
Introduction
This article is a continuation of a previous piece of analysis on malware evolution in 2005, published earlier this year. This second part examines the evolution of the criminal underground and provides an analysis of the current situation, together with examples and statistical data.
This information is intended primarily for IT security professionals with an interest in malicious software.
Milestones in 2005
Escalating Confrontation
Undoubtedly, one of the strongest trends in 2005 was the escalation of confrontation, both between cybercriminals and the antivirus industry, but also amongst cybercriminals themselves. Moreover, in 2005, cybercriminals stepped up their attacks against governmental organizations; this indicates that they are no longer satisfied with the profits made from individual users.
How can this be explained? It’s been clear for a while that the time when cyberhooligans were lone ‘enthusiasts’ who spent nights diligently programming in assembly is long gone. Many estimate that the vast profits being made by cybercriminals are far greater than the revenues of the whole antivirus industry.
Cybercriminals are tracking the activity of the antivirus industry as closely as the antivirus industry is tracking cybercriminals. For example, they use multi-scanners (a collection of the file scanners used by leading antivirus vendors) to check new modifications of existing malicious programs against vendors’ antivirus databases. Malicious programs are released only if they cannot be detected by any of the antivirus solutions.
Criminals try to subvert almost every stage of antivirus update development. Figure 1 shows the update release process before the update is available to end users.
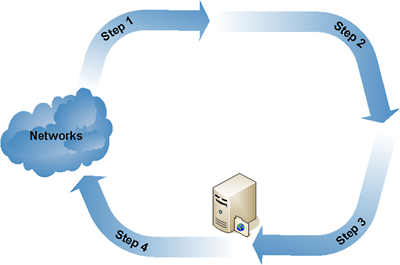 |
| Fig. 1: Update release process. |
- Stage 1: Suspicious content is intercepted in a network (any type of network e.g. the Internet, a mobile network etc.) Cybercriminals use a variety of methods to evade detection, such as identifying and avoiding network nodes which collect malicious content and conducting DDoS attacks on such nodes (this results in nodes being blocked for the duration of the attack). Targeting mass mailings of malicious programs also makes intercepting the malicious programs much more difficult. The authors of Bagle, a well-known email-worm, track users accessing the malicious links which lead to sites where the latest Bagle versions are located. Instead of having malicious files downloaded to their computers, users who frequently click the links are shown error messages. This type of denylisting is intended to obstruct antivirus companies and organizations which track network activity.
- Stage 2: Analysis of malicious code. There have been no new real developments in this area; the only real change is that polymorphic technologies are continuing to decrease in popularity. It is now more common for executable files to be packed with multiple packers (programs which compress executable files in such a way that the files can still be executed) which are not recognized by antivirus programs
- Stage 3: Update release. This is perhaps the only stage which cybercriminals so far have been unable to obstruct effectively.
- Stage 4: Installation of the update by the user. Virus writers commonly cause their programs to modify the hosts file in such a way that it is impossible for the victim machine to connect to the update servers of antivirus vendors. Consequently, this prevents the antivirus databases from being updated.
It should be stressed that once updates are released (stage 4) they are available both to end users and to cybercriminals. It is then clear to cybercriminals that their creations can now be detected; this in turn results in the release of new modifications of malicious programs.
Until recently, only a few groups of virus writers have behaved in the way described above. However, data from 2005 shows that existing groups are banding together, and new groups are emerging. This is a serious cause for concern.
Exactly why do cybercriminals combat the antivirus industry so intensively? The answer is obvious: they are fighting for their living, i.e. the money which they obtain in one way or another by infecting PCs. This is also the reason why 2005 saw increasing conflict between virus writers; another turn of the screw in the evolution of cyberwars.
Both groups and individuals within the criminal underworld fight each other in a variety of ways. They use malicious programs that destroy the software developed by rival groups, and include threats directed at each other, antivirus vendors, police and law enforcement agenices in their creations. One example of this is Net-Worm.Win32.Lebreat, which contains threats addressed to the authors of Bagle. Another fact that bears witness to the emerging confrontation is the battle for resources of infected computers. For example, in early November 2005 an attempt to hijack a botnet was detected. As a result of action taken by rival groups, a network of infected computers changed hands three times in one day. Criminals have realized that it is much simpler to obtain already infected resources than to maintain their own botnets, or to spend money on buying parts of botnets which are already in use.
It’s interesting to observe how cybercriminals communicate with each other on their forums. Flame wars break out as the virus writers try to pass off malicious programs and key generators and cracks. Sometimes they steal virtual property from each other by posting specially crafted messages; viewing such messages can lead to the user’s computer being infected. In other words, the weapons virus writers use against each other are those utilized to attack end users. Flame wars may develop into outright threats, DDoS attacks etc. Interestingly, the virus writers clearly understand the consequences of their actions, and openly discuss the merits of different antivirus solutions. They appear to forget that they are choosing protection against programs written by virus writers like themselves, and that the products they are using were actually developed expressly to protect users against their own creations.
However, criminals are no longer limiting themselves to attacking individuals. In comparison to 2004, in 2005 there were an increasing number of attacks against governmental organizations; these were conducted by criminals who clearly felt that they could act with impunity. There have been a large number of attacks against government-owned banks, e-trading portals, the military and other organizations. In modern times, when the economies of both developed and developing countries depend on information technology, the increase in such attacks naturally causes concern.
Governments are beginning to recognize the severity of the problem. But what can they do in the face of increased criminal activity? The year 2005 saw significant improvements in the response of law enforcement bodies in most developed countries to cybercrime. Here are a few of the most widely publicized cases:
- On August 26th, two authors of the Zotob (Bozori) worm were arrested (Farid Essebar, an 18-year-old Moroccan and Atilla Ekici, a 21-year-old Turk). The worm had caused the networks of ABC, CNN, The New York Times and other companies to crash. Less than two weeks passed from the appearance of the worm to the arrest of its authors.
- Two Nigerian scammers were sentenced to 37 years in jail for sending so-called 419 emails, or ‘Nigerian spam’
- Brazilian police arrested 85 people on charges of stealing tens of millions of US dollars. The criminals stole the money from the accounts of clients of financial organizations via the Internet.
Law enforcement agencies are hindered by the international nature of crimes committed by cybercriminals. It is increasingly common for criminals to live in one country and commit their crimes in another.
To conclude this section, it should be said that the efforts made by governmental agencies are clearly insufficient. The number of successful attacks against governmental (and other) cyber resources is increasing much more rapidly than the rate at which governments react.
Increased Response Speed
Since virus writers have started intensively targeting new users, the antivirus industry’s speed of response has become key. Unfortunately, most users (both total beginners and slightly more experienced users) fail to appreciate the gravity of the situation, as our poll (figure 2) shows:
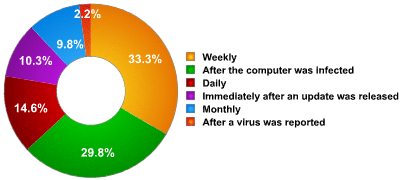 |
| Fig. 2: Distribution of users by update frequency, in % (based on an Internet poll) |
The poll results show that only 24% of users update their solution at least once a day. Given the rate at which new malicious programs appear (see figure 3), it’s easy to estimate the number of detections for malicious programs which are added in each hourly update. Consequently, it’s also easy to estimate the number of malicious programs which could potentially infect the 76% of users who do not update their solutions daily.
 |
| Fig. 3: Screenshot from http://www.kaspersky.com/viruswatchlite/ |
Presenting the number of new antivirus records added every year in graph form (figure 4) clearly shows that growth is exponential rather than linear. This means that the rate at which new malicious programs appear is also growing.
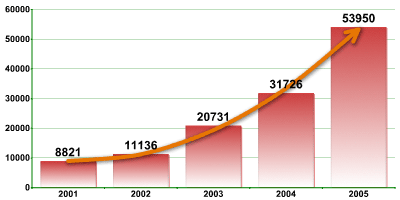 |
| Fig. 4: Number of malicious programs detected per year. |
Unfortunately, security does not only depend on the speed at which antivirus vendors respond to new threats. Users need to take a multifaceted approach and install patches that rectify vulnerabilities in the operating system and other software they use. What happens if users don’t do this? The events of August 2005, when an exploit was released for the vulnerability detailed in Microsoft Security Bulletin MS05-39, vividly demonstrates the complacency of users and the rapidity with which cybercriminals moved to exploit the vulnerability. Events developed as follows (figure 5):
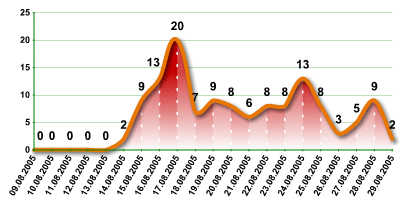 |
| Fig.5: Number of unique malicious programs exploiting the MS05-39 vulnerability per day (August 2005). |
On August 9th, Microsoft released a patch for the vulnerability detailed in MS05-39.
Three days later (on August 12th) proof of concept (PoC) code appeared; it took virus writers another two more days to develop the first malicious program to exploit the vulnerability. On August 14th, the Zotob worm was released, and, as mentioned above, caused network problems for several major companies. The graph above shows how the situation then evolved: there was a surge in the number of malicious programs based on Exploit.Win32.MS05-39, and the graph details how many unique malicious programs were detected every day). The conclusions are clear; installing patches promptly is as important as updating antivirus databases regularly. This is particularly relevant if we take into account the fact that virus writers actively wait for new PoC code which exploits critical vulnerabilities, and that the identification of new critical vulnerabilities almost inevitably leads to a surge in virus activity.
Given all of the above, potential zero-day exploits for critical vulnerabilities are a major worry. The speed at which virus writers react to new vulnerabilities could result in a virus pandemic.
So why does response speed matter? Data shows that the mass mailing of a malicious program to several million addresses using a botnet (a network of infected machines) takes about two hours. Therefore, every additional minute translates into thousands, even tens of thousands, potential new victims, making the speed at which antivirus companies respond crucial.
That Human Factor Again:
The human factor is undoubtedly hugely important. But how exactly does it affect the issue of IT security?
One example is the case of the MS05-39 vulnerability was mentioned above. The human factor certainly played a negative role here: users had a whole five days to install a patch, but many failed to do so. In some cases, this was due to in-company security policies or other limitations, but many users were simply careless, an all too human characteristic.
Another example is the case of websites which were attacked by the Monikey worm. This malicious program spread in emails disguised as a message saying that the recipient had been sent an e-card. The messages included links to the worm’s body which had been placed on numerous compromised websites. Many site administrators removed the worm’s body from their websites but didn’t block the channel used by the malicious program to penetrate the sites. As a result, the malicious program appeared on their websites repeatedly.
Unfortunately, it’s not only individuals who can be careless, but large organizations as well. In 2005 legal products containing malicious code were released, including removable storage media, software based on virus-related technologies, infected distributives etc. A curious case arose in late 2005, when a Russian billing center gave a non-existent domain (himbank.ru) in bills which were sent to clients. The address was intended for clients who wished to pay their utility bills via the Internet. Clearly, anyone could have registered this domain name and emptied the e-wallets of unsuspecting recipients. Several hundred users did try to make payment via the address during a short period of time.
Let’s move on to social engineering, which is a method virus writers (among others) use to exploit human weaknesses. The events of 2005 bear witness to the fact that virus writers are constantly looking for new and ever more sophisticated methods which will enable their creations to penetrate machines and networks.
Cybercriminals used a number of tragic events in the course of 2005 for their own gain. They exploited the fact that such events are followed by increased public interest in information relating to these events. Below are just a few examples:
- The terrorist bombings in the London Underground, which claimed about 50 lives, was followed by the mass spamming of emails entitled “TERROR HITS LONDON”. These messages contained a Trojan program; to allay suspicion, the message text included a statement that the message had been scanned by an antivirus program.
- Reports of bird flu led to the mass mailing of advertisements for a bogus drug which would, naturally, have no therapeutic effect.
- Hurricane Katrina was followed by spam entitled “Katrina killed as many as 80 people”. The message itself contained no malicious code, but it was written so as to arouse as much interest as possible. The message body contained only partial information; the user was expected to click a “Read more” link to get the rest. When the user clicked on the linked, malicious code was downloaded to the victim machine.
Of course, cybercriminals don’t only exploit users’ interest in tragic events; they use many other topics and issues, including the topic of malicious software. The situation is so grave that some users install as many antivirus solutions as they can. They mistakenly believe that the more antivirus products, the better the protection: if the first solution misses a malicious program, the second, third or fourth will be sure to detect it. Cybercriminals play on this fallacy; they use spam technologies to distribute malicious programs in the guise of antivirus solutions from well-known vendors. This method of infecting computers, which is based on users’ trust in antivirus companies, ultimately undermines this trust; users often find it hard to believe that the emails they thought were from antivirus companies were actually sent by somebody else.
Given that attacks always precede the release of protection against them – this is only logical – the antivirus industry is always half a step behind cybercriminals. Ensuring user security can be difficult, as users themselves often unwittingly aid and abet cybercriminals in infecting machines. Antivirus companies not only have to find solutions which are effective against technically sophisticated penetration methods, but also have to educate users to raise awareness of security issues and the will to tackle such problems. Despite the active educational work which the antivirus industry conducts, the number of users which performs potentially risky actions, such as opening attachments from unknown senders, remains relatively high. A Kaspersky Lab user poll, “What makes you open suspicious messages?” confirms this.
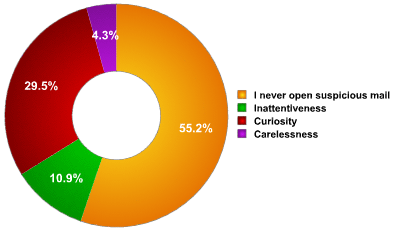 |
| Fig.6: “What makes you open suspicious messages?” |
Other Trends
New Technologies
Technologies are constantly evolving, and both cybercriminals and the IT industry make use of new technologies.
It is not the increased rate at which new malicious technologies appear that causes concern. Another, related issue is the rate at which existing technologies are being combined and adapted, resulting in more effective infection methods and a faster move towards malicious code for new platforms.
Step by step, cybercriminals are starting to target mobile devices which run fully functional operating systems (e.g. smartphones, PDAs etc). However, a significant increase in the number of malicious programs for mobile devices is still in the future. Once the number of smartphone owners who use e-payment services, and who use their phones to access such services reaches critical mass, this will undoubtedly motivate cybercriminals to start actively targeting smartphone users as a source of potential profit.
The concept of smart homes is moving ever closer to becoming a reality. Of course, smart home technology is still in its infancy, but it does exist. Time will tell if smart homes will evolve into a profitable new platform for cybercriminals to target and infect.
Rootkits
The term ‘rootkit’ as used in this article means a programming technique or code which is designed to conceal activity or objects in the system. Cybercriminals often use rootkits to hide processes, files, registry keys and network activity, all of which could reveal the presence of a malicious program in an infected system.
Rootkits are continuing to evolve and be actively used by cybercriminals. This is unsurprising, as implementing rootkits can significantly prolong the lifespan of a malicious program in an infected system as the victim is unable to detect the malicious object using standard operating system tools. An average of 6 rootkits per month were detected in 2000, but by the end of 2005, Kaspersky Lab analysts were detecting 32 such programs a month. This almost quadruple increase is shown in the graph below:
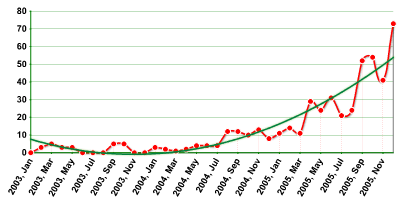 |
| Fig. 7: Increase in rootkits. |
Throughout last year, kernel-mode rootkits gradually gained in popularity over user-mode rootkits (clickhere for more information on rootkits). This indirectly indicates that there are a large number of users who use the administrator account by default, without realizing that this makes their machines potential targets, and can have serious consequences.
Business-malware
Malicious programs which can be classified as business malware are widespread, as are programs which can be classified as CrimeWare. However, nearly all malicious programs which are added to antivirus databases can be used for criminal ends. Discussing the finer details of classification is beyond the scope of this article, and the topic will therefore be treated in a separate article. However, there is space here to examine the changes which took place in this category during 2005.
The most popular type of business malware is those programs designed to steal financial data and resources. The graph below shows that this category of malware grew five-fold in 2005. The vertical axis shows the number of new malicious programs in this category identified by our analysts.
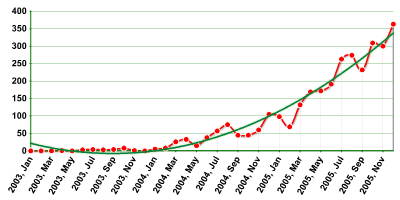 |
| Fig. 8: Increase in business malware. |
The graph clearly shows that cybercriminals see enormous profit opportunities in e-banking and e-trading systems, leading to the huge increase in business malware. Additionally, last year an increasing number of malicious programs which targeted several payment systems at once were intercepted. Prior to this, such programs were designed to target individual e-banking and e-trading systems.
Blackmail
The number of cyber-blackmail cases increased throughout 2005.
One of the reasons for this is the anonymity of the Internet, which enables cybercriminals to use blackmail with impunity. DDoS attacks are often used to attack e-commerce companies; however, Trojans which modify data are often used to attack end users. The cybercriminals will then demand money in return for restoring the modified data to its original condition.
Several examples of such malicious programs appeared in 2005, including Virus.Win32.GPCode (which encrypts user data on the hard drive), and Trojan.Win32.Krotten (which modifies the system registry in order to prevent the computer from functioning correctly).
Many users find it easier to pay the sum demanded than to wait several hours for a decryption utility from an antivirus company. The problem is that the money paid to cybercriminals encourages them to create new modifications of the malicious programs. One example of this is GPCode, originally a primitive virus, which evolved into a variant using asymmetric encryption.
Kaspersky Lab analysts have been closely tracking the evolution of such programs over the course of the year. It’s clear that such blackmail techniques will continue both to be widely used, and to continue their rapid evolution.
User Recommendations
Although this article covers a variety of security issues, there are a number of simple recommendations which will help users avoid or combat most cyberthreats.
- Do not open attachments or click links in messages which you were not expecting. This applies to emails and messages received via any other network client (e.g., ICQ). Moreover, the rule applies both to messages from unknown senders and from those in your contact list; there are lots of malicious programs that infect computers and then send messages to all contacts found. The attachment or link is usually accompanied by a plausible-sounding text encouraging the recipient to activate it. If you weren’t expecting a message, check with the sender whether the attachment or link is genuine.
- Update your antivirus solution regularly.
- Update your operating system and other software regularly.
- Back up your data regularly. This will enable you to restore data if your system crashes or data is rendered unusable by malicious programs.
- Do not use the administrator account unless necessary.
- Use a firewall.
Conclusion
Sadly, last year gives no grounds for optimism. On the contrary, 2005 brought new attack methods, and the adaptation and evolution of existing malicious technologies. All of this means that current malicious technologies can now not only be used with increased effect, but can also be used to target new platforms.
The results of 2005 shows that cybercriminals are likely to continue to focus on mobile devices and the financial sector. However, rootkits, botnets, cyber-blackmail and other criminal activities are likely to remain popular. Although law enforcement bodies have stepped up their efforts in relation to tracking and convicting cybercriminals, the threats still outweigh the countermeasures taken. It is therefore essential that users take steps to help ensure their own cyber safety.



















Malware Evolution: 2005, part two