
This week my Samsung Chromebook finally arrived. My interest in this platform had been especially piqued after my colleague Costin Raiu’s excellent analysis following the Chromebook’s introduction.
Google claims Chromebooks are so secure they don’t need anti-malware. Such a statement obviously got me interested in the system’s defenses.
Imagine my surprise when I was confronted with the following:
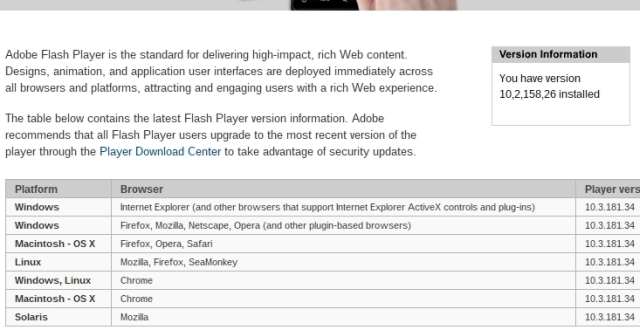
My fully updated Chromebook is running an outdated version of Flash and there’s no way to update it. To make sure this wasn’t an error, I triple checked if the system was really up to date.
This doesn’t bode well for Google’s security boast. ChromeOS is supposed to be all about being able to trust Google to take care of security for you.
Google has gone through great lengths to secure ChromeOS itself, but security doesn’t stop there. A platform needs to be properly managed if it intends on being and staying secure.
When it comes to managing the security aspect of the Android platform, Google is having some very serious problems. But Android is not marketed as being truly secure.
With ChromeOS/Chromebook there are no excuses, especially when Chrome has been receiving updates for Flash early.
Google will need to step up if it wants to turn ChromeOS into a successful platform.
We’ve reached out to Google to inform them about this issue.
UPDATE: It turns out Google’s ChromeOS is running a special version of Flash. This version of Flash did have all relevant security patches.




















New Chromebook, Old Flash Player