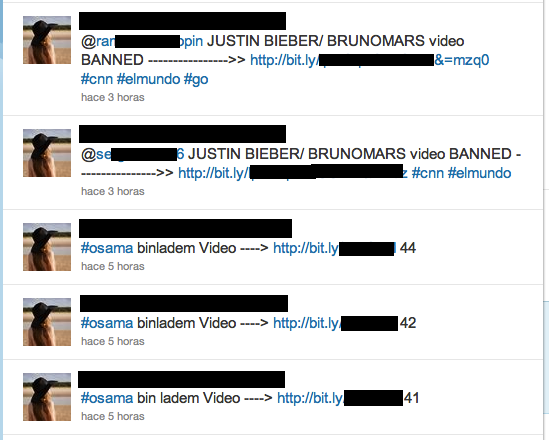
When you follow the URL, the destination page poses as a Youtube video. In this case instead of asking the victim to download a binary, when clicking the button a new malicious tweet will be created in the victims account, “replicating” itself.

Again, the purpose of the fraud is just to redirect traffic to a page with publicity, allowing the attackers to get some money thanks to a trending topic.






















Osama’s death in Twitter