
Spammers were out in force for the USA’s Independence Day, celebrating the country’s diversity in all its glory, and illustrating Jefferson’s thesis that “all men…are endowed…with certain unalienable rights…Life, Liberty, and the pursuit of Happiness”.
First up was spam confirming the predictions of some security companies predicted that cybercriminals would celebrate the holiday with a spam run spreading Waledac (which we detect as Iksmas). What could be more life-affirming than a firework display? Unfortunately, the spam containing links to a fake YouTube video of the 4th July fireworks also pushed malware onto victim machines.
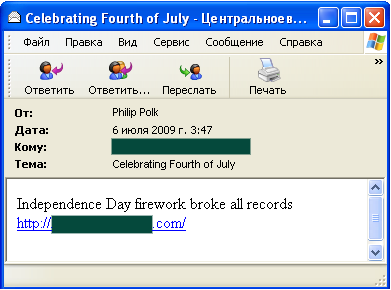
Next, the spammers exhorted recipients to celebrate freedom of choice by paying big bucks to a diploma mill:

And finally, why not pursue happiness by buying drugs online? This message linked to sites selling Xanax, Valium, Oxycontin and other prescription medications.
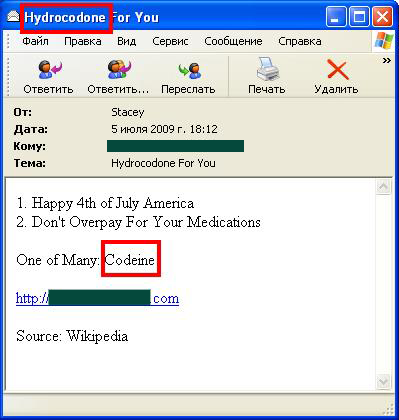
While you might get a temporary buzz (assuming the products are genuine) you may also find yourself with a nice little drug habit.
What price independence now?

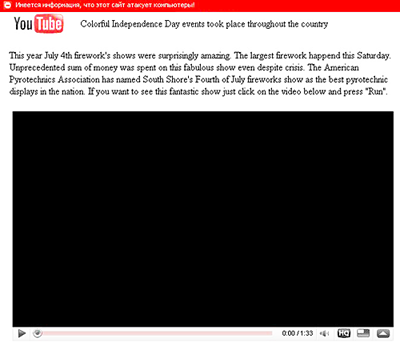





















No cause for celebration