
Yesterday several new pieces of malware were found in the Android Market by AegisLab. The first big outbreak of malicious software in the Android Market happened more than 2 months ago and there are some things in common between these cases:
- First of all, the March and May outbreaks were likely performed by Chinese hacker(s).
- Secondly, there were several pieces of malware in the official market in both cases.
The malware itself is not very interesting. It will send one SMS message to a Chinese number and after that it writes a marker “Y” in order to prevent further SMS sending.
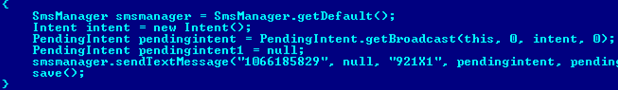
SMS sending routine
All of the malicious applications were published by the same developer named ‘zsone’. The malware was removed by Google from the Android Market immediately after its malicious nature was discovered. But there is some evidence that some of the applications developed by ‘zsone’ and identified as malicious were uploaded to the Android Market a long time ago.
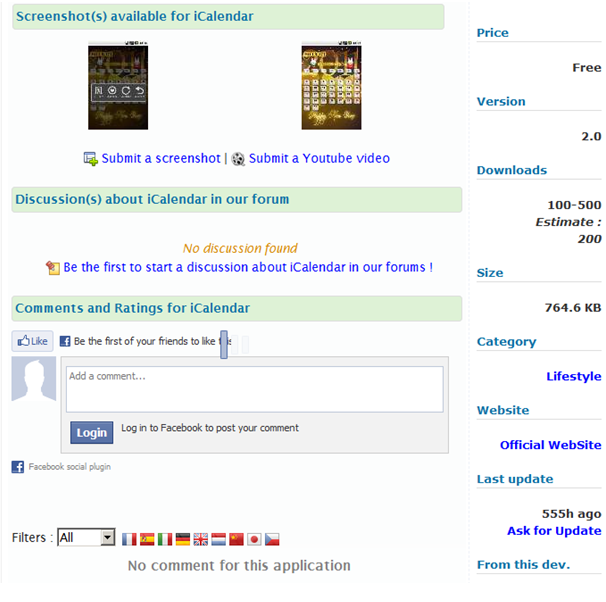
If you are searching on the web for applications for your Android device you can find some websites which ‘mirror’ the official Android Market. These websites provide various information about the application: developer, package name, system permissions, screenshots, price, version, number of downloads, last update, etc. According to one of these websites, the iCalendar application developed by ‘zsone’ was downloaded from the market ~200 times and last updated on the 19th of April:
Another application ‘3D Cube horror terrible’ created by the same developer was last updated even earlier: on the 27th of February.
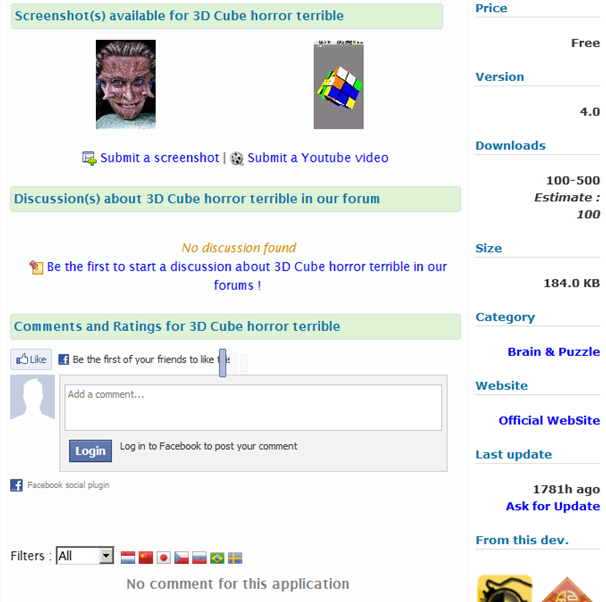
Does that mean that malware was alive in the market for at least 23 days? Or even more? Probably, yes. We checked a number of similar ‘mirroring’ websites and all of them showed the same dates of update and other information.
We detect this malware as Trojan-SMS.AndroidOS.Raden.a.






















Malware in the Android Market: here we go again