
We all play games. Some play sports, some gamble, and for some people, life itself is a game. Even computer games have become an everyday phenomenon, with millions of people playing them. Some choose Tetris, others choose Counter Strike, and everyone has fun.
The growth of the Internet has given birth to a new type of computer game: games which players can play on any computer, with thousands – even tens of thousands – of players around the world. In the world of MMORPGs (Massive Multiplayer Online Role Playing Games), also known simply as online games, players can meet other players, become friends, engage in battle, fight shoulder to shoulder against evil, find their virtual destiny – and play, play, play…
However not all is well in these virtual worlds, where virtual evil can become greedy reality. Online games are played by real people, including thieves and con artists who make real money by stealing other people’s virtual property.
This article will explore how MMORPG passwords and virtual property are stolen and how other malicious acts are committed against MMORPG players.
The Games
Online games involve exploring magnificent virtual worlds and completing tasks – known as quests – which gain the players money, valuables and experience, not points as in a more traditional computer game. These virtual riches, which are earned with the character’s blood, sweat and tears, can then be spent on other in-game valuables. These attributes, once purchased are used to complete even more difficult quests, earn more money, or to enable the character to simply continue wandering the game – there is no “Game Over” in online games.

A battle scene in the online game Lineage 2 (www.lineage2)
Online games have rules that are determined by the developers and administrators of game servers. These are the people who spend their time and real money creating and supporting virtual worlds, and this is how they earn a living.

Monica Almeida / The New York Times The support center at Blizzard, World of Warcraft developers (www.nytimes.com)
Online games can be purchased at stores or downloaded from the Internet, but in order to play you usually have to pay a monthly subscription fee. The money from these monthly fees covers traffic costs, support for game servers, the creation of new virtual worlds and new items for players (swords, spears, ships, etc.). Players can “live” for years in these rapidly growing and constantly evolving virtual worlds.
Piracy
The world of online games moves very quickly: each year new games are released and the army of players continues to grow. Almost immediately after the licensed version of a new game has been released, pirate (rogue) servers begin appearing. These rogue servers offer free versions of the worlds provided in the licensed, fee-based games.

World of Warcraft launches sales in Europe (www.worldofwarcraft.com)
The number of rogue servers is enormous. For example, a Google search for “private game server” on 22 June 2007 returned approximately 10,800,000 results and that number is constantly on the rise. One popular online game can spawn hundreds of thousands of rogue servers. This high number results from the fact that rogue servers are in high demand among players who want to save money or who simply don’t have any, like teenagers and students. The idea is very tempting: why pay a subscription to an official server every month when you can play the same game on a rogue server and you only have to cover traffic costs? However, in reality the situation is very different…
Opening a rogue server is not an easy task. Servers have to be administered and supported, and this includes financial support that covers the cost of traffic at the very least. Why do pirates bother? The answer is simple: the administrators of rogue servers sell virtual valuables for real money. Judging by the type of equipment administrators lease for servers, the sale of virtual goods brings in a considerable income.
The game quality on rogue servers is much worse than on official servers, and this creates a number of problems for players. Errors, glitches, occasional disconnects – these are all factors that slow down the game and spoil the gaming experience. It makes no difference how the player plays – masterfully, well, or poorly… Sooner or later he will realize that he’s going to be stuck on one level of the game for a very long time. This is when a player on a rogue server might resort to asking for assistance from the administrator, who is prepared to sell virtual valuables for real money (rogue servers often have pre-prepared public price lists for a range of goods and services).
The sale of virtual valuables for real money exists just about everywhere on a game server, although the game, the status of the server (rogue or official) and administrator policy will determine whether or not such sales are permitted.
Theft
Are game server administrators the only ones who can sell in-game valuables? Or can players do it, too? They can – and they do. But these “trade relations” may be prohibited by server administrators, especially those on rogue servers, because the administrator will not receive a cut. However, banning certain actions will not necessarily stop players from doing business. Some people sit down at the computer, play, earn a valuable in-game item, and sell it later for real money.
The online gaming world is a surprisingly lucrative place. There are sites where users can find the prices for in-game money on official game servers. These are, of course, illegal sales – almost all of the games listed on such resources discourage the sale of in-game valuables for real money.
Any valuable item in an online game can have a monetary equivalent in the real world. This is when demand arises and when other peoples’ virtual property is stolen. But how does this work? As it turns out, it’s fairly simple if you have the right skills and knowledge.
The player authorization system (which verifies player authenticity) in most online games is based on a password system. A player logging onto a server has to enter his username and password. Once the server has identified the user, it will allow the player to enter and s/he then has complete freedom within the game. A malicious user who enters someone else’s password can simply steal items from his victim and sell them.
Stolen items are put up for auction (on sites such as ebay.com and forums), and can be sold to other players for virtual or real money. A cyber criminal may also demand a ransom for the stolen items. Sad as it may seem, malicious users can really rake in the money from online games.
Buying stolen goods is, of course, punishable according to server rules. Players on official game servers know that if there is an incident, the administrators will act in their favor. A player can file a request or a complaint at any time and problems will be addressed as quickly as possible so that s/he can keep playing.
Rogue servers – which greatly outnumber official servers – are a different case. Since players don’t pay for support, the administration doesn’t have to deal with problems. Victims have almost no opportunity to prove that they were not involved in problems which arise with their in-game items. Proof that a password has been stolen is usually ignored; the justification for this is that any conversation can be falsified, and screenshots can be faked. False evidence can be used to accuse an innocent player who is a bothersome opponent and get him/ her removed from the game (e.g. there are penalties for using inappropriate language in-game, with the most stringent being banned from the game for several days). Money can also be made from faking the theft of items and then demanding a ransom. Administrators of rogue servers have no way of dealing with such issues, and no desire to do so.
As a result, malicious users don’t have to worry much about their actions on rogue servers, since in most cases there won’t be any comeback. On official servers the situation is much better. Players who are involved in theft will have their accounts closed and in some case their IP addresses will be blocked.
Overall, the theft of online game passwords is a serious issue. Every player is a potential target for malicious users.
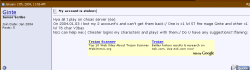
A message on a gaming forum (and some appropriate Google Ads)
How passwords for online games are stolen
As a rule, malicious users are only interested in a victim’s username and password, not the address of the server where the victim plays. The malicious user knows which server the victim plays on and is likely a player on the same server. This is the case both for thieves who earn their money on rogue servers and for those on official servers, even though the likelihood of players losing in-game items to thieves on rogue servers is much higher.
Let’s take a look at some of the methods used by cyber criminals to steal passwords.
Social engineering
One method used by cyber criminals is to enter a game or a forum on a game server and offer a bonus, or help in the game, in exchange for other players’ passwords. The cyber criminal who makes such an offer is not as naive as he may initially seem. Instead, it is the players who are looking for ways to make play easier, and who respond to such offers, who are naive. The malicious user achieves his goal (getting hold of passwords) and leaves his/ her victims with nothing.
Another well-known social engineering method is phishing, where the cyber criminal sends phishing emails, purportedly from the server administrators, which invite the player to authenticate his/ her account via a website linked in the message. Below is an example of this kind of tactic.

An example of a phishing email: the links lead to a phishing webpage at http://lineage***.ru (forum.lineage2.su)
Translated, the message reads as follows:
Hello,
You have been sent this email because you are a registered user on our server (www.Lineage2.su). Because the number of registered users of our server has increased sharply over the last month, we have to purge inactive accounts from our database. Please confirm that you still play on our server by undergoing authentification here:
If you do not authenticate your account within 48 hours of receiving this message your account will be deleted, and it will not be possible to restore it.
Yours,
The Lineage2.su administrators
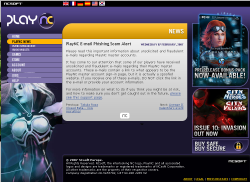
News about a phishing attack on gamers’ accounts. (eu.plaync.com)
Although such password harvesting techniques are simple and reasonably effective, they don’t result in much profit for malicious users, as more advanced, “wealthy” players don’t take the bait.
Exploiting game server vulnerabilities
A game server is a collection of system services, programs and databases designed to support gameplay. Just like any other software, the server code contains programming errors and bugs. Such potential vulnerabilities can be exploited by cyber criminals to gain access to server databases and harvest player passwords or password hashes (encrypted passwords that can be decrypted using dedicated programs).
For instance, there is a known vulnerability linked to in-game player chat. If the chat environment is not isolated from the game’s database and if special symbols/ commands are not checked, then a malicious user can access the player database directly from player chat either manually or by using a dedicated utility.
In-game chat in Lineage 2 (www.lineage2.com)
The number of vulnerabilities which a malicious user can exploit to gain access to internal server databases depends on the server. Creating special patches for vulnerabilities on rogue servers is a time-consuming process, more so than for official servers (if, of course, the administrator of a rogue server even feels it necessary to patch a vulnerability).
Another way to get passwords is by exploiting the mechanism used to remind users of forgotten passwords. Cyber criminals send specially crafted requests to the system (or simply use a brute force approach, running through possible answers to security questions), then change the victim’s password and enter the game using the new password, which of course the user doesn’t know.
Exploiting server vulnerabilities can be complex, and preparing and conducting an attack requires a great deal of intellectual effort. The result is often wasted time and effort as many hackers simply don’t have the technical skills necessary to conduct a successful attack.
Using malware
Malicious users often create malware which is then spread using any means possible:
- publishing links to malicious programs which purport to be game patches on player message boards;
- sending in-game spam containing links to a malicious program presented as a “new patch”;
- sending spam via email with a malicious program attached, or a link to a malicious program;
- spreading malicious programs via file sharing networks;
- exploiting browser vulnerabilities in order to download malicious programs when a user visits a game-related website.
More often than not, cyber criminals simply publish a link to a malicious program in-game or on a message board with a message about the great new patch/ utility/ add-on and how it makes playing so much easier…
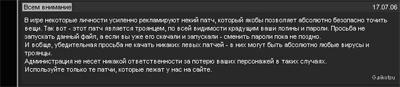
Translated, the message above reads as follows:
Attention all
Certain people in this game have been forcefully recommending a certain path, which allegedly makes it possible to enchant items completely safely. This patch is actually a Trojan which steals your user name and password. We ask you not to launch this patch, and if you’ve already downloaded it and launched it, it’s still not too late to change your password.
And here’s a general earnest request – don’t download any dodgy patches because they could contain all types of viruses and Trojans imaginable.
In such cases the administrators won’t take any responsibility for the loss of your characters.
Only use the patches which are on our site.
There are some malicious programs which only attack online game players, as well as malware designed to steal any kind of password (including passwords to online games). The most widespread programs used to steal online game passwords according to Kaspersky Lab’s classification, are Trojan-PSW.Win32 representatives and variants of the Trojan.Win32.Qhost family.
The first group of Trojans uses traditional methods to harvest data entered via the keyboard; if the player enters his/her password, the server name and other information using a keyboard on an infected computer, a malicious user will then have access to this information.
The second group of Trojans works by modifying %windir%system32driversetchosts. This file contains information about the static correspondence between the network address and the server name. If a false game server address is entered in this file, the gaming client will be authorized on the malicious user’s server (which will be sent the password) rather than on the real server.
Some Trojan-Spy.Win32.Delf variants also deserve a mention. This family configures a false proxy server in Internet Explorer which is then used to connect to online game servers (in this case, just as with the hosts file described above, all user login data is sent to the malicious user). For online games where players do not need to enter their password (a deliberate move which is designed to protect users against keyloggers), passwords are not sent to malicious users as letters or symbols, but in the form of gameplay screenshots.
Some Trojan-PSW.Win32 variants hook web forms on certain websites. Web forms are also used to harvest user passwords to an online game. Many game servers allow access to statistics or other information relating to the game via the server’s web interface if a user name and password are entered. It is when the user name and password are transmitted that this data can be stolen.
Stolen passwords can be transmitted to a malicious user via email, instant messaging, by placing a password on an FTP server, or by giving network access to a file or folder that contains the password via the Internet, FTP, or a shared folder.
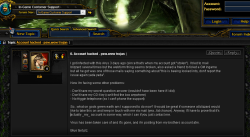
Message from a gamer about a password stolen by a malicious program
Because using malware to steal passwords is so simple (a malicious user does not need to have any technical skills) and so lucrative, malicious users tend to use this method more often than other techniques for stealing passwords.
The evolution of password stealing malware
The driving force behind evolution is natural selection. Antivirus programs act as the first line of defense for computers and have played a substantial role in the evolution of malware designed to steal passwords to online games. The stronger the defense, the harder it is to evade it; in response, malware becomes ever more complex.
The first malicious programs for online games were primitive, but today they use the latest in malware writing technology. Their evolution was threefold: the evolution of password stealing functionality, which also deliver the data to a malicious user (Trojan-PSW programs, Trojan-Spy programs); the evolution of propagation techniques (worms and viruses); the evolution of malware self-defense techniques against antivirus programs (rootkits, KillAV, and packers)
Trojans
The first recorded use of a malicious program to steal user passwords to online games was recorded in 1997 when antivirus companies began to receive emails from Ultima Online players containing malicious software for analysis. Initially these programs were classic keyloggers. Keyloggers are Trojans that do not have any direct connection to online games; they record all keystrokes made by the user (including passwords to online games).
The first malicious program to target MMORPG passwords was Trojan-PSW.Win32.Lmir.a, which appeared in late 2002. This was a simple program written in Delphi. At pre-programmed intervals it would search for windows entitled “Legend of Mir 2,” and then send all the data entered in the windows to the malicious user’s email. This malicious program was developed in China; it was not particularly original in terms of programming, nor did it seem likely that it would become particularly widespread. However, this simple and unremarkable Trojan soon became a classic among malicious users dealing in stealing MMORPG passwords. This Trojan’s source code was released onto the Internet and was then modified for other online games – a relatively easy task. Once the name of the game under attack was changed (to “MapleStory,” for example), the Trojan would steal passwords for that game. These simple modifications soon triggered the unstoppable growth and spread of MMORPG malware.
The spread of Trojan-PSW.Win32.Lmir and the large number of variants are the result of several factors:
- the popularity of Legend of Mir, the original target of Trojan-PSW.Win32.Lmir;
- the large number of servers dedicated to this game;
- the ability to spread Trojans by exploiting vulnerabilities in Internet Explorer – malicious users hacked game server websites and added a script that downloaded and launched the Trojan on players’ computers;
- the appearance of over 30 Trojan-PSW.Win32.Lmir constructors (Constructor.Win32.Lmir – dedicated software for creating and configuring Trojans designed to steal passwords for Legend of Mir 2).
Once Trojan-PSW.Win32.Lmir had proved effective, malicious users began to rewrite the program to target other popular online games. Successors to this program include Trojan-PSW.Win32.Nilage (which targeted Lineage 2) and Trojan-PSW.Win32.WOW.a (which attacks World of Warcraft players). These appeared in 2004 and 2005 respectively, and are still the most popular programs among malicious users since the popularity of the games they target continues to grow. Most Trojans of this sort are designed to steal usernames and passwords for online games on .tw domains, and later transmit the stolen data to an email or an FTP server on a .cn domain.
Most Trojans are designed to target specific online games. However, in 2006 Trojan-PSW.Win32.OnLineGames.a appeared and began stealing passwords for almost all popular online games (naturally, from server addresses where victims had already registered). The list of games targeted by this Trojan continues to grow.
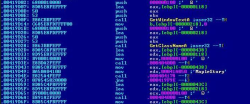
Part of Trojan-PSW.Win32.OnLineGames.fs, which steals passwords, specifically to MapleStory
A modern Trojan designed to steal passwords for online games is typically a dynamic library written in Delphi that automatically connects to all applications launched in the system. When it detects that an online game has been launched, this kind of malicious program intercepts the password entered via the keyboard, sends the data to the malicious user’s email and then deletes itself. Using a dynamic library makes it possible for the Trojan to mask its presence in the system, and also simplify installing the Trojan to the victim machine using a Trojan-Dropper, a worm, or other malware.
Worms and viruses
Since online games are so popular around the world, it’s not that difficult to find a player among average Internet users. This is why self-replication became an important factor as malware designed to steal passwords for online games evolved. These programs are designed to target as many different players as possible, from different games and servers.
The first worm to steal passwords for online games was Email-Worm.Win32.Lewor.a. This worm sent itself to addresses harvested from Outlook Express address books on infected computers. If the worm finds the user name, password and server address for “Legend of Mir” on an infected computer, it saves that data to an FTP server belonging to a malicious user. The first mass mailing of Email-Worm-Win32.Lewor.a was recorded in early June 2004.
Authors of malicious programs designed to steal passwords for online games began to add a self-replicating function to their creations. The malware would be designed to copy itself to removable disks with an additional file called “autorun.inf”; this would launch the malware when the infected disk was connected to a computer (although infection would only take place if the computer was set up to allow this kind of auto run). If a user connected a flash drive to an infected computer, the malicious program would automatically copy itself to the flash drive, and then when the infected flash drive was connected to another computer, the malicious code would be automatically launched and subsequently infect any other removable disks. (Victims included the clients of copy centers, who brought the material they wanted printed to the centers on flash drives).
Soon other kinds of malicious programs began to appear that could infect executable files and copy themselves to network resources. Such infection routines gave virus writers another opportunity to spread their creations and presented antivirus companies with another issue to address. When a malicious program has the ability to copy itself to folders accessible to a number of users (e.g. via P2P or via Microsoft Networks shared folders) this considerably increases the number of potential victims.
One example of this class of malicious programs is classified by Kaspersky Lab as Worm.Win32.Viking. The successor to Viking, Worm.Win32.Fujack was another step in the evolution of the mass spreading of malicious programs for online games.
Currently, the most recent achievement by those writing viruses for online games is the polymorphic Virus.Win32.Alman.a and its successor, Virus.Win32.Hala.a. In addition to infecting executable files, these malicious programs include worm functionality (the ability to propagate via network resources) rootkit functionality (the ability to mask its presence in the system) and backdoor functionality. An infected machine will connect to a designated server in order to listen for commands from a malicious user. Such commands may include the command to download and launch programs which are classified by Kaspersky Lab as Trojan-PSW.Win32.OnLineGames.

Part of a file infected by Virus.Win32.Alman.a
Both Alman.a and Hala.a contain a list of executable files which should not be infected. In addition to files belonging to other malicious programs, the list includes files belonging to online game clients. Why?
As a protection mechanism, both online games themselves and antivirus solutions may prevent modified executable files from being launched. Malicious users have taken this into account – they don’t want players to be prevented from playing on infected machines. After all, a victim machine infected with Trojan-PSW.Win32.OnLineGames will enable the cyber criminals to get their hands on gamers’ passwords.
| Month, year | Trojans | Worms | Viruses |
| 1997 | Classic keyloggers | ||
| 2002 December | Trojan-PSW.Win32.Lmir.a | ||
| June 2004 | Email-Worm.Win32.Lewor.a | ||
| October 2004 | Trojan-PSW.Win32.Nilage.a | ||
| February 2005 | Worm.Win32.Viking.a | ||
| December 2005 | Trojan-PSW.Win32.WOW.a | ||
| August 2006 | Trojan-PSW.Win32.OnLineGames.a | ||
| December 2006 | Worm.Win32.Fujack.a | ||
| April 2007 | Virus.Win32.Alman.a | ||
| June 2007 | Virus.Win32.Hala.a |
Self-defense technologies in malware for online games
The constant attempt to outwit antivirus companies has caused virus writers to implement self-defense technologies which will help their creations outwit antivirus software.
The first step was the use of packers – a move designed to hide code from signature scanning. Using packers protects program code against disassembly and makes it more difficult to analyze malicious programs.
The next stage involved the use of kill-av technology, which enables malware to either disable a computer’s security solution, or to make itself invisible to antivirus programs.
The latest move in malware for online games self-defense is rootkit technologies. Such technologies can hide the actions of malicious programs both from antivirus software and from all system processes.
Today’s MMORPG malware generally uses a combination of these three techniques.
As an example, Lineage2 is significantly more popular in Asia, whereas World of Warcraft is more popular in America and Europe. Trojans for these games, such as Trojan-PSW.Win32.Nilage (which steals passwords for Lineage II) and Trojan-PSW.Win32.WOW (which targets World of Warcraft), have evolved in noticeably different ways. The first program uses packers to make itself more difficult to find when scanning for signatures, enabling the program to mask its presence in the system and go undetected by an antivirus scan. The second directly counters antivirus programs by disabling security functions on the victim machine.
How modern attacks are conducted
The evolution of malware designed to steal passwords for online games lags behind the evolution of other malicious programs. This can be explained by the relatively recent emergence of online games and the malicious programs that target them. For a long time, such malicious programs were very simple and were written only in Delphi, making it easy for antivirus programs to detect and delete them. But over the past two years, in an attempt to undermine the protection provided by antivirus solutions, the authors of malicious programs targeting online games have adopted a new strategy. Today, attacks on computer players are conducted by creating worms that have multiple functions: they can self-replicate (email worms, P2P worms, network worms), infect executable files (viruses), mask their presence in the system (rootkits) and steal passwords (PSW Trojans).
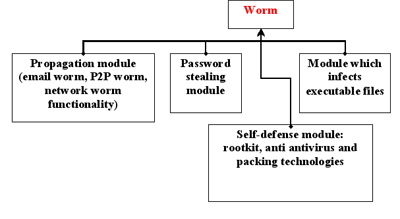
Components of malware designed to target players of online games
In a typical attack, a worm with multiple functions will be mass-mailed. One careless move by a recipient of this type of spam (clicking on a link within the message, opening an unknown file, etc.) means that all the executable files on the computer will be infected, the worm will send itself to all the addresses in the user’s address book, and the malicious code will then be present on all network resources it is able to access. But the victim won’t notice a thing, because the rootkit technology will mask its presence in the system.
Interestingly, in almost all these kinds of attacks, the stolen passwords are sent to an email address or a FTP server on a .cn domain.
Geographical considerations
When talking about the theft of passwords to online games, there’s an inevitable “Asian flavor”; statistics show that this region contains the largest number of online game players. The theft of passwords to online games primarily concerns China and South Korea. The reasons why aren’t entirely clear, but the figures speak for themselves: over 90% of all Trojans targeting online games are written in China, and 90% of the passwords stolen by these Trojans belong to players on South Korean sites.
New Trojans for online games do appear very rarely in other countries, but the number of modifications almost never exceeds 2 or 3.
Computerization and the rapid growth of IT in Russia have naturally had an impact on the evolution of computer entertainment. A typical feature of the Russian gaming industry is the popularity of BBMMORPG (Browser-Based Massive Multiplayer Online Role Playing Games). These games, the most popular of which was Fight Club (Combats.ru) in 2002, do not have a separate gaming client: all the action takes place via the browser.
A screenshot from the popular Fight Club (www.mjournal.ru)
The abundance of such games, and the huge number of people playing them, naturally attracted the attention of Russian cyber criminals. Russian attacks primarily utilized phishing methods in order to spread malicious programs. Numerous clone sites for Fight Club and other games began to appear on the Internet, as did links to these sites in phishing emails.
During one attack, an email – allegedly sent by the website’s administrators – informed the recipient that the game server’s address was changing. When players tried to enter the new address, they got an error message. A bot installed on the false site automatically changed the passwords that players entered on the game’s original server. As a result, users were unable to enter the game under their old passwords, and the thieves now had new “legitimate” passwords that gave them full freedom in the game, together with the opportunity to get their hands on someone else’s virtual property.
The phishing emails and the sites themselves are classified by Kaspersky Lab Trojan-Spy.HTML.Fraud and Trojan-Spy.HTML.Combats. But this seems to be the end of the road for Russian cyber criminals. There are, of course, other examples of new malicious programs, but there is no reason to believe there might be any large-scale attack against online game players in Russia. Attacks are limited to phishing, and the use of classic keyloggers which do not specifically target online games.
Some statistics
In contrast to Russia, the rest of the world is facing a constant increase in the number of new malicious programs and new modifications of known malicious programs that target online games. Kaspersky Lab currently receives more than 40 malicious programs targeting passwords to popular online games every day. Furthermore, the quality and quantity of these samples is constantly on the rise due to the response of antivirus companies and the increased popularity of online games. Most of these programs are coded to target specific game servers.
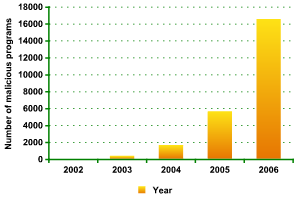
Total number of malicious programs targeting online game passwords
In 2002, nearly 99% of all MMORPG malware samples that were sent to Kaspersky Lab were classified as Trojan-PSW.Win32.Lmir. But later, as new games emerged and became more popular, the number of malicious programs targeting Legend of Mir fell considerably. Today the most popular MMORPG targets are Lineage 2 (more than 40% of all Trojans for online games target Lineage 2), World of Warcraft (20%), Gamania, Tibia and Legend of Mir (about 6% each). These indirectly reflect the popularity of each online game for which malicious users design password-stealing programs.
Below is a chart illustrating the statistics of new malware for the most popular online games in 2006: Lineage 2 and World of Warcraft.
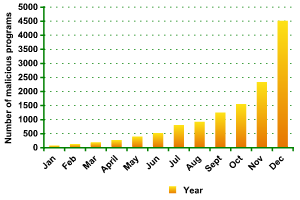
Malicious programs targeting Lineage 2 and World of Warcraft passwords, 2006
The worlds of these online games have been open to players since 2004. However, as they became more popular, they have increasingly attracted the attention of cyber criminals. In 2006, the monthly number of Trojans for Lineage 2 and World of Warcraft rocketed and at year-end accounted for 70% of all malicious programs targeting online games.
Conclusion
The number of online games is constantly growing, and the army of players is regularly swelled by new recruits. There are malicious programs designed to steal passwords from user accounts in almost all MMORPGs. If there isn’t a malicious program for a certain online game, it just means players aren’t yet ready to pay real money for virtual property.
The marked increase in the number of malicious programs for online games is explained not only by the trade economy of in-game valuables. It’s a lucrative business, and there is a lack of any real consequences for stealing passwords. The overwhelming majority of license agreements stipulate that all components of the game are the property of the developers. A player merely uses the services provided, including the account password. Consequently, he can only file a complaint about a stolen password to the administrator, not to a law enforcement body.
From a legal point of view, if a player’s virtual property is stolen, that theft is not a crime and malicious users cannot be held accountable for anything but spreading malicious programs or committing fraudulent acts.
Cyber criminals constantly have their sights set on the players of online games.
Game developers are attempting to protect their users from the actions of malicious users by introducing new authorization and authentication mechanisms, cryptographic protocols, all kinds of patches for game clients, even changes in the game’s item selection.
Antivirus companies are also trying to prevent the theft of online game passwords by promptly and regularly updating malware databases. They also add new heuristic and behavioral detections for malicious programs that target online game clients to their software on an ongoing basis.
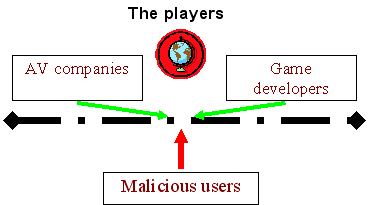
There is another effective method which can protect online game players: active collaboration with game developers and antivirus companies. In 2004, an agreement was signed between Kaspersky Lab and the developers of the Russian online game Fight Club. The agreement stated that any suspicious code found by administrators or players would be sent to Kaspersky Lab for analysis so that it could be identified and players protected against it. This turned out to be a productive agreement. Attempts to steal passwords from thousands of users were thwarted. If the attacks conducted by malicious users had been successful, the amount of (real) money they could have “earned” could have been in the tens of thousands of dollars at the very least.
What advice can we give players to prevent their passwords from being stolen? As always, take basic precautions, use common sense, don’t let yourself be led up the garden path, and last but not least, use the best antivirus available.
Online games and fraud: using games as bait





















Petro botes
What can you do to report a game that fixes there game to keep you from getting your ingame rewards (have screen shots to prove it)??
David
very nice thanks
steffan chang
Online gaming has been evolved so much that hackers and frauds are now targeting it for scams.
Thanks for raising this issue
we need more articles on it.