
Every day, we see more reports about malware in the Android Market. This time three developers known as MYOURNET, Kingmall2010, and we20090202, possibly the same person, were offering a number of Android apps for free download.
Many, if not all of the apps, were trojanized copies of legitimate apps from other developers.
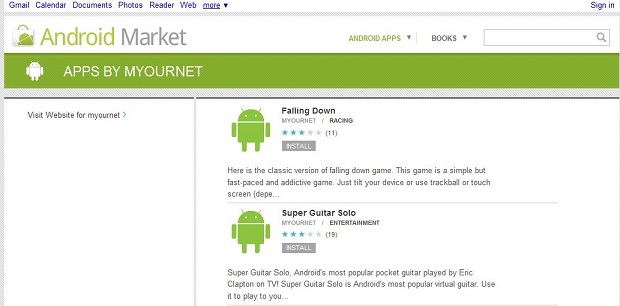
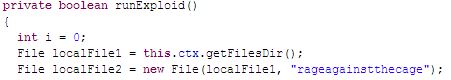
I downloaded one app in particular called Super Guitar Solo. Upon reviewing the app, I found it contains the popular “rage against the cage” root exploit commonly used to “root” Android phones and gain superuser privileges. As any Linux guru will tell you, once you have superuser rights, you have full, administrator level access to the phone’s operating system. In this case the exploit is launched without the owner’s consent.
So what is the purpose of this Trojan? The application will attempt to gather product ID, device type, language, country, and userID among other things, and then upload them to a remote server. Unlike most of the other samples seen so far, there is no attempt at sending or receiving premium rate SMS messages.
This discovery is important because up until now most of the Android malware has been found outside of the Android Market, which requires a number of special steps to be taken in order to infect the phones. In this case, users are even able to install from the web with the new Android Market format. We have previously talked about this here:
The Dark Side of the new Android Market
It’s also interesting to point out that, just as our researchers predicted last year, the cybercriminals have started taking advantage of jailbreaking tools as mentioned here:
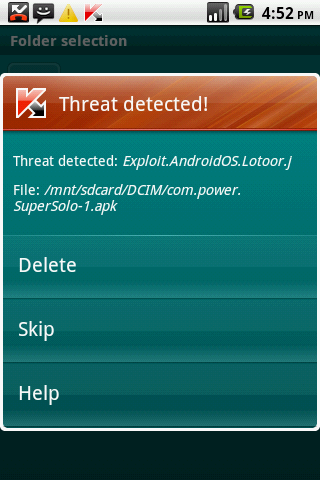
One of the important observations here is that it is likely that these are not the only live malware in the Android Market. Kaspersky recommends that you always check all the permission requests that an application is requesting at install time. This also highlights the dangers of jailbreaking or rooting your devices. This particular root exploit has been detected by Kaspersky as Exploit.AndroidOS.Lotoor.g and Exploit.AndroidOS.Lotoor.j since February 1st, so if you are a Kaspersky Mobile Security user, you are already protected.
Kaspersky will continue to examine this sample and update with any future information.
UPDATE: Google has now removed the malicious apps and the corresponding download page from the Android Market.




















Malware in the Android Market