
The .co.cc domains, littered with malicious sub domains hosting exploit pages and malicious java applets for the past several months, are now hosting FakeAv pages and “BestAntivirus2011.exe”.
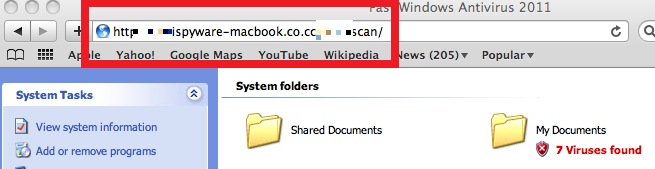
While the FakeAv rotation through .co.cc is not a shocker to security researchers at this point, one interesting domain popped out from the tens of thousands of .co.cc sub domain fakeav hits over the past day…”antispyware-macbook(dot)co(dot)cc”. This marketing quirk is odd, even for these guys. Does this domain suggest that another Apple based malware is in the works? Possibly. For now, I doubt it, because the Windows platform continues to be the dominant player, and this malware distributor seems to be very persistent at targeting the Windows platform. But it is very odd that this group is marketing “Fast Windows Antivirus 2011” from “macbook” domains.
Whatever group is using these domains, they have been very successful at conning large advertising networks into hosting their banner ads that redirect to these .co.cc sites. What they develop next is anyone’s guess. Here is a non-exhaustive list of the terms used in sub domains currently peddling the “Bestantivirus2011.exe” from these free and incredibly cheap .co.cc hosting domains over the past day or so. When users visit pages at these sites, they are presented with the usual “Your computer is infected!” scareware and “Windows Security has found on your system and will perform fast scan of system files” scam:
antispyware-companies
antispyware-shqip
antispyware-sw
antispyware-review
antispyware-trends
antispyware-sdk
antispyware-sweep
antispyware-programmer
antispyware-information
antispyware-sdat
antispyware-palsu
antispyware-ansav
antispyware-rogue
antispyware-advanced
antispyware-antivir
antispyware-trend
antispyware-sentry
antispyware-sales
antispyware-troyano
antispyware-seller
antispyware-ranking
antispyware-gpl
antispyware-priority
antispyware-com
antispyware-market
antispyware-telefon
antispyware-keys
The pages are currently detected as “Hoax.HTML.Fakeantivirus.y”, but the variants have been changing frequently over the past few months. It does not seem that these pages are related to “Lizamoon” (although they could be some cross-over), as there are rumors that the affiliate program is already shut down. The FakeAv referenced here is actively distributed at the moment. Researchers may notice the dropped component passed the Harry Potter reference “BOMBARDAMAXIMUM” as a cmd line argument.






















Odd FakeAv Marketing