
Letters about lottery wins are a standard trick used by “Nigerian” scammers. Very often, the author of such letters will explain that he is the happy winner of a multi-million lottery win, and he doesn’t know how to spend the unexpected windfall, and has decided to turn to philanthropy.
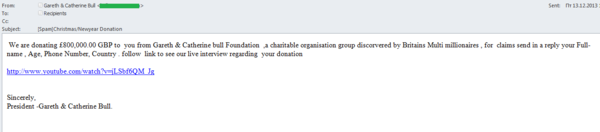
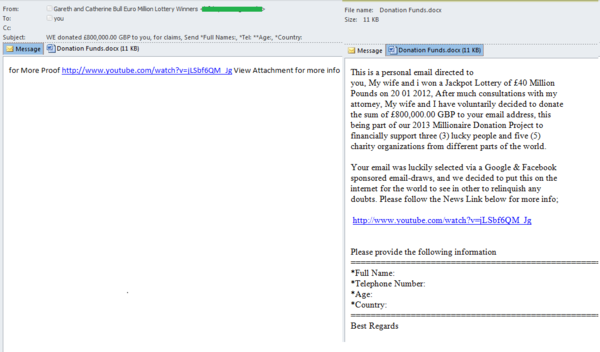
Over the last few months, we have detected several spam messages sent in the name of various people who had supposedly won a lottery within the last few years. For example, in December 2013 we received several messages sent in different spam mailings and sent in the name of the same couple who received their lottery win back in 2012. These letters had different designs and told various stories; however, all of them offered the identical sum of £800,000 to the potential victim, and gave the same link to a lottery winner interview video as a way of convincing the reader that the story was true. The scammers tried to be very brief and did not give any detailed information in the message body. However, messages in one of the mailings contained a text saying that the recipient’s email address was selected as a winner in a charity project along with two others.
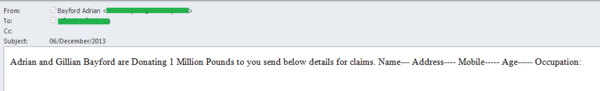
The scammers also used the names of a different couple who apparently won a lottery in November 2013, again to make their scam messages look authentic. This time, the scammers said the couple were making a donation of £1,000,000. There were no details in the letter as to how the reader could receive the money, or why the lottery winners decided to share the money with that particular recipient. To find out that information, the would-be victim had to reply to the scam message.
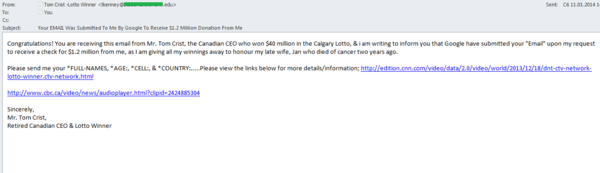
The scammers also used more recent cases. In mid-December 2013, an ordinary Canadian won $40,000,000 in a lottery; early January 2014, we detected a scam mailing in the name of the newly-minted millionaire. Unsurprisingly, the scammers attempted to entice the recipient by promising to give $1,200,000 and telling a story that the millionaire is now giving away his entire fortune in memory of his wife who died of cancer two years earlier.
To create new plots for their letters, the scammers use various real events, including both tragedies (celebrity deaths, terrorist attacks, natural disasters) and positive events like lottery wins. But no matter what the subject is of the scam messages, don’t ever believe that the senders will in fact share their money with you. Remember that references to real names and links to real publications in reputable media are no guarantee that you are being told the truth.
Millionaires Want to Share Their Money






















kevin flow
how do I find a Millionaires Want to Share Their with me?