
April in figures
The following statistics were compiled in April using data collected from computers running Kaspersky Lab products:
- 280 million malicious programs were detected and neutralized;
- 134 million (48% of all threats) web-borne infections were prevented;
- More than 24 million malicious URLs were detected.
Cyber-Threats & Hot Topics:
Mac OS X: Mass-Exploitation and APT
The unusually high activity we witnessed in March in terms of malware for Mac OS X was just the tip of the iceberg. Two stories in April have forever changed the way we view the Mac OS X security landscape: one focusing on mass-exploitation and one using Mac OS X as part of an APT.
Flashfake
Let?s start with the Flashfake botnet, also known as Flashback. The Flashfake family of malware was first detected in 2011 as Trojan-Downloader.OSX.Flashfake. It was being distributed as a fake Flash Player update, which explains the origin of the malware’s name. From September 2011 to February 2012, Flashfake was distributed using social engineering only: visitors to various websites were asked to download a fake Adobe Flash Player update.
In March’s monthly malware report we noted that hundreds of thousands of hacked WordPress blogs were being used as a new distribution method for this malware. This escalated the issue dramatically since the Flashfake malware was using exploits to infect victims’ computers, resulting in the creation of the Flashfake botnet, which was comprised of more than 750,000 Mac OS X machines.
The cybercriminal gang distributing Flashfake was able to spread the malware via WordPress by hiring the traffic from the WordPress blogs using a partner program offered by the rr.nu cybercriminal gang. About 85% of the hacked blogs were based in the U.S. and the use of the WordPress traffic enables the Flashfake gang to redirect visitors visiting WordPress sites to the hacked sites controlled by the attackers. Once a victim visited the hacked site, three different exploits attempted to infect the visitors’ computer: CVE 2011-3544, CVE 2008-5353 and CVE 2012-0507, or the site would try to fool the user into downloading and installing a JAR file with a fake signature from Apple. If one of the exploits ran successfully, the target machine was infected without any need for additional user interaction. The signed JAR would only work if the user accepts the installation. You can find more technical details on the installation process and behavior of Flashfake here.
However, the key to the success of this campaign was not only the new distribution method but the exploits used. It is interesting to see how all of them targeted Java, where the implementation and distribution of security patches for Mac OS X was done by Apple instead of being done directly by Oracle, which resulted in delays for security patches to Mac OS X end users. For example, the CVE 2012-0507 vulnerability was patched by Oracle for all other platforms on 14 February, but Apple didn’t distribute its own until 3 April, leaving Mac OS X users exposed for a long time. Java is not installed on Lion by default, though any user can choose to install it. Finally, when the patch was released, it was only available for Lion and Snow Leopard users.
As a result of this, more than 700,000 users were infected with Flashfake, 58% of them from the U.S. Kaspersky set up a verification site, Flashbackcheck.com, which allowed users to check if their computers were infected and download a free disinfection tool to remove the malware.
- The anatomy of Flashfake. Part 1
- Flashfake Mac OS X botnet confirmed
- Flashfake Removal Tool and online-checking site
- OS X Mass Exploitation – Why Now?
SabPub: New Advanced Persistent Threat (APT)
In April an active APT, SabPub, was identified that used two types of backdoor Trojans to infect users’ computers. The first Trojan used an exploit in Microsoft Word to gain entry and was created in February 2012. The second variant of SabPub, which was created in March 2012, was attacking the Mac OS X platform by exploiting a Java vulnerability. Once the custom backdoor Trojan infected a victim’s machine, it was able to take screenshots of the user’s current session and execute commands on the infected computer. To date the group behind SabPub is still actively targeting users’ computers.
New Spam Campaigns Using BlackHole Exploit Kits
Active Twitter Spam Campaign
Kaspersky Lab discovered a new ongoing spam campaign on Twitter that compromised more than 500 accounts. The spam campaign was sending embedded links to users that redirected them to malicious sites hosting the BlackHole Exploit Kit. The sites installed scareware on victims’ computers in the form of fake antivirus notifications, which prompted the user to scan their system for infection. Kaspersky Lab customers were protected from the outset of the campaign, with the threats being detected as: Trojan-FakeAV.Win32.Agent.dqs and Trojan-FakeAV.Win32.Romeo.dv.
US Airways phishing emails
In early April Kaspersky Lab reported an email phishing campaign that began at the end of March, where people were receiving fake US Airways emails. Cybercriminals sent the phishing emails in an attempt to trick people into clicking on embedded links inside the messages that offered “online reservation details,” including flight check-in options. If users clicked on any of the links, they were taken to a fake website containing a BlackHole Exploit Kit with an advanced form of Zeus malware (GameOver). The banking malware installs itself on the user’s computer and steals their banking credentials. These spam messages were sent out in mass quantities, with the cybercriminals banking on some people having flights booked with US Airways (increasing the chances they would click on the links).
Mobile malware
Android users in Japan under attack
At the moment, the vast majority of Android malware is specific to geographic regions with cybercriminals in different countries creating various types of malware to target users in specific countries. In other words, the probability of an Android user from Russia being infected by Chinese malware is very low. However, it doesn’t mean that the number of infections — and profits — generated by hackers isn’t growing.
Japan is no exception to region-specific mobile malware – and we are starting to see it become more active. In the beginning of April a new type of Android malware was discovered, which was written by Japanese mobile virus writers targeting Android devices in Japan. The malware is detected by Kaspersky Lab as Trojan.AndroidOS.FakeTimer.
Unfortunately, almost 30 different malicious apps were available on Google Play and at least 70,000 users have downloaded one of them. This particular piece of malware is able to connect to a remote server. If the connection is successful, it downloads an MP4 video file. It is also capable of stealing sensitive information from an infected device, including contact names, email addresses and phone numbers of people from a victim’s contact list. The malware uploads the stolen data to a remote server.
TigerBot – yet another SMS bot
Mobile malware which is controlled via SMS messages is gaining more and more popularity. In April, another backdoor named TigerBot was discovered. This piece of malware masks itself after the infection and doesn’t show any kind of existence on the home screen of the device. If the victim checks the running processes list on their mobile device, they may not identify TigerBot’s process name, like ‘System,’ either. The malware registers a receiver called “android.provider.Telephony.SMS_RECEIVED” in order to tap all incoming SMS messages and check whether they have a special command or not.
Various commands may lead to the recording of phone calls, stealing of GPS coordinates, sending of SMS messages or changes to network setup. All these features may cause serious information leakage. The malware can also reboot infected phones, although this is less likely to happen because it will alert the victim to a problem with the device.
Fortunately, there was no evidence that TigerBot was (or is) available in Google Play, but it’s still important to be careful when installing any applications from any source.
Kaspersky Mobile Security detects this threat as Backdoor.AndroidOS.TigerBot.
April Ratings
*These statistics represent detected verdicts of antivirus modules and were submitted by users of Kaspersky Lab products who consented to share their local data.
Web Threats
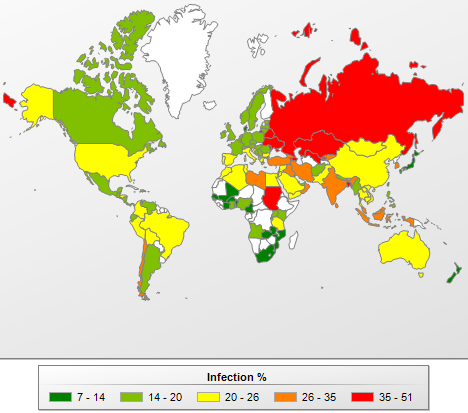
Map of infection risk while surfing the Internet
Source of web attacks by domain zone*
*Number of attacks from web resources according to domain detected by the web antivirus module.
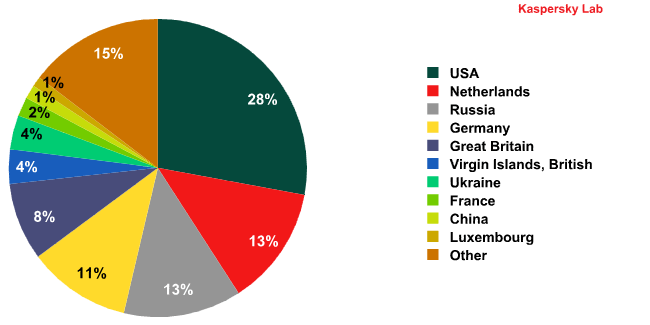
Top 10 countries where web resources were seeded with malware
(Global distribution of infected sites and malware hosts)
Top 10 threats on the Internet
| TOP 10 WAV March | % of all attacks* | Change in ranking | |
| 1 | Malicious URL | 87,6% | 0 |
| 2 | Trojan.Script.Iframer | 2,9% | 0 |
| 3 | Trojan.Script.Generic | 2,4% | 0 |
| 4 | Trojan.JS.Popupper.aw | 0,4% | 4 |
| 5 | Trojan.Win32.Generic | 0,3% | -1 |
| 6 | Trojan.JS.Agent.bxw | 0,3% | new |
| 7 | Exploit.Script.Blocker | 0,3% | new |
| 8 | Trojan-Downloader.Win32.Generic | 0,2% | new |
| 9 | Trojan-Downloader.Script.Generic | 0,2% | -4 |
| 10 | Trojan.JS.Redirector.ux | 0,2% | new |
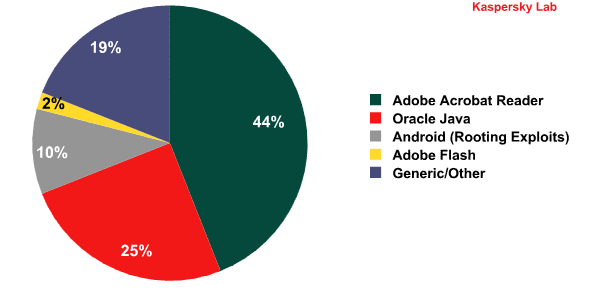
Exploits detected by the web antivirus module on users’ computers by targeted application
* Percentage of all blocked web-borne exploit attacks
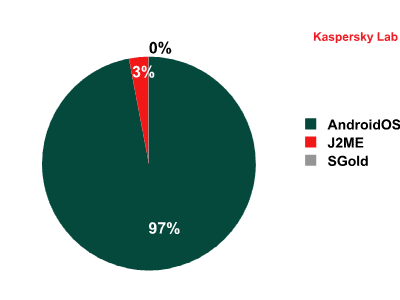
New mobile malware modifications found, April 2012
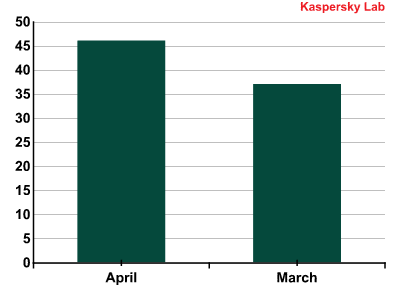
The number of new signatures for Mac OS X threats, March-April 2012
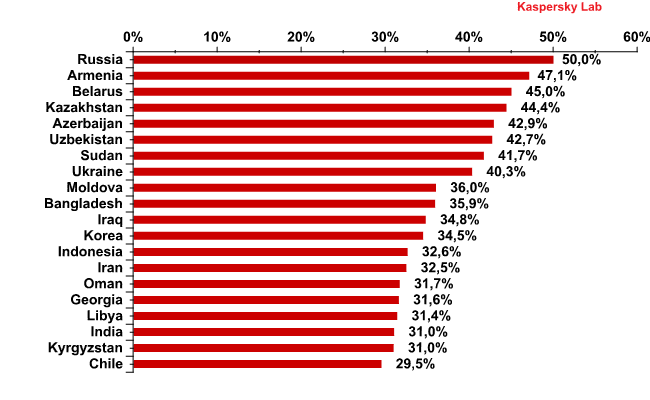
The 20 countries where users face the greatest risk of infection via the Internet
| Country | % * | Change in ranking | |
| 1 | Russian Federation | 50 | – |
| 2 | Armenia | 47,1 | – |
| 3 | Belarus | 45 | 1 |
| 4 | Kazakhstan | 44,4 | -1 |
| 5 | Azerbaijan | 42,9 | – |
| 6 | Uzbekistan | 42,7 | 2 |
| 7 | Sudan | 41,7 | – |
| 8 | Ukraine | 40,3 | -2 |
| 9 | Moldova, Republic Of | 36 | new |
| 10 | Bangladesh | 35,9 | – |
The 10 countries where users face the least risk of infection via the Internet
| Country | % * | Change in ranking | |
| 1 | Burkina Faso | 6,8238 | 5 |
| 2 | Mali | 6,8483 | new |
| 3 | Benin | 7,8883 | -1 |
| 4 | Japan | 8,1372 | -1 |
| 5 | Taiwan | 9,577 | -4 |
| 6 | Luxembourg | 10,2856 | new |
| 7 | Denmark | 11,1927 | 4 |
| 8 | South Africa | 11,7979 | new |
| 9 | Senegal | 11,9672 | new |
| 10 | Cote D’Ivoire | 11,979 | new |
When calculating, we excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
*The percentage of unique users in the country with computers running Kaspersky Lab products that blocked online threats.




















Monthly Malware Statistics: April 2012