
The year in figures
In 2017, Kaspersky Lab detected the following:
- 5,730,916 malicious installation packages
- 94,368 mobile banking Trojans
- 544,107 mobile ransomware Trojans
Trends of the year
Rooting malware: no surrender
For the last few years, rooting malware has been the biggest threat to Android users. These Trojans are difficult to detect, boast an array of capabilities, and have been very popular among cybercriminals. Their main goal is to show victims as many ads as possible and to silently install and launch the apps that are advertised. In some cases, the aggressive display of pop-up ads and delays in executing user commands can render a device unusable.
Rooting malware usually tries to gain super-user rights by exploiting system vulnerabilities that allow it to do almost anything. It installs modules in system folders, thus protecting them from removal. In some cases – Ztorg, for example – even resetting the device to factory settings won’t get rid of the malware. It’s worth noting that this Trojan was also distributed via the Google Play Store – we found almost 100 apps there infected by various Ztorg modifications. One of them had even been installed more than a million times (according to store statistics).
Another example is Trojan.AndroidOS.Dvmap.a. This Trojan uses root rights to inject its malicious code into the system runtime libraries. It was also distributed via the Google Play Store and has been downloaded more than 50,000 times.
The number of users attacked by rooting malware in 2017 decreased compared to the previous year. However, this threat is still among the most popular types of malware – almost half the Trojans in our Top 20 rating belong to families that can get root privileges. The decrease in their popularity among cybercriminals was most probably due a decline in the number of devices running older versions of Android – the malware’s main targets. According to Kaspersky Lab data, the percentage of users with devices running Android 5.0 or older declined from more than 85% in 2016 to 57% in 2017, while the proportion of Android 6.0 (or newer) users more than doubled – 21% in 2016 compared to 50% in 2017 (6% of users updated their devices during 2016, 7% – during 2017). Newer versions of Android don’t yet have common vulnerabilities that allow super-user rights to be gained, which is disrupting the activity of rooting malware.
But the decline in popularity doesn’t mean the developers have completely given up on these Trojans. There are some that continue to flood devices with ads, downloading and initializing installation of various apps, only now without exploiting vulnerabilities to obtain super-user rights. Moreover, they’re still difficult to remove thanks to a variety of system features, such as device administrator capabilities.
Of course, during the year, the attackers tried to modify or change the capabilities of their Trojans in order to preserve and increase profits. In particular, we discovered the Ztorg family using a new money-making scheme that involved sending paid text messages. Two of them, detected by Kaspersky Lab products as Trojan-SMS.AndroidOS.Ztorg.a, were downloaded from the Google Play Store tens of thousands of times. Moreover, we discovered additional modules for ‘standard’ Ztorg family Trojans that could not only send paid text messages but also steal money from a user’s account by clicking on sites with WAP subscriptions. To do this, the Trojans used a special JS file, downloaded from the criminals’ servers.
The return of the WAP clickers
It wasn’t just the creators of rooting malware that were attracted to WAP billing – in 2017, we discovered lots of new WAP Trojans. Although this behavior cannot be called new – Trojan-SMS.AndroidOS.Podec has been around since 2015 – 2017 was the year that saw a growth in the number of WAP clickers.
These Trojans generally work in the following way: they receive a list of links from the C&C, follow them (usually unnoticed by the user) and ‘click’ on page elements using a specially created JS file. In some cases, the malware visits regular advertising pages (i.e., they steal money from advertisers, rather than from the user); in other cases, they visit pages with WAP subscriptions, with the money being taken from the user’s mobile account.
A page with WAP billing usually redirects to a mobile operator page where the user confirms they agree to pay for the services. However, this doesn’t stop the Trojans – they are able to click these pages as well. They can even intercept and delete SMSs sent by mobile operators containing information about the service costs.
The dynamic development of mobile banking Trojans
Mobile bankers were also actively evolving throughout the whole of 2017, offering new ways to steal money. We discovered a modification of the FakeToken mobile banker that attacked not only financial apps but also apps for booking taxis, hotels, tickets, etc. The Trojan overlays the apps’ interfaces with its own phishing window where a user is asked to enter their bank card details. It’s worth noting that these actions appear quite normal to the user: the targeted apps are designed to make payments and are therefore likely to request this sort of data.
The latest versions of Android OS include lots of different tools designed to prevent malware from performing malicious actions. However, banking Trojans are constantly looking for ways to bypass these new restrictions, and in 2017 we saw some striking examples of this. In July, we discovered a new Trojan-Banker.AndroidOS.Svpeng.ae modification capable of granting itself the necessary permissions. The Trojan gets round these restrictions by using accessibility services – Android functions designed to create applications for users with disabilities. The Trojan asks the victim for permission to use accessibility services and grants itself some dynamic permissions that include the ability to send and receive SMSs, make calls, and read contacts. The Trojan also adds itself to the list of device administrators, thereby preventing uninstallation. It can also steal data that the user enters into other apps, i.e. operates as a keylogger.
In August, we came across yet another representative of the Svpeng mobile malware family that used accessibility services. This modification had a different goal – it blocked the device, encrypted the user’s files and demanded a ransom in bitcoins.
The rise and fall of mobile ransomware programs
The first half of 2017 was marked by a rapid growth in the number of new installation packages for mobile Trojan ransomware – in just six months we detected 1.6 times more files than in the whole of 2016. However, from June 2017, the statistics returned to normal. Interestingly, the growth was triggered by just one family – Ransom.AndroidOS.Congur. Over 83% of all installation packages for mobile Trojan ransomware detected in 2017 belonged to this family. Basically, this is extremely simple malware that changes (or sets) the PIN code on the device and asks the owner to contact the attackers via the QQ messenger.
Throughout the year mobile ransomware remained both simple and effective, with its capabilities and techniques almost unchanged: it overlaid all other windows with its own window, blocking the operation of the device. It should be noted that two popular mobile banking families – Svpeng and Faketoken – acquired modifications capable of encrypting user files, though in general encryptor functionality wasn’t that popular among mobile Trojans.
Statistics
In 2017, Kaspersky Lab detected 5,730,916 mobile malicious installation packages, which is almost 1.5 times fewer than in the previous year, although more than in any other year before and almost twice as much as in 2015.
Despite the decrease in the number of detected malicious installation packages, in 2017 we registered a growing number of mobile malware attacks – 42.7 million vs. 40 million in 2016.
The number of attacked users also continued to rise – from the beginning of January until the end of December 2017, Kaspersky Lab protected 4,909,900 unique users of Android devices, which is 1.2 times more than in 2016.
Geography of mobile threats
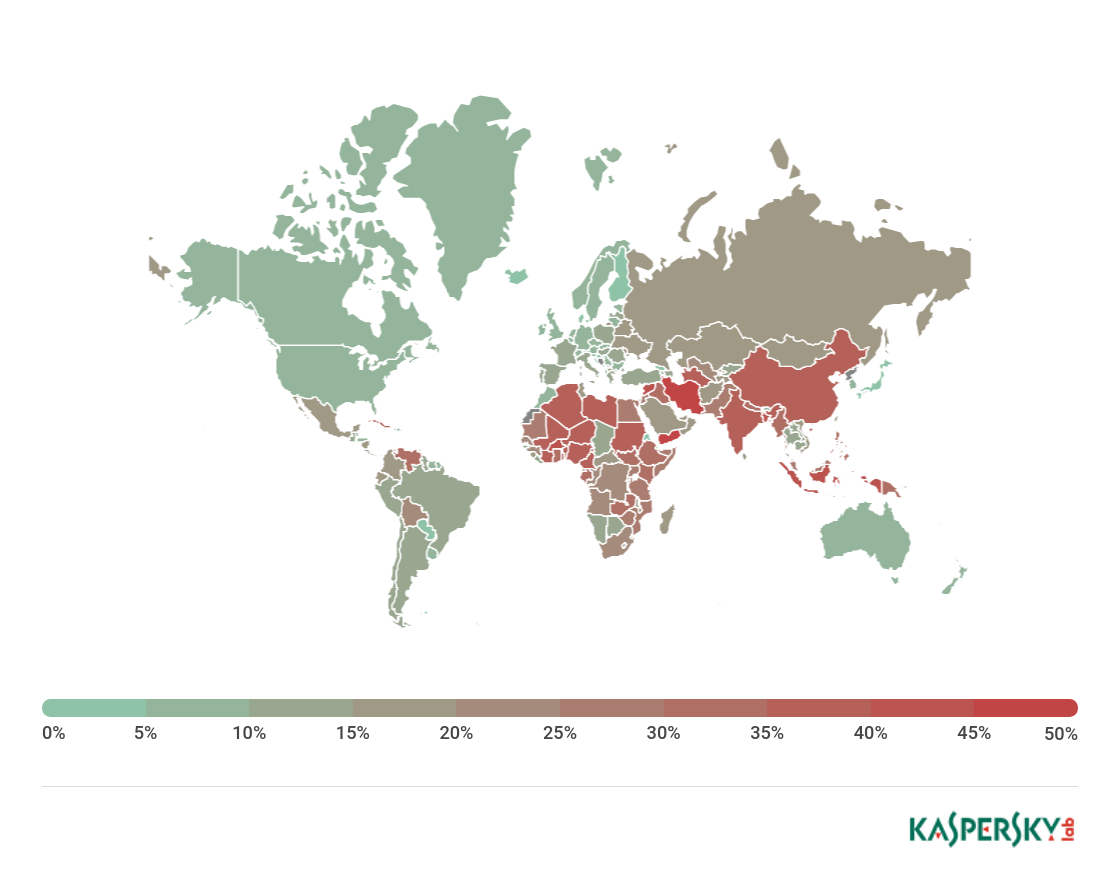
Attacks by malicious mobile software were registered in more than 230 countries and territories.
Top 10 countries attacked by mobile malware (by percentage of users attacked):
| Country* | %** | |
| 1 | Iran | 57.25 |
| 2 | Bangladesh | 42.76 |
| 3 | Indonesia | 41.14 |
| 4 | Algeria | 38.22 |
| 5 | Nigeria | 38.11 |
| 6 | China | 37.63 |
| 7 | Côte d’Ivoire | 37.12 |
| 8 | India | 36.42 |
| 9 | Nepal | 34.03 |
| 10 | Kenya | 33.20 |
* We excluded those countries in which the number of users of Kaspersky Lab’s mobile security products over the reporting period was less than 25,000.
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
Iran (57.25%), which was second in our Top 10 in 2016, came first after switching places with Bangladesh. In 2017, more than half of our mobile product users in Iran encountered mobile malware. The most widespread were advertising programs of the Ewind family, as well as Trojans of the Trojan.AndroidOS.Hiddapp family.
In second-placed Bangladesh (42.76%), users were most frequently attacked by adware, as well as by Trojan.AndroidOS.Agent.gp, a malicious program capable of stealing a user’s money by making calls to premium numbers.
In every country of this rating the most popular malicious programs were those monetized primarily through advertising. Notably, the most popular mobile malware in India (36.42%), which came eighth in the rating, was AdWare.AndroidOS.Agent.n. This malware can click on web pages, primarily advertising sites, without the user’s knowledge and earning money for ‘displaying’ adverts to the user. Other popular malware in India included Trojans from the Loapi families, which also earned money by clicking on web pages.
Types of mobile malware
In 2017, we decided to include a Trojan-Clicker category in this rating due to the active development and growing popularity of these types of malicious programs. Previously it belonged to the ‘Other’ category.
Most significantly, compared to the previous year, was the growth in detections of new Trojan-Ransom malware (+5.2 percentage points), which even outstripped the growth shown by RiskTool (+4.4 p.p.). To recap, RiskTool (47.7%) demonstrated the highest growth in 2016, with its share increasing by 24 p.p. during the year.
For the third year in a row, the percentage of Trojan-SMS installation packages declined, from 11% to 4.5%. As in 2016, this was the most considerable fall.
Trojan-Dropper malware, whose contribution grew throughout 2016, demonstrated a 2.8 p.p. decrease in the number of installation packages in 2017.
TOP 20 mobile malware programs
Please note that this rating of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or AdWare.
| Verdict | %* | |
| 1 | DangerousObject.Multi.Generic | 66.99% |
| 2 | Trojan.AndroidOS.Boogr.gsh | 10.63% |
| 3 | Trojan.AndroidOS.Hiddad.an | 4.36% |
| 4 | Trojan-Dropper.AndroidOS.Hqwar.i | 3.32% |
| 5 | Backdoor.AndroidOS.Ztorg.a | 2.50% |
| 6 | Backdoor.AndroidOS.Ztorg.c | 2.42% |
| 7 | Trojan.AndroidOS.Sivu.c | 2.35% |
| 8 | Trojan.AndroidOS.Hiddad.pac | 1.83% |
| 9 | Trojan.AndroidOS.Hiddad.v | 1.67% |
| 10 | Trojan-Dropper.AndroidOS.Agent.hb | 1.63% |
| 11 | Trojan.AndroidOS.Ztorg.ag | 1.58% |
| 12 | Trojan-Banker.AndroidOS.Svpeng.q | 1.55% |
| 13 | Trojan.AndroidOS.Hiddad.ax | 1.53% |
| 14 | Trojan.AndroidOS.Agent.gp | 1.49% |
| 15 | Trojan.AndroidOS.Loapi.b | 1.46% |
| 16 | Trojan.AndroidOS.Hiddapp.u | 1.39% |
| 17 | Trojan.AndroidOS.Agent.rx | 1.36% |
| 18 | Trojan.AndroidOS.Triada.dl | 1.33% |
| 19 | Trojan.AndroidOS.Iop.c | 1.31% |
| 20 | Trojan-Dropper.AndroidOS.Hqwar.gen | 1.29% |
* Percentage of users attacked by the malware in question, relative to all users of Kaspersky Lab’s mobile security product that were attacked.
As in previous years, first place was occupied by DangerousObject.Multi.Generic (66.99%), the verdict used for malicious programs that are detected using cloud technologies. These technologies are helpful when antivirus databases don’t yet include signatures or heuristics to detect a malicious program. This is basically how the very latest malware is detected.
Trojan.AndroidOS.Boogr.gsh (10.63%) came second. This verdict is given to files recognized as malicious by our system based on machine learning. In 2017, the most popular Trojans detected with this verdict were advertising Trojans and Trojan-Clickers.
Trojan.AndroidOS.Hiddad.an (4.36%) was third. It poses as a popular game or program and its main purpose is the aggressive display of adverts. Its main ‘audience’ is in Russia. Once launched, Trojan.AndroidOS.Hiddad.an downloads the application it imitates, and upon installation requests administrator rights to prevent its removal.
Occupying fourth was Trojan-Dropper.AndroidOS.Hqwar.i (3.32%), the verdict used for Trojans protected by a specific packer/obfuscator. In most cases, this name indicates representatives of the Asacub, FakeToken and Svpeng mobile banking families. Yet another verdict by which this packer is detected – Trojan-Dropper.AndroidOS.Hqwar.gen (1.29%) – was in 20th place.
Fifth and sixth were representatives of the Backdoor.AndroidOS.Ztorg family – advertising Trojans using super-user rights to install various applications and to prevent their removal. In 2016, a representative of this family climbed as high as second in our rating. It is worth noting that in 2017 the rating included 12 advertising Trojans – the same as in 2015, but less than in 2016.
Trojan-Dropper.AndroidOS.Agent.hb malware (1.63%) was 10th in the rating. This Trojan decrypts and runs another Trojan from the Loaipi family, which has a representative in fifth (Trojan.AndroidOS.Loapi.b). This is a complex modular malicious program whose functionality depends on the modules that it downloads from the attacker’s server. Our research has shown that their arsenal has modules for sending paid text messages, mining crypto currencies and clicking on sites with WAP subscriptions.
Trojan-Banker.AndroidOS.Svpeng.q, the most popular mobile banking Trojan in 2016, came 12th. Cybercriminals distributed it via the advertising network AdSense. This Trojan uses phishing windows to steal bank card data and also attacks SMS-banking systems.
In 14th place was Trojan.AndroidOS.Agent.gp, which steals money from users by making calls to premium numbers. It uses device administrator rights to prevent it from being removed.
Mobile banking Trojans
In 2017, we detected 94,368 installation packages for mobile banking Trojans, which is 1.3 times less than in the previous year.
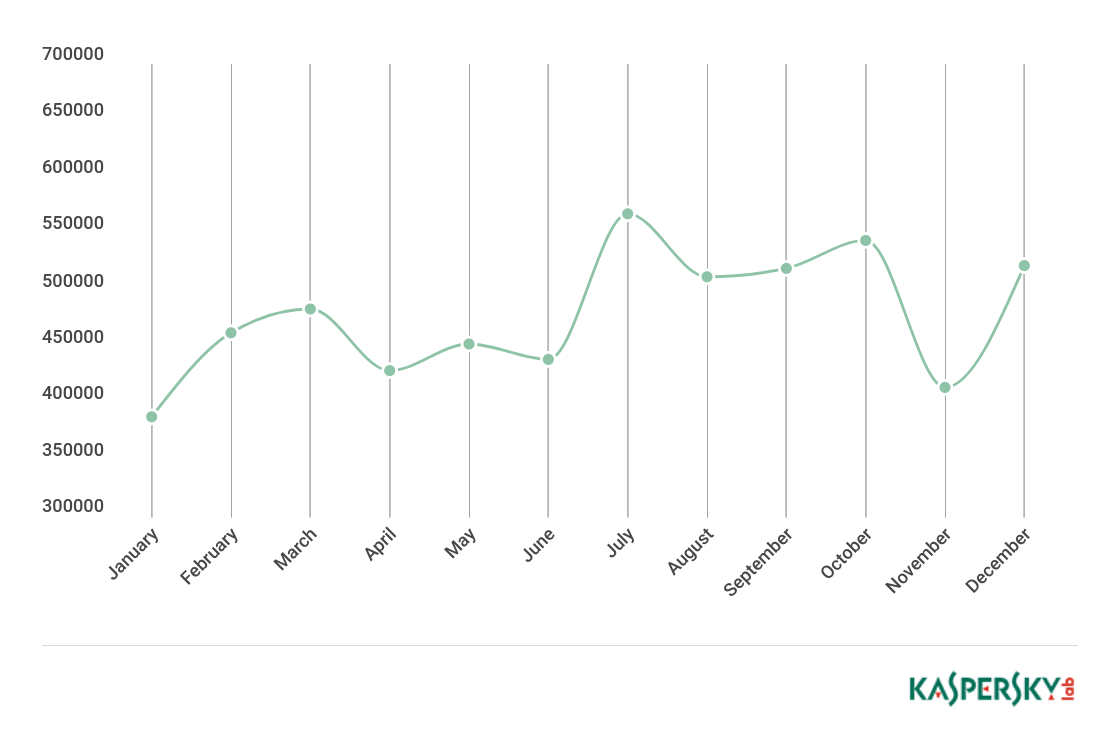
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab solutions in 2017
In 2017, mobile banking Trojans attacked 259,828 users in 164 countries.
Top 10 countries attacked by mobile banker Trojans (ranked by percentage of users attacked):
| Country* | %** | |
| 1 | Russia | 2.44 |
| 2 | Australia | 1.14 |
| 3 | Turkey | 1.01 |
| 4 | Uzbekistan | 0.95 |
| 5 | Kazakhstan | 0.68 |
| 6 | Tajikistan | 0.59 |
| 7 | Moldova | 0.56 |
| 8 | Ukraine | 0.52 |
| 9 | Latvia | 0.51 |
| 10 | Belarus | 0.40 |
* We excluded those countries in which the number of users of Kaspersky Lab’s mobile security products over the reporting period was less than 25,000.
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
The top 10 countries attacked by mobile banker Trojans in 2017 saw a slight change: South Korea and China left the rating while Turkey and Latvia took their place.
As in the previous year, Russia topped the ranking, with 2.44% of users in that country encountering mobile banking Trojans in 2017. The most popular families were Asacub, Svpeng and Faketoken.
In Australia (1.14%), representatives of the Acecard and Marcher mobile banking families were the most widespread threats. In third-placed Turkey the most active families of mobile bankers were Gugi and Asacub.
In the other countries of the Top 10, the Faketoken and Svpeng mobile banking families were the most widespread. In particular, a representative of the Svpeng family – Trojan-Banker.AndroidOS.Svpeng.q – became the most popular mobile banking Trojan for the second year in a row. It was encountered by almost 20% of all users attacked by mobile bankers in 2017. The most popular mobile banking family of 2017 was Asacub. Its representatives attacked almost every third user affected by mobile bankers.
Mobile ransomware
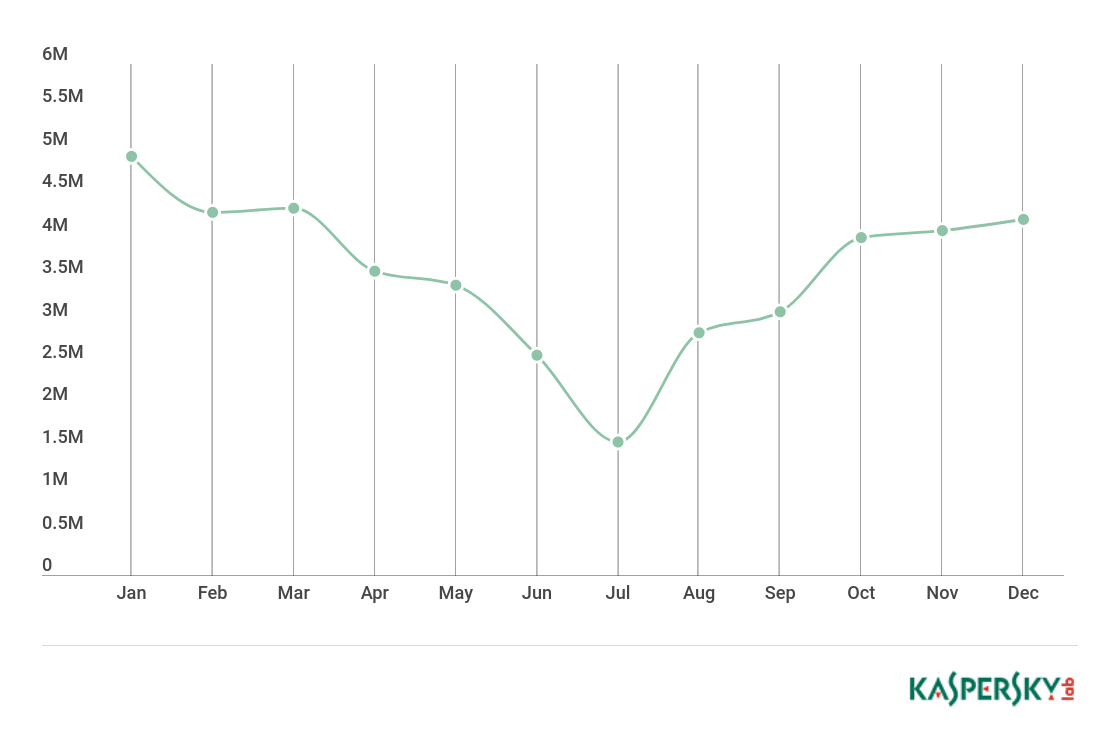
The number of detected mobile Trojan-Ransomware installation packages continued to grow in 2017. We discovered 544,107 packages, which was double the figure for 2016, and 17 times more than in 2015.
This growth was largely due to activity by the Trojan-Ransom.AndroidOS.Congur family. By Q4, the Congur family had ceased to actively generate new installation packages, which was immediately reflected in the statistics.

Number of mobile Trojan-Ransomware installation packages detected by Kaspersky Lab (Q1 2017 – Q4 2017)
Throughout 2017, Kaspersky Lab’s security products protected 110,184 users in 161 countries from mobile ransomware.
Top 10 countries attacked by mobile Trojan-Ransomware (ranked by percentage of users attacked):
| Country* | %** | |
| 1 | USA | 2.01 |
| 2 | Kazakhstan | 1.35 |
| 3 | Belgium | 0.98 |
| 4 | Italy | 0.98 |
| 5 | Korea | 0.76 |
| 6 | Poland | 0.75 |
| 7 | Canada | 0.71 |
| 8 | Mexico | 0.70 |
| 9 | Germany | 0.70 |
| 10 | Romania | 0.55 |
* We excluded those countries in which the number of users of Kaspersky Lab’s mobile security products over the reporting period was less than 25,000.
** Percentage of unique users attacked in each country by mobile Trojan-Ransomware, relative to all users of Kaspersky Lab’s mobile security product in the country.
The country attacked most by ransomware in 2017 was the US, where 2% of users encountered this threat. As in the previous year, when the US came second in the ranking, the most popular Trojan ransomware were representatives of the Trojan-Ransom.AndroidOS.Svpeng family. Then, Germany was in first place, though in 2017, a decrease in activity by the Trojan-Ransom.AndroidOS.Fusob family saw it (0.70%) drop to ninth in the rating. The Fusob family still remained the most active in Germany.
In Kazakhstan (1.35%), which came second, the most frequently used ransomware programs were various modifications of the Trojan-Ransom.AndroidOS.Small family. Fifth place in the rating was occupied by South Korea (0.76%), where most users were attacked by the Trojan-Ransom.AndroidOS.Congur family. In all the other countries of the Top 10, the Fusob and Zebt families were the most active.
Conclusion
For the last few years, advertising Trojans have been one of the main threats facing Android users. First, they are very widespread, accounting for more than half of the entries in our ratings. Secondly, they are dangerous, with many exploiting system vulnerabilities to gain root privileges. The Trojans can then get full control of a system and, for example, install their modules in system folders to prevent their removal. In some cases, even resetting the device to factory settings is not enough to get rid of the rooting malware.
However, the vulnerabilities that allow attackers to gain super-user rights are only found on older devices, and their share is declining. As a result, advertising Trojans are increasingly confronted with devices on which they cannot gain a foothold. This means the user has the chance to get rid of this malware once it starts aggressively displaying ads or installing new applications. This is probably why we are now seeing more and more advertising Trojans that don’t show ads to the user; instead, they click on them, helping their owners earn money from advertisers. The user may not even notice this behavior because the only telltale signs of infection are increased traffic and battery use.
Trojans that target WAP billing sites use similar techniques. They receive a list of links from the C&C, follow them and ‘click’ on page elements using a JS file received from the malicious server. The main difference is that they click not only advertising links but on WAP billing sites as well, which results in the theft of money from the user’s mobile account. This type of attack has been around for several years now, but it was only in 2017 that these Trojans appeared in significant numbers, and we assume this trend will continue in 2018.
In 2017, we discovered several modular Trojans that steal money via WAP billing as one of their monetization methods. Some of them also had modules for crypto-currency mining. The rise in price of crypto currency makes mining a more profitable business, although the performance of mobile devices is not that good. Mining results in rapid battery consumption, and in some cases even device failure. We also discovered several new Trojans posing as useful applications, but which were actually mining crypto currency on an infected device. If the rise of crypto currency continues in 2018, we’ll most probably see lots of new miners.
Mobile malware evolution 2017
































Anonymous
Google Play is so full of malware because Google does not care about anyone but themselves. Google’s shoddy Safe Browsing that supposedly keeps malicious apps off of Google Play fails every time.