
The use of all kind of services in a cloud basis is becoming more and more popular, enhancing productivity and reducing the needs of setting up a complex infrastructure. This approach is progressively being taken by IT industry. However, malware reacted faster in abusing this virtual infrastructure for its profit.
We have seen many examples in the past: the use of Twitter as a communication channel for a botnet, using Amazon EC2 for hosting C&Cs or abusing advertising channels for distributing malware. Today we will see, through a sample, how malware maximizes its revenues using this kind of services with a minimum impact on victims computer.
Our sample belongs to Trojan-Dropper.Win32.Drooptroop family, which has more than 7000 variants. The sample is detected by Kaspersky Internet Security as Trojan-Dropper.Win32.Drooptroop.jpa, and its peak of activity corresponds to 6th of December, mostly based in the US.
It is being distributed through an email message with a link to a Rapidshare file:
hxxp://rapidshare.com/files/4XXXXXXX0/gift.exe
Taking advantage of the Christmas campaign, the name of the binary is gift.exe. As suspicious as it is, however, most filters fail in detecting this as malicious for two reasons: the binary is not in the body message and the domain of the URL is legitimate. We have detected more than 1000 infections were technique was used for distributing the sample.
This is not the only use of external infrastructure done by the sample. Once the computer is infected,Drooptroop.jpa injects code into spoolsv.exe and intercepts browsers network functions, resulting in hijacking users requests.
Doing this, Drooptroop performs click fraud redirecting legitimate requests:
GET
/click.php?c=eNXXXXXSA HTTP/1.1
Host:
64.111.xxx.xxx
User-Agent:
Mozilla/5.0 (Windows; U; Windows NT 5.1; es-ES; rv:1.9.2.3) Gecko/20100401 Firefox/3.6.3
Accept:
text/html,applicationxhtml+xml,applicationxml;q=0.9,*/*;q=0.8
Accept-Language:
es-es,es;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding:
gzip,deflate
Accept-Charset:
ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive:
115
Connection:
keep-alive
Referer: hxxp://wwwxxx.com/go/beXXXX4
This remuneration programs are abused on a regular basis by malware. Apart from that, this malware redirects the user to rogue AV sites:
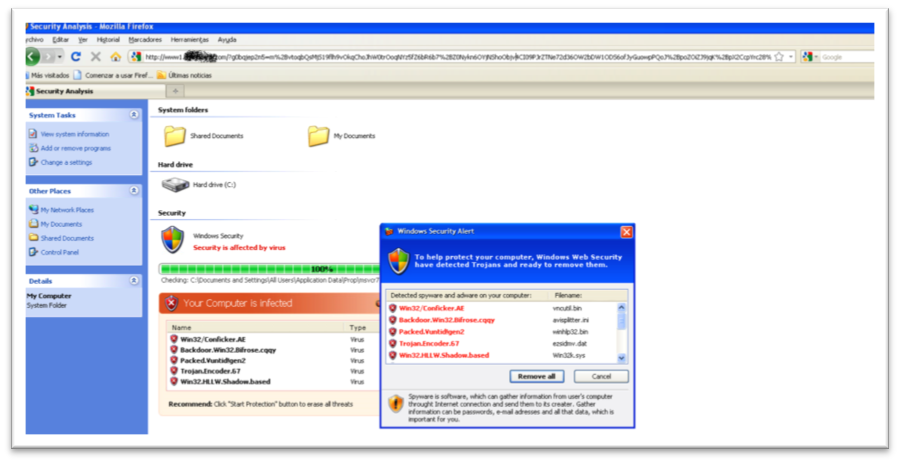
It is interesting how everything is shown in the browser. All is javascript highly obfuscated simulating explorer, so further binaries are downloaded to the computer at the scaring phase.
At this point, you probably want to run Kaspersky Internet Security to clean your system.
Summing it up, the distribution was using a remote file sharing service, the malware used click fraud to monetize and the rogue AV was all happening in the browser. However this malware still needed to infect your computer, so dont forget to protect yourself.





















Malware in the cloud