
A new blog update from Google promises a response to deal with the outbreak of the so called “DroidDream” malware that went live on the Android Market last week:
Malware in the Android Market Part 1
Malware in the Android Market Part 2
According to the blog, Google will initiate its remote-removal process by pushing the installation of a new app called “Android Market Security Tool March 2011.” We’ve had a look at this app, and it does not fix the vulnerability, it simply removes the applications known to be malicious. Google further promises changes to the market to deal with this type of issue and claims to be “working with our partners to provide the fix for the underlying security issues.”
This part seems well and good with the exception of a few glaring issues:
The Google blog is confusing. In the blog Google states “the update will automatically undo the exploit.” However this does not make your phone any less vulnerable. On my first few readings I took this to mean that vulnerable phones were now protected from the exploits used in the DroidDream malware. This is not the case.
The implementation of the fix is incredibly curious; Google pushes an application to their users without user approval, the application launches without user consent (also known as remote code execution), the application then gains root privileges, removes other applications, and then deletes itself. Any of these steps could be acceptable if the user had any input whatsoever.
There is an inability to install security patches locally. Due to the nature of Android in its current state, it’s very difficult and expensive to push security updates as you would on a desktop operating system like Linux or Windows. Unlike iPhone, which installs patches via iTunes, or Windows Mobile which uses ActiveSync, Android works almost entirely via over the air (OTA) communication. This puts the burden on mobile service providers to push data updates to all their customers over their mobile data network. This is very expensive. If Android were able to install more granular patches, and if customers were able to install these through a desktop model, even optionally, this would go to great lengths to give both service providers, manufacturers, and customers the ability and initiative to install security updates more frequently.
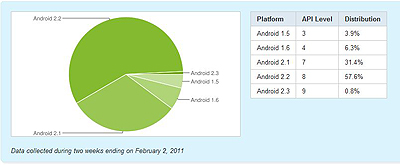
Also at issue is the fact that device manufacturers themselves do not consistently maintain or update their existing platforms. Read any mobile forum and you’ll find a host of users begging for an update to their respective devices. According to Google’s own statistics, over 40% of Android users are using a version of the operating system prior to Android 2.2. Even some of the customers running 2.2 are vulnerable as the exploit works on 2.2.1 or earlier. Unfortunately Google doesn’t break its statistics down small enough to see this number. With the small exception of the customers who receive the Android Market Security Tool update, every other person running 2.2.1 or less remains vulnerable. This means that they could get exploited right now.
Google promises changes to the Android Market, and those changes are yet to be seen. We can only hope that they will react to the larger goals of keeping all of their customers up to date and patching quickly while offering multiple ways to do so. Google and its partners have an opportunity as well as a responsibility here, let’s hope they make good on both.



















Malware in the Android Market part 3