
This app can track Gmail, WhatsApp, Instagram, and Facebook user activity. What comes next? Telegram and Threema?
Updated March 17th, 2020
The other day, our Android traps ensnared an interesting specimen of commercial software that is positioned as a parental control app, but may also be used to secretly monitor family members or colleagues – or, in other words, for stalking. Such apps are often called stalkerware. On closer inspection, we found that this app outstrips all existing software of its class in terms of functionality. Let’s take a look one step at a time.
Modern stalkerware
What is the usual functionality of stalkerware? The most basic thing is to transmit the victim’s current geolocation. There are many such “stalkers”, since various special web resources are used to display coordinates, and they only contain a few lines of code.
Often, their creators use geofencing technology, whereby a notification about the victim’s movements is sent only if they go beyond (or enter) a particular area. In some cases, functions to intercept SMS and call data (spyware that’s able to log them is much less common) are added to the geolocation transmission.
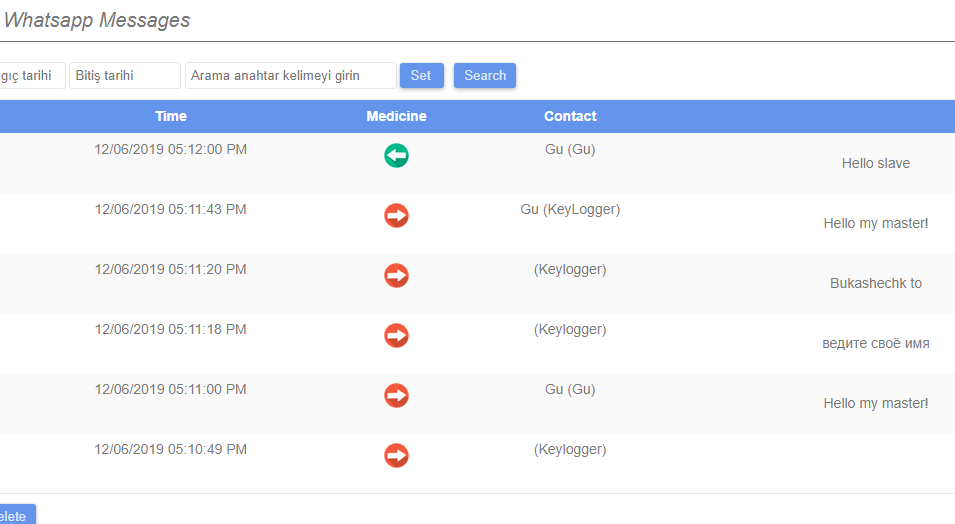
But today, SMS are used mainly for receiving one-time passwords and not much else — their niche has been captured almost entirely by messengers, which these days even facilitate business negotiations. Moreover, they claim to be an alternative to “traditional” voice communication. So any software with tracking/spying functionality worth its salt must be able to intercept data from messengers. The sample we found (assigned the verdict Monitor.AndroidOS.MonitorMinor.c) is a rare piece of monitoring software that could be used for stalking purposes that can do this.
MonitorMinor features
In a “clean” Android operating system, direct communication between apps is prevented by the sandbox, so stalkerware cannot simply turn up and gain access to, say, WhatsApp messages. This access model is called DAC (Discretionary Access Control). When an app is installed on the system, a new account and app directory are created, the latter being accessible only to this account. For example, WhatsApp stores the user’s chat history in the file /data/data/com.whatsapp/databases/msgstore.db, which only the user and WhatsApp itself have access to. Other messengers work in a similar way.
The situation changes if a SuperUser-type app (SU utility) is installed, which grants root access to the system. Exactly how they get on the device — installed at the factory, by a user, or even by malware — is not so important. The main point is that they cause one of the system’s key security mechanisms to cease to exist (in fact, all security systems cease to exist, but it is DAC that we are interested in right now).
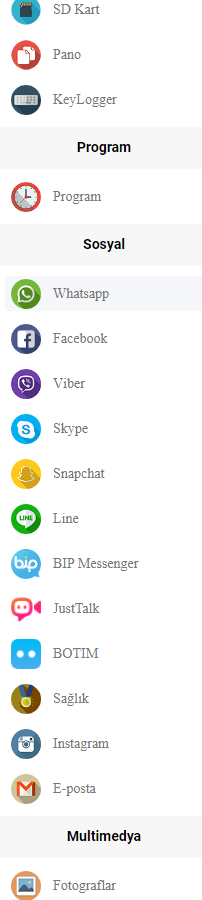
It is the presence of this utility that the creators of MonitorMinor are perhaps counting on. By escalating privileges (running the SU utility), it gains full access to data in the following apps:
- LINE: Free Calls & Messages
- Gmail
- Zalo – Video Call
- Kik
- Hangouts
- Viber
- Hike News & Content
- Skype
- Snapchat
- JusTalk
- BOTIM
In other words, all the most popular modern communication tools.
Intercepting the device unlock code
MonitorMinor’s functionality is not limited to intercepting data from social networking apps and messengers: using root privileges, it extracts the file /data/system/gesture.key from the device, which contains the hash sum for the screen unlock pattern or the password. This lets the MonitorMinor operator unlock the device, when it’s nearby or when the operator will have physical access to the device the next time. This is the first time we have registered such a function in all our experience of monitoring mobile platform threats.
Persistence
When MonitorMinor acquires root access, it remounts the system partition from read-only to read/write mode, then copies itself to it, deletes itself from the user partition, and remounts it back to read-only mode. After this “castling” move, the application cannot be removed using regular OS tools. Sure, the option to escalate privileges is not available on all devices, and without root one might assume that the software would be less effective. But not if it’s MonitorMinor.
MonitorMinor features without root
Android is a very user-friendly operating system. It is especially friendly to users with disabilities: with the Accessibility Services API, the phone can read aloud incoming messages and any other text in app windows. What’s more, with the help of Accessibility Services, it is possible to obtain in real time the structure of the app window currently displayed on the smartphone screen: input fields, buttons, their names, etc.
It is this API that the stalkerware uses to intercept events in the above-listed apps. Put simply, even without root, MonitorMinor is able to operate effectively on all devices with Accessibility Services (which means most of them).
A keylogger function is also implemented in this app through this same API. That is, MonitorMinor’s reach is not limited to social networks and messengers: everything entered by the victim is automatically sent to the MonitorMinor servers. The app also monitors the clipboard and forwards the contents. The app also allows its owner to:
- Control the device using SMS commands
- View real-time video from the device’s cameras
- Record sound from the device’s microphone
- View browsing history in Chrome
- View usage statistics for certain apps
- View the contents of the device’s internal storage
- View the contacts list
- View the system log
Propagation
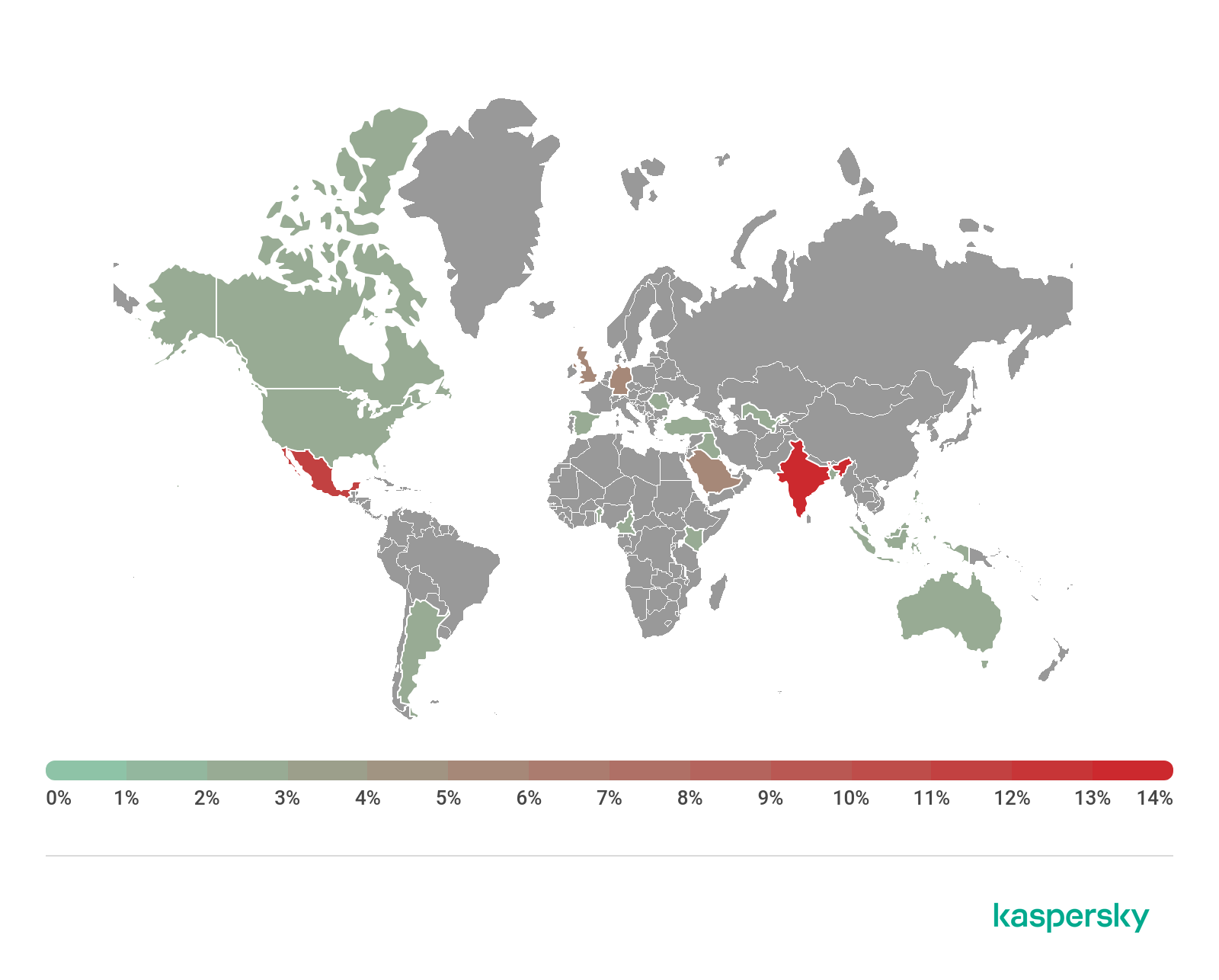
According to KSN statistics, India currently has the largest share of installations of this application (14.71%). In addition, a Gmail account with an Indian name is stitched into the body of MonitorMinor, which hints at its country of origin. That said, we also discovered control panels in Turkish and English.
The second country in terms of usage is Mexico (11.76%), followed by Germany, Saudi Arabia, and the UK (5.88%), separated by only a few thousandths of one percent.
Conclusion
MonitorMinor is superior to other tracking apps that can be used for stalking purposes in many aspects. It implements all kinds of tracking features, some of which are unique and is almost impossible to detect on the victim’s device. If the device has root access, its operator has even more options available. For example, they can retrospectively view what the victim has been doing on social networks. Note too that the Monitor.AndroidOS.MonitorMinor.c is obfuscated, which means that its creators may be aware of the existence of anti-stalkerware tools and try to counter them.
Yet we should note that the License agreement available on the website, from which the application is distributed, clearly states that users of the application are not allowed to use it for silent monitoring of another person without written consent. Moreover, the authors of the agreement warn that in some countries such actions may be subject to investigation by law enforcement agencies. So, formally, it is hard to deny that the developers of this application took steps to provide information about the potential consequences of unlawful usage of the app.
On the other hand, we can’t see how this information can help potential targets of stalkers that would decide to use this app. It is very intrusive and is able to exist on the target’s device without being visible to its owner, and it can silently harvest practically every bit of the target’s personal communications. Due to the powerful characteristics of this app, we decided to draw attention to it and inform those who defend people from stalkerware of the potential threat it poses. This is not just another parental control application.
The market has plenty of Parental Control solutions that do their job properly without providing the “Parent” with a super set of instruments to track their “kids'” personal life. We are not in the position to teach other developers how to create parental control applications, however, it is our job to let our clients and other parties know when there is something out there that could be used to significantly impede on their privacy.
IOCs
ECAC763FEFF38144E2834C43DE813216
MonitorMinor: vicious stalkerware?



















Tulley
I have reason to believe this is on my Android