
For a long time we´ve been interested in operational security (OPSEC), and although you can find tons of cool technical tips about protecting digital information, we always felt that something was missing. After all, we live in a physical, or analog world as well as a digital one, and we have encounters with other real people. After asking around, we found that one of the biggest worries of our technical community was how to behave during these interactions. So we decided to work on creating some realistic and easy to remember tips for exactly these situations.
Threat modeling
OPSEC is all about hiding information from your adversaries. We categorized our adversaries into just two groups: those who have resources and those who don´t. Plain and simple.
The first group comprises intelligence agencies, military organizations and the big bad boys. The second contains the rest. Important: no resources is not the same as no danger, but they are less able to track you unless you give away information for free.
Our tips are focused on encounters with the first group, since that is more likely to happen.
Recruitment
Agencies are always on the look-out for new assets to recruit – this is what they’ve been doing for centuries.
It all starts with the spotting process, identifying an asset who could meet their requirements based on the position and access to information. Next they profile the target, partly using OSINT. After that it’s time to choose between the carrot and the stick, and pick out the most effective motivators on offer: money, blackmail, ideology, sex, etc.
Then some guy will approach us, maybe in person, maybe through LinkedIn. He’ll probably pose as some businessman who will pay us a lot for nothing much, just a few easy reports from time to time.
When this happens we want to get to the Termination phase ASAP, ideally after being written off as a waste of time and effort.
We can just say “No”, but they may keep increasing the pressure. On the other hand, we can refuse while providing alternatives, redirecting the request to another person ready to handle this.
Create a protocol for yourself and your organization in order to handle these situations effectively, minimizing the researcher ´s exposure. Be prepared in advance for situations where we are more vulnerable.
Borders
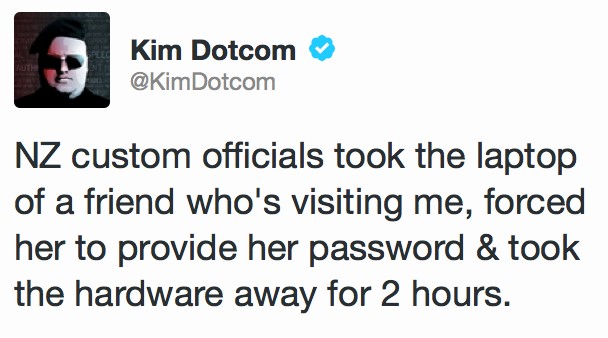
Crossing an international border can be one of the most vulnerable places. Somehow they are like a parallel dimension: although you are physically in one territory, the laws are just different, or maybe even non-existent.
We´ve learnt a few things regarding borders: there is always some exception to the law that officers might use in extreme scenarios. You can find legal advice here https://www.eff.org/wp/defending-privacy-us-border-guide-travelers-carrying-digital-devices. However this is what you should NOT do:
- Regardless of whether you consent to a search or not, do NOT stop the officer if he starts checking your stuff. This is a felony.
- You don´t have to answer questions, but if you decide to do so, do not lie to the officer. Again, a felony.
This is our advice about how to react in a situation like this. These rules will provide you with peace of mind, help you stay calm and not freak out. Hopefully they will stop you overreacting, making things worse and talking too much, starting with: “I have nothing to hide, let me explain …”.
- Be cooperative.
- Don´t make things worse.
- Have your story prepared and be ready to back it up.
- Golden rule: Don´t bring any valuable content with you! You should encrypt, upload and retrieve on arrival at your destination.
Other situations
Sometimes we could find ourselves going to a meeting in a strange country with a suspicion that something is not quite right. Some advice for this:
- Don´t go alone.
- Don´t rely on your host for transport
- Plan exit routes and “safe” places, have your contacts ready.
In some cases the meeting itself won´t be the “trap”; it’s just an excuse to get you to leave your computer in a known location the hotel, or in a cloakroom.
It is always a good idea to let someone know where you are going and tell them to react if you don´t ping them in a reasonable period of time. This also lets your adversaries know that you are ready – a simple casual comment will do the job.
Another concern is physical surveillance. To be honest, if this is done by sophisticated professionals there isn’t much we can do about it and we probably won’t even notice. But remember – don’t try anything stupid; you’re not James Bond. Acting like it’s a movie can only make things worse.
If you are very concerned, escalate the situation and involve the person in your company who is responsible for dealing with local contacts. If you feel uncomfortable, move to a public place or directly move to your embassy.
Conclusions
You’ve probably already spotted a common theme in most of all these situations. First, keep calm and do not make things worse. You can rely on a third party to send in the cavalry when you need it. This is why your company should provide you with a single person to contact when you’re in trouble. Also you might need international legal support.
However the key lesson is: do your homework. If you travel abroad, spend some time finding local contacts, get the telephone number and directions for your embassy, plan your meetings, let other people know where you are and make sure they are ready to act quickly in certain situations. Have your travel laptop ready and consider what information you bring with you. If you remember your lessons, you will be fine.
Analog OPSEC 101 – operational security in the physical world





















KhunpremPB Nobu
Thank you very much